Identity and access management in healthcare is a best practice for ensuring employees, vendors, contractors, and subcontractors are provided with appropriate access to the technology resources and data they need to perform their required duties and policies, procedures, and technology are in place to prevent unauthorized individuals from accessing resources and sensitive data.
Identity and access management consists of administrative, technical, and physical safeguards to keep resources and data locked down, with access to resources and data granted based on job role, authority, and responsibility. Identity and access management, in short, is about providing the right people with access to the right resources and data, at the right time, for the right reasons, while preventing unauthorized access at all times.
For a business with a small staff and few third-party vendors, identity and access management is straightforward. With few individuals requiring access to systems and data, ensuring everyone has access to the systems and data they need and nothing more is a relatively simple process. In healthcare, identity and access management is much more complicated. Access must be granted to a wide range of devices, including desktops, laptops, smartphones, routers, controllers, and a wide range of medical devices. Healthcare organizations typically use a wide variety of vendors, all of whom require access to systems and data, and there is often a high staff turnover, making it difficult to onboard and offboard in a timely manner.
To add to the problem, hackers are actively targeting healthcare organizations due to the value of the data they hold. Healthcare organizations are also heavily reliant on data and IT systems to support healthcare operations and ensure patient safety, making the sector an ideal target for ransomware gangs. The extent to which these attacks are succeeding highlights the difficulty healthcare organizations have with securing their systems and preventing unauthorized access.
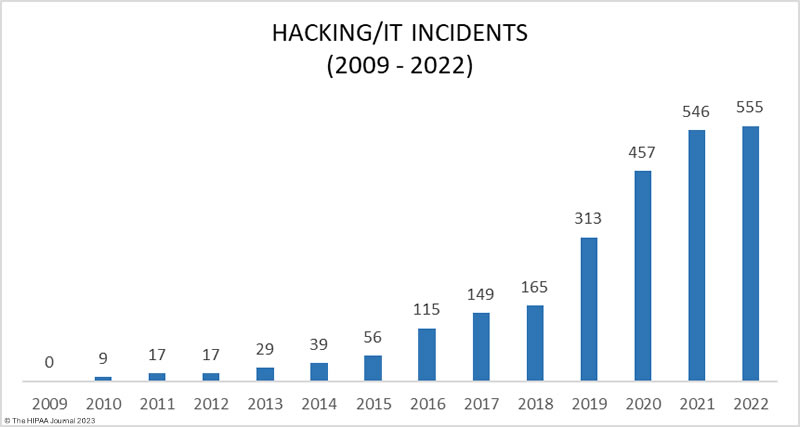
The increase in data breaches due to hacking. Data Source: HHS’ OCR Breach Portal.
Overview of Identity and Access Management
Identity and access management covers five key areas: Policy, identity management, access management, security, and monitoring. An identity and access management policy is required which determines who has access to systems and data and who has the authority to alter the functionality of IT systems. The policy must also cover onboarding and offboarding employees, vendors, and applications, and the actions that must be logged and monitored.
Identity management is a set of processes for establishing the identity of a person or device when they first make contact and for any subsequent interactions. Access management involves authentication and dictates the actions that a user is permitted to perform, with security controls implemented to prevent unauthorized access. Finally, logging is required to record system activity and data interactions to allow investigations of unauthorized activity, with logs routinely monitored and alerts generated and investigated in response to anomalous behavior.
Principles of Identity and Access Management in Healthcare
There are five key principles of identity and access management: Identification, authentication, authorization, access governance, and logging/monitoring of access and user activity.
Identification
All users – employees, vendors, contractors & subcontractors – and devices and applications that require access to systems and data must be identified and their true identities established. Identification is concerned with establishing the digital identity of a user, device, or system, which is usually achieved with a unique username/IP address.
Authentication
When a user or device has been identified, it is necessary to authenticate to prove that the user or device is what it claims to be. This is commonly achieved with a unique password associated with the username or device. Since usernames and passwords can be guessed or obtained, additional forms of authentication are required.
Authorization
Once the identity of a user has been established and authentication has occurred, they will be provided with conditional access to systems and data. Each user and device will need to be authorized to perform certain actions, access data, or administer the system, with authorization based on the principle of least privilege. Permissions should be set to the minimum necessary level required by that user to perform their duties.
Access Governance
Access governance relates to the policies and procedures for assigning, managing, and revoking access and ensuring the correct permissions are set for each user, device, or application, with users managed through a central user repository.
Logging and Monitoring
Logs of access and system activity must be generated and monitored regularly to identify unauthorized access and anomalous behavior that could indicate compromise or unauthorized access.
Common Identity and Access Weaknesses in Healthcare
Malicious actors view the healthcare industry as an easy target and commonly exploit identity and access weaknesses to gain a foothold in healthcare networks, move laterally, steal data, and conduct highly damaging attacks that severely disrupt operations and put patient safety at risk. While many sectors face similar challenges with identity and access management, a combination of factors makes effective management particularly challenging in healthcare, and vulnerabilities are commonly introduced that can be easily exploited. Across the healthcare sector, there are common weaknesses that are frequently exploited by malicious insiders and cyber threat actors, the most common of which are highlighted below.
Poor identity and access management
There is a lack of assurance that an individual or entity that seeks access is who they claim to be at many healthcare organizations. In healthcare, employees, contractors, and others require access to networks, applications, and data, there are regular changes to roles and responsibilities, and often a high staff turnover, which makes identity and access management a significant challenge, and all too often there is a lack of monitoring resulting in compromises and unauthorized access going undetected.
Role-based access control (RBAC) is commonly used by healthcare organizations as it is easier to manage access rights when users are bundled together based on their roles. This reduces the number of access policies and makes management easier since different roles require access to similar resources; however, this approach can result in users being given access to resources that do not need, with controls far less stringent than they need to be. This is especially important regarding access to PHI. Each year, many snooping incidents are reported where employees have been able to access patient records when there is no legitimate work reason for the access, with investigations revealing unauthorized access has been occurring for months or years.
Healthcare organizations need to keep on top of access rights and ensure that permissions are appropriate to roles and responsibilities, with strong identity and access management, especially for privileged accounts. Access controls should be implemented based on the principle of least privilege and there should be consistent implementation of policies across the entire organization, with regular audits conducted to ensure employees and third-party vendors have the correct access rights. The failure to terminate access promptly when contracts end or employees change roles or find new employment puts healthcare data and systems at risk.
The annual HIMSS healthcare cybersecurity surveys have shown that a large percentage of healthcare organizations are not implementing identity and access management across the organization, resulting in security vulnerabilities that can easily be exploited to gain access to systems and data. Identity and access management (IAM) software eliminates the complexity of identity and access management and allows controls to be set to ensure secure access is granted to employees and devices while making it difficult for unauthorized individuals to gain access to sensitive resources.
Slow Migration to Zero Trust
Strong identity and access management is necessary to restrict access to systems and data; however, healthcare organizations should be working toward implementing a zero-trust security framework. The traditional security approach is based on protecting the perimeter, essentially trusting anyone or anything that is inside that perimeter; however, the increase in the use of cloud infrastructure means there is no longer a clearly defined perimeter to protect. A zero-trust approach assumes that the network has been compromised, and ensures that if there is a security breach, an attacker does not have free rein over everything inside the network perimeter. Zero trust involves a constant process of authentication, authorization, and validation before access is granted to applications and data. There is no doubt that zero trust is the future of healthcare security and can prevent malicious actors from gaining access to healthcare networks and data and limit the harm that can be caused when attacks succeed; however, adoption of zero trust has been slow in the healthcare industry.
Poor password practices
HIPAA-covered entities should do more than comply with HIPAA password requirements, which only call for HIPAA-regulated entities to “implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed,” along with procedures for monitoring login attempts, and procedures for creating, changing, and safeguarding passwords.
Many healthcare data breaches result from the failure of users to set strong, unique passwords for their accounts, password reuse across multiple platforms, and password sharing. User-generated passwords can often be brute forced with ease, password reuse exposes organizations to credential stuffing attacks, and password sharing violates HIPAA as it is not possible to track user activity.
Robust password policies should be set and enforced, but shortcuts can easily be taken by employees. One solution is to use a password manager, which solves the problem of creating strong passwords and employees having to remember them. Password managers have a secure password generator that can be used to generate truly random strings of characters that are resistant to brute force attacks and stores them securely in an encrypted vault.
One authentication solution that should be considered is single sign-on (SSO), which allows access to be carefully controlled without disrupting workflows, while helping to eliminate some of the security weaknesses associated with passwords. Rather than having to log in to multiple systems, each of which requires a different login, the user authenticates once, and all subsequent logins occur using a security token or a physical device. SSO solutions also offer centralized access logs that can help with monitoring for unauthorized access.
Reliance on single-factor rather than multifactor authentication
It is telling that one of the most commonly cited improvements to security following a healthcare data breach is the implementation of multi-factor authentication across the organization when the proactive implementation of MFA could have prevented the data breach. Multifactor authentication is one of the most important defenses against phishing, which continues to be a leading cause of healthcare data breaches, yet multifactor adoption in healthcare lags other sectors.
Multifactor authentication requires additional means of authentication other than a password for verifying a user’s identity. The authentication process requires something a person knows (a password) in combination with something a person has (a physical device or token) or something inherent to the user (a fingerprint, face recognition, or biometric data). While any type of multifactor authentication is better than single-factor authentication, an increasing number of phishing attacks are exploiting weak multifactor authentication controls. The gold standard is phishing-resistant MFA, such as FIDO/WebAuthn authentication. Regardless of which method is used, multifactor authentication needs to be implemented consistently across the entire organization.
Failure to secure third-party vendor access
Hackers may attack healthcare organizations directly but it is now increasingly common for malicious actors to exploit security weaknesses to gain access to vendor networks, through which they can abuse remote access tools to gain access to healthcare organizations’ networks. Supply chain attacks allow access to be gained to multiple healthcare networks via an attack on a single vendor. While it is important to restrict employee access using the principle of least privilege, the same applies to vendor access. Vendor access needs to be closely monitored, yet around half of healthcare organizations do not routinely monitor vendor access.
Insufficient logging and monitoring
Many healthcare organizations discover their systems have been breached several weeks or months after the network has been compromised, with the intrusion only detected when ransomware is used to encrypt files. Log management and intrusion detection solutions identify anomalies that could indicate a system compromise, and generate alerts when suspicious activity is detected, allowing investigations to be conducted to identify unauthorized access quickly, thus minimizing the harm that is caused.
I have already touched on insider breaches from an access rights perspective, which can be minimized with the right access policies and effective user management; however, one of the biggest failures comes from a lack of logging and monitoring of access. There have been insider breaches where employees have snooped on patient records for years before the unauthorized access is detected due to access logs not being routinely monitored. The key to effective monitoring is automation. IT solutions should be used that constantly monitor for unauthorized access, can distinguish between proper and improper access to ePHI, and generate alerts when suspicious activity is detected.
HIPAA and Identity and Access Management
Effective identity and access management is a fundamental part of healthcare cybersecurity and compliance with the HIPAA Rules. The HIPAA Privacy Rule – 45 C.F.R. § 164.514(h) – has a standard concerning the verification of identity and the authority of a person to have access to PHI, while the technical safeguards of the HIPAA Security Rule – 45 CFR 164.312(d) – require regulated entities to implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed. The Security Rule also has a standard for access control and tracking user activity – 45 C.F.R § 164.312(a)(1), and 45 C.F.R § 164.312(b) requires audit controls for recording and monitoring activity in information systems.
The HIPAA Security Rule does not stipulate specific authentication solutions that should be used for identity and access management; instead, the measures should be informed by the entity’s risk analysis and should sufficiently reduce risks to the confidentiality, integrity, and availability of ePHI. The HHS’ Office for Civil Rights drew attention to authentication in its June 2023 Cybersecurity Newsletter and pointed out that authentication measures should reflect the level of risk. “Different touchpoints for authentication throughout a regulated entity’s organization may present different levels of risk, thus requiring the implementation of authentication solutions appropriate to sufficiently reduce risk at those various touchpoints,” explained OCR. “For example, remote access to a regulated entity’s information systems and ePHI may present a greater risk than access in person, thus stronger authentication processes (e.g., multi-factor authentication) may be necessary when permitting or expanding remote access to reduce such risks sufficiently.” OCR suggests following the advice of CISA, and implementing, as a minimum, multifactor authentication solutions on Internet-facing systems, such as email, remote desktop applications, and Virtual Private Networks (VPNs).
Conclusion
Healthcare cybersecurity starts with effective identity and access management. HIPAA-regulated entities should ensure they develop, implement, and maintain effective identity and access policies, implement strong authentication processes, and take steps to address password weaknesses, taking advantage of the latest cybersecurity solutions to automate authentication and access policies as far as possible. Proper access governance is essential, including monitoring logs to identify potential compromises and unauthorized access to PHI by insiders.
With so many competing priorities, investment in cybersecurity often falls far short of what is required; however, with hacking incidents continuing to increase and ransomware attacks impacting patient care, cybersecurity is at last being viewed as not just an IT issue, but a critical patient safety issue that warrants appropriate investment.
Steve Alder, Editor-in-Chief, HIPAA Journal
The post Editorial: The Importance of Identity and Access Management (IAM) in Healthcare appeared first on HIPAA Journal.
