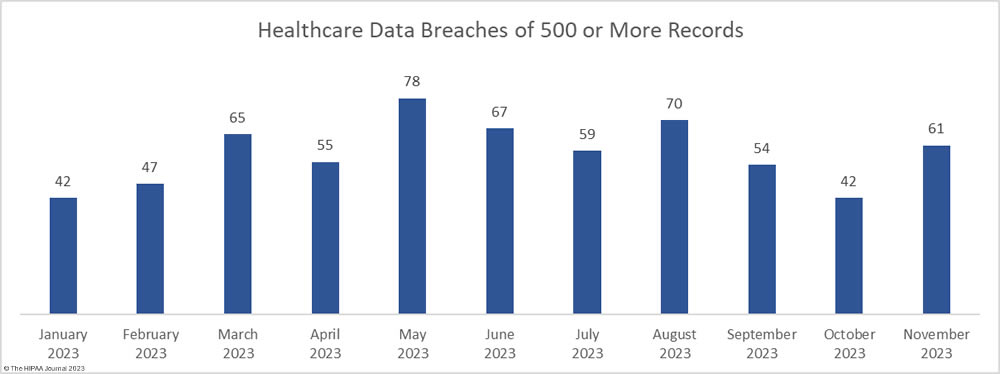
After two months of declining healthcare data breaches, there was a 45% increase in reported breaches of 500 or more healthcare records. In November, 61 large data breaches were reported to the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) – three more than the monthly average for 2023. From January 1, 2023, through November 30, 2023, 640 large data breaches have been reported.
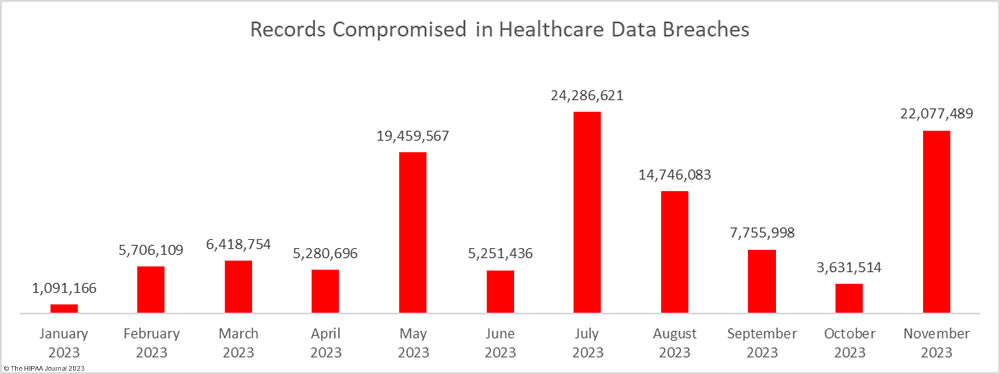
In addition to an increase in data breaches, there was a massive increase in the number of breached records. 22,077,489 healthcare records were exposed or compromised across those 61 incidents – a 508% increase from October. November was the second-worst month of the year in terms of breached records behind July, when 24 million healthcare records were reported as breached. There is still a month of reporting left but 2023 is already the worst-ever year for breached healthcare records. From January 1, 2023, through November 30, 2023, 115,705,433 healthcare records have been exposed or compromised – more than the combined total for 2021 and 2022.
Largest Healthcare Data Breaches in November 2023
November was a particularly bad month for large data breaches, with 28 breaches of 10,000 or more records, including two breaches of more than 8 million records. Two of the breaches reported in November rank in the top ten breaches of all time and both occurred at business associates of HIPAA-covered entities. The largest breach occurred at Perry Johnson & Associates, Inc. (PJ&A) a provider of medical transcription services. The PJ&A data breach was reported to OCR as affecting 8,952,212 individuals, although the total is higher, as some of its clients have chosen to report the breach themselves. Hackers had access to the PJ&A network for more than a month between March and May 2023.
The second-largest breach was reported by Welltok, Inc. as affecting 8,493,379 individuals. Welltok works with health plans and manages communications with their subscribers. The Welltok data breach is one of many 2023 data breaches involving the exploitation of a zero-day vulnerability in Progress Software’s MOVEit Transfer file transfer solution by the Clop hacking group. Globally, more than 2,615 organizations had the vulnerability exploited and data stolen.
A further three data breaches were reported that involved the protected health information of more than 500,000 individuals. Sutter Health was also one of the victims of the mass hacking of the MOVEit vulnerability and had the data of 845,441 individuals stolen, as did Blue Shield of California (636,848 records). In both cases, the MOVEit tool was used by business associates of those entities. East River Medical Imaging in New York experienced a cyberattack that saw its network breached for three weeks between October and September 2023, during which time the hackers exfiltrated files containing the PHI of 605,809 individuals. All 28 of these large data breaches were hacking incidents that saw unauthorized access to network servers.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Cause of Breach |
| Perry Johnson & Associates, Inc., which does business as PJ&A |
NV |
Business Associate |
8,952,212 |
Hacking and data theft incident |
| Welltok, Inc. |
CO |
Business Associate |
8,493,379 |
Hacking incident (MOVEit Transfer) |
| Sutter Health |
CA |
Healthcare Provider |
845,441 |
Hacking incident at business associate (MOVEit Transfer) |
| California Physicians’ Service d/b/a Blue Shield of California |
CA |
Health Plan |
636,848 |
Hacking incident at business associate (MOVEit Transfer) |
| East River Medical Imaging, PC |
NY |
Healthcare Provider |
605,809 |
Hacking and data theft incident |
| State of Maine |
ME |
Health Plan |
453,894 |
Hacking incident (MOVEit Transfer) |
| Proliance Surgeons |
WA |
Healthcare Provider |
437,392 |
Ransomware attack |
| Medical Eye Services, Inc. |
NY |
Business Associate |
377,931 |
Hacking incident (MOVEit Transfer) |
| Medical College of Wisconsin |
WI |
Healthcare Provider |
240,667 |
Hacking incident (MOVEit Transfer) |
| Warren General Hospital |
PA |
Healthcare Provider |
168,921 |
Hacking and data theft incident |
| Financial Asset Management Systems (“FAMS”) |
GA |
Business Associate |
164,796 |
Ransomware attack |
| Morrison Community Hospital District |
IL |
Healthcare Provider |
122,488 |
Ransomware attack (BlackCat) |
| South Austin Health Imaging LLC dba Longhorn Imaging Center |
TX |
Healthcare Provider |
100,643 |
Hacking and data theft incident (SiegedSec threat group) |
| Mulkay Cardiology Consultants at Holy Name Medical Center, P.C. |
NJ |
Healthcare Provider |
79,582 |
Ransomware attack (NoEscape) |
| International Paper Company Group Health and Welfare Plan (the “IP Plan”) |
TN |
Health Plan |
78,692 |
Hacking incident at business associate (MOVEit Transfer) |
| CBIZ KA Consulting Services, LLC |
NJ |
Business Associate |
30,806 |
Hacking incident (MOVEit Transfer) |
| Endocrine and Psychiatry Center |
TX |
Healthcare Provider |
28,531 |
Hacking and data theft incident |
| Blue Shield of California OR Blue Shield of California Promise Health Plan |
CA |
Business Associate |
26,523 |
Hacking incident at business associate (MOVEit Transfer) |
| Wyoming County Community Health System |
NY |
Healthcare Provider |
26,000 |
Hacking and data theft incident |
| Westat, Inc. |
MD |
Business Associate |
20,045 |
Hacking incident (MOVEit Transfer) |
| Psychiatry Associates of Kansas City |
KS |
Healthcare Provider |
18,255 |
Hacking and data theft incident |
| Southwest Behavioral Health Center |
UT |
Healthcare Provider |
17,147 |
Hacking and data theft incident |
| TGI Direct, Inc. |
MI |
Business Associate |
16,113 |
Hacking incident (MOVEit Transfer) |
| Pharmacy Group of Mississippi, LLC |
MS |
Healthcare Provider |
13,129 |
Hacking and data theft incident |
| U.S. Drug Mart, Inc. |
TX |
Healthcare Provider |
13,016 |
Hacking and data theft incident at business associate |
| Catholic Charities of the Diocese of Rockville Centre d/b/a Catholic Charities of Long Island |
NY |
Healthcare Provider |
13,000 |
Hacking and data theft incident |
| Foursquare Healthcare, Ltd. |
TX |
Healthcare Provider |
10,890 |
Ransomware attack |
| Saisystems International, Inc. |
CT |
Business Associate |
10,063 |
Hacking and data theft incident |
November 2023 Data Breach Causes and Data Locations
Many of the month’s breaches involved the mass hacking of a vulnerability in the MOVEit Transfer solution by the Clop threat group. MOVEit data breaches continue to be reported, despite the attacks occurring in late May. According to the cybersecurity firm Emsisoft, at least 2,620 organizations were affected by these breaches, and 77.2 million records were stolen. 78.1% of the affected organizations are based in the United States. Progress Software is currently being investigated by the U.S. Securities and Exchange Commission over the breach. Hacking/ransomware attacks accounted for 88.52% of the month’s data breaches (54 incidents) and 99.94% of the breached records (22,064,623 records). The average data breach size was 408,604 records and the median breach size was 10,477 records.
Ransomware gangs continue to target the healthcare industry, and in November several ransomware groups listed stolen healthcare data on their leak sites including NoEscape and BlackCat. Many hacking groups choose not to use ransomware and instead just steal data and threaten to sell or publish the data if the ransom is not paid, such as Hunter’s International and SiegedSec. Since there is little risk of ransomware actors being apprehended and brought to justice, the attacks are likely to continue. OCR is planning to make it harder for cyber actors to succeed by introducing new cybersecurity requirements for healthcare organizations. These new cybersecurity requirements will be voluntary initially but will later be enforced. New York has also announced that stricter cybersecurity requirements for hospitals will be introduced in the state, and financial assistance will be offered.
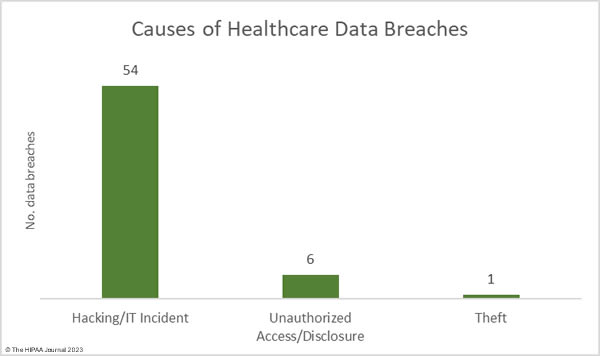
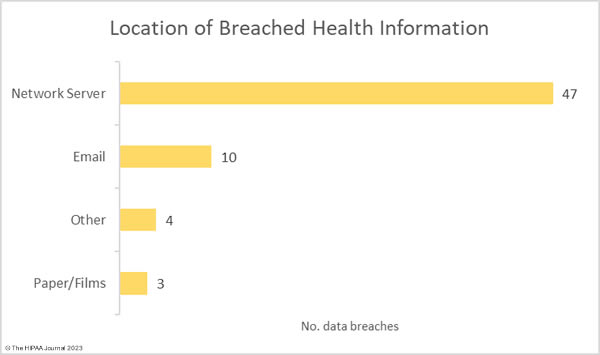
There were 6 data breaches classified as unauthorized access/disclosure incidents, across which 10,371 records were impermissibly accessed by or disclosed to unauthorized individuals. The average data breach size was 1,481 records and the median breach size was 1,481 records. There was one reported incident involving the theft of paperwork that contained the protected health information of 2,495 individuals. For the second consecutive month, there were no reported loss or improper disposal incidents. The most common location of breached PHI was network servers, which accounted for 77% of all incidents. 10 incidents involved PHI stored in email accounts.
Where did the Data Breaches Occur?
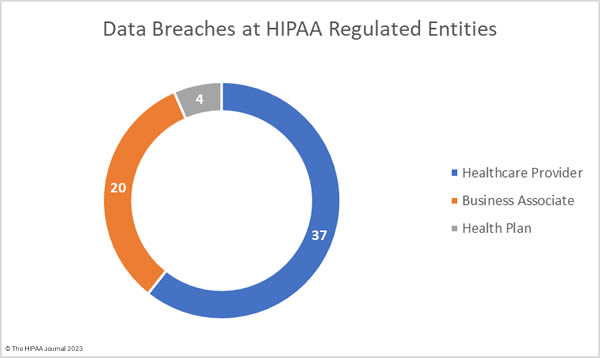
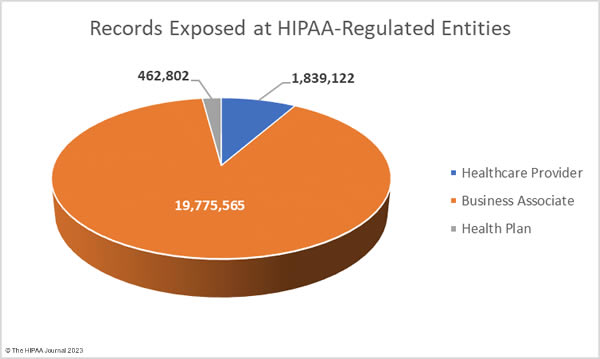
The OCR data breach portal shows healthcare providers were the worst affected HIPAA-regulated entity in November, with 42 reported data breaches. There were 13 data breaches reported by business associates and 6 data breaches reported by health plans. The problem with these figures is they do not accurately reflect where the data breaches occurred. When a business associate experiences a data breach, they may report it to OCR, the affected covered entities may report the breach or a combination of the two. As such, the raw data often does not accurately reflect the number of data breaches occurring at business associates of HIPAA-covered entities. The data used to compile the charts below has been adjusted to show where the data breach occurred rather than the entity that reported the breach.
Geographical Distribution of Healthcare Data Breaches
Data breaches were reported by HIPAA-regulated entities in 28 states. California was the worst affected state with 8 reported breaches, followed by New York with 6.
| State |
Number of Breaches |
| California |
8 |
| New York |
6 |
| Illinois & Texas |
5 |
| Connecticut, Florida, Georgia, Indiana, Iowa, Kansas, Maine, Michigan, Minnesota, New Jersey, Oregon, South Carolina & Washington |
2 |
| Arizona, Colorado, Maryland, Massachusetts, Mississippi, Nevada, Ohio, Pennsylvania, Tennessee, Utah & Wisconsin |
1 |
HIPAA Enforcement Activity in November 2023
OCR announced one enforcement action in November. A settlement was agreed with St. Joseph’s Medical Center to resolve allegations of an impermissible disclosure of patient information to a reporter. OCR launched an investigation following the publication of an article by an Associated Press reporter who had been allowed to observe three patients who were being treated for COVID-19. The article included photographs and information about the patients and was circulated nationally. OCR determined that the patients had not provided their consent through HIPAA authorizations, therefore the disclosures violated the HIPAA Privacy Rule. St. Joseph Medical Center settled the alleged violations and paid an $80,000 financial penalty.
HIPAA is primarily enforced by OCR although State Attorneys General may also investigate HIPAA-regulated entities and they also have the authority to issue fines for HIPAA violations. In November, one settlement was announced by the New York Attorney General to resolve alleged violations of HIPAA and state laws. U.S. Radiology Specialists Inc. was investigated over a breach of the personal and protected health information of 198,260 individuals, including 95,540 New York Residents. The New York Attorney General’s investigation determined that U.S. Radiology Specialists was aware that vulnerabilities existed but failed to address those vulnerabilities in a timely manner. Some of those vulnerabilities were exploited by cyber actors in a ransomware attack. U.S. Radiology Specialists agreed to pay a $450,000 financial penalty and ensure full compliance with HIPAA and state laws.
The post November 2023 Healthcare Data Breach Report appeared first on HIPAA Journal.






