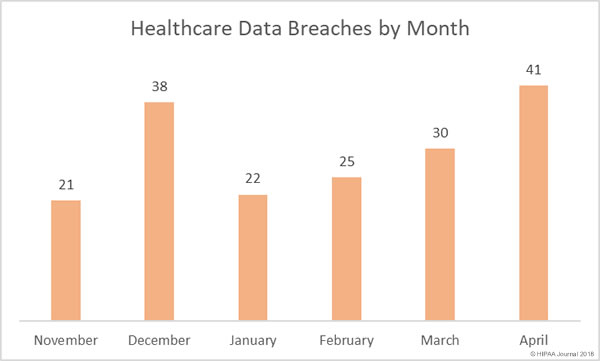
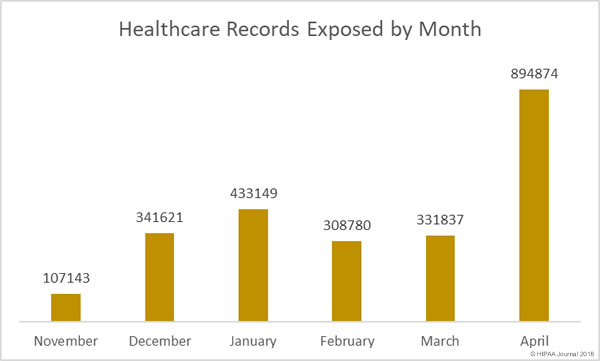
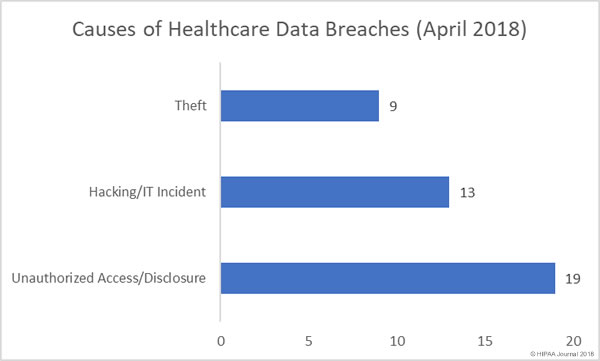
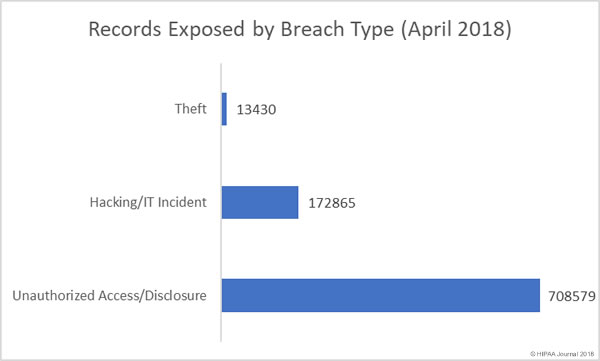
A recent audit conducted by the Government Accountability Office (GAO) has shown patients still face many challenges obtaining copies of their health information and healthcare providers and insurers are struggling to meet HIPAA requirements – and in some cases – are breaching HIPAA Rules.
A 21st Century Cures Act provision required GAO to conduct a study on patient access to medical records. The audit involved interviews with stakeholders, vendors, provider organizations, patient advocates, and state and HHS officials. The audit was conducted in four states – Ohio, Kentucky, Rhode Island and Wisconsin – which were chosen, in part, due to the range of fees charged for providing patients with copies of their medical records.
Under HIPAA, patients are permitted to request copies of their health records from their providers. Patients can request their health records in paper or digital form and the requests must be processed within 30 days. HIPAA-covered entities are allowed to charge a reasonable, cost-based fee for providing patients with copies of their health data.
Patients obtain copies of their health information for several reason: To take a more active role in their own healthcare, to take their medical records to new providers, to resolve disputes with their insurers, to provide to lawyers, or for disability claims.
Patients also make requests for their records to be forward on to another person or entity by their provider, such as when they want a second opinion from another physician. Third parties may also be instructed by patients to obtain copies of their health records – a lawyer for example.
The GAO audit determined that the fees charged by providers varied considerably from state to state and for different types of request.
Some states have established fee schedules, formulas and limits for allowable fees. Three of the states – Ohio, Rhode Island, and Wisconsin – have established per-page fee amounts and different rates for obtaining medical images such as copies of X-rays. Ohio has established a per-page fee amount for third party requests, Rhode Island has a maximum fee for providers that use an EHR for patient and patient-directed requests, while Kentucky allows patients to obtain one free copy of their medical records and sets a maximum charge of $1 per page for any additional copies.
While HIPAA stipulates that providers can only charge a reasonable, cost-based fee for patient requests and patient-directed requests, those limits do not apply to third party requests for copies of data, and the charges are often considerably higher.
Excessive Fees Charged for Providing Copies of Health Information
In 2016, the Department of Health and Human Services’ Office for Civil Rights issued guidance for HIPAA-covered entities on the fees that could be charged for providing patients with copies of their health information. Even so, some providers are not following HIPAA Rules.
In the GAO report, examples are provided of the excessive fees that have been charged. One patient was charged a fee of $148 for a single PDF of their medical records, and two patients were each charged more than $500 for a single request to obtain a copy of their medical records. One patient was charged a retrieval fee by a release-of-information (ROI) vendor for a copy of her health records, even though such fees are not permitted under HIPAA. There have also been cases of providers charging annual subscription fees for providing access to medical records.
One problem faced by patients whose medical conditions have required many visits to physicians is the amount of data stored by their providers. Their health records span many pages and fees are charged per page. That can make obtaining copies of health records prohibitively expensive.
The GAO report indicates many patients have made attempts to obtain copies of their medical records from their providers but cancelled the requests when they discovered to cost of doing so. There have been cases where providers have refused patients who have requested copies of their health records and patients have failed to challenge their providers.
The report made it clear that even though efforts have been made to improve understanding of HIPAA Rules, many patients are still unsure of their rights under HIPAA.
Healthcare Organizations Face Major Challenges Providing Access to Health Records
It is not only a challenge for patients to obtain their health records. Many providers also face challenges finding and retrieving information and processing the requests. Often, patients’ data are stored in digital format and on paper/film. Paper records may be stored in different locations and digital records stored in multiple EHRs.
Many providers find it difficult to allocate the necessary resources to the task of providing copies of medical records to patients and staff struggle to find the time to process requests due to extremely busy workloads.
Thorough checks must be made of the records to make sure patients are only provided with data from their own records. Sometimes, the process of transferring data from physical records to digital versions result in different patient records being merged.
There are also security challenges. While HIPAA allows patients to receive digital copies of their data, on a memory stick for example, plugging in such a device could introduce a malware infection.
Some healthcare providers have eased the strain by making patient health information available through patient portals. This has helped reduce the number of requests for providing copies of health data. Unfortunately, patient portals do not contain entire health records and patients may not be able to get the information they need.
Interviews with OCR officials revealed hundreds of complaints have been submitted by patients who have experienced difficulties accessing their medical records. The most common complaints are the failure of a provider to process requests for copies of health information within 30 days, excessive fees for the information, the failure to respond to requests to send health records to caregivers and family members, and denying requests from parents to obtain copies of their children’s medical records.
OCR is currently considering whether any further guidance is required to clarify allowable fees under HIPAA Rules, further to the guidance it issued on the matter in 2016.
The post GAO: Medical Records Can be Difficult and Expensive to Obtain appeared first on HIPAA Journal.