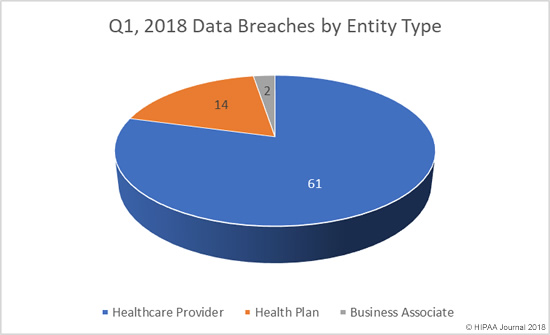
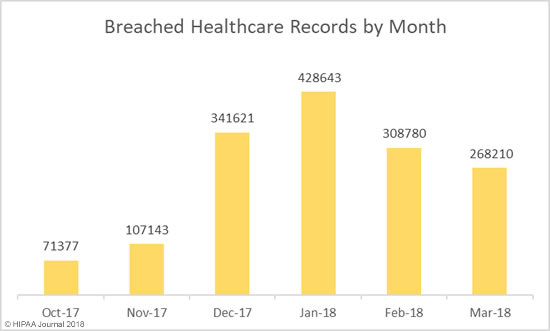
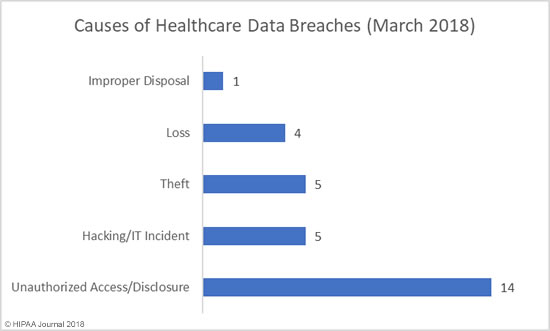
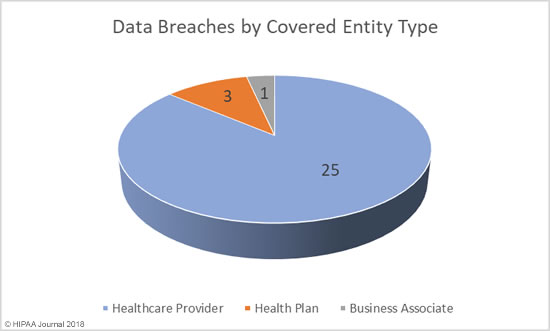
One of the biggest data security challenges is how to defend against insider threats in healthcare. Insiders are responsible for more healthcare data breaches than hackers, making the industry unique.
Verizon’s Protected Health Information Data Breach Report highlights the extent of the problem. The report shows 58% of all healthcare data breaches and security incidents are the result of insiders.
Healthcare organizations also struggle to detect insider breaches, with many breaches going undetected for months or even years. One healthcare employee at a Massachusetts hospital was discovered to have been accessing healthcare records without authorization for 14 years before the privacy violations were detected, during which time the records of more than 1,000 patients had been viewed.
Healthcare organizations must not only take steps to reduce the potential for insider breaches, they should also implement technological solutions, policies, and procedures that allow breaches to be detected rapidly when they do occur.
What are Insider Threats?
Before explaining how healthcare organizations can protected against insider threats, it is worthwhile covering the main insider threats in healthcare.
An insider threat is one that comes from within an organization. That means an individual who has authorization to access healthcare resources, which includes EMRs, healthcare networks, email accounts, or documents containing PHI. Resources can be accessed with malicious intent, but oftentimes mistakes are made that can equally result in harm being caused to the organization, its employees, or its patients.
Insider threats are not limited to employees. Any individual who is given access to networks, email accounts, or sensitive information in order to complete certain tasks could deliberately or accidentally take actions that could negatively affect an organization. That includes business associates, subcontractors of business associates, researchers, volunteers, and former employees.
The consequences of insider breaches can be severe. Healthcare organizations can receive heavy fines for breaches of HIPAA Rules and violations of patient privacy, insider breaches can damage an organization’s reputation, cause a loss of patient confidence, and leave organizations open to lawsuits.
According to the CERT Insider Threat Center, insider breaches are twice as costly and damaging as external threats. To make matters worse, 75% of insider threats go unnoticed.
Insider threats in healthcare can be split into two main categories based on the intentions of the insider: Malicious and non-malicious.
Malicious Insider Threats in Healthcare
Malicious insider threats in healthcare are those which involve deliberate attempts to cause harm, either to the organization, employees, patients, or other individuals. These include the theft of protected health information such as social security numbers/personal information for identity theft and fraud, the theft of data to take to new employers, theft of intellectual property, and sabotage.
Research by Verizon indicates 48% of insider breaches are conducted for financial gain, and with healthcare data fetching a high price on the black market, employees can easily be tempted to steal data.
A 2018 Accenture survey conducted on healthcare employees revealed one in five would be prepared to access and sell confidential data if the price was right. 18% of the 912 employees surveyed said they would steal data for between $500 and $1,000.
Alarmingly, the survey revealed that almost a quarter (24%) of surveyed healthcare employees knew of someone who had stolen data or sold their login credentials to an unauthorized outsider.
Disgruntled employees may attempt to sabotage IT systems or steal and hold data in case they are terminated. However, not all acts of sabotage are directed against employers. One notable example comes from Texas, where a healthcare worker used hospital devices to create a botnet that was used to attack a hacking group.
Non-Malicious Insider Threats in Healthcare
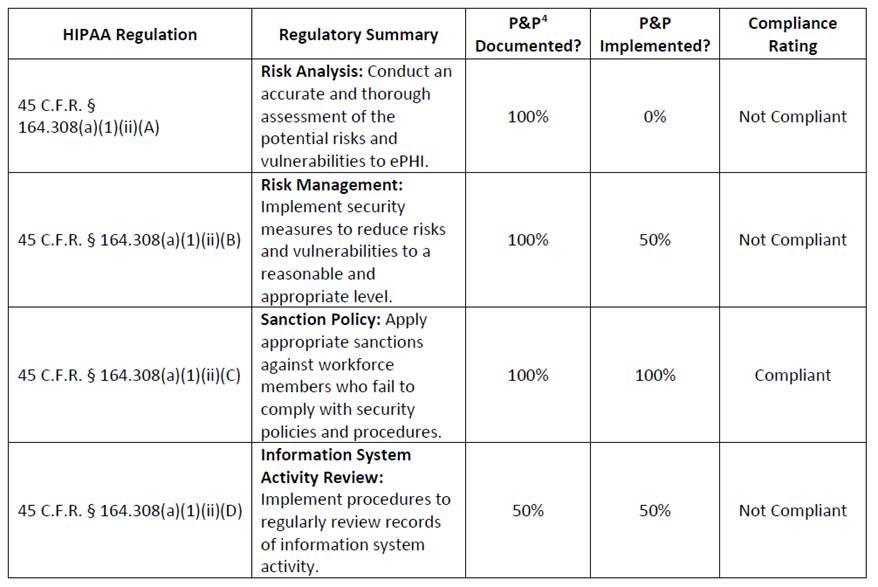
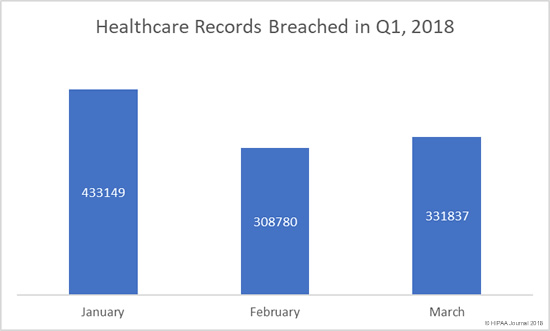
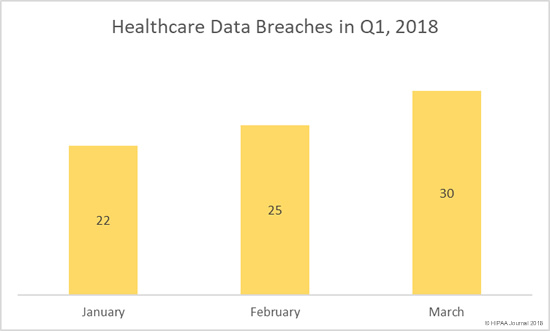
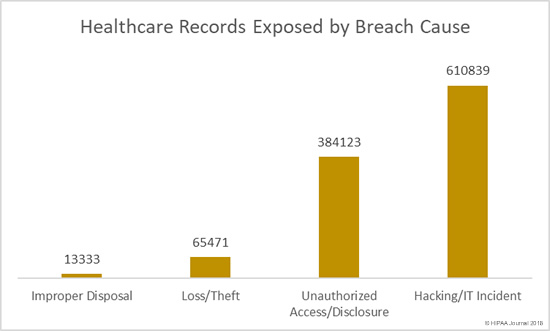
The Breach Barometer reports from Protenus/databreaches.net break down monthly data breaches by breach cause, including the number of breaches caused by insiders. All too often, insiders are responsible for more breaches than outsiders.
Snooping on medical records is all too common. When a celebrity is admitted to hospital, employees may be tempted to sneak a look at their medical records, or those of friends, family members, and ex-partners. The motivations of the employees are diverse. The Verizon report suggests 31% of insider breaches were employees accessing records out of curiosity, and a further 10% were because employees simply had access to patient records.
Other non-malicious threats include the accidental loss/disclosure of sensitive information, such as disclosing sensitive patient information to others, sharing login credentials, writing down login credentials, or responding to phishing messages.
The largest healthcare data breach in history – the theft of 78 million healthcare records from Anthem Inc.- is believed to have been made possible because of stolen credentials.
The failure to ensure PHI is emailed to the correct recipient, the misdirection of fax messages, or leaving portable electronic devices containing ePHI unattended causes many breaches each year. The Department of Health and Human Services’ Office for Civil Rights’ breach portal or ‘Wall of Shame’ is littered with incidents involving laptops, portable hard drives, smartphones, and zip drives that have stolen after being left unattended.
How to Defend Against Insider Threats in Healthcare
The standard approach to mitigating insider threats can be broken down into four stages: Educate, Deter, Detect, and Investigate.
Educate: The workforce must be educated on allowable uses and disclosures of PHI, the risk associated with certain behaviors, patient privacy, and data security.
Deter: Policies must be developed to reduce risk and those policies enforced. The repercussions of HIPAA violations and privacy breaches should be clearly explained to employees.
Detect: Healthcare organizations should implement technological solutions that allow them to detect breaches rapidly and access logs should be regularly checked.
Investigate: When potential privacy and security breaches are detected they must be investigated promptly to limit the harm caused. When the cause of the breach is determined, steps should be taken to prevent a recurrence.
Some of the specific steps that can be taken to defend against insider threats in healthcare are detailed below:
Perform Background Checks
It should be standard practice to conduct a background check before any individual is employed. Checks should include contacting previous employers, Google searches, and a check of a potential employee’s social media accounts.
HIPAA training
All healthcare employees should be made aware of their responsibilities under HIPAA. Training should be provided as soon as possible, and ideally before network or PHI access is provided. Employees should be trained on HIPAA Privacy and Security Rules and informed of the consequences of violations, including loss of employment, possible fines, and potential criminal penalties for HIPAA violations.
Implement anti-phishing defenses
Phishing is the number one cause of data breaches. Healthcare employees are targeted as it is far easier to gain access to healthcare data if an employee provides login credentials than attempting to find software vulnerabilities to exploit. Strong anti-phishing defenses will prevent the majority of phishing emails from reaching inboxes. Advanced spam filtering software is now essential.
Security awareness training
Since no technological solution will prevent all phishing emails from reaching inboxes, it is essential – from a security and compliance perspective – to teach employees the necessary skills that will allow them to identify phishing attempts and other email/web-based threats.
Employees cannot be expected to know what actions place data and networks at risk. These must be explained if organizations want to eradicate risky behavior. Security awareness training should also be assessed. Phishing simulation exercises can help to reinforce training and identify areas of weakness that can be tackled with further training.
Encourage employees to report suspicious activity
Employees are often best placed to identify potential threats, such as changes in the behavior of co-workers. Employees should be encouraged to report potentially suspicious behavior and violations of HIPAA Rules.
While Edward Snowden did not work in healthcare, his actions illustrate this well. The NSA breach could have been avoided if his requests for co-workers’ credentials were reported.
Controlling access to sensitive information
The fewer privileges employees have, the easier it is to prevent insider breaches in healthcare. Limiting data access to the minimum necessary amount will limit the harm caused in the event of a breach. You should be implementing the principle of least privilege. Give employees access to the least amount of data as possible. This will limit the data that can be viewed or stolen by employees or hackers that manage to obtain login credentials.
Encrypt PHI on all portable devices
Portable electronic devices can easily be stolen, but the theft of a device need not result in the exposure of PHI. If full disk encryption is used, the theft of the device would not be a reportable incident and patients’ privacy would be protected.
Enforce the use of strong passwords
Employees can be told to use strong passwords or long passphrases, but unless password policies are enforced, there will always be one employee that chooses to ignore those policies and set a weak password. You should ensure that commonly used passwords and weak passwords cannot be set.
Use two-factor authentication
Two-factor authentication requires the use of a password for account access along with a security token. These controls prevent unauthorized access by outsiders, as well as limiting the potential for an employee to use another employee’s credentials.
Terminate access when no longer required
You should have a policy in place that requires logins to be deleted when an employee is terminated, a contract is completed, or employees leave to work for another organization. There have been many data breaches caused by delays in deleting data access rights. Data access should not be possible from the second an employee walks out the door for the last time.
Monitor Employee Activity
If employees require access to sensitive data for work purposes it can be difficult to differentiate between legitimate data access and harmful actions. HIPAA requires PHI access logs to be maintained and regularly checked. Since this is a labor-intensive task, it is often conducted far too infrequently. The easiest way to ensure inappropriate accessing of medical records is detected quickly is to implement action monitoring software and other software tools that can detect anomalies in user activity and suspicious changes in data access patterns.
The post How to Defend Against Insider Threats in Healthcare appeared first on HIPAA Journal.