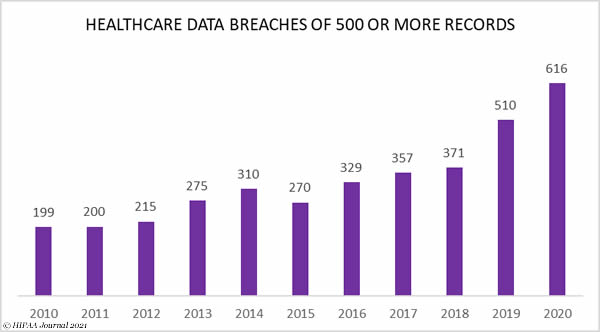
2020 was the worst ever year for healthcare industry data breaches. 616 data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights. 28,756,445 healthcare records were exposed, compromised, or impermissibly disclosed in those breaches, which makes 2020 the third worst year in terms of the number of breached healthcare records.
The chart below clearly shows how healthcare industry data breaches have steadily increased over the past decade and the sharp rise in breaches in the past two years.
The Largest Healthcare Data Breaches in 2020
When a breach occurs at a business associate of a HIPAA-covered entity, it is often the covered entity that reports the breach rather than the business associate. In 2020, a massive data breach was experienced by the cloud service provider Blackbaud Inc. Hackers gained access to its systems and stole customer fundraising databases before deploying ransomware. Blackbaud was issued with a ransom demand and a threat that the stolen data would be released publicly if the ransom was not paid. Blackbaud decided to pay the ransom to prevent the exposure of client data. Blackbaud received assurances that the stolen data was permanently deleted and not been further disclosed.
The total victim count from the Blackbaud ransomware attack may never be known, but more than 6 dozen healthcare providers have reported being affected to date and over 8 million healthcare records have potentially been compromised. That breach clearly tops the list of the largest healthcare data breaches in 2020 and ranks as one of the largest healthcare data breaches of all time.
2020’s Largest Healthcare Data Breaches
The individual entities that reported data breaches in 2020 involving more than 300,000 healthcare records are listed below. In some cases, the actual data breach occurred prior to 2020, but was only discovered and reported in 2020.
Trinity Health – 3,320,726 Individuals
At more than 3.3 million records, Trinity Health was the worst affected healthcare victim of the ransomware attack on Blackbaud Inc. The hackers potentially obtained the philanthropy database of the Livonia, Michigan-based Catholic health system, which contained patient and donor information from 2000 to 2020.
MEDNAX Services, Inc. – 1,290,670 Individuals
Sunrise, FL-based MEDNAX Services Inc, a provider of revenue cycle management and other administrative services to its affiliated physician practice groups, suffered a breach of its Office 365 environment in June 2020 after employees responded to phishing emails. The breach was extensive, involving patient and guarantor information such as Social Security numbers, driver’s license numbers, and health insurance and financial information.
Inova Health System – 1,045,270 Individuals
Virginia-based Inova Health System was also a victim of the Blackbaud ransomware attack. The hackers gained access to Blackbaud’s systems on February 7, 2020 and the breach continued until May 20, 2020. Ransomware was deployed on May 14, 2020. Inova’s fundraising database was potentially compromised which contained patient and donor information.
Magellan Health Inc. 1,013,956 Individuals
Arizona-based Magellan Health was the victim of an April 2020 ransomware attack in which the protected health information of patients was potentially compromised. The attack ended with the deployment of ransomware but started with a spear phishing email. Several of its affiliated entities were also affected by the breach.
Dental Care Alliance – 1,004,304 Individuals
Sarasota, FL-based Dental Care Alliance, LLC, a dental support organization with more than 320 affiliated dental practices across 20 states, reported a breach of its systems in December. Few details have been released about the nature of the hacking incident as the investigation is still ongoing. The breach affected many of its affiliated dental practices.
Luxottica of America Inc. – 829,454 Individuals
Luxottica of America Inc., an operator of vision care facilities across the United States and owner of the eyewear brands Ray-Ban, Oakley, and Persol, experienced a cyberattack in August 2020 which saw hackers gain access to its web-based appointment scheduling system which contained the PHI of patients of its eye care partners.
Northern Light Health – 657,392 Individuals
The Maine health system Northern Light Health was also a victim of the ransomware attack on Blackbaud Inc. The hackers potentially gained access to its fundraising database which contained patient and donor information.
Health Share of Oregon – 654,362 Individuals
In May 2020, the Medicaid coordinated care organization Health Share of Oregon reported the theft of a laptop computer from its non-emergent medical transportation vendor. The laptop was stolen in November 2019 and was not encrypted, which potentially gave the thief access to patents’ contact information, Health Share ID numbers, and Social Security numbers.
Florida Orthopaedic Institute – 640,000 Individuals
Florida Orthopaedic Institute suffered a ransomware attack in April which saw patient information on its servers encrypted. Prior to the use of ransomware, patient data may have been viewed or obtained by the hackers.
Elkhart Emergency Physicians – 550,000 Individuals
Elkhart Emergency Physicians reported a breach in May 2020 involving the improper disposal of patient records by a third-party storage vendor – Central Files Inc. Elkhart Emergency Physicians was the worst affected entity, but several other clients of the vendor were also impacted by the breach. The records had been dumped without being shredded after the storage facility permanently closed.
Aetna ACE – 484,157 Individuals
Aetna reported a data breach in December which occurred at business associate EyeMed, which provides vision benefit services for its members. The breach occurred when an EyeMed employee responded to a phishing email, which allowed the attacker to gain access to email accounts containing PHI. Several EyeMed clients were affected by the breach.
Saint Luke’s Foundation – 360,212 Individuals
Kansas City, MO-based Saint Luke’s Foundation was also a victim of the ransomware attack on Blackbaud Inc. The hackers potentially gained access to its fundraising database which contained patient and donor information.
NorthShore University Health System – 348,746 Individuals
Evanston, IL-based NorthShore University Health System was also affected by the ransomware attack on Blackbaud Inc. The hackers potentially gained access to its fundraising database.
SCL Health Colorado – 343,493 Individuals
SCL Health Colorado was also a victim of the Blackbaud ransomware attack. The PHI of patients in its Colorado, Montana and Kansas locations was potentially accessed by the attackers.
AdventHealth – 315,811 Individuals
The Altamonte Springs, FL-based healthcare system AdventHealth was also a victim of the Blackbaud ransomware attack which saw the hackers gain access to its fundraising database.
Nuvance Health – 314,829 Individuals
Nuvance Health was a victim of the ransomware attack on Blackbaud Inc. The hackers potentially gained access to its fundraising database between February and May.
Magellan Rx Management – 314,704 Individuals
Magellan Rx Management was one of the victims of the ransomware attack on its parent company, Magellan Health, in April. The hackers potentially stole patient data prior to encrypting files.
The Baton Rouge Clinic – 308,169 Individuals
The Baton Rouge Clinic in Louisiana experienced a cyberattack in early July involving ransomware. The attackers potentially viewed or obtained patient data prior to the deployment of ransomware.
The post Largest Healthcare Data Breaches in 2020 appeared first on HIPAA Journal.