The provision of password managers for MSPs is a rapidly growing industry due to the increasing number of Managed Service Providers being targeted by cybercriminals. Indeed, in a recent “State of the Channel” survey, 95% of MSP respondents agreed that their businesses – rather than the clients they provide a managed service for – were being targeted with attacks.
It is not difficult to understand why cybercriminals are targeting MSPs. A successful “supply-chain ransomware attack” against an MSP can prevent an MSP providing a service to its clients; and even though it may only be the MSPs systems that are encrypted with ransomware, clients may be unable to operate their businesses due to the nature of the services provided by the MSP.
SMB clients are also under attack, but not to such a great extent as MSBs. 78% of respondents to the Datto “State of the Channel” survey reported attacks against SMB clients in the past two years – with adware, spyware, and viruses accounting for nearly as much disruption as ransomware. What was more concerning were the ways in which cybercriminals were accessing systems to deploy malware:
- 54% of respondents reported an attack was the result of a phishing email
- 27% of respondents said attacks were attributable to poor user practices.
- 26% of respondents attributed attacks to a lack of cybersecurity training
- 24% of respondents said weak passwords and poor credential management was to blame.
Among other responses to the survey (multiple answers were allowed) lost and stolen user credentials, a lack of funding for IT security, and a lack of executive buy-in for adopting security solutions were given as reasons for successful cyberattacks. All of these reasons could be prevented – or substantially mitigated – by implementing a password manager for MSPs.
How Password Managers for MSPs Protect MSPs
One statistic missing from Datto´s State of the Channel report is the percentage of cyberattacks attributable to MSP susceptibility compared to the percentage of cyberattacks attributable to client susceptibility. While it could be assumed clients may be easier targets due to a lack of security expertise, it is noticeable the report states “more than half [of MSPs] are now using password management and multi-factor authentication tools “
The inclusion of the word “now” in the statement is revealing inasmuch as it implies fewer than half of MSPs were using password management tools previously. Again, there is no distinction between whether password managers for MSPs are being used exclusively within the MSP businesses or if MSPs are also providing “password-management-as-a-service” to clients, but let´s start with how password managers for MSPs protect MSP businesses.
How login credentials are created, saved, and shared between teams can have an impact on any business´s online security. Research has shown that many employees use weak passwords because they are more memorable, re-use passwords across multiple sites to save having to remember multiple passwords, store login credentials in unprotected documents and spreadsheets, and share passwords via unsecure channels of communication such as email, SMS, and chat services.
When businesses implement a password manager, they can also enforce password policies requiring the use of strong, unique passwords for each account. Most commercial password managers support cross-platform, cross-browser synchronization, integration with directory services, and secure encrypted credential sharing – giving employees a safe way to exchange passwords, credit card details, and other sensitive information.
Password managers for MSPs can be used not only to protect business credentials, but clients’ credentials as well. Passwords are stored in a secure user vault and, when a user visits a website for which a password has been saved, the login credentials are auto-filled automatically. This means that if a user inadvertently clicks on a phishing email and is redirected to a fake phishing site, the login credentials will not auto-fill – alerting the user to a possible threat.
With password policies enforcing good password practices, educating users on good password hygiene, and eliminating the potential for weak passwords, the primary methods of cybercriminal access into MSP systems are eliminated. With regards to a lack of funding for IT security or executive buy-in, password managers for MSPs are inexpensive compared to the cost of recovering from a successful cyberattack and – when provided to clients as “password-management-as-a-service” – password managers for MSPs can generate more income than they cost.
Separating MSP Credentials from Client Credentials
Providing clients with password-management-as-a-service should not only be viewed as a revenue generator. By providing an MSP password management service which clients can use to access saved passwords form any location via any device, MSPs are reducing the number of calls they will receive for password resets. Furthermore, by allowing clients to apply their own password policies, MSPs are encouraging clients to develop good password practices and become more security conscious.
Nonetheless, potentially managing hundreds of passwords per user across hundreds of clients can create an administrative nightmare – notwithstanding that an MSP has to manage its own user passwords and not get them confused with client passwords. To overcome this potential issue, some password managers for MSPs – such as Bitwarden – have developed “Provider Portals” which keep the login credentials of MSPs users separate from those of its clients.
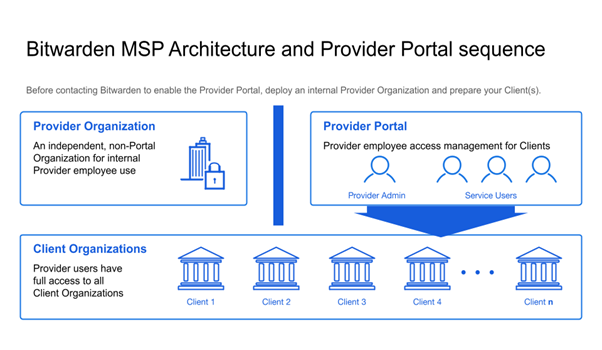
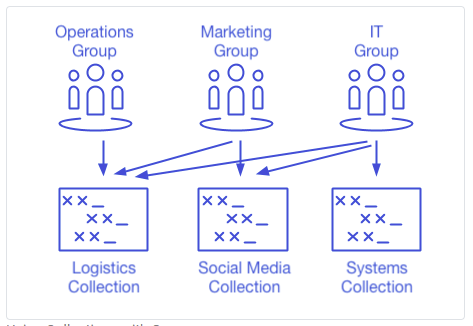 This architecture enables MSP users to access and manage clients´ credentials without the potential for mixing up credentials for different clients or confusing them with MSP credentials. Furthermore – using Bitwarden as an example – MSPs can create an “organization” for each client; and, within each organization, “collections” of shared password and corporate data can be made available to authorized “groups”. Each organization, collection, or group can have separate password policies applied if necessary.
This architecture enables MSP users to access and manage clients´ credentials without the potential for mixing up credentials for different clients or confusing them with MSP credentials. Furthermore – using Bitwarden as an example – MSPs can create an “organization” for each client; and, within each organization, “collections” of shared password and corporate data can be made available to authorized “groups”. Each organization, collection, or group can have separate password policies applied if necessary.
This structure allows for either MSP users or clients to run “per-client” health checks on credentials stored in client vaults to identify weak, re-used, or compromised passwords. MSP users and clients also have access to event logs that record when actions occur in client vaults (passwords changed, groups created, etc.). Not only do the event logs enable transparency between MSPs and clients, but they can also be integrated into SIEMs and other external systems to enhance security.
More about Bitwarden Password Managers for MSPs
Bitwarden password managers for MSPs are built on open source software that has been assessed for security by independent audits as well as being vetted by the open source community. They offer MSPs certain benefits over other enterprise password management solutions inasmuch as they synchronize with user directories via an easy-to-use Directory Connector (rather than an SCIM Bridge) that supports on-premises directories as well as cloud directories.
From a client´s perspective, Bitwarden has a user-friendly interface that simplifies password management. Clients´ employees receive a personal password vault in addition to the organization vault which encourages them to store personal credentials securely. Having access to a personal vault tends to result in better password hygiene and security awareness, which reflects in how corporate data is securely managed.
Ultimately, the provision of a password manager to clients, either as a managed service or a resale, will result in clients becoming more resilient to phishing attacks, improve user practices, enhance cybersecurity, and eliminate the use of weak passwords – reducing the client management overhead. If you would like to find out more about Bitwarden, organize a free trial of a password manager for MSPs, or discuss Bitwarden´s MSP Partner Program, visit www.bitwarden.com.
The post What are the Best Password Managers for MSPs? appeared first on HIPAA Journal.