In 2023, the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) received record numbers of complaints about cybercrime with losses increasing by 22% to a record-breaking $12.5 billion, according to the 2023 FBI Internet Crime Report. ICR registered 880,418 complaints in 2023, up 10% from 2022, with phishing/spoofing the most commonly reported cybercrime with 298,878 complaints, followed by personal data breaches (55,851 complaints) and non-payment/non-delivery (50,523 complaints).
The costliest type of cybercrime was investment fraud, with losses increasing from $3.31 billion in 2022 to $4.57 billion in 2023 – a 38% increase. The second biggest cause of losses to cybercrime was business email compromise (BEC) with $2.9 billion in reported losses across 21,489 complaints, followed by tech support scams with 37,560 complaints and $1.3 billion in reported losses. IC3 received 2,825 complaints related to ransomware, including 1,193 ransomware complaints from critical infrastructure entities, up 18% from 2022. Healthcare was the worst affected sector with 249 reports about ransomware attacks, followed by critical manufacturing with 218 reported attacks, and government facilities with 156 reported attacks. Out of the 16 critical infrastructure sectors, 14 sectors had at least one member that fell victim to a ransomware attack. There was also a 74% increase in ransom payments, with $59.6 million paid to ransomware groups to recover encrypted data and prevent the sale or exposure of stolen data, up from $34.4 million in 2022.
Losses to ransomware are far higher, as many victims do not report attacks to the FBI or disclose their losses. For instance, a law enforcement operation targeting the Hive ransomware group in 2023 saw the FBI gain access to the Hive group’s infrastructure which revealed that only 20% of the group’s victims had reported the attack to the FBI. The FBI encourages victims to report attacks regardless of whether the ransom is paid. By reporting the incident, the FBI may be able to provide information on decryption, help recover stolen data, and potentially seize/recover ransom payments. Reporting attacks allows the FBI to gain insights into adversary tactics and ultimately bring the perpetrators to justice.
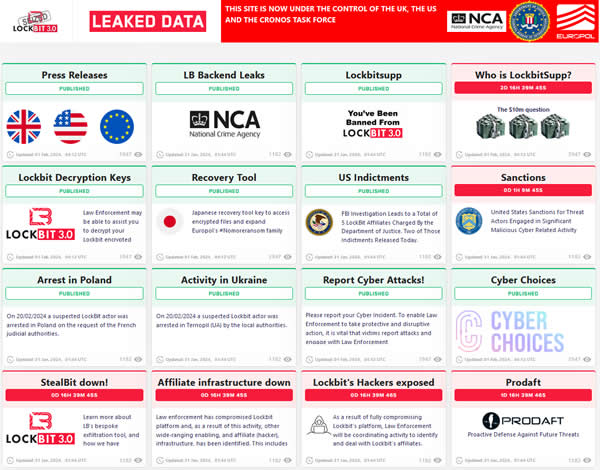
The most active ransomware group in 2023 was LockBit, which conducted 175 attacks on critical infrastructure entities, followed by ALPHV/BlackCat (100), Akira (95), Royal (63), and Black Basta (41). In February this year, a law enforcement operation disrupted the LockBit group, but the disruption was short-lived, with the group bouncing back quickly after the takedown. The ALPHV/BlackCat group survived a December 2023 takedown and reacted to the disruption by allowing its affiliates to attack previously prohibited sectors and encouraging them to attack healthcare organizations. After a ransomware attack on Change Healthcare in February 2024, the group refused to pay the affiliate, pocketed the $22 million ransom payment, and shut down its operation.
ALPHV/Blackcat was a major player in the ransomware market; however, attacks are unlikely to fall as a result of the operation shutting down. ALPHV/Blackcat is expected to rebrand and return with a new operation and even if that doesn’t happen, the affiliates that worked with the group will simply switch to an alternative ransomware-as-a-service group and continue conducting attacks. The ALPHV/Blackcat attack on Change Healthcare serves as a warning to other organizations that are considering paying the ransom. $22 million was paid to have the stolen data deleted but after being cheated out of their share of the ransom, the affiliate behind the attack retained the stolen data. Ransomware gangs are continuing to adjust their tactics to increase the probability of their victims paying the ransom. The FBI has identified emerging ransomware trends such as the use of multiple ransomware strains against the same victim and data destruction tactics to pressure victims into negotiating and paying the ransom.
The post FBI Data Shows Ransomware Attack Surge as Cybercrime Losses Reach $12.5 Billion appeared first on HIPAA Journal.