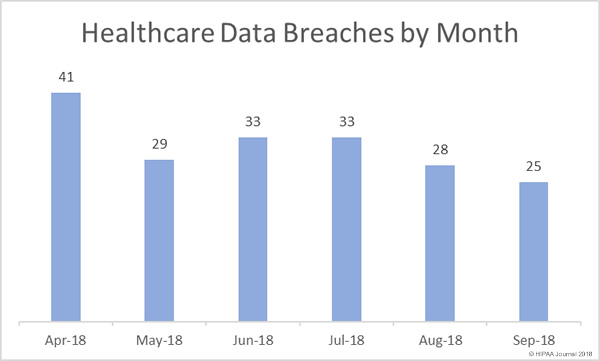
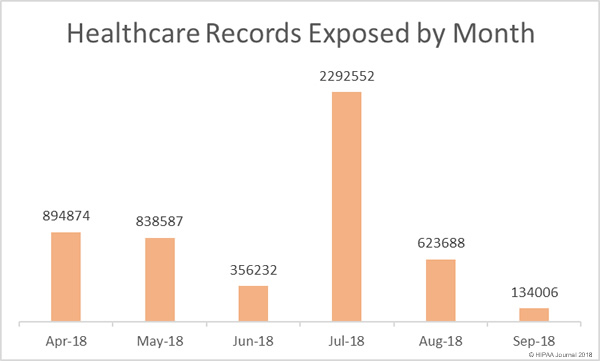
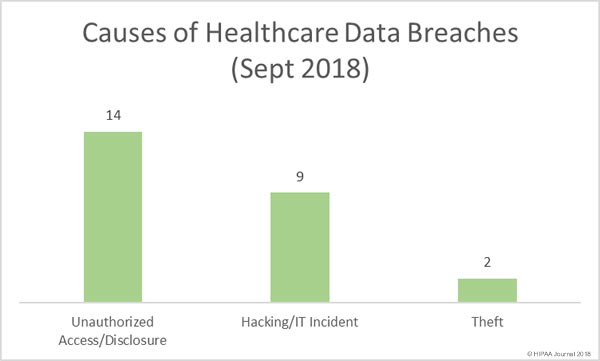
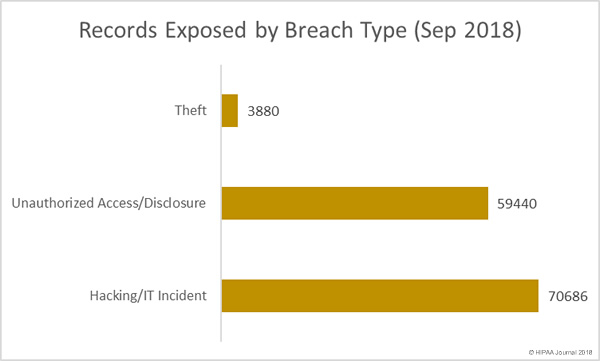
The U.S. Department of Homeland Security will be forming a new agency solely focused on cybersecurity following the passing of new legislation by Congress.
The Cybersecurity and Infrastructure Security Agency Act of 2018 (CISA Act) amends the Homeland Security Act of 2002 can calls for DHS to form a new Cybersecurity and Infrastructure Security Agency. The CISA Act was unanimously passed by the House of Representatives and just awaits the president’s signature.
The new agency will be formed through the reorganization of the National Protection and Programs Directorate (NPPD) and will have the same status as other DHS agencies such as the U.S. Secret Service.
The NPPD is already responsible for reducing and eliminating threats to U.S. critical physical and cyber infrastructure, with cybersecurity elements covered by the Office of Cybersecurity and Communications and the National Risk Management Center.
NPPD currently coordinates IT security initiatives with other entities, local, state, tribal and territorial governments and the private sector and oversees cybersecurity at federal government civilian agencies.
The new name better reflects the work NPPD does and emphasizes the importance of cybersecurity in securing the nation’s critical infrastructure. The new agency will consolidate information security and physical infrastructure security in a unified agency.
“The cyber threat landscape is constantly evolving, and we need to ensure we’re properly positioned to defend America’s infrastructure from threats digital and physical,” said DHS Secretary Kirstjen M. Nielsen. “It was time to reorganize and operationalize NPPD into the Cybersecurity and Infrastructure Security Agency.”
Having a single agency in charge of the nation’s cybersecurity will help the U.S. government address current security gaps. At present, each federal agency is responsible for its own IT systems and managing cyber risks. Regardless of size and budget, each government entity must ensure cyber risks are managed and reduced to a minimal level. There are also several government agencies that cover various cybersecurity functions, which is inefficient and results in security gaps.
“Elevating the cybersecurity mission within the Department of Homeland Security, streamlining our operations, and giving NPPD a name that reflects what it actually does will help better secure the nation’s critical infrastructure and cyber platforms,” said Christopher Krebs, current undersecretary of the NPPD. “The changes will also improve the Department’s ability to engage with industry and government stakeholders and recruit top cybersecurity talent.”
The post Congress Passes CISA Act Which Calls for New Cybersecurity Agency Within DHS appeared first on HIPAA Journal.