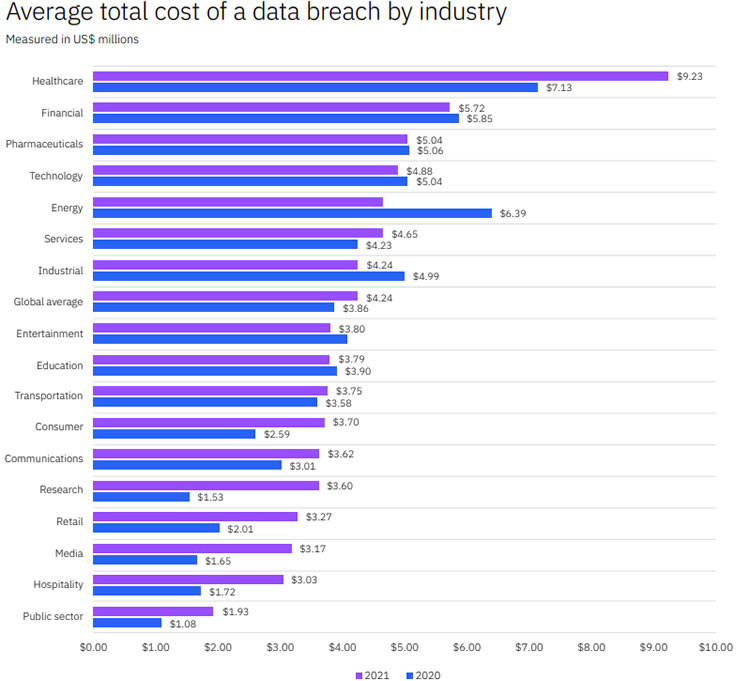
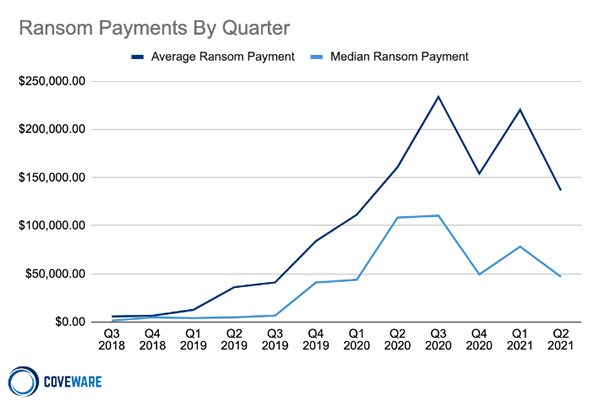
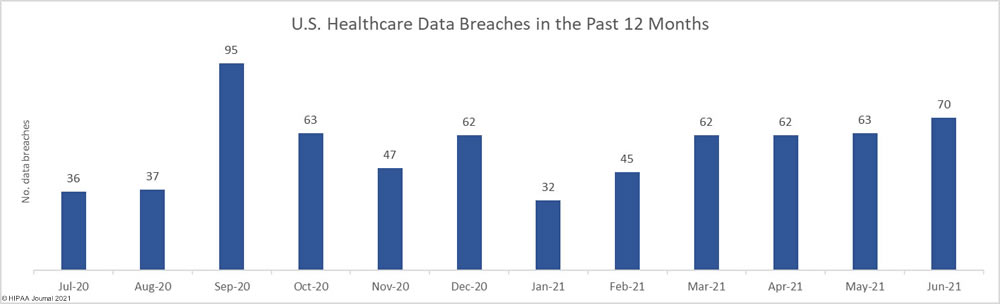
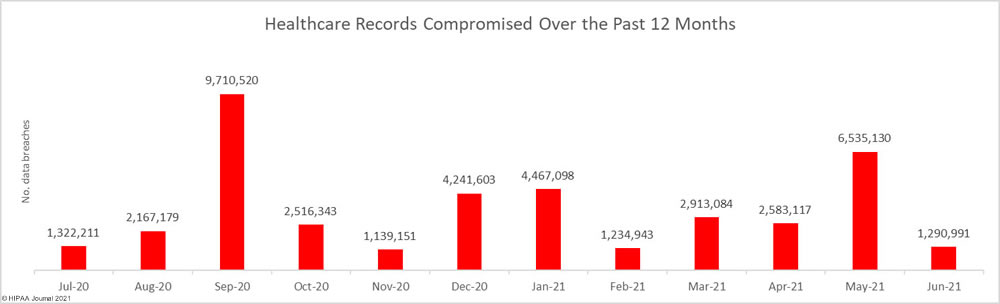
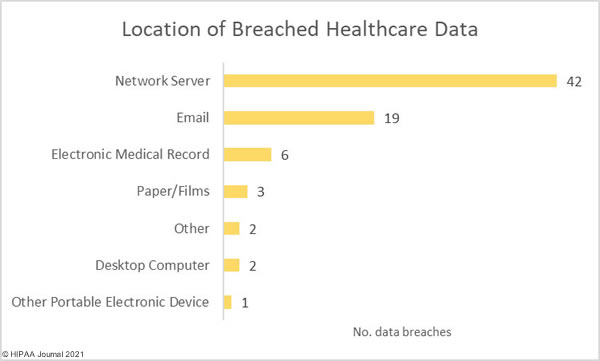
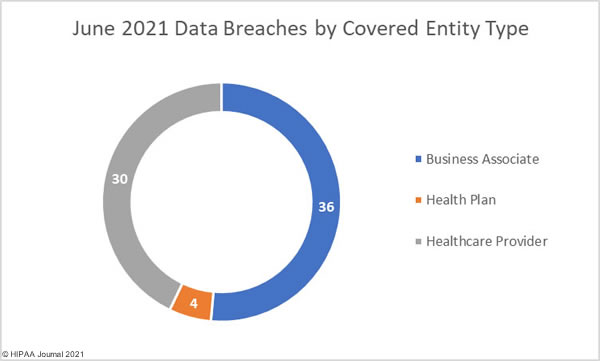
Nine critical vulnerabilities have been identified in the Nexus Control Panel of Swisslog Healthcare Translogic Pneumatic Tube System (PTS) stations, which are used in more than 80% of major hospitals in the United States. Pneumatic tube systems are used to rapidly send test samples and medications around hospitals and the vulnerable PTS stations are present in 3,000 hospitals worldwide, including 2,300 in the United States.
 The vulnerabilities, collectively named ‘PwnedPiper’, were discovered by researchers at Armis Security. In total, 9 critical flaws were identified in the Nexus Control Panel and the firmware of all current models of Translogic PTS stations are affected.
The vulnerabilities, collectively named ‘PwnedPiper’, were discovered by researchers at Armis Security. In total, 9 critical flaws were identified in the Nexus Control Panel and the firmware of all current models of Translogic PTS stations are affected.
The vulnerabilities identified by the researchers are common in Internet of Things (IoT) devices but are far more serious in pneumatic tube systems, which are part of hospitals’ critical infrastructure. The Armis researchers pointed out that these systems are prevalent in hospitals, yet they have never been thoroughly analyzed or researched.
The flaws could be exploited by a threat actor to cause denial of service, harvest sensitive data such RFID credentials of employees, and to perform reconnaissance to identify the functions or location of the stations and gain an understanding of the physical layout of the PTS network. The vulnerabilities could also be exploited in a ransomware attack.
The flaws include the use of hard-coded passwords, memory corruption vulnerabilities, privilege escalation flaws, unencrypted connections, unauthenticated firmware updates, and remote code execution vulnerabilities. If exploited, an attacker could gain full control of all Nexus stations in a hospital.
“This research sheds light on systems that are hidden in plain sight but are nevertheless a crucial building block to modern-day healthcare,” said Nadir Izrael, Armis co-founder and CTO. “Understanding that patient care depends not only on medical devices, but also on the operational infrastructure of a hospital is an important milestone to securing healthcare environments.”
The researchers detailed a scenario in which the flaws could be exploited to deliver ransomware. First an attacker would need a foothold in the hospital network. This could be as simple as exploiting a vulnerability in a low-grade IoT device such as a hospital IP camera. Once network access is gained, the Translogic PTS could be targeted since it is connected to hospital networks. Any of 5 vulnerabilities could then be exploited to achieve remote code execution in an attack that could see all Nexus stations compromised, either using ransomware or simply shutting down stations.
“In this volatile state, the hospital’s operations can be severely derailed,” said the researchers. “Medications supplied to departments, timely delivery of lab samples, and even blood units supplied to operating rooms all depending on constant availability of the PTS.”
Armis presented the findings at Black Hat USA. Swisslog Healthcare has patched 8 of the 9 vulnerabilities in Nexus Control Panel version 7.2.5.7, with the one remaining vulnerability due to be fixed in an upcoming release. The remaining vulnerability, tracked as CVE-2021-37160, affects legacy systems and is due to the lack of firmware validation during a file upload for a firmware update.
There have been no known cases of the vulnerabilities being exploited. Swisslog Healthcare has suggested mitigations and workarounds in its security advisory for hospitals that are unable to upgrade to the latest version of the Nexus Control Panel.
The post Multiple Critical Vulnerabilities Identified in Pneumatics System Used in 2,300 U.S. Hospitals appeared first on HIPAA Journal.