Pressure is continuing to be applied on Google and its parent company Alphabet to disclose information about how the protected health information (PHI) of patients of Ascension will be used, and the measures put in place to ensure PHI is secured and protected against unauthorized access.
The partnership between Google and Ascension was announced on November 11, 2019 following the publication of a story in the Wall Street Journal. A whistleblower at Google had shared information with the WSJ and expressed concern that millions of healthcare records had been shared with Google without first obtaining consent from patients. It was also alleged that Google employees could freely download PHI.
In its announcement, Google stated that the collaboration – named Project Nightingale – involved migrating Ascension’s infrastructure to the cloud and that it was helping Ascension implement G Suite tools to improve productivity and efficiency. Patient data was also being provided to Google to help develop AI and machine learning technologies to improve patient safety and clinical quality. When the migration of data has been completed, Google will have access to the health data of around 50 million patients.
Google has confirmed it is a business associate of Ascension and has signed a business associate agreement and is fully compliant with HIPAA regulations, but many privacy advocates are concerned about the partnership. Several members of Congress have also expressed concern and are seeking answers about the safeguards that have been put in place to secure patient data and how patient data will be used. The HHS’ Office for Civil Rights has also confirmed it is investigating Google and Ascension to make sure HIPAA Rules have not been violated.
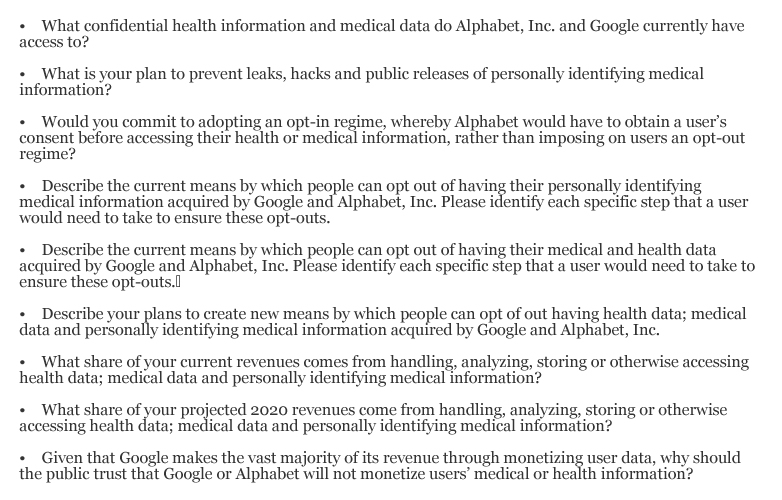
Earlier this month, Rep. Pramila Jayapal (D-Washington), a member of the House Judiciary Subcommittee on Antitrust, Commercial, and Administrative Law, wrote to Google and Alphabet expressing concern about the partnership. She has demanded answers to several questions about how protected health information has been obtained, the measures put in place to protect patient data, and how Google will be using the PHI.
“As Google and parent company Alphabet have engaged in an ever-widening acquisition of the highly personal health-related information of millions of people, Americans now face the prospect of having their sensitive health information handled by corporations who may misuse it,” wrote Rep. Jayapal in her Dec 6, 2019 letter. “I am especially concerned that your company has not provided sufficient assurances that this sensitive data will be kept safe, and that patients’ data is being acquired by your companies without their consent and without any opt-out provision.”
Rep. Jayapal is particularly concerned about how that information will be used. Google is amassing huge quantities of healthcare data from several sources. Google’s healthcare-focused AI unit, Medical Brain, is actively acquiring health data, Alphabet has partnered with the Mayo Clinic, and Google has acquired the UK startup, DeepMind. NHS data has already been provided to Google. Google is also looking to acquire Fitbit, which holds health-related data on 25 million users of its wearable devices.
“The fact that Google makes the vast majority of its revenue through behavioral online advertising—creating an incentive to commoditize all user information—renders the company’s expansion into health services all the more troubling,” wrote Rep. Jayapal.
Rep. Jayapal also pointed out that Google does not have a blemish-free track record when it comes to protecting health and medical information, referencing one incident in which chest X-ray images from the National Institute of Health were almost posted online before Google realized they contained personally identifiable information. She also stated there is an active lawsuit that claims Google companies have obtained patient information from a major medical facility and DeepMind was found to have violated the Data Protection Act in the UK by using patient data to develop new apps.
Rep. Jayapal has given Google and Alphabet until January 5, 2020 to answer her questions, as detailed below:
The post Rep. Jayapal Seeks Answers from Google and Alphabet on Ascension Partnership appeared first on HIPAA Journal.