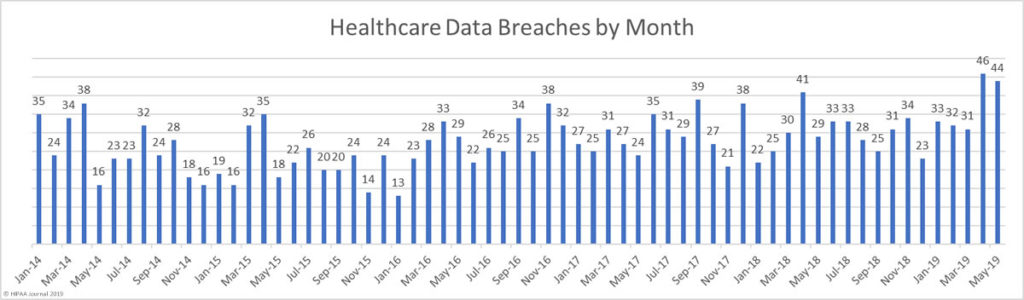
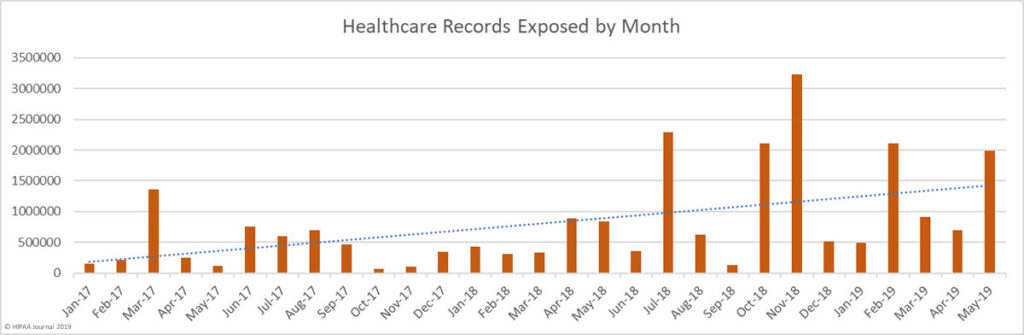
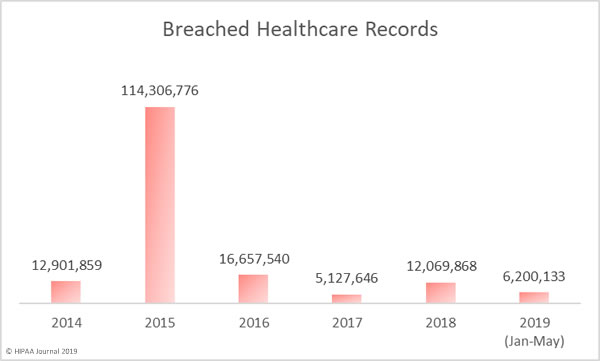
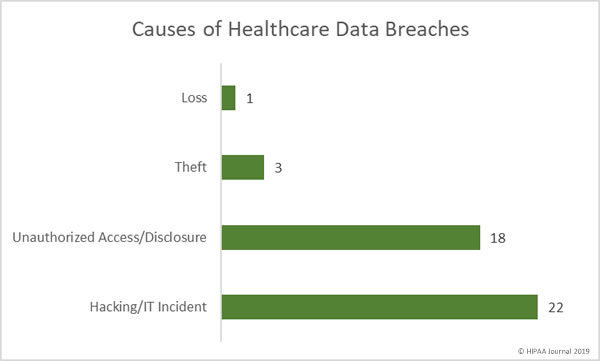
Cybercriminals are managing to find and exploit vulnerabilities to gain access to healthcare networks and patient data with increasing regularity. The past two months have been the worst and second worst ever months for healthcare data breaches in terms of the number of breaches reported.
Phishing attacks on healthcare organizations have increased and email is now the most common location of breached protected health information. However, a recent analysis of the data breaches reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) in the past 12 months has revealed servers to be the biggest risk. Servers were found to be involved in more than half of all healthcare data breaches.
Clearwater Cyberintelligence Institute (CCI) analyzed the 90 healthcare data breaches reported to OCR in the past 12 months. Those breaches resulted in the exposure, impermissible disclosure, or theft of the records of more than 9 million individuals.
The CCI analysis revealed 54% of all reported breaches of 500 or more healthcare records were in some way related to servers.
Servers house essential programs that are used across the healthcare organization. As a central repository of programs and data, they are an attractive target for hackers. Once access has been gained, data can be viewed, copied, altered, or deleted, systems can be sabotaged, and healthcare organizations can be subjected to extortion using ransomware.
CCI performed a risk analysis to determine high and critical risks facing health systems and hospitals. CCI determined 63% of all identified risks were related to the failure to adequately address vulnerabilities in servers.
The high number of server-related data breaches clearly shows that those flaws are being exploited by hackers to gain access to healthcare networks.
According to CCI, one of the most common server vulnerabilities is the failure to keep on top of user account management. When employees leave the company their accounts must be deleted. Dormant accounts are a major risk and are often used by malicious actors to access systems and mask their activities. CCI notes the risk increases with the number of accounts that are left dormant. The longer those accounts are left open, the greater the likelihood that at least one will be used for illicit or malicious purposes.
To address this risk, security controls should be implemented that automatically disable or delete accounts when the HR department changes the status of an employee. If that is not possible, CCI recommends conducting frequent, periodic reviews to ensure all unused accounts are disabled.
In an ideal world, an account would be disabled instantly. In practice, CCI recommends having the systems, policies, and procedures in place to ensure no account remains open for more than 48 hours after it is no longer required.
Reviews of system activity logs should also be conducted to determine whether dormant accounts have been used inappropriately or if any actively used accounts have been compromised or are being misused.
Excessive permissions on user accounts is another serious server vulnerability. Excessive permissions can result in accidental or deliberate access, alteration, or deletion of data. The failure to restrict access rights is also a violation of the HIPAA principle of least privilege.
CCI reports that the risk of excessive user permissions is highest in organizations that do not regularly review user permissions (43.6%), perform user activity reviews (43.6%), or when there is a lack of proper user account management (43.1%).
Regular reviews of user activity will help healthcare organizations to quickly identify anomalies in user data that could be indicative of account misuse or a cyberattack. The frequency of those reviews should be dictated by several factors, including staff turnover and the number of users. CCI suggests user permission and user activity log reviews at least every quarter for an organization with 100 or more users.
The post Vulnerabilities in Servers Behind Majority of Healthcare Data Breaches appeared first on HIPAA Journal.