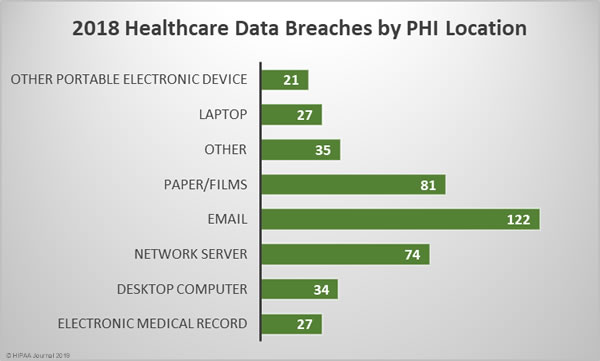
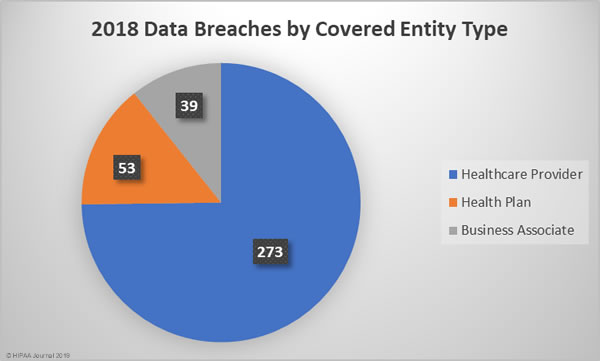
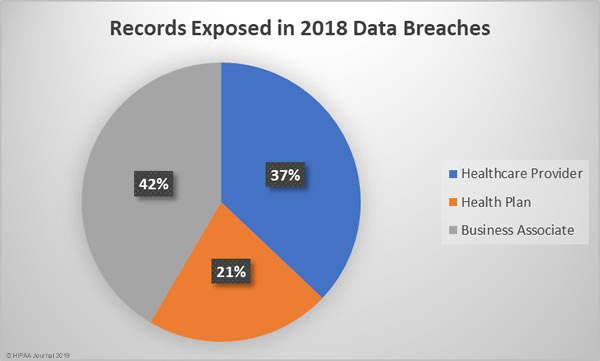
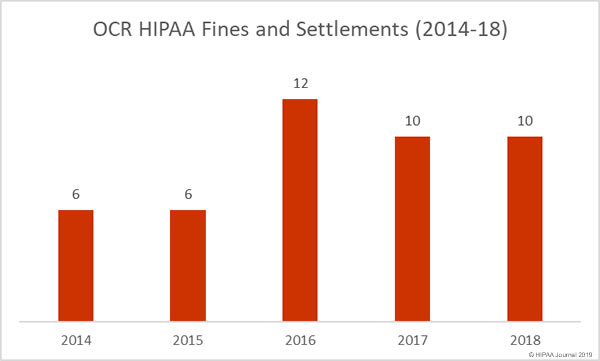
On Monday, February 11, 2019, the HHS’ Office of the National Coordinator for Health Information Technology (ONC) and the Centers for Medicare and Medicaid Services (CMS) released new rules covering patient data access and information blocking.
The aim of the new rules is to advance interoperability and support the meaningful exchange and use of health information. The rules are intended to increase competition, encourage innovation, and give patients control over their health data.
One of the main goals is to make health information accessible via application programming interfaces (APIs). Currently consumers use a wide range of smartphone apps for paying bills and accessing information. It should be just as easy to gain access to healthcare data through apps and for healthcare data to be provided electronically at no cost.
One of the main requirements of the new rules is for healthcare providers and health plans to implement data sharing technologies that support the transition of care to new healthcare providers and health plans. Whenever a patient wishes to start seeing a new physician or wants to change to a new health plan, their health data should be seamlessly transferred.
The CMS rule proposes that by 2020, all healthcare organizations working with Medicare and Medicaid will be required to share health information and claims data with patients electronically via an API. This would make it easy for patents to change health plan and take their data with them. It will ensure that by 2020, 125 million patients will be able to receive their claims information electronically.
The ONC rule updates its conditions of certification, which require health IT developers to publish APIs that allow access to patient data without any special effort. The goal is for healthcare organizations to adopt standardized APIs to support the accessing of structured and unstructured health data via mobile devices.
The ONC rule implements the 21st Century Cure Act’s information blocking provisions and adds seven new exceptions to the information blocking rule – Actions and activities which are not classed as information blocking.
The new exceptions are:
- Practices that prevent patients from being harmed
- Practices that protect the privacy of electronic health information
- Practices that ensure the security of electronic health information
- Maintaining and improving health IT performance with user agreement
- Recovering reasonable costs to allow the exchange, use, and accessing of electronic health information
- Denying access, exchange, and use of electronic health information because it is unfeasible or would impose a substantial burden, which is unreasonable under the circumstances.
- Licensing of technical artifacts to support the interoperability of electronic health information on reasonable and non-discriminatory terms
The ONC has proposed that healthcare providers found to be blocking information sharing should be named and shamed to discourage the practice and suggests that those organizations may also face financial penalties. “We are going to expose the bad actors who are purposely trying to keep patients from their own information,” explained CMS Administrator Seema Verma
Comments have also been requested on including pricing information along with electronic health information to allow patients to see exactly how much they are paying for their healthcare.
“These proposed rules strive to bring the nation’s healthcare system one step closer to a point where patients and clinicians have the access they need to all of a patient’s health information, helping them in making better choices about care and treatment,” said HHS Secretary Alex Azar. “By outlining specific requirements about electronic health information, we will be able to help patients, their caregivers, and providers securely access and share health information. These steps forward for health IT are essential to building a healthcare system that pays for value rather than procedures, especially through empowering patients as consumers.”
The post ONC and CMS Propose New Rules on Patient Access and Information Blocking appeared first on HIPAA Journal.