The HIPAA Journal has compiled healthcare data breach statistics from October 2009, when the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) started publishing summaries of healthcare data breaches on its website.
 This page is regularly updated to reflect the latest healthcare data breach statistics. These statistics and graphs were last updated on October 27, 2025, and are based on data obtained from OCR up to and including October 20, 2025. Check back regularly to get the latest healthcare data breach statistics and healthcare data breach trends. You can view our 2024 healthcare data breach report here. You can also receive a free copy of our HIPAA Compliance Checklist to understand your organization’s responsibilities under HIPAA.
This page is regularly updated to reflect the latest healthcare data breach statistics. These statistics and graphs were last updated on October 27, 2025, and are based on data obtained from OCR up to and including October 20, 2025. Check back regularly to get the latest healthcare data breach statistics and healthcare data breach trends. You can view our 2024 healthcare data breach report here. You can also receive a free copy of our HIPAA Compliance Checklist to understand your organization’s responsibilities under HIPAA.
Trends In Healthcare Data Breach Statistics
Our healthcare data breach statistics clearly show there has been an upward trend in data breaches over the past 14 years, with 2021 seeing more data breaches reported than any other year since records first started being published by OCR.
Data breaches increased once again in 2022, with OCR receiving reports of 720 data breaches of 500 or more records. There was no letup in cyberattacks on healthcare organizations in 2023, which set two new records: The most reported data breaches and the most breached records. In 2023, 725 data breaches were reported to OCR, and across those breaches, more than 133 million records were exposed or impermissibly disclosed.
The healthcare data breach statistics below only include data breaches of 500 or more records that have been reported to OCR, as while HIPAA requires all data breaches to be reported regardless of size, OCR does not publish details of smaller data breaches. The breaches included in the statistics and graphs below include closed cases and breaches that are still being investigated by OCR for potential HIPAA violations.
 Between October 21, 2009, when OCR first started publishing summaries of data breach reports on its “Wall of Shame”, and December 31, 2023, 5,887 large healthcare data breaches have been reported. On January 22, 2023, the breach portal listed 857 data breaches as still under investigation. This time last year, there were 882 breaches listed as under investigation, which shows OCR has made little progress in clearing its backlog of investigations – something that is unlikely to change given the chronic lack of funding for the department.
Between October 21, 2009, when OCR first started publishing summaries of data breach reports on its “Wall of Shame”, and December 31, 2023, 5,887 large healthcare data breaches have been reported. On January 22, 2023, the breach portal listed 857 data breaches as still under investigation. This time last year, there were 882 breaches listed as under investigation, which shows OCR has made little progress in clearing its backlog of investigations – something that is unlikely to change given the chronic lack of funding for the department.
There have been notable changes over the years in the main causes of breaches. The loss/theft of healthcare records and electronic protected health information dominated the breach reports between 2009 and 2015. The move to digital record keeping, more accurate tracking of electronic devices, and more widespread adoption of data encryption have been key in reducing these data breaches. There has also been a downward trend in improper disposal incidents and unauthorized access/disclosure incidents, but data breaches continue to increase due to a massive increase in hacking incidents and ransomware attacks. In 2023, OCR reported a 239% increase in hacking-related data breaches between January 1, 2018, and September 30, 2023, and a 278% increase in ransomware attacks over the same period. In 2019, hacking accounted for 49% of all reported breaches. In 2023, 79.7% of data breaches were due to hacking incidents.
It is not just the number of data breaches that is increasing, as the breaches are becoming more severe. 2021 was a bad year for data breaches, with 45.9 million records breached, and 2022 was worse with 51.9 million records breached, but 2023 smashed all previous records with an astonishing 168 million records exposed, stolen, or otherwise impermissibly disclosed. The huge total for 2023 includes 26 data breaches of more than 1 million records and four breaches of more than 8 million records. The largest data breach of the year affected 11,270,000 individuals – the second-largest healthcare data breach of all time.
There appears to have been a slight reduction in healthcare data breaches in 2024, although it is a little too early to tell, as OCR has yet to add all reported data breaches for last year to the data breach portal. While healthcare data breaches are down, the number of compromised records has increased again from last year’s record-breaking total to more than 276 million breached records, including the largest-ever healthcare data breach – the ransomware attack at Change Healthcare, which affected an estimated 190 million individuals.
The breach data is updated at least monthly, with the previous month’s figures typically added around the 21st of each month, so check back frequently to see the emerging trends for the current year.
The Biggest U.S. Healthcare Data Breaches of All Time
| Rank | Year | Name of HIPAA-Regulated Entity | State | Entity Type | Individuals Affected | Type of Breach |
| 1 | 2024 | Change Healthcare, Inc. | MN | Business Associate | 192,700,000 | Hacking/IT Incident |
| 2 | 2015 | Anthem Inc. | IN | Health Plan | 78,800,000 | Hacking/IT Incident |
| 3 | 2023 | Welltok, Inc. | CO | Business Associate | 14,782,887 | Hacking/IT Incident |
| 4 | 2024 | Kaiser Foundation Health Plan, Inc. | CA | Health Plan | 13,400,000 | Unauthorized Access/Disclosure |
| 5 | 2019 | Optum360, LLC | MN | Business Associate | 11,500,000 | Hacking/IT Incident |
| 6 | 2023 | HCA Healthcare | TN | Business Associate | 11,270,000 | Hacking/IT Incident |
| 7 | 2015 | Premera Blue Cross | WA | Health Plan | 11,000,000 | Hacking/IT Incident |
| 8 | 2019 | Laboratory Corporation of America Holdings dba LabCorp | NC | Healthcare Provider | 10,251,784 | Hacking/IT Incident |
| 9 | 2015 | Excellus Health Plan, Inc. | NY | Health Plan | 9,358,891 | Hacking/IT Incident |
| 10 | 2023 | Perry Johnson & Associates, Inc. dba PJ&A | NV | Business Associate | 9,302,588 | Hacking/IT Incident |
| 11 | 2023 | Maximus, Inc. | VA | Business Associate | 9,179,390 | Hacking/IT Incident |
| 12 | 2023 | Managed Care of North America | GA | Business Associate | 8,627,242 | Hacking/IT Incident |
| 13 | 2014 | Community Health Systems Professional Services Corporations | TN | Healthcare Provider | 6,121,158 | Hacking/IT Incident |
| 14 | 2023 | PharMerica Corporation | KY | Healthcare Provider | 5,815,591 | Hacking/IT Incident |
| 15 | 2025 | Yale New Haven Health System | CT | Healthcare Provider | 5,556,702 | Hacking/IT Incident |
| 16 | 2024 | Ascension Health | MO | Healthcare Provider | 5,466,931 | Hacking/IT Incident |
| 17 | 2025 | Episource, LLC | CA | Business Associate | 5,418,866 | Hacking/IT Incident |
| 18 | 2011 | Science Applications International Corporation (SA | VA | Business Associate | 4,900,000 | Loss |
| 19 | 2023 | HealthEC LLC | NJ | Business Associate | 4,786,241 | Hacking/IT Incident |
| 20 | 2025 | Blue Shield of California | CA | Business Associate | 4,700,000 | Hacking/IT Incident |
| 21 | 2015 | University of California, Los Angeles Health | CA | Healthcare Provider | 4,500,000 | Hacking/IT Incident |
| 22 | 2014 | Community Health Systems Professional Services Corporation | TN | Business Associate | 4,500,000 | Theft |
| 23 | 2024 | HealthEquity, Inc. | UT | Business Associate | 4,300,000 | Hacking/IT Incident |
| 24 | 2022 | Independent Living Systems, LLC | FL | Business Associate | 4,226,508 | Hacking/IT Incident |
| 25 | 2023 | Reventics, LLC | FL | Business Associate | 4,212,823 | Hacking/IT Incident |
| 26 | 2021 | 20/20 Eye Care Network, Inc | FL | Business Associate | 4,142,440 | Hacking/IT Incident |
| 27 | 2022 | OneTouchPoint, Inc. | WI | Business Associate | 4,112,892 | Hacking/IT Incident |
| 28 | 2023 | Colorado Department of Health Care Policy & Financing | CO | Health Plan | 4,091,794 | Hacking/IT Incident |
| 29 | 2013 | Advocate Health and Hospitals Corporation, d/b/a Advocate Medical Group | IL | Healthcare Provider | 4,029,530 | Theft |
| 30 | 2024 | Concentra Health Services, Inc. | TX | Healthcare Provider | 3,998,163 | Hacking/IT Incident |
| 31 | 2016 | Banner Health | AZ | Healthcare Provider | 3,620,000 | Hacking/IT Incident |
| 32 | 2021 | Florida Healthy Kids Corporation | FL | Health Plan | 3,500,000 | Hacking/IT Incident |
| 33 | 2015 | Medical Informatics Engineering | IN | Business Associate | 3,500,000 | Hacking/IT Incident |
| 34 | 2016 | Newkirk Products, Inc. | NY | Business Associate | 3,466,120 | Hacking/IT Incident |
| 35 | 2023 | Regal Medical Group, Lakeside Medical Organization, ADOC Acquisition, & Greater Covina Medical Group | CA | Healthcare Provider | 3,388,856 | Hacking/IT Incident |
| 36 | 2020 | Trinity Health | MI | Business Associate | 3,320,726 | Hacking/IT Incident |
| 37 | 2023 | CareSource | OH | Business Associate | 3,180,537 | Hacking/IT Incident |
| 38 | 2023 | Cerebral, Inc | DE | Business Associate | 3,179,835 | Unauthorized Access/Disclosure |
| 39 | 2024 | Centers for Medicare & Medicaid Services | MD | Health Plan | 3,112,815 | Hacking/IT Incident |
| 40 | 2023 | NationsBenefits Holdings, LLC | FL | Business Associate | 3,099,502 | Hacking/IT Incident |
| 41 | 2022 | Advocate Aurora Health | WI | Healthcare Provider | 3,000,000 | Unauthorized Access/Disclosure |
| 42 | 2019 | Dominion Dental Services, Inc., Dominion National Insurance Company, and Dominion Dental Services USA, Inc. | VA | Health Plan | 2,964,778 | Hacking/IT Incident |
| 43 | 2021 | Lincare Holdings Inc. | FL | Healthcare Provider | 2,918,444 | Hacking/IT Incident |
| 44 | 2024 | Acadian Ambulance Service, Inc. | LA | Healthcare Provider | 2,896,985 | Hacking/IT Incident |
| 45 | 2022 | Connexin Software, Inc. | PA | Business Associate | 2,846,039 | Hacking/IT Incident |
| 46 | 2023 | Navvis & Company, LLC | MO | Business Associate | 2,824,726 | Hacking/IT Incident |
| 47 | 2024 | A&A Services d/b/a Sav-Rx | NE | Business Associate | 2,812,336 | Hacking/IT Incident |
| 48 | 2023 | ESO Solutions, Inc. | TX | Business Associate | 2,700,000 | Hacking/IT Incident |
| 49 | 2025 | DaVita Inc. | CO | Healthcare Provider | 2,689,826 | Hacking/IT Incident |
| 50 | 2023 | Harvard Pilgrim Health Care | MA | Health Plan | 2,662,337 | Hacking/IT Incident |
| 51 | 2018 | AccuDoc Solutions, Inc. | NC | Business Associate | 2,652,537 | Hacking/IT Incident |
| 52 | 2021 | NEC Networks, LLC d/b/a CaptureRx | TX | Business Associate | 2,600,000 | Hacking/IT Incident |
| 53 | 2021 | Smile Brands, Inc. | CA | Business Associate | 2,592,494 | Hacking/IT Incident |
| 54 | 2024 | WebTPA Employer Services, LLC (“WebTPA”) | TX | Business Associate | 2,518,533 | Hacking/IT Incident |
| 55 | 2023 | Norton Healthcare Inc. | KY | Healthcare Provider | 2,500,000 | Hacking/IT Incident |
| 56 | 2023 | Enzo Clinical Labs, Inc. | NY | Healthcare Provider | 2,470,000 | Hacking/IT Incident |
| 57 | 2023 | Florida Health Sciences Center, Inc. dba Tampa General Hospital | FL | Healthcare Provider | 2,430,920 | Hacking/IT Incident |
| 58 | 2021 | Forefront Dermatology, S.C. | WI | Healthcare Provider | 2,413,553 | Hacking/IT Incident |
| 59 | 2024 | INTEGRIS Health | OK | Healthcare Provider | 2,385,646 | Hacking/IT Incident |
| 60 | 2022 | Shields Health Care Group, Inc. | MA | Business Associate | 2,380,483 | Hacking/IT Incident |
| 61 | 2023 | Postmeds, Inc. | CA | Healthcare Provider | 2,364,359 | Hacking/IT Incident |
| 62 | 2023 | Centers for Medicare & Medicaid Services | MD | Health Plan | 2,342,357 | Hacking/IT Incident |
| 63 | 2024 | Medical Management Resource Group, L.L.C. | AZ | Business Associate | 2,264,157 | Hacking/IT Incident |
| 64 | 2016 | 21st Century Oncology | FL | Healthcare Provider | 2,213,597 | Hacking/IT Incident |
| 65 | 2023 | McLaren Health Care | MI | Healthcare Provider | 2,103,881 | Hacking/IT Incident |
| 66 | 2023 | Berry, Dunn, McNeil & Parker, LLC | ME | Business Associate | 2,068,426 | Hacking/IT Incident |
| 67 | 2014 | Xerox State Healthcare, LLC | TX | Business Associate | 2,000,000 | Unauthorized Access/Disclosure |
| 68 | 2023 | Arietis Health, LLC | FL | Business Associate | 1,975,066 | Hacking/IT Incident |
| 69 | 2023 | Great Expressions Dental Centers | MI | Healthcare Provider | 1,925,397 | Hacking/IT Incident |
| 70 | 2022 | Professional Finance Company, Inc. | CO | Business Associate | 1,918,941 | Hacking/IT Incident |
| 71 | 2025 | Anne Arundel Dermatology | MD | Healthcare Provider | 1,905,000 | Hacking/IT Incident |
| 72 | 2011 | IBM | NY | Business Associate | 1,900,000 | Unknown |
| 73 | 2022 | Apria Healthcare LLC | IN | Healthcare Provider | 1,868,831 | Hacking/IT Incident |
| 74 | 2023 | Pension Benefit Information, LLC | MN | Business Associate | 1,866,694 | Hacking/IT Incident |
| 75 | 2023 | Fred Hutchinson Cancer Center | WA | Healthcare Provider | 1,840,927 | Hacking/IT Incident |
| 76 | 2024 | Summit Pathology and Summit Pathology Laboratories, Inc. | CO | Healthcare Provider | 1,813,538 | Hacking/IT Incident |
| 77 | 2023 | Performance Health Technology | OR | Business Associate | 1,752,076 | Hacking/IT Incident |
| 78 | 2023 | NASCO | GA | Business Associate | 1,744,655 | Hacking/IT Incident |
| 79 | 2024 | OnePoint Patient Care | AZ | Healthcare Provider | 1,741,152 | Hacking/IT Incident |
| 80 | 2019 | Clinical Pathology Laboratories, Inc. | TX | Healthcare Provider | 1,733,836 | Hacking/IT Incident |
| 81 | 2020 | Dental Care Alliance, LLC | FL | Business Associate | 1,723,375 | Hacking/IT Incident |
| 82 | 2011 | GRM Information Management Services | NJ | Business Associate | 1,700,000 | Theft |
| 83 | 2022 | Baptist Medical Center | TX | Healthcare Provider | 1,608,549 | Hacking/IT Incident |
| 84 | 2019 | Inmediata Health Group | PR | Healthcare Clearing House | 1,565,338 | Unauthorized Access/Disclosure |
| 85 | 2021 | Eskenazi Health | IN | Healthcare Provider | 1,515,918 | Hacking/IT Incident |
| 86 | 2022 | Community Health Network, Inc. as an Affiliated Covered Entity | IN | Healthcare Provider | 1,500,000 | Unauthorized Access/Disclosure |
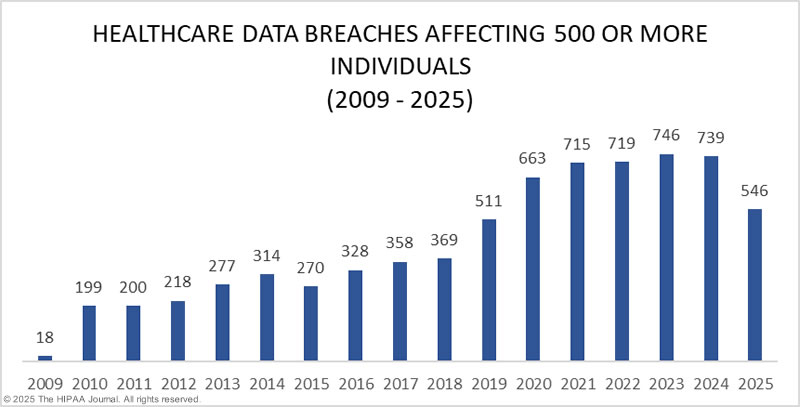
Healthcare Data Breaches by Year
Between 2009 and 2024, 6,759 healthcare data breaches of 500 or more records were reported to OCR. Those breaches have resulted in the exposure or impermissible disclosure of the protected health information of 846,962,011 individuals. That equates to more than 2.6x the population of the United States. In 2018, healthcare data breaches of 500 or more records were being reported at a rate of around 1 per day. Fast forward 5 years, and the rate has more than doubled. In 2023, an average of 1.99 healthcare data breaches of 500 or more records were reported each day, and on average, 364,571 healthcare records were breached every day. While similar numbers of healthcare data breaches were reported in 2024, the number of individuals affected by those breaches has increased significantly. In 2024, the protected health information of 276,775,457 individuals was exposed or stolen. On average, that is 758,288 records per day!
Healthcare Records Exposed by Year

There has been a general upward trend in the number of records exposed each year, with a massive increase in 2015. Until 2023, 2015 was the worst year in history for breached healthcare records, with more than 112 million records exposed or impermissibly disclosed. 2015 was particularly bad due to three massive data breaches at health plans: Anthem Inc., Premera Blue Cross, and Excellus. The Anthem breach affected 78.8 million of its members, with the Premera Blue Cross and Excellus data breaches both affecting around 10 million+ individuals. Those data breaches are small in comparison to the data breach at Change Healthcare in 2024, which affected an estimated 190 million individuals. The second-largest data breach of 2024 was reported by Kaiser Foundation Health Plan and affected 13.4 million individuals.
Average/Median Healthcare Data Breach Size by Year


Largest Healthcare Data Breaches (2009 – 2024)
The largest healthcare data breach occurred at Anthem Inc. in 2015 and involved the records of 78.8 million individuals. A data breach as large as that seemed unlikely to occur again, but this year that record has been smashed. A ransomware attack on Change Healthcare has resulted in the theft of the protected health information of 190 million individuals. You can read more about this devastating cyberattack in this article.
* PJ&A reported the data breach to OCR as affecting 8,952,212 individuals, but some of its covered entity clients reported the data breach themselves. In total, more than 13 million individuals are known to have been affected by the PJ&A data breach.
These figures are calculated based on the reporting entity. When a data breach occurs at a business associate, it may be reported by the business associate or by each affected HIPAA-covered entity. For instance, in 2022, the electronic health record provider Eye Care Leaders suffered a ransomware attack. Each covered entity reported the breach separately. The HIPAA Journal has tracked the breach reports, and at least 39 HIPAA-covered entities were affected, and the records of more than 3.09 million individuals were exposed. Similarly, a major data breach occurred at American Medical Collection Agency in 2019 that was reported by each covered entity, rather than AMCA. That breach affected more than 25 million individuals. Even when business associates of HIPAA-covered entities self-report the data breaches, some of their covered entity clients choose to report the breach themselves. As a result, business associate data breaches tend to be under-represented in analyses of healthcare data breaches.
Causes of Healthcare Data Breaches


Healthcare Hacking Incidents by Year
Our healthcare data breach statistics show hacking is now the leading cause of healthcare data breaches, although it should be noted that healthcare organizations are now much better at detecting hacking incidents than they were in 2010. The low number of hacking/IT incidents in the earlier years could be partially due to the failure to detect hacking incidents and malware infections, although it is clear that there has been a massive increase in attacks in recent years. Many of the hacking incidents between 2014 and 2018 occurred many months – and in some cases, years – before they were detected.


Unauthorized Access/Disclosures by Year
As with hacking, healthcare organizations are getting better at detecting insider breaches and reporting those breaches to the Office for Civil Rights, although as the chart below shows, the severity of these breaches has increased significantly in recent years. These incidents include employee errors, negligence, snooping on medical records, and data theft by malicious insiders. Better HIPAA and security awareness training, along with the use of technologies for monitoring access to medical records, are helping to reduce these data breaches.


Loss/Theft of PHI and Unencrypted ePHI by Year
Our healthcare data breach statistics show that HIPAA-covered entities and business associates have gotten significantly better at protecting healthcare records with administrative, physical, and technical controls such as encryption, although unencrypted laptops and other electronic devices are still being left unsecured in vehicles and locations accessible by the public. Many of these theft/loss incidents involve paper records, which can equally result in the exposure of large amounts of patient information.


Improper Disposal of PHI/ePHI by Year
HIPAA requires healthcare data, whether in physical or electronic form, to be permanently destroyed when no longer required. The improper disposal of PHI is a relatively infrequent breach cause and typically involves paper records that have not been sent for shredding or have been abandoned.


Healthcare Data Breaches by HIPAA-Regulated Entity Type
The table below shows the raw data from OCR of the data breaches by the entity reporting the breaches; however, this data does not tell the whole story, as data breaches occurring at business associates may be reported by the business associate of each affected covered entity or a combination of the two. Many online reports that provide healthcare data breach statistics fail to accurately reflect where many data breaches are occurring.
Healthcare Data Breaches: Reporting Entity (2009 – 2025)
| Year | Healthcare Provider | Health Plan | Business Associate | Healthcare Clearinghouse | Total |
| 2009 | 14 | 1 | 3 | 0 | 18 |
| 2010 | 134 | 21 | 44 | 0 | 199 |
| 2011 | 135 | 19 | 45 | 1 | 200 |
| 2012 | 154 | 23 | 40 | 1 | 218 |
| 2013 | 191 | 20 | 64 | 2 | 277 |
| 2014 | 200 | 40 | 74 | 0 | 314 |
| 2015 | 195 | 61 | 14 | 0 | 270 |
| 2016 | 256 | 50 | 22 | 0 | 328 |
| 2017 | 285 | 52 | 21 | 0 | 358 |
| 2018 | 274 | 53 | 42 | 0 | 369 |
| 2019 | 396 | 59 | 54 | 2 | 511 |
| 2020 | 514 | 73 | 74 | 2 | 663 |
| 2021 | 516 | 104 | 93 | 2 | 715 |
| 2022 | 504 | 86 | 129 | 0 | 719 |
| 2023 | 469 | 103 | 172 | 2 | 746 |
| 2024 | 541 | 77 | 118 | 3 | 739 |
| 2025 | 409 | 35 | 100 | 2 | 546 |
| Total | 5,187 | 877 | 1,109 | 17 | 7,190 |
The graphs below paint a more accurate picture of where healthcare data breaches are occurring, rather than the entities that have reported the data breaches, and clearly show the extent to which business associate data breaches have increased in recent years. In 2023, more than 93 million healthcare records were exposed or stolen in data breaches at business associates compared to 34.9 million records in breaches at healthcare providers. The charts below show data breaches by reporting entity.


These data highlight the importance of securing the supply chain, conducting due diligence on vendors before their products and services are used, and monitoring existing vendors for HIPAA Security Rule compliance and cybersecurity. In 2023, one of the biggest challenges in healthcare cybersecurity is securing the supply chain.
OCR Settlements and Fines for HIPAA Violations
The penalties for HIPAA violations can be severe. Multi-million-dollar fines are possible when violations have been allowed to persist for several years or when there is systemic non-compliance with the HIPAA Rules, making HIPAA compliance financially as well as ethically important.
The penalty structure for HIPAA violations is detailed in the infographic below. These figures are adjusted annually for inflation. The current penalty amounts can be found here.
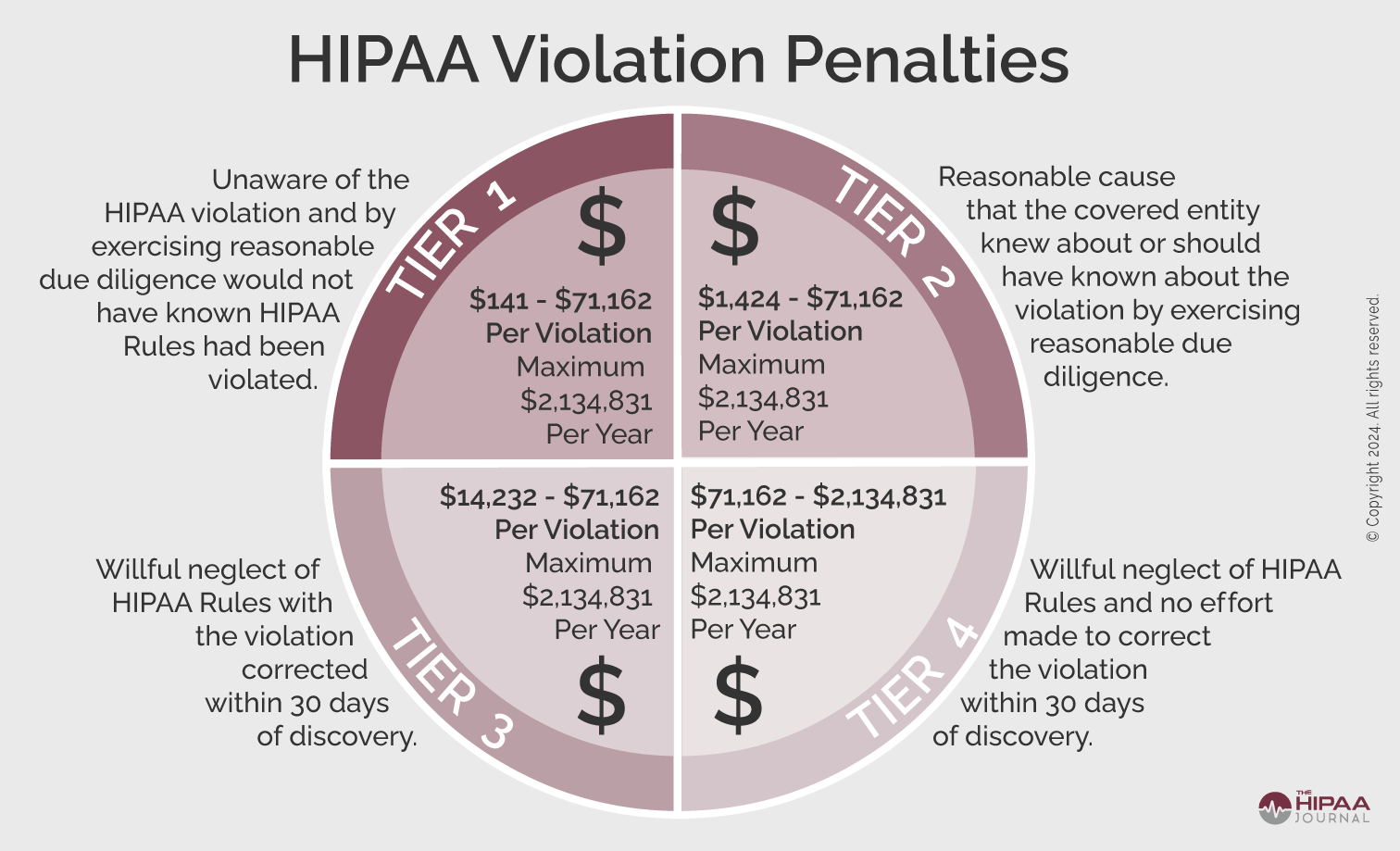
OCR Settlements and Fines Over the Years
Further information on HIPAA fines and settlements can be viewed on our HIPAA violation fines page, which details all HIPAA violation fines imposed by OCR since 2008. As the graph below shows, HIPAA enforcement activity has steadily increased over the past 14 years, with 2022 being a record year, with 22 penalties imposed. The major rise in HIPAA violation penalties in 2020 was largely due to a new enforcement initiative by OCR targeting non-compliance with the HIPAA Right of Access – the right of patients to access and obtain a copy of their healthcare data. 11 settlements were reached with healthcare providers in 2020 to resolve cases where patients were not given timely access to their medical records, and in 2021, all but two of the 14 penalties were for HIPAA Right of Access violations. From September 2019 to December 2023, 46 penalties have been imposed to resolve HIPAA Right of Access violations.
There was an increase in HIPAA enforcement activity in 2024, as while OCR only announced 16 civil monetary penalties and settlements in 2024 to resolve alleged HIPAA violations, OCR Director Melanie Fontes Rainer explained that OCR had in fact closed 22 HIPAA investigations with financial penalties, although OCR announced six of those HIPAA cases in early January 2024 before the administration change. The high level of HIPAA enforcement has continued in 2025, largely due to the new HIPAA risk analysis enforcement initiative. Under this initiative, OCR is focused on compliance with the risk analysis provision of the HIPAA Security Rule – the most commonly identified HIPAA Security Rule violation. By focusing on this aspect of Security Rule compliance, OCR is able to complete investigations more quickly, helping to reduce the large backlog of data breach cases, while also holding HIPAA-regulated entities to account for risk analysis failures. As of May 31, 2025, OCR has closed 9 investigations with financial penalties for HIPAA risk analysis failures under this enforcement initiative.

How Much Has OCR Fined HIPAA Covered Entities and Business Associates?
In addition to an increase in fines and settlements, penalty amounts increased considerably between 2015 and 2018. In 2018, the largest ever financial penalty for HIPAA violations was paid by Anthem Inc. to resolve potential violations of the HIPAA Security Rule that were discovered by OCR during the investigation of its 78.8 million record data breach in 2015. Anthem paid $16 million to settle the case. In 2020, Premera Blue Cross settled potential violations of the HIPAA Rules and paid a $6,850,000 penalty to resolve its 2015 data breach of the PHI of almost 10.5 million individuals, and in 2021, a $5,000,000 settlement was agreed upon with Excellus Health Plan to resolve HIPAA violations identified that contributed to its 2015 data breach of the PHI of almost 9.4 million individuals.
While large financial penalties are still imposed to resolve HIPAA violations, the trend has been for smaller penalties to be issued in recent years, with those penalties imposed on healthcare organizations of all sizes. It is no longer the case that smaller healthcare organizations escape HIPAA fines. In 2022, 55% of the financial penalties imposed by OCR were on small medical practices.
The fall in revenues from OCR’s enforcement activities in recent years is due to OCR reassessing the language of the HITECH Act, which called for penalties for HIPAA violations to be increased. OCR determined that the language of the HITECH Act had been misinterpreted at the time and reduced the penalty caps in three of the four penalty tiers. OCR is now petitioning Congress to increase the penalty caps to increase the deterrent effect.



It was expected that 2018 would see fewer fines for HIPAA-covered entities than in the past two years due to HHS budget cuts, but that did not prove to be the case. 2018 was a record-breaking year for HIPAA fines and settlements, beating the previous record of $23,505,300 set in 2016 by 22%. OCR received payments totaling $28,683,400 in 2018 from HIPAA-covered entities and business associates who had violated HIPAA Rules, and 2020 saw a major increase in enforcement activity with 19 settlements. The number of financial penalties was reduced in 2021; however, 2022 saw penalties increase, with 22 financial penalties announced by OCR, more than in any other year to date. There was a reduction in enforcement actions in 2023, although there was an increase in penalty amounts. OCR had been concentrating on HIPAA Right of Access violations, for which the penalties are generally relatively low, as only one HIPAA provision is typically violated. In 2023, OCR imposed more fines for HIPAA Security Rule violations, where the entity concerned violated multiple aspects of the Security Rule, hence the higher penalties.
In 2024, OCR closed 22 HIPAA investigations with financial penalties, although only 16 were announced in 2024. The remainder were announced by OCR in early January 2025, and the high level of enforcement activity has continued in 2025, with this year looking like it will be a record year for HIPAA enforcement. More detailed information on these settlements and civil monetary penalties can be found on our HIPAA Violation Cases page.
OCR Penalties for HIPAA Violations (2008 – 2025)
| Year | Covered Entity | Amount | Penalty Type |
| 2025 | Cadia Healthcare Facilities | $182,000 | Settlement |
| 2025 | BST & Co. CPAs, LLP | $175,000 | Settlement |
| 2025 | Syracuse ASC (Specialty Surgery Center of Central New York) | $250,000 | Settlement |
| 2025 | Deer Oaks – The Behavioral Health Solution | $225,000 | Settlement |
| 2025 | Comstar LLC | $75,000 | Settlement |
| 2025 | BayCare Health System | $800,000 | Settlement |
| 2025 | Vision Upright MRI | $5,000 | Settlement |
| 2025 | Comprehensive Neurology | $25,000 | Settlement |
| 2025 | PIH Health | $600,000 | Settlement |
| 2025 | Guam Memorial Hospital Authority | $25,000 | Settlement |
| 2025 | Northeast Radiology | $350,000 | Settlement |
| 2025 | Health Fitness Corporation | $227,816 | Settlement |
| 2025 | Oregon Health & Science University | $200,000 | Civil Monetary Penalty |
| 2025 | Warby Parker Inc. | $1,500,000 | Civil Monetary Penalty |
| 2025 | Northeast Surgical Group | $10,000 | Settlement |
| 2025 | South Broward Hospital District (Memorial Health System) | $60,000 | Settlement |
| 2025 | Solara Medical Supplies | $3,000,000 | Settlement |
| 2025 | USR Holdings | $337,750 | Settlement |
| 2025 | Virtual Private Network Solutions | $90,000 | Settlement |
| 2025 | Elgon Information Systems | $80,000 | Settlement |
| 2024 | Inmediata Health Group | $250,000 | Settlement |
| 2024 | Children’s Hospital Colorado Health System | $548,265 | Civil Monetary Penalty |
| 2024 | Gulf Coast Pain Consultants, dba Clearway Pain Solutions Institute | $1,190,000 | Civil Monetary Penalty |
| 2024 | Holy Redeemer Family Medicine | $35,581 | Settlement |
| 2024 | Rio Hondo Community Mental Health Center | $100,000 | Civil Monetary Penalty |
| 2024 | Bryan County Ambulance Authority | $90,000 | Settlement |
| 2024 | Plastic Surgery Associates of South Dakota | $500,000 | Settlement |
| 2024 | Gums Dental Care | $70,000 | Civil Monetary Penalty |
| 2024 | Providence Medical Institute | $240,000 | Civil Monetary Penalty |
| 2024 | Cascade Eye and Skin Centers | $250,000 | Settlement |
| 2024 | American Medical Response | $115,200 | Civil Monetary Penalty |
| 2024 | Heritage Valley Health System | $950,000 | Settlement |
| 2024 | Essex Residential Care (Hackensack Meridian Health, West Caldwell Care Center) | $100,000 | Civil Monetary Penalty |
| 2024 | Phoenix Healthcare | $35,000 | Settlement |
| 2024 | Green Ridge Behavioral Health | $40,000 | Settlement |
| 2024 | Montefiore Medical Center | $4,750,000 | Settlement |
| 2023 | Optum Medical Care of New Jersey | $160,000 | Settlement |
| 2023 | Lafourche Medical Group | $480,000 | Settlement |
| 2023 | St. Joseph’s Medical Center | $80,000 | Settlement |
| 2023 | Doctors’ Management Services | $100,000 | Settlement |
| 2023 | L.A. Care Health Plan | $1,300,000 | Settlement |
| 2023 | UnitedHealthcare | $80,000 | Settlement |
| 2023 | iHealth Solutions (dba Advantum Health) | $75,000 | Settlement |
| 2023 | Yakima Valley Memorial Hospital | $240,000 | Settlement |
| 2023 | Manasa Health Center, LLC | $30,000 | Settlement |
| 2023 | MedEvolve Inc. | $350,000 | Settlement |
| 2023 | David Mente, MA, LPC | $15,000 | Settlement |
| 2023 | Banner Health | $1,250,000 | Settlement |
| 2023 | Life Hope Labs, LLC | $16,500 | Settlement |
| 2022 | Health Specialists of Central Florida Inc | $20,000 | Settlement |
| 2022 | New Vision Dental | $23,000 | Settlement |
| 2022 | Great Expressions Dental Center of Georgia, P.C. | $80,000 | Settlement |
| 2022 | Family Dental Care, P.C. | $30,000 | Settlement |
| 2022 | B. Steven L. Hardy, D.D.S., LTD, dba Paradise Family Dental | $25,000 | Settlement |
| 2022 | New England Dermatology and Laser Center | $300,640 | Settlement |
| 2022 | ACPM Podiatry | $100,000 | Civil Monetary Penalty |
| 2022 | Memorial Hermann Health System | $240,000 | Settlement |
| 2022 | Southwest Surgical Associates | $65,000 | Settlement |
| 2022 | Hillcrest Nursing and Rehabilitation | $55,000 | Settlement |
| 2022 | MelroseWakefield Healthcare | $55,000 | Settlement |
| 2022 | Erie County Medical Center Corporation | $50,000 | Settlement |
| 2022 | Fallbrook Family Health Center | $30,000 | Settlement |
| 2022 | Associated Retina Specialists | $22,500 | Settlement |
| 2022 | Coastal Ear, Nose, and Throat | $20,000 | Settlement |
| 2022 | Lawrence Bell, Jr. D.D.S | $5,000 | Settlement |
| 2022 | Danbury Psychiatric Consultants | $3,500 | Settlement |
| 2022 | Oklahoma State University – Center for Health Sciences | $875,000 | Settlement |
| 2022 | Dr. Brockley | $30,000 | Settlement |
| 2022 | Jacob & Associates | $28,000 | Settlement |
| 2022 | Dr. U. Phillip Igbinadolor, D.M.D. & Associates, P.A. | $50,000 | Civil Monetary Penalty |
| 2022 | Northcutt Dental-Fairhope | $62,500 | Settlement |
| 2021 | Advanced Spine & Pain Management | $32,150 | Settlement |
| 2021 | Denver Retina Center | $30,000 | Settlement |
| 2021 | Dr. Robert Glaser | $100,000 | Civil Monetary Penalty |
| 2021 | Rainrock Treatment Center LLC (dba monte Nido Rainrock) | $160,000 | Settlement |
| 2021 | Wake Health Medical Group | $10,000 | Settlement |
| 2021 | Children’s Hospital & Medical Center | $80,000 | Settlement |
| 2021 | The Diabetes, Endocrinology & Lipidology Center, Inc. | $5,000 | Settlement |
| 2021 | AEON Clinical Laboratories (Peachstate) | $25,000 | Settlement |
| 2021 | Village Plastic Surgery | $30,000 | Settlement |
| 2021 | Arbour Hospital | $65,000 | Settlement |
| 2021 | Sharpe Healthcare | $70,000 | Settlement |
| 2021 | Renown Health | $75,000 | Settlement |
| 2021 | Excellus Health Plan | $5,100,000 | Settlement |
| 2021 | Banner Health | $200,000 | Settlement |
| 2020 | Peter Wrobel, M.D., P.C., dba Elite Primary Care | $36,000 | Settlement |
| 2020 | University of Cincinnati Medical Center | $65,000 | Settlement |
| 2020 | Dr. Rajendra Bhayani | $15,000 | Settlement |
| 2020 | Riverside Psychiatric Medical Group | $25,000 | Settlement |
| 2020 | City of New Haven, CT | $202,400 | Settlement |
| 2020 | Aetna | $1,000,000 | Settlement |
| 2020 | NY Spine | $100,000 | Settlement |
| 2020 | Dignity Health, dba St. Joseph’s Hospital and Medical Center | $160,000 | Settlement |
| 2020 | Premera Blue Cross | $6,850,000 | Settlement |
| 2020 | CHSPSC LLC | $2,300,000 | Settlement |
| 2020 | Athens Orthopedic Clinic PA | $1,500,000 | Settlement |
| 2020 | Housing Works, Inc. | $38,000 | Settlement |
| 2020 | All Inclusive Medical Services, Inc. | $15,000 | Settlement |
| 2020 | Beth Israel Lahey Health Behavioral Services | $70,000 | Settlement |
| 2020 | King MD | $3,500 | Settlement |
| 2020 | Wise Psychiatry, PC | $10,000 | Settlement |
| 2020 | Lifespan Health System Affiliated Covered Entity | $1,040,000 | Settlement |
| 2020 | Metropolitan Community Health Services dba Agape Health Services | $25,000 | Settlement |
| 2020 | Steven A. Porter, M.D | $100,000 | Settlement |
| 2019 | Jackson Health System | $2,154,000 | Civil Monetary Penalty |
| 2019 | Texas Department of Aging and Disability Services | $1,600,000 | Civil Monetary Penalty |
| 2019 | University of Rochester Medical Center | $3,000,000 | Settlement |
| 2019 | Touchstone Medical imaging | $3,000,000 | Settlement |
| 2019 | Sentara Hospitals | $2,175,000 | Settlement |
| 2019 | Medical Informatics Engineering | $100,000 | Settlement |
| 2019 | Korunda Medical, LLC | $85,000 | Settlement |
| 2019 | Bayfront Health St. Petersburg | $85,000 | Settlement |
| 2019 | West Georgia Ambulance | $65,000 | Settlement |
| 2019 | Elite Dental Associates | $10,000 | Settlement |
| 2018* | University of Texas MD Anderson Cancer Center | $4,348,000 | Civil Monetary Penalty |
| 2018 | Anthem Inc | $16,000,000 | Settlement |
| 2018 | Fresenius Medical Care North America | $3,500,000 | Settlement |
| 2018 | Massachusetts General Hospital | $515,000 | Settlement |
| 2018 | Brigham and Women’s Hospital | $384,000 | Settlement |
| 2018 | Boston Medical Center | $100,000 | Settlement |
| 2018 | Filefax, Inc. | $100,000 | Settlement |
| 2017 | Children’s Medical Center of Dallas | $3,200,000 | Civil Monetary Penalty |
| 2017 | Memorial Healthcare System | $5,500,000 | Settlement |
| 2017 | Cardionet | $2,500,000 | Settlement |
| 2017 | Memorial Hermann Health System | $2,400,000 | Settlement |
| 2017 | 21st Century Oncology | $2,300,000 | Settlement |
| 2017 | MAPFRE Life Insurance Company of Puerto Rico | $2,200,000 | Settlement |
| 2017 | Presense Health | $475,000 | Settlement |
| 2017 | Metro Community Provider Network | $400,000 | Settlement |
| 2017 | St. Luke’s-Roosevelt Hospital Center Inc. | $387,000 | Settlement |
| 2017 | The Center for Children’s Digestive Health | $31,000 | Settlement |
| 2016 | Lincare, Inc. | $239,800 | Civil Monetary Penalty |
| 2016 | Advocate Health Care Network | $5,550,000 | Settlement |
| 2016 | Feinstein Institute for Medical Research | $3,900,000 | Settlement |
| 2016 | University of Mississippi Medical Center | $2,750,000 | Settlement |
| 2016 | Oregon Health & Science University | $2,700,000 | Settlement |
| 2016 | New York Presbyterian Hospital | $2,200,000 | Settlement |
| 2016 | St. Joseph Health | $2,140,500 | Settlement |
| 2016 | North Memorial Health Care of Minnesota | $1,550,000 | Settlement |
| 2016 | Raleigh Orthopaedic Clinic, P.A. of North Carolina | $750,000 | Settlement |
| 2016 | University of Massachusetts Amherst (UMass) | $650,000 | Settlement |
| 2016 | Catholic Health Care Services of the Archdiocese of Philadelphia | $650,000 | Settlement |
| 2016 | Care New England Health System | $400,000 | Settlement |
| 2016 | Complete P.T., Pool & Land Physical Therapy, Inc. | $25,000 | Settlement |
| 2015 | Triple S Management Corporation | $3,500,000 | Settlement |
| 2015 | Lahey Hospital and Medical Center | $850,000 | Settlement |
| 2015 | University of Washington Medicine | $750,000 | Settlement |
| 2015 | Cancer Care Group, P.C. | $750,000 | Settlement |
| 2015 | St. Elizabeth’s Medical Center | $218,400 | Settlement |
| 2015 | Cornell Prescription Pharmacy | $125,000 | Settlement |
| 2014 | New York and Presbyterian Hospital and Columbia University | $4,800,000 | Settlement |
| 2014 | Concentra Health Services | $1,725,220 | Settlement |
| 2014 | Parkview Health System, Inc. | $800,000 | Settlement |
| 2014 | QCA Health Plan, Inc., of Arkansas | $250,000 | Settlement |
| 2014 | Skagit County, Washington | $215,000 | Settlement |
| 2014 | Anchorage Community Mental Health Services | $150,000 | Settlement |
| 2013 | WellPoint | $1,700,000 | Settlement |
| 2013 | Affinity Health Plan, Inc. | $1,215,780 | Settlement |
| 2013 | Idaho State University | $400,000 | Settlement |
| 2013 | Shasta Regional Medical Center | $275,000 | Settlement |
| 2013 | Adult & Pediatric Dermatology, P.C. | $150,000 | Settlement |
| 2012 | Alaska DHSS | $1,700,000 | Settlement |
| 2012 | Massachusetts Eye and Ear Infirmary and Massachusetts Eye and Ear Associates, Inc. | $1,500,000 | Settlement |
| 2012 | Blue Cross Blue Shield of Tennessee | $1,500,000 | Settlement |
| 2012 | Phoenix Cardiac Surgery | $100,000 | Settlement |
| 2012 | The Hospice of Northern Idaho | $50,000 | Settlement |
| 2011 | Cignet Health of Prince George’s County | $4,300,000 | Civil Monetary Penalty |
| 2011 | General Hospital Corp. & Massachusetts General Physicians Organization Inc. | $1,000,000 | Settlement |
| 2011 | University of California at Los Angeles Health System | $865,500 | Settlement |
| 2010 | Rite Aid Corporation | $1,000,000 | Settlement |
| 2010 | Management Services Organization Washington Inc. | $35,000 | Settlement |
| 2009 | CVS Pharmacy Inc. | $2,250,000 | Settlement |
| 2008 | Providence Health & Services | $100,000 | Settlement |
*In 2021, following an appeal, the civil monetary penalty imposed on the University of Texas MD Anderson Cancer Center by the HHS’ Office for Civil Rights was vacated.
State Attorneys General HIPAA Fines and Other Financial Penalties for Healthcare Organizations
State attorneys general can bring actions against HIPAA-covered entities and their business associates for violations of the HIPAA Rules. Penalties range from $100 per HIPAA violation up to a maximum of $25,000 per violation category, per year.
Only a handful of U.S. states have imposed penalties for HIPAA violations; however, that changed in 2019 when many state Attorneys General started participating in multistate actions against HIPAA-covered entities and business associates that experienced major data breaches and were found not to be in compliance with the HIPAA Rules.
The penalties detailed below have been imposed by state attorneys general for HIPAA violations and violations of state laws. It is common for penalties to be imposed solely for violations of state laws, even though there are corresponding HIPAA violations.
Attorneys General HIPAA Fines (2008 – 2025)
| Year | State | Covered Entity | Amount |
| 2024 | Indiana | Westend Dental | $350,000 |
| 2024 | New York | HealthAlliance | $1,400,000 ($850,000 suspended) |
| 2024 | New York | Albany ENT & Allergy Specialists | $1,000,000 ($500,000 suspended); $2.25M investment in cybersecurity |
| 2024 | New York, New Jersey, Connecticut | Enzo Biochem/Enzo Clinical Labs | $4,500,000 |
| 2024 | Washington | Allure Esthetic | $5,000,000 |
| 2024 | California | Adventist Health Hanford | $10,000 |
| 2024 | California | Blackbaud | $6,750,000 |
| 2024 | California | Quest Diagnostics | $5,000,000 |
| 2024 | New York | Refuah Health Center | $450,000 and an investment of $1.2 million in cybersecurity |
| 2023 | New York | New York Presbyterian Hospital | $300,000 |
| 2023 | New York | Healthplex | $400,000 |
| 2023 | Indiana | CarePointe ENT | $120,000 |
| 2023 | New York | U.S. Radiology Specialists Inc. | $450,000 |
| 2023 | Multistate (32 states and PR) | Inmediata | $1,400,000 |
| 2023 | New York | Personal Touch Holding Corp | $350,000 |
| 2023 | Multistate (49 states and DC) | Blackbaud | $49,500,000 |
| 2023 | Colorado | Broomfield Skilled Nursing and Rehabilitation Center | $60,000 ($25,000 suspended) |
| 2023 | Indiana | Schneck Medical Center | $250,000 |
| 2023 | California | Kaiser Foundation Health Plan Foundation Inc. and Kaiser Foundation Hospitals | $49,000,000 |
| 2023 | California | Kaiser Permanente | $450,000 |
| 2023 | New York | Professional Business Systems Inc. dba Practicefirst Medical Management Solutions | $550,000 |
| 2023 | Multi-state: Oregon, New Jersey, Florida, Pennsylvania | EyeMed Vision Care | $2,500,000 |
| 2023 | New York | Heidell, Pittoni, Murphy & Bach LLP | $200,000 |
| 2023 | Pennsylvania & Ohio | DNA Diagnostics Center | $400,000 |
| 2022 | Oregon & Utah | Avalon Healthcare | $200,000 |
| 2022 | Massachusetts | Aveanna Healthcare | $425,000 |
| 2022 | New York | EyeMed Vision Care | $600,000 |
| 2021 | New Jersey | Regional Cancer Care Associates (Regional Cancer Care Associates LLC, RCCA MSO LLC, and RCCA MD LLC) | $425,000 |
| 2021 | New Jersey | Regional Cancer Care Associates (Regional Cancer Care Associates LLC, RCCA MSO LLC, and RCCA MD LLC) | $425,000 |
| 2021 | New Jersey | Diamond Institute for Infertility and Menopause | $495,000 |
| 2021 | Multistate | American Medical Collection Agency | $21 million (suspended) |
| 2020 | Multistate | CHSPSC LLC | $5,000,000 |
| 2020 | Multistate | Anthem Inc. | $39.5 million |
| 2020 | California | Anthem Inc. | $8.7 million |
| 2019 | Multistate | Premera Blue Cross | $10,000,000 |
| 2019 | Multistate | Medical Informatics Engineering | $900,000 |
| 2019 | California | Aetna | $935,000 |
| 2018 | Massachusetts | McLean Hospital | $75,000 |
| 2018 | New Jersey | EmblemHealth | $100,000 |
| 2018 | New Jersey | Best Transcription Medical | $200,000 |
| 2018 | Connecticut | Aetna | $99,959 |
| 2018 | New Jersey | Aetna | $365,211.59 |
| 2018 | District of Columbia | Aetna | $175,000 |
| 2018 | Massachusetts | UMass Memorial Medical Group / UMass Memorial Medical Center | $230,000 |
| 2018 | New York | Arc of Erie County | $200,000 |
| 2018 | New Jersey | Virtua Medical Group | $417,816 |
| 2018 | New York | EmblemHealth | $575,000 |
| 2018 | New York | Aetna | $1,150,000 |
| 2017 | California | Cottage Health System | $2,000,000 |
| 2017 | Massachusetts | Multi-State Billing Services | $100,000 |
| 2017 | New Jersey | Horizon Healthcare Services Inc., | $1,100,000 |
| 2017 | Vermont | SAManage USA, Inc. | $264,000 |
| 2017 | New York | CoPilot Provider Support Services, Inc | $130,000 |
| 2015 | New York | University of Rochester Medical Center | $15,000 |
| 2015 | Connecticut | Hartford Hospital/ EMC Corporation | $90,000 |
| 2014 | Massachusetts | Women & Infants Hospital of Rhode Island | $150,000 |
| 2014 | Massachusetts | Boston Children’s Hospital | $40,000 |
| 2014 | Massachusetts | Beth Israel Deaconess Medical Center | $100,000 |
| 2013 | Massachusetts | Goldthwait Associates | $140,000 |
| 2012 | MN | Accretive Health | $2,500,000 |
| 2012 | Massachusetts | South Shore Hospital | $750,000 |
| 2011 | Vermont | Health Net Inc. | $55,000 |
| 2011 | Indiana | WellPoint Inc. | $100,000 |
| 2010 | Connecticut | Health Net Inc. | $250,000 |
Click for further information HIPAA enforcement by State Attorneys General.
Federal Trade Commission Fines and Penalties
In 2009, the Federal Trade Commission (FTC) published a new rule that required vendors of personal health records and related entities to notify consumers following a breach involving unsecured information. The FTC Health Breach Notification Rule applies only to identifying health information that is not covered by HIPAA. The Rule does not apply to HIPAA-covered entities or business associates, which have reporting requirements per the HIPAA Breach Notification Rule.
The FTC issued a policy update in 2021 stating its intention to start actively enforcing compliance. Prior to 2023, no financial penalties had been imposed for breach notification failures but that changed in February 2023.
| Entity | Company Type | Penalty Type | Amount | Reason |
| Cerebral | Mental health telehealth company | Settlement | $7.1 million ($10 million CMP, $8 million suspended. $5.1 million in refunds to customers) | Impermissible disclosure of personal and health information to third parties such as Google and Snapchat |
| Monument | Alcohol addiction treatment company | Settlement | $2.5 million (suspended) | Impermissible disclosure of personal and health information to third parties such as Google. |
| Easy Healthcare (Premom) | Fertility tracking health app provider | Settlement | $200,000 | Impermissible disclosure of personal and health information to third parties such as Google and Facebook. Failure to issue timely notifications |
| BetterHelp Inc. | Online counseling service provider | Settlement | $7,800,000 | Impermissible disclosure of personal and health information to third parties such as Google and Facebook |
| GoodRx Holdings Inc. | Telemedicine platform provider | Settlement | $1,500,000 | Failure to notify consumers about the impermissible disclosure of personal and health information to third parties such as Google and Facebook |
Healthcare Data Breach Statistics FAQs
How does the number of data breaches in the healthcare sector compare with other sectors?
The number of data breaches in the healthcare sector compares poorly with other sectors. An analysis of data breaches recorded on the Privacy Rights database between 2015 and 2022 showed that 32% of all recorded data breaches were in the healthcare sector – almost double the number recorded in the financial and manufacturing sectors.

Why are there so many more data breaches in the healthcare sector than in other sectors?
There are so many more data breaches in the healthcare sector than in other sectors because healthcare data is more valuable on the black market than any other type of data. This is because it takes longer for healthcare fraud to be discovered and stolen data can be used for longer compared to (for example) a stolen credit card which can be stopped as soon as the breach is discovered.
It is also the case that organizations in the healthcare sector have stricter breach notification requirements than in other sectors. Certain types of breaches (i.e., ransomware attacks) have to be reported even if it cannot be established data has been compromised. The increasing number of recent ransomware attacks may have influenced the healthcare data breach statistics.
Why has the average HIPAA penalty decreased since 2018 despite increases in the number of breaches and median breach size?
The average HIPAA penalty has decreased since 2018 despite increases in the number of breaches and median breach size because in recent years the Office for Civil Rights (OCR) has been running a right of access initiative to clamp down on providers who fail to provide patients with access to their PHI within the thirty days allowed.
Penalties for right of access failures are less than for high-volume data breaches, and this has resulted in a decrease in the average HIPAA penalty in recent years. However, while the average HIPAA penalty issued by OCR has decreased, penalties issued by State Attorneys General have remained constant, while it is too early to find trends in fines issued by the FTC.
If a healthcare professional discloses PHI without authorization, is this included in the healthcare data breach statistics?
If a healthcare professional discloses PHI without authorization, the disclosure is unlikely to appear in the healthcare data breach statistics because the statistics are compiled from breaches involving 500 or more records. Therefore, individual unauthorized disclosures of PHI are not included in the figures. However, if the unauthorized disclosure is investigated by OCR and found to be attributable to willful neglect, any subsequent fines will be included in the settlement statistics.
How can healthcare organizations mitigate data breaches?
Healthcare organizations can mitigate data breaches using various methods. The most effective is to encrypt protected health information to render it unusable, unreadable, or indecipherable in the event of a data breach attack. This will ensure data is not compromised and the attack will not have to be reported to the Office for Civil Rights.
Other steps include implementing two-factor authentication on privileged accounts to mitigate the consequences of credential theft, running checks on all storage volumes (cloud and on-premises) to ensure appropriate permissions are applied, checking network connections for unauthorized open ports, and eliminating Shadow IT environments developed as workarounds.
How are successful phishing attacks recorded in the HIPAA breach reports?
Successful phishing attacks are recorded in the HIPAA breach reports as Hacking/IT Incidents. However, as other cybersecurity incidents such as ransomware attacks and events attributable to malware are also categorized as Hacking/IT Incidents, it is not possible to determine how many successful phishing attacks there have been affecting more than 500 individuals.
Why doesn’t HHS fine every covered organization when a HIPAA data breach occurs?
HHS doesn’t fine every covered organization when a HIPAA data breach occurs because not all data breaches are attributable to HIPAA violations. For example, successful ransomware attacks are notifiable events even when no PHI is disclosed and when systems can be quickly restored from backups because, for a period of time, PHI was unavailable.
Why is the number of HIPAA breaches increasing despite more awareness about HIPAA compliance?
The number of HIPAA breaches is increasing despite more awareness about HIPAA compliance due to the increasing digitalization of healthcare data and the increasing sophistication of cyberattacks. While there is an argument that more awareness about HIPAA compliance is having an impact on the lower number of HIPAA breaches attributable to lost or stolen drives and devices, there is a counterargument that, because of the increase in cloud computing, fewer covered organizations are transporting unencrypted PHI on drives and devices.
How can HIPAA covered entities better secure their supply chains to prevent data breaches attributable to business associates?
HIPAA covered entities can better secure their supply chains to prevent data breaches attributable to business associates by conducting more thorough due diligence on each business associate. Many covered entities rely on “good faith assurances” rather than investigating the measures each business associate has in place to prevent data breaches, the training provided to business associate workforces, and the security of communication channels used to transmit PHI.
What is the difference between a healthcare data breach and a HIPAA data breach?
The difference between a healthcare data breach and a HIPAA data breach is that a healthcare data breach is one in which healthcare data is accessed without authorization from a healthcare provider (who may or may not be a HIPAA covered entity or business associate), while a HIPAA data breach is a breach of any Protected Health Information (which can include financial information) from any covered health plan, health care clearinghouse, or healthcare provider, or any business associate providing a service for or on behalf of a covered entity.
Therefore, not only is it the nature of the data that distinguishes a healthcare data breach from a HIPAA data breach (i.e., healthcare data vs healthcare, payment, and other data with protected status), but also the status of the organization where data was accessed without authorization (i.e., covered or non-covered healthcare provider vs HIPAA covered entity or business associate). The difference may be subtle, but it can impact the breach notification requirements, the regulatory authority, and the penalty for a data breach.
The post Healthcare Data Breach Statistics appeared first on The HIPAA Journal.