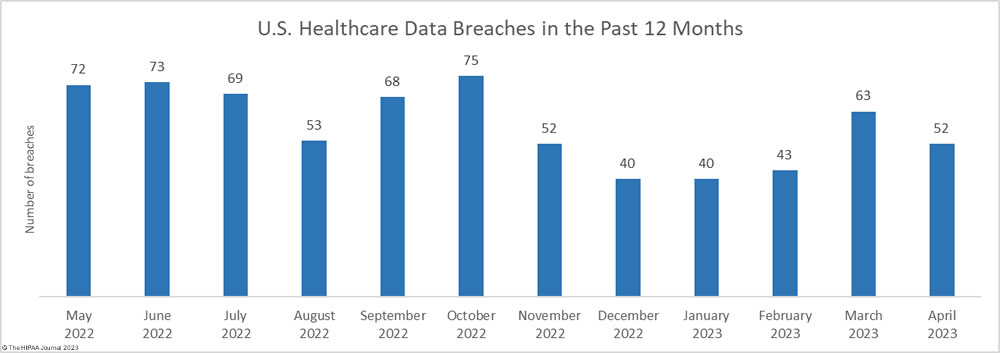
There was a 17.5% month-over-month fall in the number of reported healthcare data breaches with 52 breaches of 500 or more records reported to the HHS’ Office for Civil Rights (OCR) – less than the 12-month average of 58 breaches per month, and one less than in April 2022.
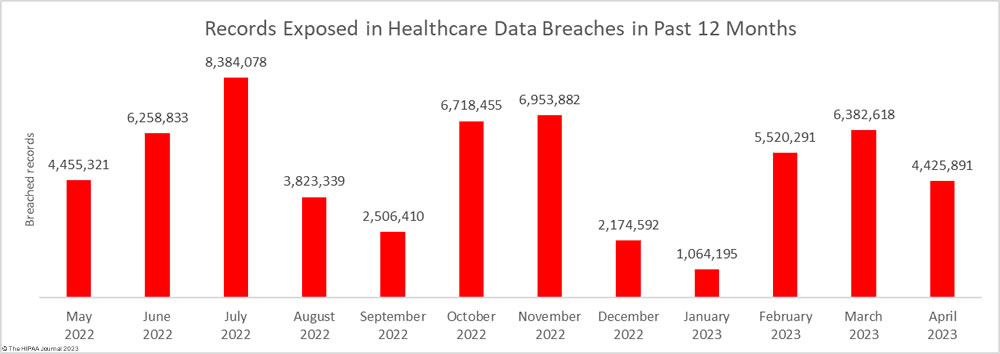
One of the largest healthcare data breaches of the year was reported in April, but there was still a significant month-over-month reduction in breached records, which fell by 30.7% to 4,425,891 records. The total is less than the 12-month average of 4.9 million records a month, although more than twice the number of records that were breached in April 2022.
Largest Healthcare Data Breaches Reported in April 2023
As previously mentioned, April saw a major data breach reported that affected 3,037,303 individuals – The third largest breach to be reported by a single HIPAA-covered entity so far this year, and the 19th largest breach to be reported by a single HIPAA-regulated entity to date. The breach occurred at the HIPAA business associate, NationsBenefits Holdings, and was a data theft and extortion attack by the Clop ransomware group involving the Fortra GoAnywhere MFT solution. 8 of the month’s 21 breaches of 10,000 or more records were due to these Clop attacks, including the top 5 breaches in April. Brightline Inc. was also hit hard by those attacks, which were reported separately for each covered entity client (9 reports). Together, the attacks on Brightline involved the PHI of more than 964,000 individuals.
18 of the 21 breaches of 10,000 or more records were hacking incidents. The remaining three breaches were unauthorized disclosures of protected health information, one due to tracking technologies and the other two due to mailing errors. While ransomware and data theft/extortion attacks dominated the breach reports, phishing, business email compromise, and other email account breaches are common, with 5 of the top 21 breaches involving hacked email accounts. End-user security awareness training is recommended to reduce susceptibility to these attacks and multifactor authentication should be implemented on all email accounts, ideally using phishing-resistant multifactor authentication.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Location of Breached Information |
Breach Cause |
| NationsBenefits Holdings, LLC |
FL |
Business Associate |
3,037,303 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| Brightline, Inc. |
CA |
Business Associate |
462,241 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| Brightline, Inc. |
CA |
Business Associate |
199,000 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| Brightline, Inc. |
CA |
Business Associate |
180,694 |
Network Server, Other |
Hacking and extortion (Fortra GoAnywhere MFT) |
| California Physicians’ Services d/b/a Blue Shield of California |
CA |
Business Associate |
61,790 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| MiniMed Distribution Corp. |
CA |
Healthcare Provider |
58,374 |
Network Server |
Unauthorized disclosure of PHI to Google and other third parties (Tracking code) |
| Brightline, Inc. |
CA |
Business Associate |
49,968 |
Network Server, Other |
Hacking and extortion (Fortra GoAnywhere MFT) |
| United Steelworkers Local 286 |
PA |
Health Plan |
37,965 |
Email |
Hacked email account |
| Retina & Vitreous of Texas, PLLC |
TX |
Healthcare Provider |
35,766 |
Network Server |
Hacking incident |
| Brightline, Inc. |
CA |
Business Associate |
31,440 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| Brightline, Inc. |
CA |
Business Associate |
21,830 |
Network Server |
Hacking and extortion (Fortra GoAnywhere MFT) |
| Iowa Department of Health and Human Services – Iowa Medicaid Enterprise (Iowa HHS-IME) |
IA |
Health Plan |
20,815 |
Network Server |
Hacking incident at business associate (Independent Living Systems)_ |
| Lake County Health Department and Community Health Center |
IL |
Healthcare Provider |
17,000 |
Email |
Hacked email account |
| Southwest Healthcare Services |
ND |
Healthcare Provider |
15,996 |
Network Server |
Hacking incident (data theft confirmed) |
| La Clínica de La Raza, Inc. |
CA |
Healthcare Provider |
15,316 |
Email |
Hacked email accounts |
| St. Luke’s Health System, Ltd. |
ID |
Healthcare Provider |
15,246 |
Paper/Films |
Mailing error |
| Two Rivers Public Health Department |
NE |
Healthcare Provider |
15,168 |
Email |
Hacked email account |
| Robeson Health Care Corporation |
NC |
Healthcare Provider |
15,045 |
Network Server |
Malware infection |
| Northeast Behavioral Health Care Consortium |
PA |
Health Plan |
13,240 |
Email |
Hacked email account (Phishing) |
| Centers for Medicare & Medicaid Services |
MD |
Health Plan |
10,011 |
Paper/Films |
Mailing error at business associate (Palmetto GBA) |
| Modern Cardiology Associates |
PR |
Healthcare Provider |
10,000 |
Network Server |
Hacking incident |
Causes of April 2023 Healthcare Data Breaches
Hacking and other IT incidents continue to dominate the breach reports, accounting for 36 of the month’s breaches (69.2%) and the vast majority of the breached records. Across those incidents, 4,077,019 healthcare records were exposed or stolen – 92.1% of the records that were breached in April. The average breach size was 119,914 records and the median breach size was 9,675 records.
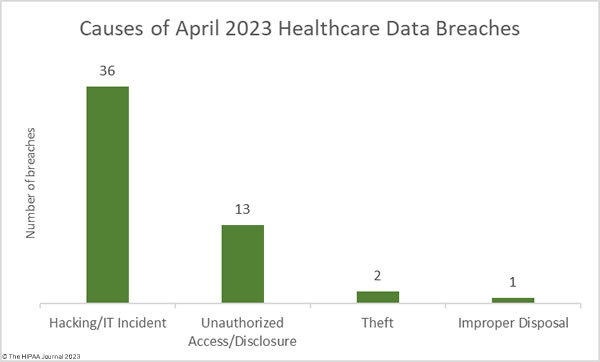
Ransomware attacks continue to be conducted by there has been a notable shift in tactics, with many ransomware gangs opting for data theft and extortion without encrypting files, as was the case with the attacks conducted by the Clop ransomware group which exploited a zero-day vulnerability in the Fortra GoAnywhere MFT solution. The BianLian threat group has previously conducted attacks using ransomware, but this year has been primarily conducting extortion-only attacks, which are quieter and faster. 12 of the month’s breaches (40%) involved hacked email accounts, highlighting the importance of security awareness training and multifactor authentication.
There were 13 unauthorized access/disclosure incidents in April, including a 58K-record incident involving tracking technologies that transferred sensitive data to third parties such as Google, instances of paper records not being secured, and PHI that had been exposed over the Internet. Across those 13 breaches, 105,155 records were impermissibly disclosed. The average breach size was 8,089 records and the median breach size was 1,304 records.
There were two theft incidents involving 3,321 records in total and one improper disposal incident. The improper disposal incident was reported as involving 501 records – a placeholder commonly used to meet the Breach Notification Rule reporting deadline when the total number of individuals affected has yet to be determined. As the chart below shows, the majority of incidents involved ePHI stored on network servers and in email accounts.
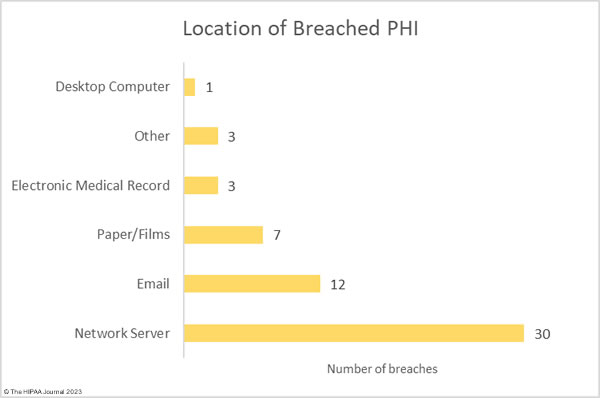
Where Did the Breaches Occur?
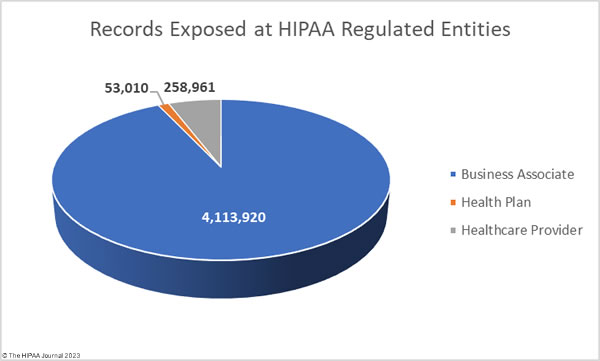
The raw data on the OCR breach portal shows the reporting entity, which in some cases is a HIPAA-covered entity when the breach actually occurred at a business associate. The breach portal shows 31 data breaches were reported by healthcare providers, 8 by health plans, and 13 by business associates. The charts below are based on where the breach occurred, rather than the entity that reported the data breach, to better reflect the extent to which data breaches are occurring at business associates.
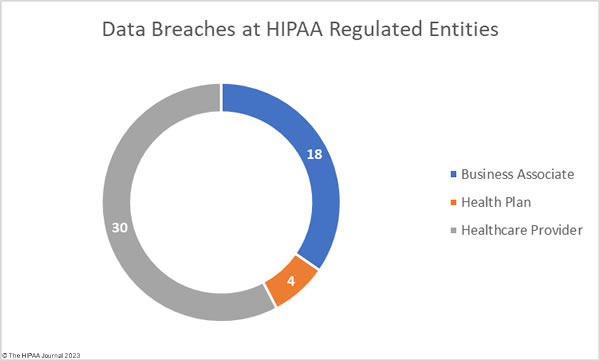
While healthcare providers were the worst affected HIPAA-regulated entity, the majority of the month’s breached records were due to data breaches at business associates.
Geographical Distribution of April 2023 Healthcare Data Breaches
Data breaches of 500 or more records were reported by HIPAA-regulated entities in 25 states and Puerto Rico, with California the worst affected state with 16 breaches, 9 of which were the same incident that was reported separately for each client by Brightline Inc., which is why the breach count was so high for California this month.
| State |
Breaches |
| California |
16 |
| Florida |
4 |
| New York & Pennsylvania |
3 |
| Illinois, Kentucky, Ohio, & Texas |
2 |
| Alabama, Arizona, Idaho, Iowa, Indiana, Maryland, Michigan, Minnesota, Nebraska, North Carolina, North Dakota, Oregon, Utah, Virginia, Washington, West Virginia, Wisconsin & Puerto Rico |
1 |
HIPAA Enforcement Activity in April 2023
No HIPAA enforcement actions were announced by OCR or state attorneys general in April 2023 to resolve violations of HIPAA and state laws, and no Health Breach Notification Rule enforcement actions were announced by the Federal Trade Commission.
The post April 2023 Healthcare Data Breach Report appeared first on HIPAA Journal.





