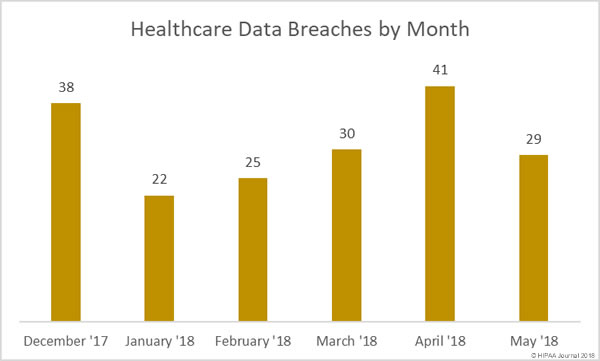
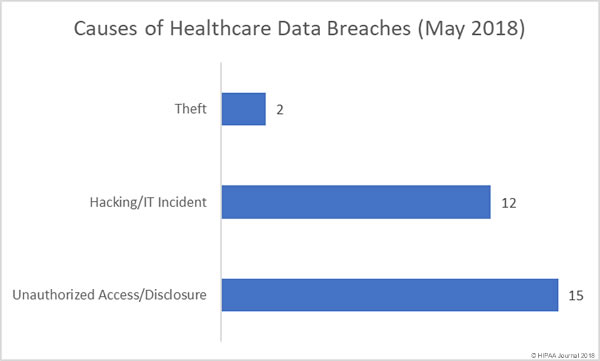
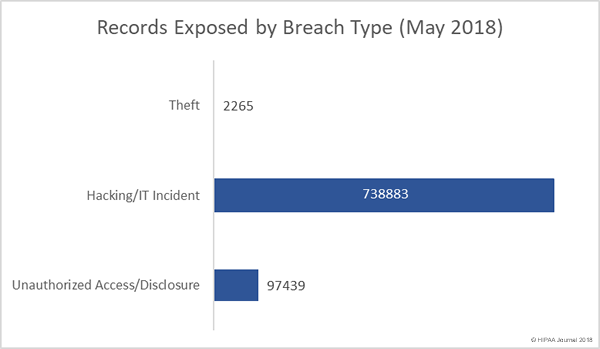
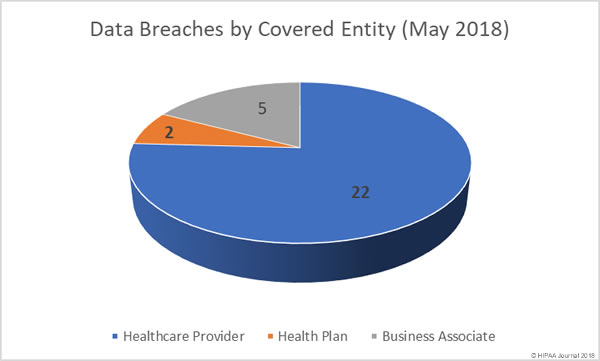
Healthcare organizations have been reminded of HIPAA patch management requirements to ensure the confidentiality, integrity, and availability of ePHI is safeguarded.
Patch Management: A Major Challenge for Healthcare Organizations
Computer software often contains errors in the code that could potentially be exploited by malicious actors to gain access to computers and healthcare networks.
Software, operating system, and firmware vulnerabilities are to be expected. No operating systems, software application, or medical device is bulletproof. What is important is those vulnerabilities are identified promptly and mitigations are put in place to reduce the probability of the vulnerabilities being exploited.
Security researchers often identify flaws and potential exploits. The bugs are reported to manufacturers and patches are developed to fix the vulnerabilities to prevent malicious actors from taking advantage.
Unfortunately, it is not possible for software developers to test every patch thoroughly and identify all potential interactions with other software and systems and still release patches in a timely manner.
Therefore, IT departments must test the patches before they are applied. IT teams must also ensure that patches are applied on all vulnerable systems and no device is missed.
With so many IT systems and software applications in use and the frequency that patches are released, patch management can be a major challenge for healthcare organizations.
HIPAA Patch Management Requirements
The HHS’ Office for Civil Rights has recently drawn attention to the importance of patching in its June 2018 cybersecurity newsletter. OCR explains the HIPAA patch management requirements and how patching vulnerable software is an essential element of HIPAA compliance. OCR describes patch management as “the process of identifying, acquiring, installing and verifying patches for products and systems.”
“Security vulnerabilities may be present in many types of software including databases, electronic health records (EHRs), operating systems, email, applets such as Java and Adobe Flash, and device firmware,” wrote OCR. “Identifying and mitigating the risks unpatched software poses to ePHI is important to ensure the protection of ePHI and in fulfilling HIPAA requirements.”
Patch management is not specifically mentioned in the HIPAA Security Rule, although the identification of vulnerabilities is covered in the HIPAA administrative safeguards under the security management process standard.
Vulnerabilities to the confidentiality, integrity, and availability of ePHI should be identified through an organization’s risk analyses – 45 C.F.R. § 164.308(a)(1)(i)(A) – and subjected to HIPAA-compliant risk management processes – 45 C.F.R. § 164.308(a)(1)(i)(B).
Patch management is also covered under the security awareness and training standard – 45 C.F.R. § 164.308(a)(5)(ii)(B) – protection from malicious software – and the evaluation standard – 45 C.F.R. § 164.308(a)(8).
Discovering Vulnerabilities and Possible Mitigations
To ensure patches can be applied, it is essential for IT teams to have a complete inventory of all systems, devices, operating systems, firmware, and software installed throughout the organization. Regular scans should also be conducted to identify unauthorized software – shadow IT – that has been installed.
The United States Computer Emergency Readiness Team (US-CERT) and the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) provide up to date information on new vulnerabilities, mitigations, and patches. Covered entities should regularly check their websites and, ideally, sign up for alerts. Information on vulnerabilities and patches should also be obtained from software vendors and medical device manufacturers.
The Patch Management Process
In order for a HIPAA-covered entity to ensure HIPAA patch management requirements are satisfied and vulnerabilities to the confidentiality, integrity, and availability of ePHI are reduced to an acceptable level, robust patch management policies and procedures need to be developed and implemented.
OCR suggests the patch management process should include:
- Evaluation: Determine whether patches apply to your software/systems.
- Patch Testing: Test patches on an isolated system to determine if there are any unforeseen or unwanted side effects, such as applications not functioning properly or system instability.
- Approval: Following testing, approve patches for deployment.
- Deployment: Deploy patches on live or production systems.
- Verification and Testing: After deployment, continue to test and audit systems to ensure patches have been applied correctly and that there are no unforeseen side effects.
Resources:
NIST Special Publication 800-40 Guide to Enterprise Patch Management Technologies (Revision 3) is an excellent resource covering best practices for patch management.
The post OCR Draws Attention to HIPAA Patch Management Requirements appeared first on HIPAA Journal.