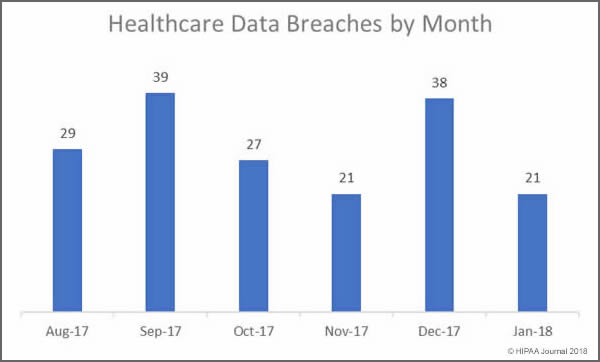
Our January 2018 Healthcare Data Breach Report details the healthcare security incidents reported to the Department of Health and Human Services’ Office for Civil Rights in January 2018. There were 21 security breaches reported to OCR in January which is a considerable improvement on the 39 incidents reported in December 2017.
Last month saw 428,643 healthcare records exposed. While there was a 46.15% drop in the number of healthcare data breaches reported in January month over month, 87,022 more records were exposed or stolen than in December. January was the third consecutive month where the number of breached records increased month over month.
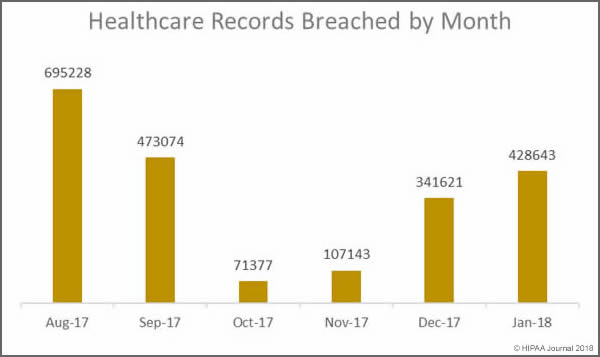
The mean breach size in January was 20,412 records – very similar to the mean breach size in December 2017 (20,487 records). However, the high mean value was due to a particularly large breach of 279,865 records reported by Oklahoma State University Center for Health Sciences. In January, the healthcare data breaches reported were far less severe than in December. In January the median breach size was 1,500 records. In December it was 15,857 records.
Largest Healthcare Data Breaches in January 2018
In January there were only four breaches reported that impacted more than 10,000 individuals, compared to nine such incidents in December 2017. Hacking incidents continue to result in the largest data breaches with five of the top six breaches the result of hacking/IT incidents, which includes hacks, malware infections and ransomware attacks.
| Covered Entity |
Entity Type |
Individuals Affected |
Type of Breach |
| Oklahoma State University Center for Health Sciences |
Healthcare Provider |
279865 |
Hacking/IT Incident |
| Onco360 and CareMed Specialty Pharmacy |
Healthcare Provider |
53173 |
Hacking/IT Incident |
| Agency for Health Care Administration |
Health Plan |
30000 |
Hacking/IT Incident |
| Decatur County General Hospital |
Healthcare Provider |
24000 |
Hacking/IT Incident |
| Charles River Medical Associates, pc |
Healthcare Provider |
9387 |
Loss |
| Westminster Ingleside King Farm Presbyterian Retirement Communities, Inc. |
Healthcare Provider |
5228 |
Hacking/IT Incident |
| RGH Enterprises, Inc. |
Healthcare Provider |
4586 |
Unauthorized Access/Disclosure |
| Gillette Medical Imaging |
Healthcare Provider |
4476 |
Unauthorized Access/Disclosure |
| Zachary E. Adkins, DDS |
Healthcare Provider |
3677 |
Theft |
| Steven Yang, D.D.S., INC. |
Healthcare Provider |
3202 |
Theft |
Main Causes of Healthcare Data Breaches in January 2018
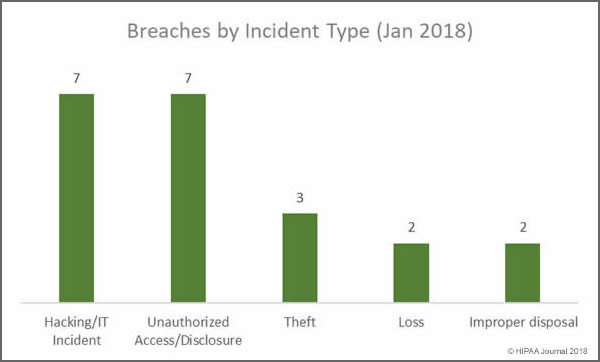
While hacking/IT incidents and unauthorized access/disclosures shared top spot in January, the biggest cause of breaches was actually errors made by employees and insider wrongdoing. Insiders were behind at least 11 of the 21 breaches reported in January. Four of the five loss/theft incidents involved portable electronic devices. Those incidents could have been avoided if encryption had been used.
Main Causes of January 2018 Data Breaches
- Hacking/IT Incidents: 7 breaches
- Unauthorized Access/Disclosure: 7 breaches
- Loss/theft of physical records and portable devices: 5 breaches
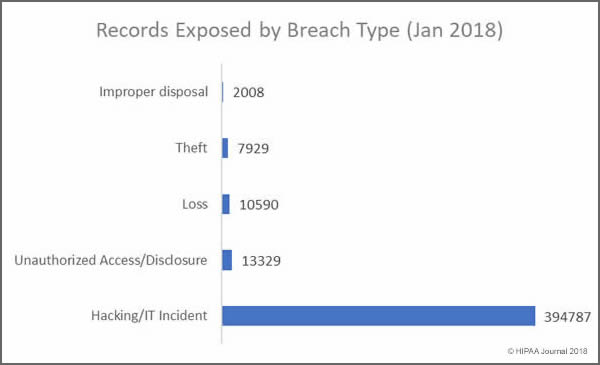
Records Exposed by Breach Type
The vast majority of individuals impacted by healthcare data breaches in January 2018 had their health data accessed or stolen in hacking/IT incidents. January saw a significant reduction in records exposed due to loss or theft – In December, incidents involving the loss or theft of devices and physical records impacted 122,921 individuals.
Main Causes of Exposed Healthcare Records in January 2018
- Hacking/IT Incidents: 394,787 healthcare records exposed in 7 security incidents
- Loss/theft of physical records and portable devices: 18,519 records exposed in 5 incidents
- Unauthorized Access/Disclosure: 13,329 healthcare records exposed in 7 incidents
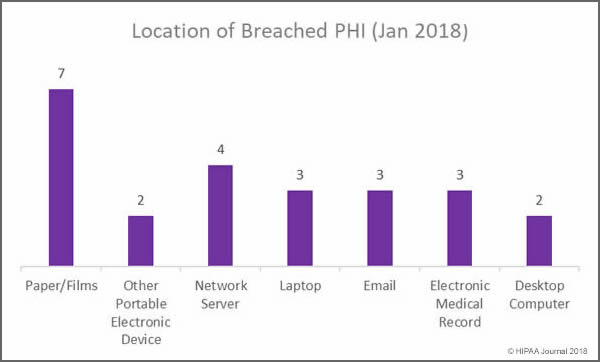
Location of Data Breaches in January 2018
Overall, more incidents were reported involving electronic copies of health data in January, but covered entities must ensure that appropriate physical security and access controls are in place to prevent unauthorized accessing and theft of paper records. Training must also be provided to staff on disposing of physical records. Two improper disposal incidents were reported in January involving physical records.
Main Locations of Exposed Healthcare Records in January 2018
- Paper/Films: 13,514 records exposed in 7 incidents: 4 unauthorized access/disclosures; 2 improper disposal incidents, and one incident involving the loss of records
- Network Servers: 310,593 healthcare records exposed in 4 hacking/IT incidents involving network servers: 1 Hack, 2 malware incidents and one incident for which the cause is unknown
- Laptop computers: 3 incidents involving laptop computers: 2 stolen devices and one hack/IT incident
- Email: Three incidents involving unauthorized access/disclosure due to phishing and two hacking incidents
- EMRs: 3 incidents involving EMRs: 2 unauthorized access incidents (Physician/nurse) and 1 hacking incident
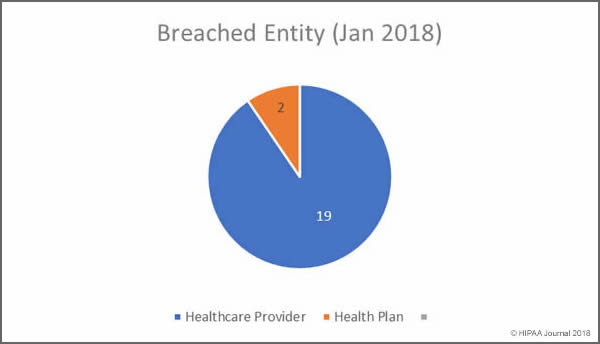
January 2018 Healthcare Data Breaches by Covered Entity
In January, no business associates of HIPAA covered entities reported data breaches, and according to the OCR breach summaries, none of the 21 security breaches had any business associate involvement. Healthcare providers were the worst affected with 19 breaches reported.
Healthcare Records Breached
- Healthcare providers: 398,009 healthcare records exposed in 19 incidents
- Health plans: 30,634 healthcare records exposed in 2 incidents
January Healthcare Data Breaches by State
In January, covered entities based in 15 states reported data breaches that impacted more than 500 individuals.
California was the worst hit state by some distance with 5 covered entities reporting breaches. Tennessee and Wyoming had two breaches apiece, with one incident reported by organizations based in Florida, Illinois, Kentucky, Massachusetts, Maryland, New Mexico, Nevada, Ohio, Oklahoma, Pennsylvania, Utah, and Washington.
Financial Penalties for HIPAA Covered Entities in January
There were no OCR HIPAA fines or settlements announced in January to resolve violations of HIPAA Rules, although the New York Attorney General did settle a case with health insurer Aetna.
Aetna was required to pay the NY AG’s office $1.15 million to resolve violations of HIPAA Rules and state laws. The violations were discovered during an investigation into a serious privacy breach experienced in July 2017. A mailing was sent to approximately 12,000 members in which details of HIV medications were visible through the clear plastic windows of the envelopes – An unauthorized disclosure of PHI. The mailing was sent on behalf of Aetna by a settlement administrator.
Further, it was alleged that Aetna provided PHI to its outside counsel, who in turn provided that information to the settlement administrator – a subcontractor – yet no business associate agreement was in place prior to that disclosure.
Aetna also settled a class action lawsuit in January over the breach. The lawsuit was filed by HIV/AIDS organizations on behalf of the victims of the breach. Aetna settled the lawsuit for $17,161,200.
That is unlikely to be the end of the fines. OCR may decide to take action over the breach and alleged HIPAA violations, and other state attorneys general have opened investigations. Aetna is also embroiled in costly legal action with its settlement administrator.
Data source for breaches: Department of Health and Human Services’ Office for Civil Rights.
The post January 2018 Healthcare Data Breach Report appeared first on HIPAA Journal.






