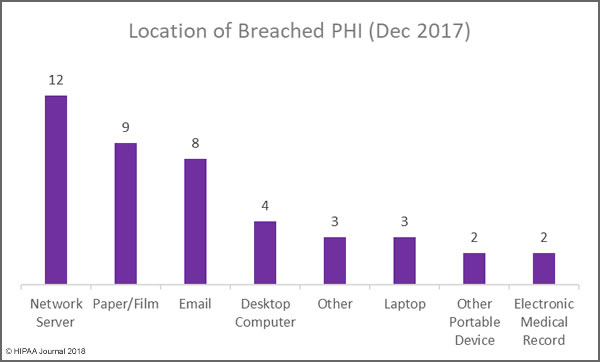
A summary and analysis of healthcare data breaches in 2017 has been published by Protenus. Data for the report is obtained from Databreaches.net, which tracks healthcare data breaches reported to OCR, the media, and other sources. The 2017 breach report gives an indication of the state of healthcare cybersecurity. So how has 2017 been?
There Were at Least 477 Healthcare Data Breaches in 2017
In some respects, 2017 was a good year. The super-massive data breaches of 2015 were not repeated, and even the large-scale breaches of 2016 were avoided. However, healthcare data breaches in 2017 occurred at rate of more than one per day.
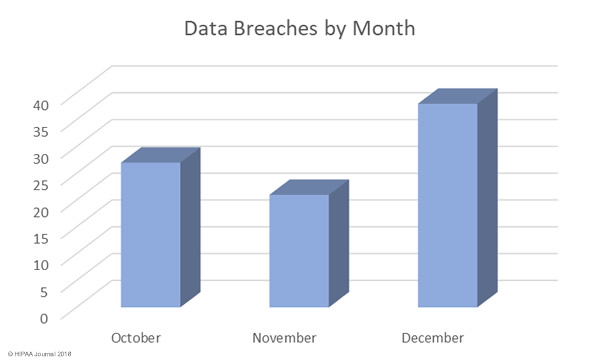
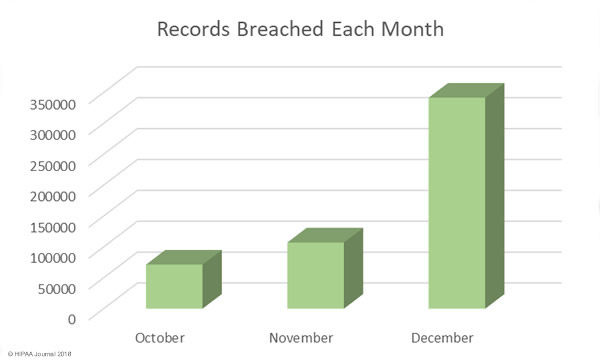
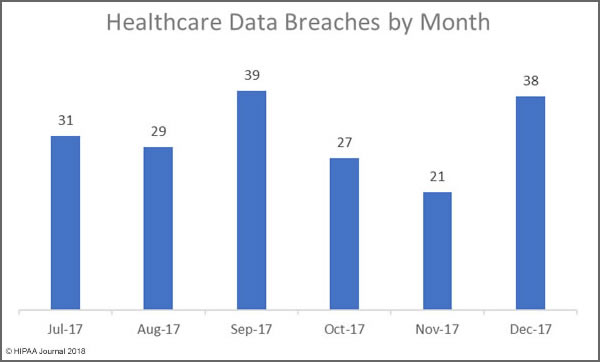
There were at least 477 healthcare data breaches in 2017 according to the report. While all those breaches have been reported via one source or another, details of the nature of all the breaches is not known. It is also unclear at this stage exactly how many healthcare records were exposed. Numbers have only been obtained for 407 of the breaches.
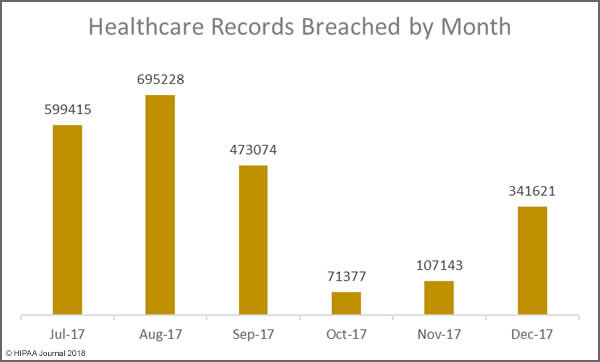
There was a slight increase (6%) in reported breaches in 2017, up from 450 incidents in 2016. However, there was a massive reduction in the number of breached records. In 2016, there were 27,314,647 records exposed/stolen. The 407 healthcare data breaches in 2017 resulted in the exposure/theft of 5,579,438 records.
In 2017, there were no million-record+ breaches. The largest security incident was a breach of 697,800 records. That breach was an insider incident where a healthcare employee downloaded PHI onto a USB drive and CD.
Main Causes of Healthcare Data Breaches in 2017
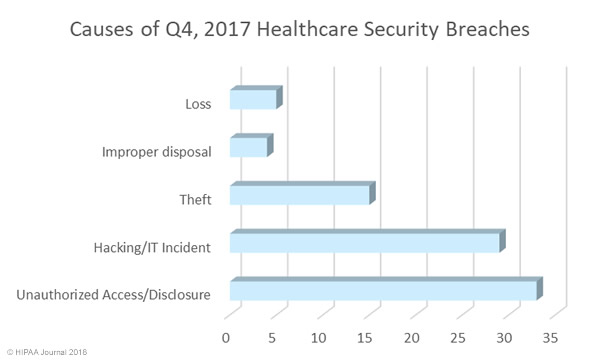
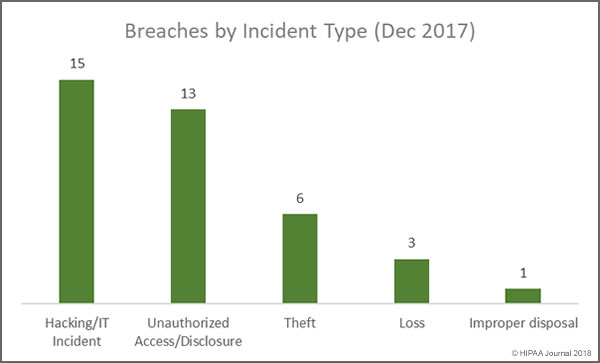
There were two causes of healthcare data breaches in 2017 that dominated the breach reports – Hacking/IT incidents and insider breaches, both of which were behind 37% of the year’s breaches. 178 incidents were attributed to hacking/IT incidents. There were 176 breaches caused by insider wrongdoing or insider errors.
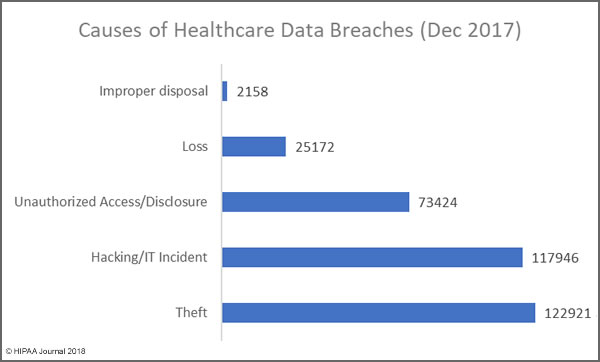
Hacking/IT incidents resulted in the exposure/theft of 3,436,742 records, although detailed data is only available for 144 of those breaches. In 2016, 86% of breaches were attributed to hacking/IT incidents. In 2016, 120 hacking incidents were reported which resulted in the exposure/theft of 23,695,069 records. The severity of hacks/insider incidents was therefore far lower in 2017, even though hacking incidents were more numerous.
What is clear from the breach reports is a major increase in malware/ransomware attacks, which were at more than twice the level seen in 2016. This could be explained, in part, by the issuing of new guidance from OCR on ransomware attacks. OCR confirmed that ransomware attacks are usually reportable security incidents under HIPAA Rules. Until the issuing of that guidance, many healthcare organizations did not report ransomware attacks unless it was clear that data had been stolen or viewed prior to or during the attack.
Insider breaches continue to plague the healthcare industry. Data is available for 143 of the 176 data breaches attributed to insiders. 1,682,836 records were exposed/stolen in those incidents. While the totals are still high, there were fewer insider incidents in 2017 than 2016, and the incidents resulted in fewer exposed records. There were 192 insider-related incidents in 2016 and those incidents resulted in the exposure/theft of 2,000,262 records.
Protenus broke down the incidents into insider error – mistakes made by healthcare employees – and insider wrongdoing, which included theft and snooping. The breakdown was 102 insider errors and 70 cases of insider wrongdoing. Four incidents could not be classified as either. One of the cases of snooping lasted for an astonishing 14 years before it was discovered.
While theft of PHI by employees is difficult to eradicate, arguably the easiest cause of healthcare data breaches to prevent is theft of electronic devices containing unencrypted PHI. If devices are encrypted, if they are stolen the incidents do not need to be reported. There has been a steady reduction in theft breaches over the past few years as encryption has been more widely adopted. Even so, 58 breaches (16%) were due to theft. Data is available for 53 of those incidents, which resulted in the exposure of 217,942 records. The cause of 47 healthcare data breaches in 2017 could not be determined from the data available.
Breached Entities and Geographic Spread
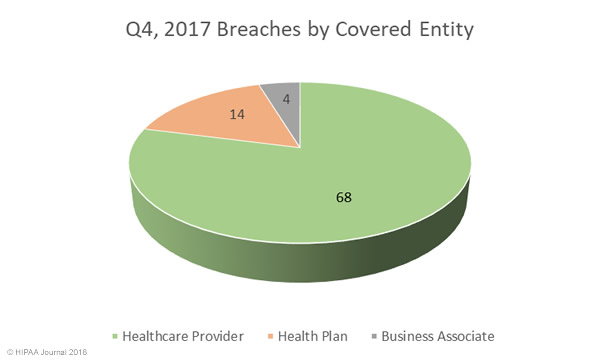
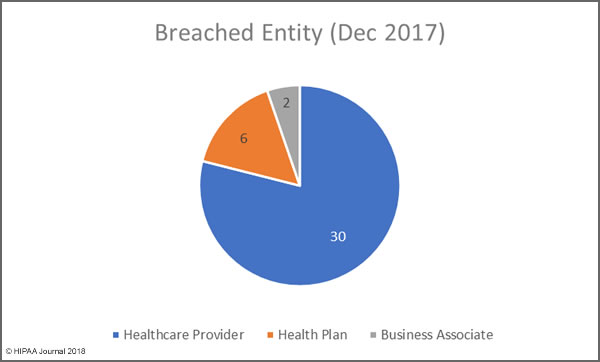
The breaches affected 379 healthcare providers (80%), 56 health plans (12%), and 4% involved other types of covered entity. Business associate reported 23 incidents (5%) although a further 66 breaches (14%) reported by covered entities had some business associate involvement. Figures are known for 53 of those breaches, which resulted in the exposure/theft of 647,198 records. Business associate breaches were lower than in 2016, as was the number of records exposed by those breaches.
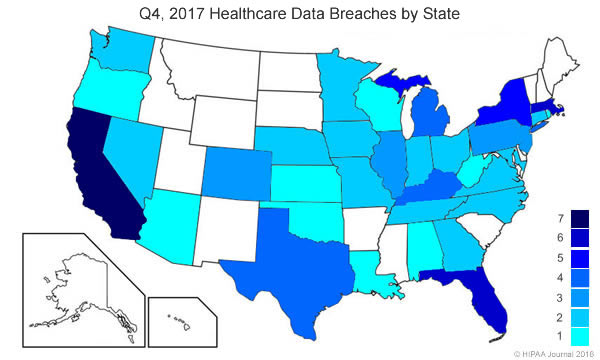
There were breaches by covered entities and business associates based in 47 states, Puerto Rico and the District of Columbia. Interestingly, three states were free from healthcare data breaches in 2017 – Hawaii, Idaho, and New Mexico. California was the worst hit with 57, followed by Texas on 40, and Florida with 31.
Slower Detection, Faster Notification
Reports of healthcare data breaches in 2017 show that in many cases, breaches are not detected until many months after the breach occurred. The average time to discover a breach, based on the 144 incidents for which the information is known, was 308 days. Last year the average time to discover a breach was 233 days. It should be noted that the data were skewed by some breaches that occurred more than a decade before discovery.
The Breach Notification Rule of the Health Insurance Portability and Accountability Act (HIPAA) allows up to 60 days from the discovery of a breach to report the incident. The average time to report a breach, based on the 220 breaches for which information was available, was 73 days. Last year the average was 344 days.
The faster reporting may have been helped by the OCR settlement with Presense Health in January for delaying breach notifications – The first HIPAA penalty solely for late breach notifications.
Overall there were several areas where the healthcare industry performed better in 2017, although the report shows there is still considerable room for improvement, especially in breach prevention, detection and reporting.
The post Analysis of Healthcare Data Breaches in 2017 appeared first on HIPAA Journal.