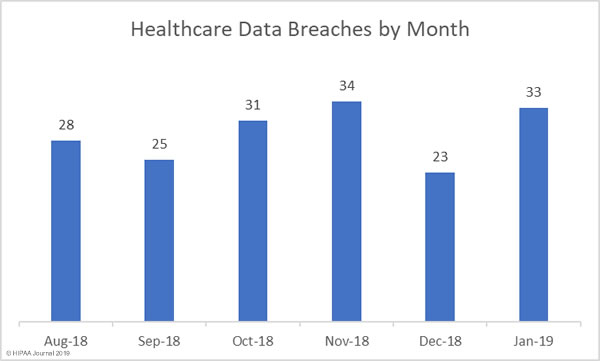
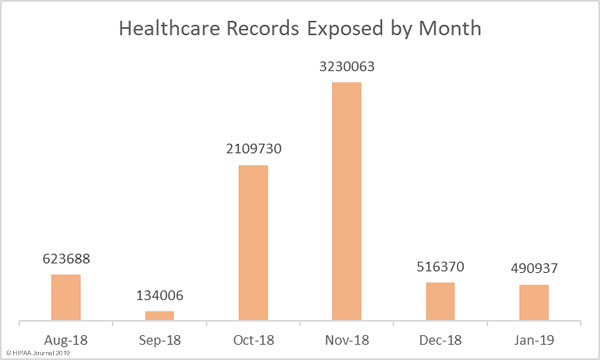
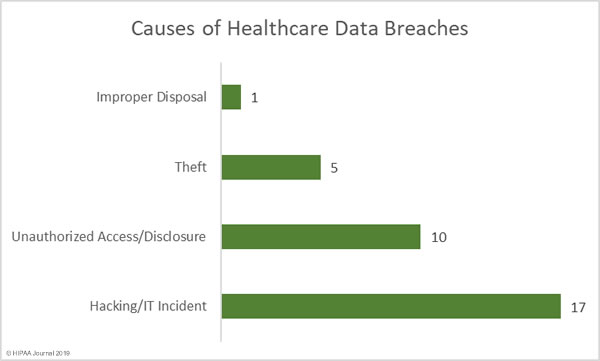
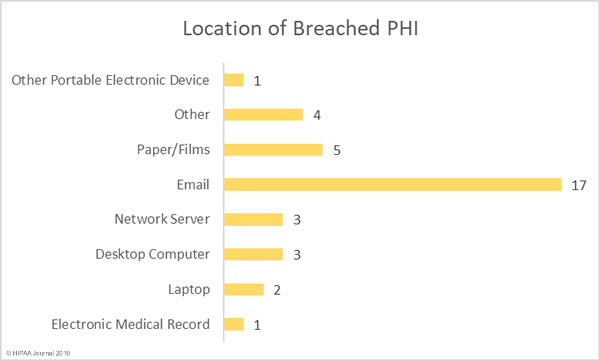
The National Health Service (NHS) has commissioned a report on the costs of pagers and the extent of their use in NHS Trusts in the UK. The study revealed around 130,000 pagers are used in NHS Trusts – Approximately 10% of the world’s pagers – and the annual cost is around £6.6 million ($8.73 million).
Advantages and Disadvantages of Pagers in Healthcare
Pagers have served the healthcare industry well for several decades and they are still useful devices. Pagers are easy to use, they are small, easy to carry, and batteries can last months between charges. The pager system uses its own transmitters and frequencies and the signals can pass through structures. Consequently, coverage is excellent, and communication is fast and reliable. Pagers have one function and they perform that task very well.
However, there are many drawbacks to pagers in healthcare. Most of the pagers used by NHS Trusts do not support two-way communication. When a message is received, a doctor must find a phone and call a number to receive the message. When an immediate response is not possible, messages are often written down and they can be forgotten or lost. When responding to messages, doctors often find the number is engaged and so begins a time-consuming game of phone tag. Pages also do not convey the sense of urgency.
To investigate the use of pagers, the Department of Health commissioned a report from CommonTime, a digital solutions company. The firm concluded that the devices should not continue to be used in the NHS and that it was surprising for legacy equipment such as pagers to still be relied upon in emergency situations.
UK Health Secretary Matt Hancock is keen to see legacy technology such as pagers phased out. He views emails and mobile phones as a better option in terms of speed, security, and cost. Pagers are expensive to run. Switching to alternative, modern methods of communication could save the NHS millions each year. The report suggests that the use of mobile devices and mobile software in place of pagers could save the NHS around £2.7 million ($3.57 million) a year.
Messaging Apps and Secure Email to Replace NHS Pagers
Secure messaging apps on smartphones are a viable alternative to pagers and can be run at a fraction of the cost. The apps offer similar capabilities as WhatsApp and Skype, but with enhanced security and message accountability.
The West Suffolk NHS Foundation Trust trialed the use of a smartphone app in 2017 and replaced all of its pagers and found that it saved a considerable amount of time communicating with doctors and saved on costs. The app allowed two-way communications between doctors, could be used by healthcare professionals to communicate with each other, allowed group chats, and worked on smartphones, tablets and desktops.
Mobile technology may improve security and allow the NHS to cut costs, but the technology is not without drawbacks. There are often dead-spots in hospitals where signals cannot be received on mobile devices, mobile networks can face slowdowns which delay the delivery of urgent messages, and there is potential for mobile devices to interfere with hospital equipment. Those issues will need to be resolved over the coming two years, although NHS Trusts will be permitted to keep some pagers for emergency situations, such as when mobile networks go down or hospital Wi-Fi goes offline.
Fax Machines to be Phased Out by 2020
The latest report follows a 2018 study by the Royal College of Surgeons which revealed that the NHS was still using around 9,000 fax machines to send documents. In December 2018, the Department of Health announced that fax machines would be phased out and would be replaced by secure, encrypted email to improve patient safety and cybersecurity. NHS Trusts have not been permitted to buy new fax machines since January 2019 and fax machines will be completely phased out by April 2020.
These are just two of the initiatives that Hancock is pursuing to update the technology used by the NHS. As the May 2017 WannaCry ransomware attacks showed, it is not just legacy equipment that is a problem. A study conducted after the attacks revealed 60% of NHS Trusts were still using Windows XP, even though the operating system is a major security risk and is no longer supported. In May 2018, the UK government signed a £150 million ($1.98 million) deal with Microsoft to upgrade all Windows XP and Windows 7 machines to Windows 10. That process will be completed by January 14, 2020.
The post NHS to Phase Out Pagers by End of 2021 appeared first on HIPAA Journal.