A recent study conducted by the Ponemon Institute on behalf of IBM Security has revealed the hidden cost of data breaches, and for the first time, the cost of mitigating 1 million-record+ data breaches.
The study provides insights into the costs of resolving data breaches and the full financial impact on organizations’ bottom lines. For the global study, 477 organizations were recruited and more than 2,200 individuals were interviewed and asked about the data breaches experienced at their organizations and the associated costs. The breach costs were calculated using the activity-based costing (ABC) methodology. The average number of records exposed or stolen in the breaches assessed in the study was 24,615 and 31,465 in the United States.
Last year, the Annual Cost of a Data Breach Study by the Ponemon Institute/IBM Security revealed the cost of breaches had fallen year over year to $3.62 million. The 2018 study, conducted between February 2017 and April 2018, showed data breach costs have risen once again.
The average cost of a data breach is now $3.86 million – An annual increase of 6.4%. The per capita cost of a data breach has risen by 4.8%, from $141 per record in 2017 to $148 per record in 2018.
Data breaches are costlier to resolve in the United States, where the average cost was $7.91 million. The cost of a data breach also varies considerably between industry sectors. The highest data breach resolution costs are for healthcare data breaches, which typically cost an average of $408 per record. This is considerably higher than financial services data breaches in second place, which cost an average of $206 per record. The lowest costs were in the public sector, with costs of $75 per record.
The type of breach has a bearing on the cost. Cyberattacks by malicious insiders and criminals cost an average of $157 per record, system glitches cost an average of $131 per record to resolve, while breaches caused by human error cost an average of $128 to resolve.
The mean time to identify a breach was 197 days and the mean time to contain a breach was 69 days. The time taken to identify and contain breaches both increased in the past year, which has been attributed to an increase in the severity of cyberattacks in this year’s sample.
Suffering one breach is bad enough, although many companies experience multiple breaches. IBM determined that companies that experience a data breach have a 27.9% chance of experiencing a second material breach within two years.
The Cost of Mega Data Breaches
For the first time, Ponemon/IBM analyzed the costs of mega data breaches, which are data breaches that have resulted in the theft or exposure of more than 1 million records. The number of mega data breaches experienced has nearly doubled in the past five years from 9 in 2013 to 16 in 2017.
The average time to detect and contain these mega data breaches was 365 days – almost 100 days longer than smaller data breaches which took an average of 266 days to detect and contain.
These mega data breaches can prove to be incredibly costly to resolve. The average cost of a mega data breach involving 1 million records is $40 million. That figure rises to an average of $350 million for a breach involving the exposure/theft of 50 million records. The biggest cost of these mega data breaches is loss of customers, typically costing $118 million for a 50-million record breach.
For the study, the costs of breach mitigation were divide into four areas; Detection and escalation, notification, post data breach response, and lost business cost. The costs for mega data breaches are detailed in the table below:
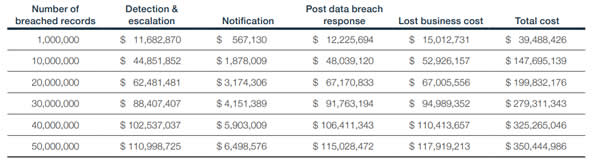
Source: IBM Security
Factors that Affect the Cost of a Data Breach
As with previous studies, Ponemon/IBM identified several factors that can have an impact on the cost of data breaches.
“Knowing where the costs lie, and how to reduce them, can help companies invest their resources more strategically and lower the huge financial risks at stake,” said Wendi Whitmore, Global Lead for IBM X-Force Incident Response and Intelligence Services (IRIS).
The time taken to identify and contain a breach has a significant bearing on cost. When companies can contain a breach within 30 days they typically save around $1 million in breach resolution costs. Companies that identified and contained a breach within 100 days spent around $1 million less than those that took longer than 100 days.
The most important factor affecting the cost of a data breach is having an incident response team in place, which reduces the breach cost by an average of $14 per compromised record. In second place is the widespread use of encryption, which reduces the cost of a data breach by $13 per record.
Business continuity management reduced the per capita cost by $9.3 as did employee training. Participation in threat sharing reduced the per capita cost by $8.7 and use of an artificial intelligence cybersecurity platform reduced the cost by $8.2.
One of the biggest costs following a data breach is loss of customers. All businesses experience churn following a breach, although steps can be taken to reduce churn. Organizations that implement programs to preserve trust and loyalty before a breach experience lower churn rates, as do companies that have a chief Privacy Office (CPO) or Chief Information Security Officer (CISO) to direct initiatives to improve customer trust in the guardianship of personal information. When businesses offer identify theft protection and credit monitoring services to breach victims, churn rate is reduced.
Companies that lost 1% of their customers as a result of a breach had an average total cost of $2.8 million, whereas a loss of 4% or more customers saw breach costs rise to an average of $6 million – a difference of $3.2 million.
When companies employ security automation the cost of data breaches falls to $2.88 million per breach, although without any security automation the average breach cost is $4.43 million – a difference of $1.55 million per breach.
The main factors that increase the cost of a data breach are third-party involvement, which increases the cost by $13.4 per record. If a company is experiencing a major cloud migration at the time of the breach the cost increases by $11.9 per record. Compliance failures also increase the breach cost by $11.9 per record.
Extensive use of mobile platforms increases the breach cost by $10 per record while companies that extensively use IoT devices add $5.4 per record to data breach costs.
While breach victims need to be notified as soon as possible, rushing to issue breach notifications before all the facts have been obtained increases the cost of the data breach by $4.9 per record.
The 2018 Cost of a Data Breach Study can be viewed on this link.
The post Healthcare Data Breach Costs Highest of Any Industry at $408 Per Record appeared first on HIPAA Journal.