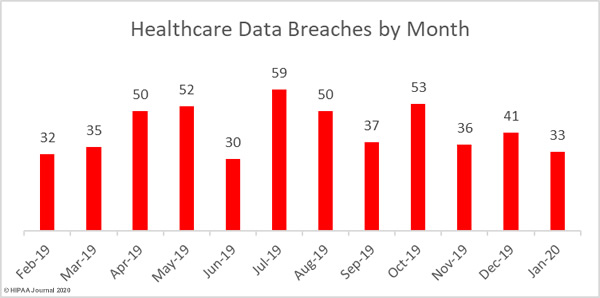
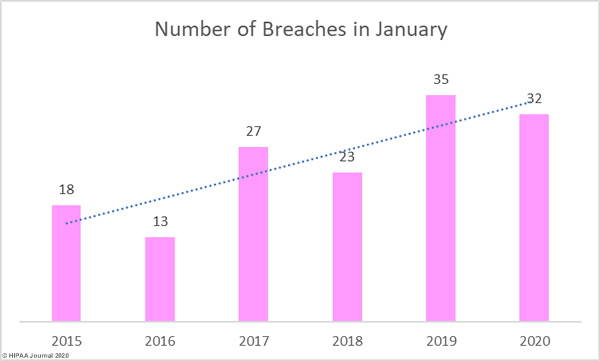
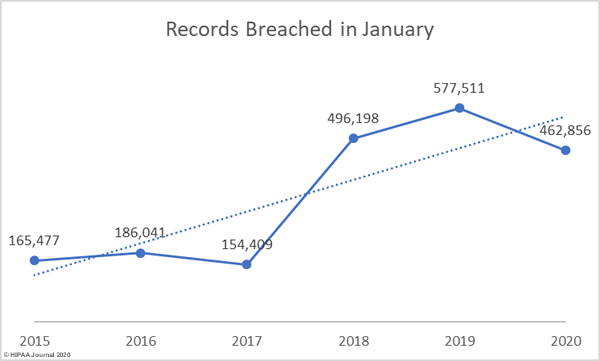
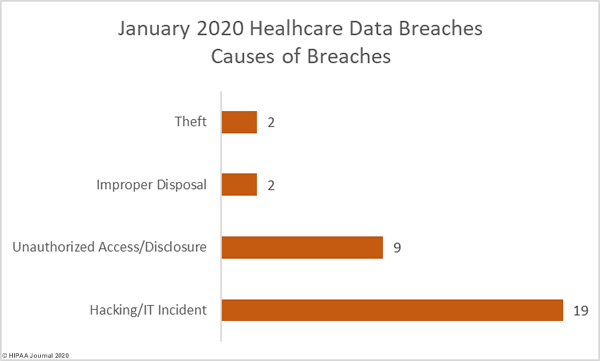
The healthcare industry is digitizing business management and data management processes and is adopting new technology to improve efficiency and cut costs, but that technology, in many cases, has been added to infrastructure, processes, and software from a different era and as a result, many vulnerabilities are introduced.
The healthcare industry is being targeted by cybercriminals who are looking for any chink in the armor to conduct their attacks, and many of those attacks are succeeding. The healthcare industry is the most targeted industry sector and one third of data breaches in the United States happen in hospitals.
According to the recently published 2020 Healthcare Security Vision Report from CyberMDX almost 30% of healthcare delivery organizations (HDOs) have experienced a data breach in the past 12 months, clearly demonstrating that the healthcare industry is struggling to address vulnerabilities and block cyberattacks.
Part of the reason is the number of difficult-to-secure devices that connect to healthcare network. The attack surface is huge. It has been estimated that globally there are around 450 million medical devices connected to healthcare networks and 30% of those devices are in the United States. That equates to around 19,300 connected medical devices and clinical assets per hospital in the United States. It is not uncommon for large hospitals to have more than 100,000 connected devices. On average, one in 10 devices on hospital networks are medical devices.
The report reveals 80% of device makers and HDOs say medical devices are difficult to secure due to a lack of knowledge on how to secure them, a lack of training on secure coding practices, and pressure to meet product deadlines.
71% of HDOs say they do not have a comprehensive cybersecurity program that includes medical devices, and 56% believe there will be a cyberattack on their medical devices in the next 12 months. That figure jumps to 58% when you ask medical device manufacturers. Even if an attack occurred, only 18% of HDOs say they are confident that they would be able to detect such an attack.
45% of Medical Devices Vulnerable to Flaws Such as BlueKeep
CyberMDX’s analysis revealed 61% of medical devices are exposed to some degree of cyber risk. 15% are exposed to BlueKeep flaws, 25% are exposed to DejaBlue flaws, and 55% of imaging devices run on outdated software that is vulnerable to exploits such as BlueKeep and DejaBlue. Overall, around 22% of Windows devices on hospital networks are vulnerable to BlueKeep.
BlueKeep and DejaBlue are vulnerabilities that can be exploited via Remote Desktop Protocol (RDP). The flaws can be exploited remotely and allow an attacker to take full control of vulnerable devices. BlueKeep is also wormable, so malware could be created that could spread to other vulnerable devices on a network with no user interaction required.
BlueKeep affects older Windows versions – Windows XP to Windows 7 and Windows Server 2003 to 2008 R2 – but many medical devices run on those older operating systems and have not been updated to protect against exploitation. DejaBlue affects Windows 7 and later versions.
Even Linux-based operating systems are vulnerable. Approximately 15% of connected hospital assets and 30% of medical devices are vulnerable to a flaw known as SACK Panic. It has been estimated that around 45% of medical devices are vulnerable to at least one flaw.
Prompt Patching is Critical, But That’s Not Straightforward
CyberMDX’s research found that 11% of HDOs don’t patch their medical devices at all and when patches are applied, the process is slow. 4 months after a vulnerability as serious as BlueKeep is discovered, an average hospital will only have patched around 40% of vulnerable devices.
The situation could actually be far worse, as the report reveals 25% of HDOs do not have a full inventory of their connected devices and an additional 13% say their inventory is unreliable. 36% do not have a formal BYOD policy and CyberMDX says a typical hospital has lost track of around 30% of its connected devices.
Patching medical devices is no easy task. “Where vulnerabilities concern unmanaged devices, there is no easy way to identify the relevant patch level for each device and no way to centrally push patches (through the active directory and SCCM) to devices distributed throughout the organization,” explained CyberMDX. “For these devices, technicians must individually investigate and manually attend the affected devices.”
Alarmingly, even though medical devices are vulnerable to attack, a majority of HDOs neglect granular network segmentation or segment their networks for reasons other than security, so when network segmentation is used, segments contain a variety of different devices with some connections open to the internet.
If flaws are exploited, many HDOs would struggle to detect an attack. More than a third of HDOs do not continuously monitor their connected devices and a further 21% identify, profile, and monitor their devices manually.
So, What is the Solution?
Improving the security of medical devices is no easy task, as CyberMDX explains. It requires “continuous review of configuration practices, segmentation, network restrictions, appropriate use, credential management, vulnerability monitoring, patching & updating, lifecycle management, recall tracking, access and role controls, compliance assurance, pen testing, live context-aware traffic monitoring & analysis, oversight of partner and third-party security practices, and more.” Further, “If you don’t know what devices you have networked, you won’t be able to understand their individual attack vectors.”
Improving security is certainly a daunting task, but the goal is not to make your organization 100% secure, as that would be an impossible goal. The aim should be to address the most important issues and to significantly reduce the attack surface.
“By more clearly defining lifecycle-wide security responsibilities and expectations with your vendors, by restricting functionally unnecessary in-VLAN communications, by investing in staff-wide cyber training, by normalizing basic network hygiene practices (like password and access management, patching & updating, etc.), and by tweaking security policies (at the NAC or firewall level) specifically for monitors, infusion pumps, and patient tracking devices, you can dramatically shrink your attack surface in short order,” suggest CyberMDX.
The post Alarming Number of Medical Devices Vulnerable to Exploits Such as BlueKeep appeared first on HIPAA Journal.