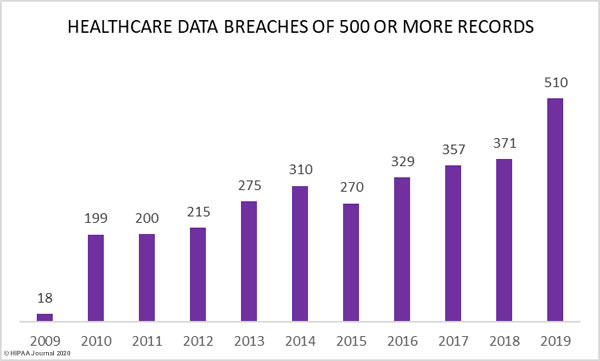
Figures from the Department of Health and Human Services’ Office for Civil Rights breach portal show a major increase in healthcare data breaches in 2019. Last year, 510 healthcare data breaches of 500 or more records were reported, which represents a 196% increase from 2018.
As the graph below shows, aside from 2015, healthcare data breaches have increased every year since the HHS’ Office for Civil Rights first started publishing breach summaries in October 2009.
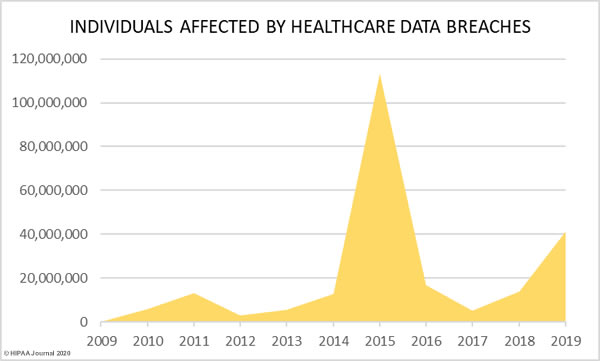
37.47% more records were breached in 2019 than 2018, increasing from 13,947,909 records in 2018 to 41,335,889 records in 2019.
Last year saw more data breaches reported than any other year in history and 2019 was the second worst year in terms of the number of breached records. More healthcare records were breached in 2019 than in the six years from 2009 to 2014. In 2019, the healthcare records of 12.55% of the population of the United States were exposed, impermissibly disclosed, or stolen.
Largest Healthcare Data Breaches of 2019
The table below shows the largest healthcare data breaches of 2019, based on the entity that reported the breach.
| Name of Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach | Location of Breached Information | |
| 1 | Optum360, LLC | Business Associate | 11500000 | Hacking/IT Incident | Network Server |
| 2 | Laboratory Corporation of America Holdings dba LabCorp | Healthcare Provider | 10251784 | Hacking/IT Incident | Network Server |
| 3 | Dominion Dental Services, Inc., Dominion National Insurance Company, and Dominion Dental Services USA, Inc. | Health Plan | 2964778 | Hacking/IT Incident | Network Server |
| 4 | Clinical Pathology Laboratories, Inc. | Healthcare Provider | 1733836 | Unauthorized Access/Disclosure | Network Server |
| 5 | Inmediata Health Group, Corp. | Healthcare Clearing House | 1565338 | Unauthorized Access/Disclosure | Network Server |
| 6 | UW Medicine | Healthcare Provider | 973024 | Hacking/IT Incident | Network Server |
| 7 | Women’s Care Florida, LLC | Healthcare Provider | 528188 | Hacking/IT Incident | Network Server |
| 8 | CareCentrix, Inc. | Healthcare Provider | 467621 | Hacking/IT Incident | Network Server |
| 9 | Intramural Practice Plan – Medical Sciences Campus – University of Puerto Rico | Healthcare Provider | 439753 | Hacking/IT Incident | Network Server |
| 10 | BioReference Laboratories Inc. | Healthcare Provider | 425749 | Hacking/IT Incident | Other |
| 11 | Bayamon Medical Center Corp. | Healthcare Provider | 422496 | Hacking/IT Incident | Network Server |
| 12 | Memphis Pathology Laboratory d/b/a American Esoteric Laboratories | Healthcare Provider | 409789 | Unauthorized Access/Disclosure | Network Server |
| 13 | Sunrise Medical Laboratories, Inc. | Healthcare Provider | 401901 | Hacking/IT Incident | Network Server |
| 14 | Columbia Surgical Specialist of Spokane | Healthcare Provider | 400000 | Hacking/IT Incident | Network Server |
| 15 | Sarrell Dental | Healthcare Provider | 391472 | Hacking/IT Incident | Network Server |
| 16 | UConn Health | Healthcare Provider | 326629 | Hacking/IT Incident | |
| 17 | Premier Family Medical | Healthcare Provider | 320000 | Hacking/IT Incident | Network Server |
| 18 | Metro Santurce, Inc. d/b/a Hospital Pavia Santurce and Metro Hato Rey, Inc. d/b/a Hospital Pavia Hato Rey | Healthcare Provider | 305737 | Hacking/IT Incident | Network Server |
| 19 | Navicent Health, Inc. | Healthcare Provider | 278016 | Hacking/IT Incident | |
| 20 | ZOLL Services LLC | Healthcare Provider | 277319 | Hacking/IT Incident | Network Server |
The above table does not tell the full story. When a business associate experiences a data breach, it is not always reported by the business associate. Sometimes a breach is experienced by a business associate and the covered entities that they work with report the breaches separately, as was the case with American Medical Collection Agency (AMCA), a collection agency used by several HIPAA covered entities.
In 2019, hackers gained access to AMCA systems and stole sensitive client data. The breach was the second largest healthcare data breach ever reported, with only the Anthem Inc. data breach of 2015 having impacted more individuals.
HIPAA Journal tracked the breach reports submitted to OCR by each affected covered entity. At least 24 organizations are known to have had data exposed/stolen as a result of the hack.
Organizations Affected by the 2019 AMCA Data Breach
| Healthcare Organization | Confirmed Victim Count |
| Quest Diagnostics/Optum360 | 11,500,000 |
| LabCorp | 10,251,784 |
| Clinical Pathology Associates | 1,733,836 |
| Carecentrix | 467,621 |
| BioReference Laboratories/Opko Health | 425,749 |
| American Esoteric Laboratories | 409,789 |
| Sunrise Medical Laboratories | 401,901 |
| Inform Diagnostics | 173,617 |
| CBLPath Inc. | 141,956 |
| Laboratory Medicine Consultants | 140,590 |
| Wisconsin Diagnostic Laboratories | 114,985 |
| CompuNet Clinical Laboratories | 111,555 |
| Austin Pathology Associates | 43,676 |
| Mount Sinai Hospital | 33,730 |
| Integrated Regional Laboratories | 29,644 |
| Penobscot Community Health Center | 13,299 |
| Pathology Solutions | 13,270 |
| West Hills Hospital and Medical Center / United WestLabs | 10,650 |
| Seacoast Pathology, Inc | 8,992 |
| Arizona Dermatopathology | 5,903 |
| Laboratory of Dermatology ADX, LLC | 4,082 |
| Western Pathology Consultants | 4,079 |
| Natera | 3,035 |
| South Texas Dermatopathology LLC | 15,982 |
| Total Records Breached | 26,059,725 |
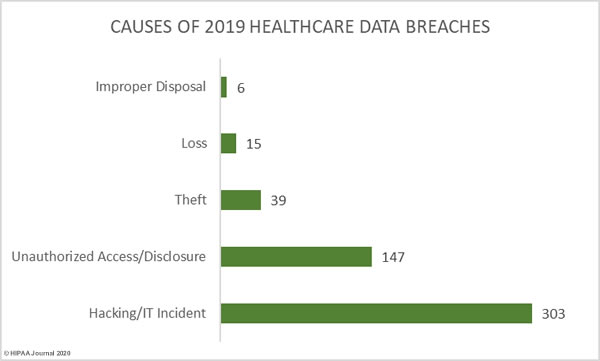
Causes of 2019 Healthcare Data Breaches
The HHS’ Office for Civil Rights assigns breaches to one of five different categories:
- Hacking/IT incidents
- Unauthorized access/disclosures
- Theft
- Loss
- Improper disposal
59.41% of healthcare data breaches in 2019 were classified as hacking/IT incidents and involved 87.60% of all breached records. 28.82% of data breaches were classed as unauthorized access/disclosure incidents and involved 11.27% of all records breached in 2019.
10.59% of breaches were classed as loss and theft incidents involving electronic devices containing unencrypted electronic protected health information or physical records. Those incidents accounted for 1.07% of breached records in 2019.
1.18% of breaches and 0.06% of breached records were due to improper disposal of physical records and devices containing electronic protected health information.
| Breach Cause | Incidents | Breached Records | Mean Breach Size | Median Breach Size |
| Hacking/IT Incident | 303 | 36,210,097 | 119,505 | 6,000 |
| Unauthorized Access/Disclosure | 147 | 4,657,932 | 31,687 | 1,950 |
| Theft | 39 | 367,508 | 9,423 | 2,477 |
| Loss | 15 | 74,271 | 4,951 | 3,135 |
| Improper Disposal | 6 | 26,081 | 4,347 | 4,177 |
We have not tracked the cause of each breach reported in 2019, but the table below provides an indication of the biggest problem area for healthcare organizations – Securing email systems and blocking phishing attacks. The email incidents include misdirected emails, but the majority of email incidents were phishing and spear phishing attacks.
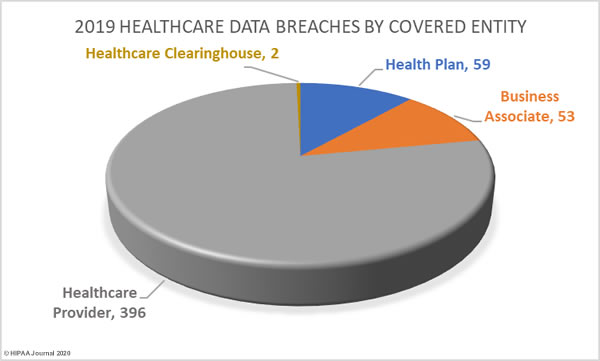
Healthcare Data Breaches by Covered Entity
77.65% of 2019 data breaches were reported by healthcare providers (369 incidents), 11.57% of breaches were reported by health plans (59 incidents), and 0.39% of data breaches were reported by healthcare clearinghouses (2 incidents).
23.33% of the year’s breaches involved business associates to some extent. 10.39% of data breaches were reported by business associates (53 incidents) and 66 data breaches were reported by a covered entity which stated there was some business associate involvement.
States Worst Affected by Healthcare Data Breaches
Data breaches were reported by HIPAA-covered entities or business associates in 48 states, Washington DC, and Puerto Rico. The worst affected state was Texas with 60 data breaches reported. California was the second most badly hit with 42 reported data breaches.
The only states where no data breaches of 500 or more records were reported were North Dakota and Hawaii.
| State | Breaches | State | Breaches | State | Breaches | State | Breaches | State | Breaches |
| Texas | 60 | Maryland | 14 | Arkansas | 9 | Alabama | 4 | Mississippi | 2 |
| California | 42 | Washington | 14 | South Carolina | 9 | Alaska | 4 | Montana | 2 |
| Illinois | 26 | Georgia | 13 | New Jersey | 8 | Iowa | 4 | South Dakota | 2 |
| New York | 25 | North Carolina | 13 | Massachusetts | 7 | Kentucky | 4 | Washington DC | 2 |
| Ohio | 25 | Tennessee | 11 | Puerto Rico | 7 | Nebraska | 4 | West Virginia | 2 |
| Minnesota | 23 | Arizona | 10 | Virginia | 7 | Oklahoma | 4 | Delaware | 1 |
| Florida | 22 | Colorado | 10 | Louisiana | 6 | Utah | 4 | Kansas | 1 |
| Pennsylvania | 19 | Connecticut | 10 | New Mexico | 6 | Wyoming | 3 | New Hampshire | 1 |
| Missouri | 17 | Indiana | 10 | Wisconsin | 6 | Idaho | 2 | Rhode Island | 1 |
| Michigan | 16 | Oregon | 10 | Nevada | 5 | Maine | 2 | Vermont | 1 |
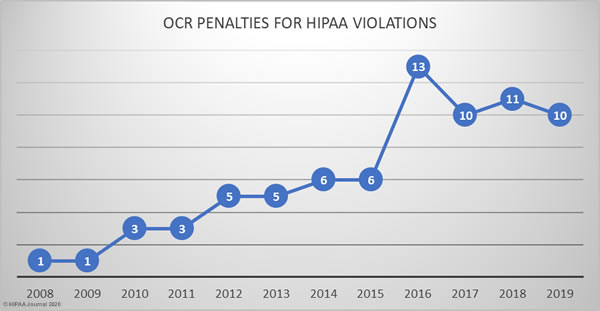
HIPAA Enforcement in 2019
The HHS’ Office for Civil Rights continued to enforce compliance with HIPAA at a similar level to the previous three years.
In 2019, there were 10 HIPAA enforcement actions that resulted in financial penalties. 2 civil monetary penalties were imposed and 8 covered entities/business associates agreed settlements with OCR to resolve HIPAA violations.
In total, $12,274,000 was paid to OCR in fines and settlements. The largest financial penalties of the year resulted from investigations of potential HIPAA violations by University of Rochester Medical Center and Touchstone Medical Imaging. Both cases were settled for £3,000,000.
OCR uncovered multiple violations of HIPAA Rules while investigating separate loss/theft incidents reported by University of Rochester Medical Center. OCR discovered risk analysis and risk management failures, a lack of encryption on portable electronic devices, and insufficient device and media controls.
Touchstone Medical Imaging experienced a data breach that resulted in the impermissible disclosure of 307,839 individuals’ PHI due to the exposure of an FTP server over the internet. OCR investigated and determined there had been risk analysis failures, business associate agreements failures, insufficient access rights, a failure to respond to a security incident, and violations of the HIPAA Breach Notification Rule.
Sentara Hospitals agreed to a $2.175 million settlement stemming from a 577-record data breach that was reported to OCR as only affecting 8 individuals. OCR told Sentara Hospitals that the breach notification needed to be updated to include the other individuals affected by the mailing error, but Sentara Hospitals refused. OCR determined a financial penalty was appropriate for the breach notification reporting failure and the lack of a business associate agreement with one of its vendors.
A civil monetary penalty of $2.154 million was imposed on the Miami, FL-based nonprofit academic medical system, Jackson Health System (JHS). Following a data breach, OCR investigated and found a compliance program that had been in disarray for several years. The CMP resolved multiple violations of HIPAA Privacy Rule, Security Rule, and Breach Notification Rule.
A civil monetary penalty of $1,600,000 was imposed on Texas Department of Aging and Disability Services for multiple violations of HIPAA Rules discovered during the investigation of breach involving an exposed internal application. OCR discovered there had been risk analysis failures, access control failures, and information system activity monitoring failures, which contributed to the impermissible disclosure of 6,617 patients’ ePHI.
Medical Informatics Engineering, an Indiana-based provider of electronic medical record software and services, experienced a major data breach in 2015 at its NoMoreClipboard subsidiary. Hackers used a compromised username and password to gain access to a server that contained the protected health information (PHI) of 3.5 million individuals. OCR determined there had been a risk analysis failure and the case was settled for $100,000. MIE also settled a multi-state action with state attorneys general over the same breach and settled that case for $900,000.
The Carroll County, GA ambulance company, West Georgia Ambulance, was investigated over the reported loss of an unencrypted laptop computer that contained the PHI of 500 patients. OCR found there had been a risk analysis failure, there was no security awareness training program for staff, and HIPAA Security Rule policies and procedures had not been implemented. The case was settled for $65,000.
There was one financial penalty for a social media HIPAA violation. Elite Dental Associates respondents to patient reviews on Yelp, and in doing so impermissibly disclosed PHI. OCR determined a financial penalty was appropriate and the case was settled for $10,000.
OCR also launched a new HIPAA enforcement initiative in 2019, under which two settlements were reached with covered entities over HIPAA Right of Access failures. Korunda Medical and Bayfront Health St. Petersburg had both failed to respond to patient requests for copies of their health information within a reasonable time frame. Both covered entities settled their HIPAA violation cases with OCR for $85,000.
OCR HIPAA Settlements and Civil Monetary Penalties in 2019
HIPAA Enforcement by State Attorneys General in 2019
State attorneys general can also take action over violations of HIPAA Rules. There were three cases against covered entities and business associates in 2019. As previously mentioned, Medical Informatics Engineering settled a multi-state lawsuit and paid a financial penalty of $900,000.
A second multi-state action was settled by Premera Blue Cross. The lawsuit pertained to a 2015 hacking incident that resulted in the theft of 10.4 million records. The investigation uncovered multiple violations of violations of HIPAA Rules and resulted in a $10 million financial penalty.
The California attorney general also took legal action over a data breach that affected 1,991 California residents. The health insurer Aetna had sent two mailings to its members in which highly sensitive information relating to HIV and Afib diagnoses was visible through the windows of the envelopes. The case was settled for $935,000.
The post 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.