A recent survey by Black Book Research indicates the healthcare industry is not doing enough to tackle the threat of cyberattacks, and that cybersecurity is still not being taken seriously enough.
The survey was conducted on 323 strategic decision makers at U.S. healthcare firms in Q4, 2017. Even though the threat of cyberattacks is greater than ever, and the healthcare industry will remain the number one target for cybercriminals in 2018, only 11% of healthcare organizations plan to appoint a cybersecurity officer in 2018 to take charge of security. Currently 84% of provider organizations do not have a dedicated leader for cybersecurity.
Payer organizations are taking cybersecurity more seriously. 31% have appointed a manager for their cybersecurity programs and 44% said they would make an appointment next year. Overall, 15% of all surveyed organizations said they have a chief information security office in charge of cybersecurity.
The survey also revealed that cybersecurity best practices are not being widely adopted in the healthcare industry. Even though HIPAA calls for regular risk assessments to be conducted, 54% of respondents said risk assessments were not conducted regularly at their organization, while 39% said they do not carry out firewall penetration tests.
Further, while there have been increases in budgets, it would appear that cybersecurity is a low priority. 89% of respondents said that in 2018, budgeted IT funds were primarily being directed to business functions with provable business cases. Only a small percentage of those budgets are being allocated to cybersecurity.
In order for cybersecurity goals to be met, there needs to be C-Suite involvement, yet 92% of respondents said that cybersecurity and data breaches were not major talking points in board meetings. “Cybersecurity has to be a top-down strategic initiative as it’s far too difficult for IT security teams to achieve their goals without the board leading the charge,” said Doug Brown, Managing Partner of Black Book.
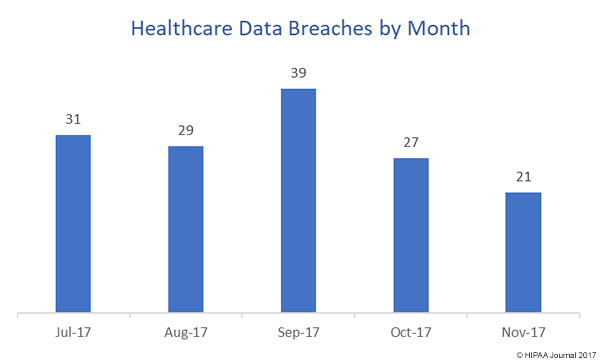
With two weeks left in December, there have been 331 healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights. The total for 2016 was 327 breaches, having increased from 270 breaches in 2015. At the current rate, the milestone of 350 breaches for the year may even be reached. There is also no indication that the year on year increases in data breaches will not continue in 2018.
“The critical role of medical facilities, combined with poor security practices and lack of resources, make them vulnerable to financially and politically motivated attacks,” said Brown.
Unless more is done to ensure cybersecurity goals are met, next year is likely to be yet another record-breaking year for healthcare data breaches.
The post Study Reveals Cybersecurity in Healthcare is Not Being Taken Seriously Enough appeared first on HIPAA Journal.