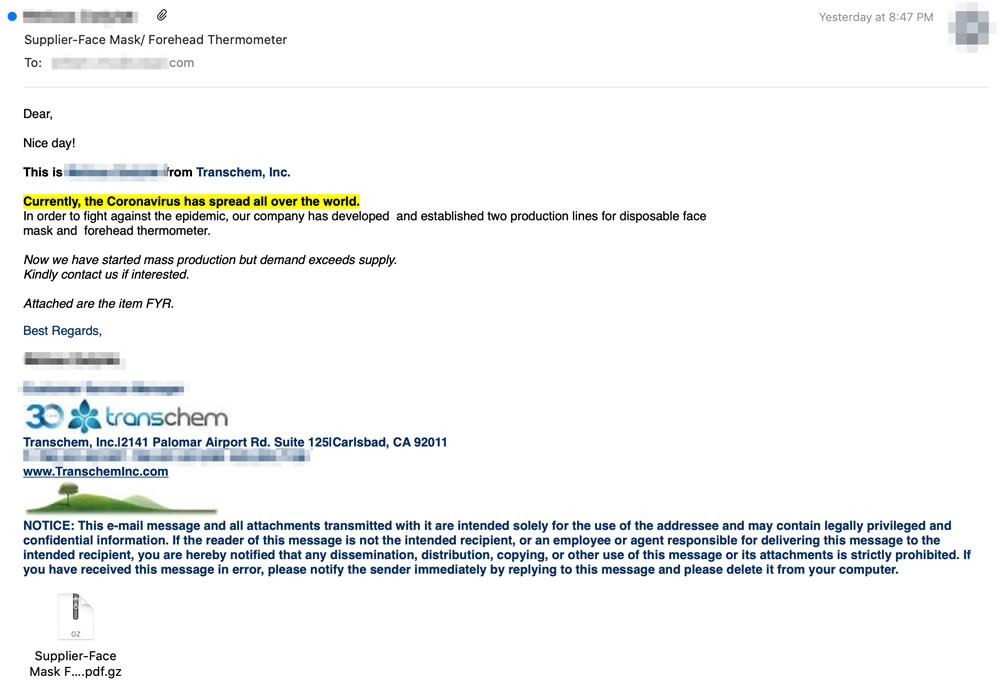
A sophisticated COVID-19 themed phishing campaign has been detected that spoofs chemical manufacturers and importers and exporters offering the recipient personal protective equipment (PPE) such as disposable face masks, forehead temperature thermometers, and other medical supplies to help in the fight against COVID-19.
The campaign was detected by researchers at Area 1 Security, who say the campaign has been active since at least May 2020 and has so far targeted thousands of inboxes. The threat actors behind the campaign regularly change their tactics, techniques, and procedures (TTPs) to evade detection by security tools, typically every 10 days.
The threat actors regularly rotate IP addresses for each new wave of phishing emails, frequently change the companies they impersonate, and revise their phishing lures. In several of the intercepted emails, in addition to spoofing a legitimate company, the names of real employees along with their email addresses and contact information are used to add legitimacy. The emails use the logos of the spoofed companies and the correct URL of the company in the signature. By including correct contact information, should any checks be performed by the recipient they may be led to believe the message is genuine.
The aim of the threat actors is to deliver the Agent Tesla Trojan. Agent Tesla is an advanced remote access Trojan (RAT) that gives the attackers access to an infected device, allowing them to perform a range of malicious actions. The RAT is capable of logging keystrokes on an infected device and stealing sensitive information from the user’s AppData folder, which is sent to the command and control server via SMTP. The malware can also steal data from web browsers, email, FTP and VPN clients.
The RAT is offered on hacking forums as malware-as-a-service and has proven popular due to the ease of conducting campaigns and the low cost of using the malware, although the researchers note that Agent Tesla can be downloaded for free via a torrent available on Russian websites. The malware includes a User interface (UI) that allows users to track infections and access data stolen by the malware.
The RAT is delivered a compressed file attachment. If the attachment is extracted, the recipient will be presented with an executable file with a double extension, that will appear to be a .pdf file. Since Windows is configured by default to hide known file extensions, the extracted file will appear to be a.pdf file when it is actually an executable file. The display name is “Supplier-Face Mask Forehead Thermometer.pdf”, but the actual file is “Supplier-Face Mask Forehead Thermometer.pdf.exe” or “Supplier-Face Mask Forehead Thermometer.pdf.gz”.
The hash is frequently changed to avoid being detected as malware by security solutions. When the hash is changed, the malware will not be detected by signature-based security solutions until definitions are updated to include the new hash.
The attackers also take advantage of flaws in the configuration of email authentication protocols such as DMARC, DKIM, and SPF when spoofing the domains of legitimate companies.
According to the researchers, the attackers are mostly using a shotgun approach, rather than spear phishing emails on a select number of targets; that said, the researchers have identified some targeted attacks on executives of Fortune 500 companies.
Since the campaign is regularly updated to evade detection by security solutions, it is important to raise awareness of the campaign with employees to prevent them inadvertently installing the malware.
The post Agent Tesla Trojan Distributed in COVID-19 Phishing Campaign Offering PPE appeared first on HIPAA Journal.