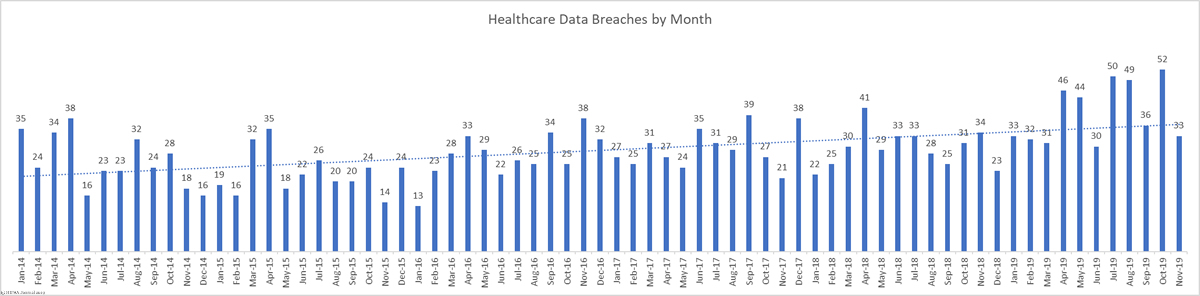
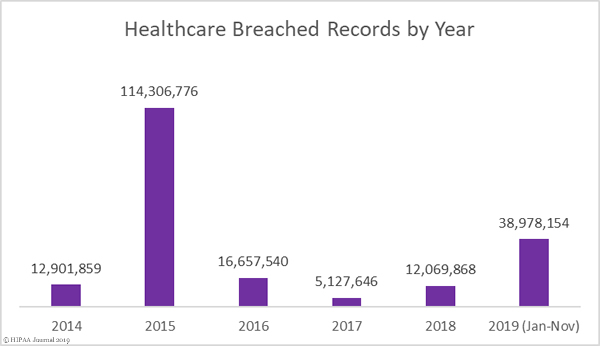
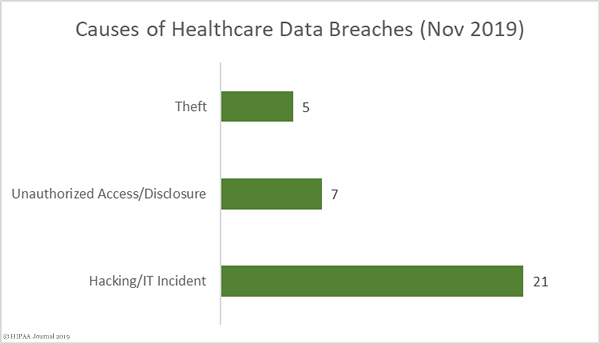
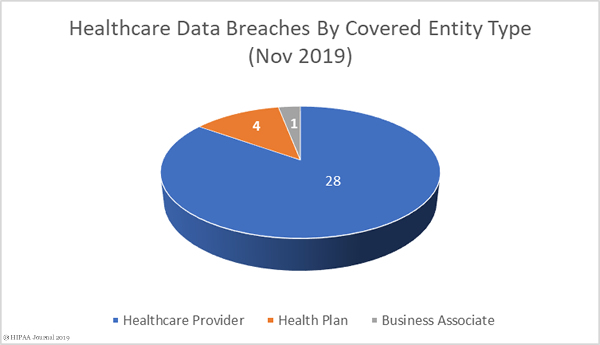
Healthcare industry data breaches are occurring more frequently than ever before. The healthcare data breach figures for 2019 have yet to be finalized, but so far 494 data breaches of more than 500 records have been reported to the HHS’ Office for Civil Rights and more than 41.11 million records were exposed, stolen, or impermissibly disclosed in 2019. That makes 2019 the worst ever year for healthcare data breaches and the second worst in terms of the number of breached healthcare records.
The healthcare industry now accounts for around four out of every five data breaches and 2020 looks set to be another record-breaking year. The cost to the healthcare industry from those breaches is expected to reach $4 billion in 2020.
The poor state of healthcare cybersecurity was highlighted by a survey of healthcare security professionals conducted in late 2019 by Black Book Market Research. The survey was conducted on 2,876 security professionals from 733 provider organizations to identify cybersecurity gaps, vulnerabilities, and deficiencies in the healthcare industry.
The survey revealed more than 93% of healthcare organizations experienced a data breach between Q3, 2016. 57% of surveyed healthcare providers experienced more than 5 breaches in that period. Even though there is a high risk of a data breach being suffered, investment in cybersecurity is nowhere near the level it needs to be.
“It is becoming increasingly difficult for hospitals to find the dollars to invest in an area that does not produce revenue,” said Doug Brown, founder of Black Book. According to 90% of hospital representatives surveyed, IT security budgets have remained level since 2016.”
The survey revealed hospital systems have increased their cybersecurity budgets to around 6% of their IT spend but spending on cybersecurity by physician organizations has decreased since 2018 and now stands at less than 1% of their IT budget.
When money is spent on cybersecurity, solutions are often purchased blindly or with little vision or discernment. The survey showed that between 2016 and 2018, 92% of data security purchase decisions were made by the C-suite without any users or affected department managers being involved in the purchasing decision.
Despite the threat of attack, 92% of healthcare organizations lack full time cybersecurity professionals and only 21% of hospitals said they had a dedicated security executive. Only 6% of those respondents said that individual was the Chief Information Security Officer (CISO). Physician groups are much less likely to have a CISO. Only 1.5% of physician groups with more than 10 clinicians said they had a dedicated CISO.
More CISOs and cybersecurity professionals are sorely needed, but it is unclear where those individuals will come from due to a nationwide shortage of skilled cybersecurity professionals. In the meantime, cybersecurity is having to be outsourced to managed service providers as a stop-gap measure.
Other key findings of the survey include:
- 96% of IT professionals said threat actors are outpacing medical enterprises
- More money is being spent on marketing to repair damaged reputations after a breach than is spent on combating the consequences of data breaches.
- 35% of healthcare organizations did not scan for vulnerabilities before an attack
- 87% of healthcare organizations have not had a cybersecurity drill with an incident response process
- 40% of providers surveyed do not carry out measurable assessments of their cybersecurity status.
- 26% of hospital respondents and 93% of physician organizations currently report they do not have an adequate solution to instantly detect and respond to an organizational attack.
The post Healthcare Data Breaches Predicted to Cost Industry $4 Billion in 2020 appeared first on HIPAA Journal.