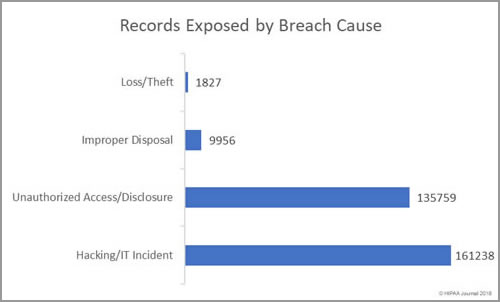
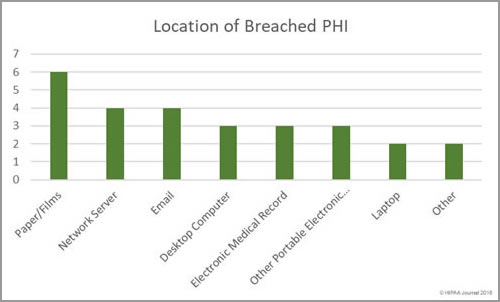
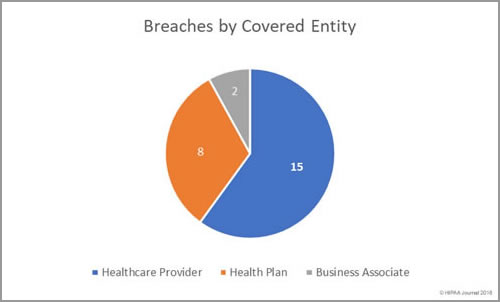
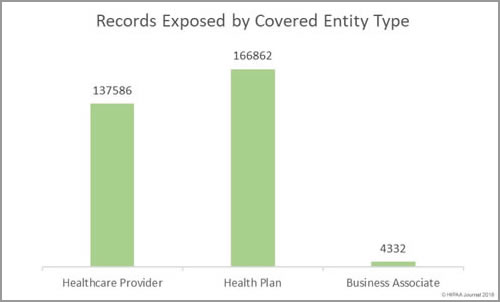
HIMSS has published the results of its annual healthcare cybersecurity survey, which provides insights into the state of cybersecurity in healthcare and identified the top healthcare security threats.
The HIMSS 2018 cybersecurity survey was conducted on 239 respondents from the healthcare industry between December 2017 and January 2018. The results of the survey were announced at the HIMSS 2018 Conference & Exhibition in Las Vegas.
36.8% of respondents had positions in executive management and 37.2% were employed in non-executive management positions. The remaining 25.9% were in non-management positions such as cybersecurity specialists and analysts. 41.2% of respondents were primarily responsible for cybersecurity, 32.6% had some responsibility, and 11.8% sometimes had responsibility for cybersecurity.
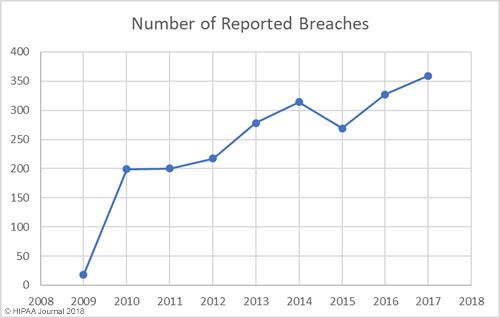
Most Healthcare Organizations Have Experienced a Significant Security Incident in the Past 12 Months
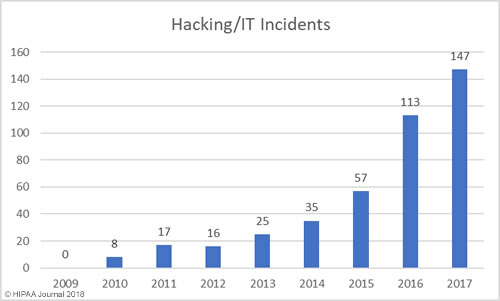
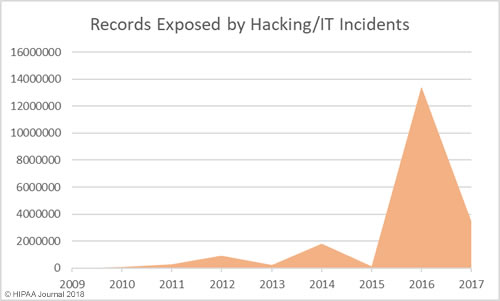
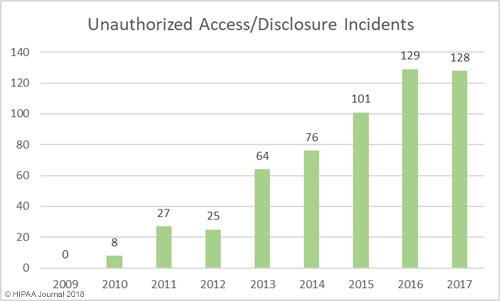
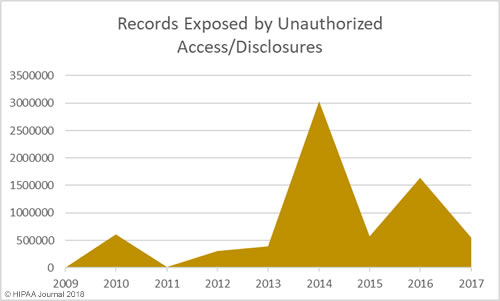
The threat of healthcare cyberattacks is greater than ever and the past 12 months has been a torrid year. In the past 12 months, 75.7% of respondents said they had experienced a recent significant security incident. 96% of those respondents were able to characterize the threat actor responsible, with the top three being online scam artists such as phishers (37.6%), negligent insiders (20.8%), and hackers (20.1%).
61.4% of respondents said email was the main initial point of compromise. In second place was ‘other’ which included compromised customer networks, web application attacks, guessed passwords, misconfigured software/cloud services, and human error. In joint third – both with 3.2% of responses – was a compromised organizational website and hardware/software pre-loaded with malware. 11.6% said they did not know how the attackers gained access to their networks/data.
In the majority of cases (68.2%), incidents were discovered internally (40.7% by security teams / 27.5% by non-security personnel). 67.7% of breaches were detected within 7 days, with 47.1% detected within 24 hours.
Healthcare Cybersecurity Is Improving
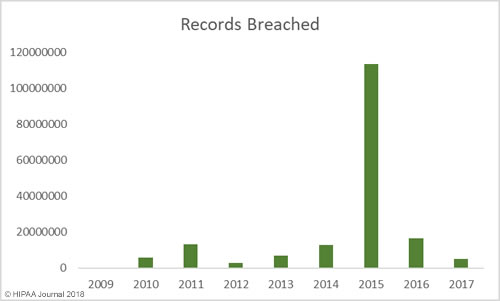
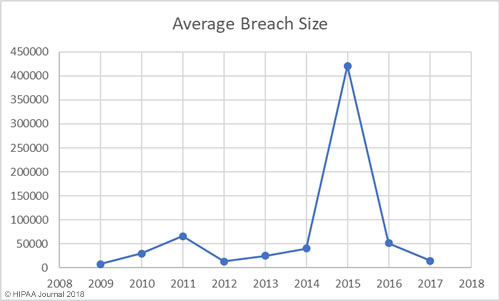
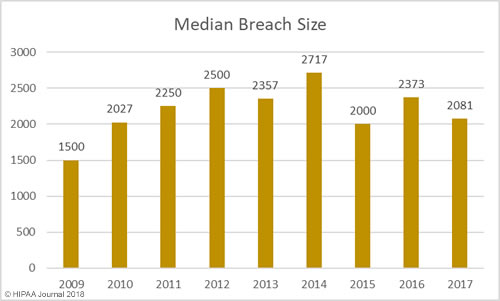
The past 12 months have seen an increase in healthcare security incidents, although the severity of data breaches has reduced year over year. This indicates cybersecurity in healthcare is improving, which was backed up by the HIMSS survey results.
84.3% of respondents said more resources are now being used to address cybersecurity with only 3.3% saying resources have decreased year over year. 60% of respondents said their organization now employs a senior information security leader.
55.8% of respondents said a dedicated or defined amount of the current budget is allocated for cybersecurity. 26.5% of respondents said there was no specific carve out for cybersecurity but money was being spent as needed or could be requested. Only 2.8% said no money is spent on cybersecurity.
HIPAA requires healthcare organizations to conduct regular risk assessments to identify potential threats to the confidentiality, integrity, and availability of protected health information. The survey revealed healthcare organizations are being proactive and are conducting risk assessments and using the results to direct their cybersecurity efforts.
45.5% said they are performing security risk assessments annually, 5.6% were conducting risk assessments every 6 months, 9% performed risk assessments once a month, and 9.6% said they performed risk assessments daily. Alarmingly, 5.1% said they do not perform risk assessments and 4.5% conducted risk assessments less frequently than once a year.
Actions Directed by Risk Assessments

Source: HIMSS
Plenty of Room for Improvement
While cybersecurity is improving, there are still multiple areas where improvements can and should be made and too little is being done to deal with the main healthcare security threats. The recent HIPAA compliance audits and penalties for HIPAA violations have prompted many healthcare organizations to concentrate on HIPAA compliance, which has been a greater priority than security.
HIMSS says compared to other industry sectors, healthcare cybersecurity programs lack maturity and that typically cybersecurity programs have only been running for five or fewer years. HIMSS suggests that even with the healthcare industry being heavily targeted by cybercriminals, “many cybersecurity professionals are still getting used to the idea that there are bad actors out there that are directly or indirectly targeting healthcare organizations.”
The main barriers for remediating and mitigating cyberattacks were a lack of appropriate personnel (52.4%) and a lack of financial resources (46.6%). Other barriers were too many application vulnerabilities (28.6%), too many endpoints (27.5%), too many new and emerging threats (27%) not enough cyber security intelligence (23.3%) and a network infrastructure that was too complex to secure (20.6%).
13.3% said they had no cybersecurity staff and 43.2% said their ratio of cybersecurity staff to IT users was greater than 1:500.
The majority of organizations are spending 6% or less of their IT budgets on cybersecurity, 16.9% of organizations had not adopted a cybersecurity framework, and 37.1% of organizations only conducted penetration tests annually. Even though the threat from within is significant, 24.2% of healthcare organizations did not have an insider threat management program and 27% said they had such a program but it was informal.
Phishing and email attacks are major concerns and are behind the majority of healthcare security breaches and OCR has also made it clear that phishing and security awareness training should be an ongoing process, yet 51.8% of healthcare organizations are still only conducting security awareness training annually. Only 32.9% said they test their employees phishing awareness with phishing simulations.
Top Healthcare Security Threats
There are many healthcare security threats, although some are perceived to pose more of a threat than others. There was little to choose between the three main threats to network and data security. Data breaches and data leakage were ranked as top healthcare security threats by 11.8% of respondents, ransomware was in second place rated as a top cybersecurity threat by 11.3% of respondents, with credential stealing malware in third place on 11%. Malicious insiders were seen as a major threat by 10.1% of respondents and wiper malware was rated as a serious threat by 10% of respodents.
When asked about future cybersecurity priorities the top areas were incident response (11.9%), risk assessment and management (11.9%), business continuity and disaster recovery (11.8%), awareness training programs (11.6%), cloud security (11.2%), website security (10.8%), physical security (10.7%), and information sharing (10.4%).
The full results of the HIMSS 2018 Cybersecurity survey can be viewed here.
The post HIMSS Survey Reveals Top Healthcare Security Threats appeared first on HIPAA Journal.