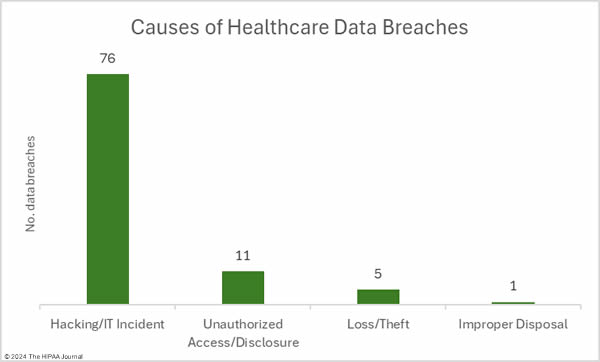
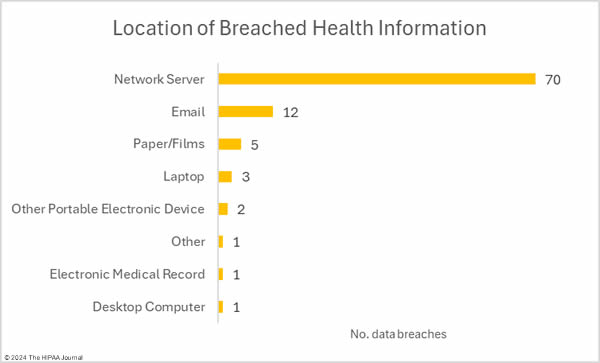
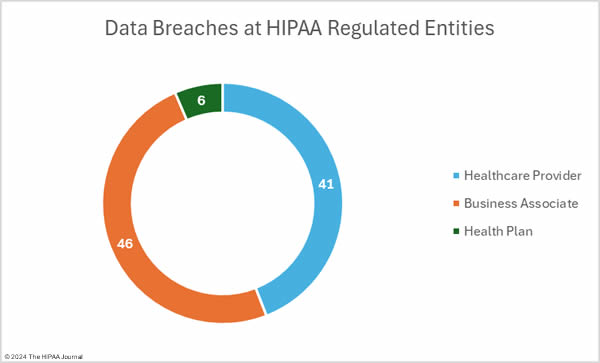
Cyberattacks have been reported by the University of Tennessee Health Science Center, SysInformation Healthcare Services (EqualizeRCM/1st Credentialing), and Jackson Medical Center. Moveable Feast has discovered the improper disposal of documents containing PHI.
University of Tennessee Health Science Center – Ransomware Attack
The University of Tennessee Health Science Center (UT-HSC) said a cyberattack on one of its vendors has resulted in the exposure and possible theft of the protected health information of 19,353 patients who received obstetrics and gynecology (OB/GYN) services at Regional One Health (ROH).
UT-HSC contracted with a company called KMJ Health Solutions which provided patient handoff software that is used to support OB/GYN patients and ensure they receive the appropriate care when they are transferred to another healthcare provider. UT-HSC was notified by KMJ on or around November 29, 2023, about a security incident discovered while investigating a server outage. KMJ erased and reformatted the server and hired a cybersecurity firm to investigate the incident but was unable to make a definitive determination about whether there had been unauthorized access. On January 18, 2024, KMJ’s hosting provider, Liquid Web, found evidence of a ransomware attack but could not determine whether the attackers downloaded a copy of the data stored in the eDocList.
The potentially affected individuals had received OB/GYN services at ROH between November 2014 and November 2023. The information potentially compromised included first and last name, medical record number, age, date of admission, allergies, service, resident assigned, parity, diagnoses, prenatal provider, laboratory results, medications, fetal or delivery details, contraception, type of infant feeding, and information regarding follow up care.
KMJ has implemented new technical safeguards including vulnerability scans, penetration testing, and configuration reviews. Due to the nature of the exposed data, UT-HSC does not believe there is any significant risk of identity theft or harm to credit; however, the affected individuals have been advised to be on the lookout for any letters, emails, or phone calls, and other communications from unknown individuals wanting to discuss any of the services received from ROH.
SysInformation Healthcare Services (EqualizeRCM/1st Credentialing) – Cyberattack
SysInformation Healthcare Services (SysInformation), an Austin, TX-based provider of revenue cycle support to medical billing companies and hospitals that does business as EqualizeRCM and 1st Credentialing, has experienced a cyberattack that caused a network outage. SysInformation said suspicious activity was detected within its network in June 2023. IT systems were secured, and third-party forensics experts were engaged to investigate the incident. The investigation revealed unauthorized access to its network between June 3, 2023, and June 18, 2023, and certain files had been exfiltrated.
SysInformation said an extensive review was conducted to determine the types of information involved and the individuals affected and notification letters were mailed to the affected individuals on April 17, 2024. The types of data involved varied from individual to individual and may have included one or more of the following: name, government identification number, date of birth, Driver’s license number, employer identification number, electronic signature, financial account information, health insurance information, medical history/treatment information, login information, mother’s maiden name, government-issued identification number, passport information, Social Security number, and/or tax identification number.
Complimentary credit monitoring services have been offered to the affected individuals, security policies and procedures have been reviewed, and additional safeguards have been implemented to prevent similar incidents in the future. The breach has been reported to regulators; however, it is not yet shown on the HHS’ Office for Civil Rights breach portal, so it is currently unclear how many individuals have been affected.
Jackson Medical Center – Cyberattack
Jackson Medical Center in Alabama has notified 509 patients about the exposure of some of their protected health information in a cyberattack that disrupted some of its IT systems. The attack was detected on February 22, 2024, and third-party forensics experts were engaged to investigate the incident and confirmed that an unauthorized third party had access to its network between February 17, 2024, and February 22, 2024. During that time, files were accessed or removed from its network.
A review of the affected files confirmed on March 8, 2024, that they contained patients’ protected health information including names and one or more of the following: contact information, dates of birth, driver’s license or state identification numbers, diagnoses, treatment information, and/or health insurance information. Notification letters have been mailed to the affected individuals and complimentary identity monitoring services have been offered to patients whose Social Security numbers, driver’s license numbers, or state identification numbers were potentially involved. Jackson Medical Center said additional safeguards and technical security measures have been implemented to further protect and monitor its systems.
Moveable Feast – Improper Disposal of Documents
Moveable Feast, a Baltimore, MD-based non-profit that provides care to individuals living with HIV/AIDS and other life-threatening illnesses, has discovered that documents containing sensitive data were disposed of incorrectly. Moveable Feast’s policies require sensitive documents to be placed in shredding bins, but some were inadvertently disposed of in regular recycling bins. The HIPAA violation was discovered when a recycling bin awaiting curb pickup was blown over, scattering its contents.
Staff collected most of the documents, but some pages could not be retrieved. The missing pages contained the information of 568 individuals such as their client number, name, gender, race, and age, and for a subset of Moveable Feast clients, the last 4 digits of their Social Security numbers. Notification letters have been sent to all affected individuals and 12 months of credit monitoring services have been made available at no cost. Staff members have also been retrained on handling sensitive information.
The post Cyberattacks Reported by UT Health Science Center; SysInformation Healthcare Services; Jackson Medical Center appeared first on HIPAA Journal.