HIPAA compliance for business associates has acquired greater significance since the publication of proposals to align the HIPAA Security Rule more closely with HHS’ Healthcare Sector Cybersecurity Strategy – among which is a requirement for covered entities to obtain verifications from business associates that they have implemented measures to protect electronic Protected Health Information.
The implication of this requirement – if finalized – is that covered entities will only be permitted to contract services from business associates that can demonstrate compliance with HIPAA. However, demonstrating compliance with HIPAA is not straightforward for many business associates because what HIPAA compliance for business associates consists of can vary considerably depending on the type of service provided to or on behalf of a covered entity.
Despite the variety of compliance requirements, some areas of HIPAA compliance are common to all business associates. Business associates that can demonstrate compliance with these common areas via independent certification are likely to have a competitive advantage against other service providers to the healthcare industry. This article explains what these common areas of compliance are and what business associates need to do to comply with HIPAA.
What is a HIPAA Business Associate?
A HIPAA business associate is an organization, or a person who is not a member of a covered entity’s workforce, that provides services to or on behalf of a covered entity which enable the business associate to have “persistent access” to Protected Health Information (PHI). Examples of HIPAA business associates include medical billing service providers, software providers (including Managed Service Providers), and accreditation organizations with access to PHI.
There are exceptions to this definition of a HIPAA business associate. Some providers of healthcare and payment services, and organizations or persons for whom access to PHI is incidental or transient, do not qualify as HIPAA business associates. Researchers also do not qualify as HIPAA business associates when PHI is disclosed for research because the purpose of the disclosure is not regulated by the HIPAA Administrative Simplification Regulations.
When an organization or person qualifies as a HIPAA business associate, they are required to comply with all applicable standards, requirements, and implementation specifications of the HIPAA Administrative Simplification Regulations. Each HIPAA business associate must determine which standards, requirements, and implement specifications are applicable to the service being provided, and implement policies, procedures, and other measures as necessary.
Why HIPAA Compliance for Business Associates is Important
When the HIPAA Privacy Rule was published in 2002, covered entities were required to obtain “satisfactory assurances” HIPAA business associates would only use PHI disclosed to them for the purposes of the service being provided, would safeguard the information from misuse, and would help the covered entity comply with some of their HIPAA Privacy Rule obligations by providing a service that enabled the covered entity to carry out its functions compliantly.
However, until the passage of the HITECH Act in 2009, HIPAA business associates could not be held accountable for the failure to uphold their satisfactory assurances. The HITECH Act made HIPAA business associates and their downstream subcontractors directly liable for compliance with certain requirements of the HIPAA Rules. The direct liability of HIPAA business associates and downstream subcontractors was codified in the HIPAA Omnibus Final Rule in 2013.
“Where provided, the standards, requirements, and implementation specifications adopted under this subchapter apply to a business associate.” (§160.102(b))
More recently, The Department of Health and Human Services (HHS) published a Notice of Proposed Rulemaking in January 2025 which, when finalized, will require covered entities to obtain written verifications from their HIPAA business associates that each HIPAA business associate has deployed and is operating technical safeguards that protect the confidentiality, integrity, and availability of PHI maintained on electronic information systems.
As the Notice of Proposed Rulemaking has the objective of aligning the HIPAA Security Rule with HHS’ Cybersecurity Performance Goals, and as compliance with HHS’ Cybersecurity Performance Goals may also become a condition of participation in Medicare and Medicaid, verifiable HIPAA compliance for business associates may soon become a condition for providing services to or on behalf of covered entities in the healthcare industry.
The Responsibilities of HIPAA Business Associates
The responsibilities of HIPAA business associates are much the same as they were in 2002 – only use PHI for the purposes of the service being provided, safeguard the information from misuse, and support the covered entity’s functions by providing a HIPAA compliant service. HIPAA business associates may use PHI for internal management and administration purposes, but there must be a documented chain of custody if PHI is disclosed to downstream subcontractors.
How HIPAA business associates fulfil their responsibilities depends on their existing status. For example, a software provider that wants to break into the healthcare market may only now be starting their journey to HIPAA compliance, while a Managed Service Provider with existing healthcare clients may already be fulfilling some responsibilities of HIPAA business associates – but not all – and may need to review and revise its operations to achieve full HIPAA compliance.
For the benefit of organizations and persons starting their journeys to HIPAA compliance, this article focuses on the common areas of HIPAA compliance for business associates from start to finish. Existing HIPAA business associates can use this article to identify gaps in compliance activities, while those with additional or uncommon HIPAA compliance responsibilities should seek advice from an independent compliance professional.
The Basics
Do You Qualify as a HIPAA Business Associate?
The first thing to determine is whether the service being provided qualifies you as a HIPAA business associate or subcontractor. If the service does not involve disclosures of PHI by a covered entity or upstream business associate, if disclosures of PHI are incidental or transient, or if the service is exempted under the HIPAA definition of a business associate, it is not necessary to comply with HIPAA (although other privacy and security regulations may apply).
Are disclosures of PHI involved?
Examples of when a service does not involve disclosures of PHI by a covered entity to a third party include when an organization provides email services to a healthcare provider, but the healthcare provider does not use email service to send, receive, or store PHI. Alternatively, an organization could provide software for an on-premises email server, but the organization does not have access to PHI sent, received, stored, or transmitted by the on-premises email server.
Are disclosures of PHI incidental?
Incidental disclosures of PHI are usually considered to be disclosures secondary to permitted disclosures of PHI that cannot reasonably be prevented. In the context of HIPAA compliance for business associates, incidental disclosures are when a third party whose services do not ordinarily involve uses and disclosures of PHI has unintended access to PHI. Examples could include a landscape gardener who recognizes a patient in the garden of a nursing home.
Is access to PHI transient?
Transient disclosures of PHI are disclosures to transmission-only services that do not have repeated or routine access to PHI. Example of third parties that do not qualify as a HIPAA business associate because their access to PHI is transient include the US Postal Service and other private couriers such as Fed-Ex, UPS, and DHL. Internet Service Providers also do not qualify as HIPAA business associates when they are used for transmission purposes only.
Is the service exempted?
Several types of services are exempted from qualifying as HIPAA business associates when the service being provided on behalf of a covered entity is for the treatment of a patient (i.e., medical specialists, laboratories, etc.) or for payment processing. However, the exemption for payment processing only applies to financial institutions providing their “normal” services for customers – not to developers and vendors of payment processing applications.
If You Qualify as a HIPAA Business Associate … …
If you qualify as a HIPAA business associate, there are several activities you must undertake before providing a service for or on behalf of a covered entity. The first is to appoint a HIPAA Privacy Officer and a HIPAA Security Officer. The HIPAA Privacy Officer is responsible for ensuring compliance with all applicable HIPAA Administrative Simplification Requirements, while the HIPAA Security Officer is responsible for implementing the HIPAA Security Rule Safeguards.
Both roles can be outsourced, designated to existing employees, or – in smaller organizations – designated to the same employee. However, other than in exceptional circumstances, it is important to appoint both roles. It is rare that HIPAA compliance for business associates can be accomplished complying solely with the requirements of the HIPAA Security Rule. In most cases a more holistic approach to HIPAA compliance for business associates is necessary.
Business Associate Agreements
Before any PHI is disclosed to a HIPAA business associate, upstream covered entities must enter into a HIPAA Business Associate Agreement with the business associate. The Agreement establishes the permissible uses and disclosures of PHI by the business associate, how the business associate will respond to patients exercising their HIPAA rights, and responsibility for reporting disclosures of PHI not permitted by the Agreement, security incidents, and data breaches.
If your organization (as a HIPAA business associate) is using a service provided by a third party subcontractor (i.e., Microsoft 365) in the provision of the service to the covered entity, and PHI will be disclosed to the downstream subcontractor, your organization must also enter into a Business Associate Agreement with the downstream subcontractor. Some subcontractors (i.e., Microsoft) have a standard Business Associate Agreement that your organization must agree to.

Determine which standards apply
Determining which standards of HIPAA apply to a service is one of the most complicated areas of HIPAA compliance for business associates. This is because, while most business associates are aware the service has to comply with the Administrative, Physical, and Technical Safeguards of the HIPAA Security Rule, many overlook the Security Rule’s General Requirements – including the requirement to:
“Protect against any reasonably anticipated uses or disclosures [of PHI] that are not permitted or required under subpart E of this part (the HIPAA Privacy Rule).” (§164.306(a))
In addition to being aware of which uses and disclosures of PHI are permitted by the HIPAA Privacy Rule – and in what circumstances – and implementing policies and procedures to prevent violations of the HIPAA Privacy Rule, business associates may also have to prepare for individuals exercising their HIPAA rights and security incident notifications – the responsibility for which may be subject to the terms of upstream and downstream Business Associate Agreements.
Map the flow of PHI in all formats
One of the factors that can affect which standards of HIPAA apply is how PHI is created, received, maintained, or transmitted by the organization. For example, if PHI is received verbally, written down, and then transferred to an electronic system for storage, it will be necessary to have procedures in place to compliantly dispose of the media on which the PHI was written down as well as the final disposition of PHI stored on the electronic system.
Mapping the flow of PHI in all formats will also enable HIPAA business associates to determine when an individual’s consent or authorization is required prior to further disclosing PHI (for example, Substance Use Disorder records), or when an attestation is required from the recipient of PHI that the information will not be used to investigate or impose liability on any person for the mere act of seeking, obtaining, providing, or facilitating lawful reproductive health care.
Conduct Risk Analyses
Determining which HIPAA standards apply and mapping how PHI flows through the organization will help HIPAA business associates better prepare for a risk analysis – a process required by the HIPAA Security Rule, but also potentially necessary for PHI in all formats depending on the nature of the service(s) being provided to a covered entity. HIPAA risk analyses should be based on guidance published by HHS and adjusted as necessary to accommodate uncommon circumstances.
Identify and document potential vulnerabilities and threats to PHI
Business associates are required to identify and document vulnerabilities which, if triggered by a reasonably anticipated threat, would create a risk of unauthorized access to – or disclosure of – PHI. All vulnerabilities and reasonably anticipated threats from both internal and external sources must be documented.
Assess the capabilities of existing policies and security measures
Most organizations will already have some policies and security measures in place to support HIPAA compliance for business associates. However, business associates should assess whether the existing policies and security measures are sufficient to reduce identified vulnerabilities and risks to a reasonable and appropriate level.
Determine the likelihood and impact of a threat occurrence
It is not possible to eliminate all risks to the confidentiality, integrity, and availability of PHI, but by determining the likelihood and impact of a threat occurrence, HIPAA business associates should be able to prioritize which vulnerabilities should be addressed either by implementing additional technical safeguards or the provision of workforce training.
Determine the level of risk and potential consequences
Determining the level of risk to PHI and the potential consequences of a data breach will help HIPAA business associates with the development of contingency plans, data backup plans, and emergency mode operation plans (as required by the Administrative Safeguards) to ensure the availability of covered entities’ PHI during a HIPAA security incident
Implement additional policies and security measures as required
If existing policies and security measures are not sufficient to reduce identified vulnerabilities and risks to a reasonable and appropriate level, business associates are required to implement additional policies and security measures as required, and document the reasons for them based on the previous steps in the risk analysis process.
Reassess periodically and in response to a regulatory or operational change
A risk analysis is required every time there is a change in regulations or work practices, and when new technology is implemented. If none of these events occur, HIPAA business associates must still perform a periodic technical and non-technical evaluation to ensure policies and security measures remain effective and in compliance with HIPAA.
Common Safeguards
Because business associates must implement administrative, physical, and technical safeguards based on the outcome of a risk analysis, there is no one-size-fits-all guidance for what safeguards must be implemented in order to accomplish HIPAA compliance for business associates. Nonetheless, there are several common safeguards that must be implemented in order for HIPAA business associates to comply with HIPAA.
Physical security
Secure locations in which PHI in all formats is stored and restrict physical access to systems on which PHI is maintained. It may also be necessary to secure workstations and other devices or media which can access PHI depending on whether PHI is stored locally on the workstations, devices, and media, and what other technical safeguards exist to prevent unauthorized access.
Unique user IDs
Although HIPAA does not stipulate password requirements, business associates are required to assign unique user IDs for all members of the workforce. If user IDs consist of a username and password, it is important to enforce the use of strong passwords and be conscious that the mandatory use of MFA is included in the proposed update to the HIPAA Security Rule.
Minimum Necessary
Other than in exempted circumstances, uses and disclosures of PHI must be limited to the minimum necessary to fulfil the purpose of a use or disclosure. This means assigning different access permissions to systems depending on their functions, and different access permissions to workforce members depending on their roles.
Maintain audit logs
One of the purposes of assigning unique user IDs is to create audit logs and monitor access to PHI by workforce members. For this reason, it is important workforce members are instructed not to share login credentials with other members of the workforce. The audit logs should also monitor access to PHI by applications and be configured to flag anomalies that could indicate unauthorized access.
Workforce training
A common issue with HIPAA compliance for business associates is that the security awareness training provided by business associates is generic. According to the General Requirements of the HIPAA Security Rule, workforce training must be designed to protect against reasonably anticipated uses or disclosures of PHI not required or permitted by the HIPAA Privacy Rule.
Sanctions Policy
Business associates are required to apply sanctions against workforce members for any violation of the HIPAA Privacy Rule or for any violation of a policy implemented by the business associate to comply with the HIPAA Security Rule. Business associates that do not have, do not explain, or do not enforce a sanctions policy are themselves in violation of HIPAA.
Incident Management Preparation
According to §164.304 of the HIPAA Security Rule, the definition of a HIPAA security incident is any “attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system.” The reason that unsuccessful security incidents must be monitored is to identify trends in failed access attempts in order to identify future potential risks to the security of PHI.
System configurations
In order to monitor unsuccessful security incidents, systems should be configured where it is possible to automatically detect and log events such as unsuccessful brute force attacks on log-in credentials, pings, and scans looking for undefended network ports. Anti-virus software and email systems should also be monitored for increasing volumes of detected malware and spam emails.
Reporting procedures
Procedures should also be developed for members of the workforce to report incidents that have evaded detection by security software or that have resulted from their own actions. In some cases, it can be beneficial to implement a system that facilitates anonymous reports to ensure that workforce members report an incident before it develops into a more serious event.
Incident management plan
Business associates must develop an incident management plan that includes incident monitoring, tracking, handling, and response for each type of incident. The plan must be documented and include the procedures for determining whether an incident is notifiable to an upstream covered entity. This can depend on the content of the Business Associate Agreement.
Incident preparedness testing
The incident management plan must be tested periodically for each type of incident and revised as necessary if vulnerabilities are discovered or if an analysis of detected unsuccessful security incidents identifies an increasing incident type. It may also be necessary to test workforce members on their abilities to identify and report incidents using a safe or sandboxed environment.
Procedures for receiving notifications
If a HIPAA business associate uses services provided by a downstream subcontractor, and the Business Associate Agreement with the downstream subcontractor specifies the business associate must be notified of security incidents and data breaches, the business associate must have procedures in place for receiving notifications (i.e., a point of contact, the method of notification, etc.).
Procedures for making notifications
Procedures must also be in place for notifying upstream covered entities when a HIPAA security incident or data breach occurs. Depending on the content of the Business Associate Agreement with the upstream covered entity, it may also be necessary to have procedures in place to notify affected individuals and HHS’ Office for Civil Rights in the event of a data breach.
Documentation and Reviews
One of the most important elements of HIPAA compliance for business associates is documentation. The accurate documentation of how PHI flows through the organization, risk analyses, and policies and procedures to support HIPAA compliance are essential. It is also important that all HIPAA training is documented as well as any sanctions imposed for violations of HIPAA. Business Associate Agreements and breach notifications must also be documented.
Organized documentation implies operational efficiency, which can help build trust in upstream covered entities. Organized documentation also makes it easier to keep on top of periodic reviews and evaluations. In addition, although documentation alone will not absolve a business associate from liability in the event of an avoidable HIPAA violation, organized documentation provides visible evidence of a business associate’s good faith effort to be HIPAA compliant.
It is important for certain documents to be reviewed periodically (risk analyses, incident management plans, etc.). However, HIPAA documentation is not the only regulatory requirements business associates may have to comply with and it is advisable to implement a policy management platform that not only manages HIPAA documentation and reviews, but also other documentation required by other federal and state agencies (i.e., OSHA, CMS, etc.).
The Strategic Advantage of HIPAA Compliance for Business Associates
HIPAA compliance is often seen as a legal obligation, but for business associates, it can also serve as a strategic advantage. By embracing HIPAA standards, demonstrating a commitment to safeguarding PHI via independent certification, and aligning HIPAA compliance activities with broader privacy and security frameworks, business associates not only fulfill their HIPAA compliance responsibilities but can also enhance their reputation and unlock growth opportunities.
Demonstrating compliance with applicable HIPAA Administrative Simplification Regulations via white papers, case studies, and independent certifications positions HIPAA business associates as reliable and attractive partners. This can serve as a differentiator in the healthcare industry when a compliance-certified HIPAA business associate is compared to other vendors and service providers – opening doors to business opportunities, contracts, and collaborations.
Business associates that invest in HIPAA compliance are better positioned to adapt to new laws and industry standards. The processes and systems established for HIPAA compliance often lay the groundwork for meeting future regulatory requirements, ensuring long-term sustainability and success. For those willing to embrace the challenges and opportunities of HIPAA compliance for business associates, the rewards extend far beyond meeting regulatory requirements – they lead to lasting business growth and innovation.
The post HIPAA Compliance for Business Associates appeared first on The HIPAA Journal.

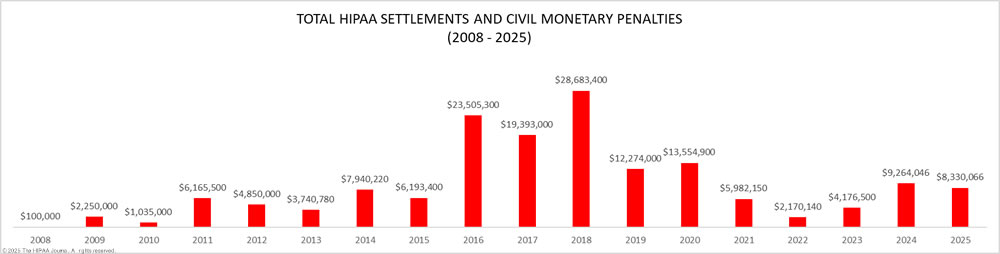
 In this article, we provide a detailed explanation of HIPAA violation fines that have been imposed on HIPAA-regulated entities found to have violated the HIPAA Rules.
In this article, we provide a detailed explanation of HIPAA violation fines that have been imposed on HIPAA-regulated entities found to have violated the HIPAA Rules.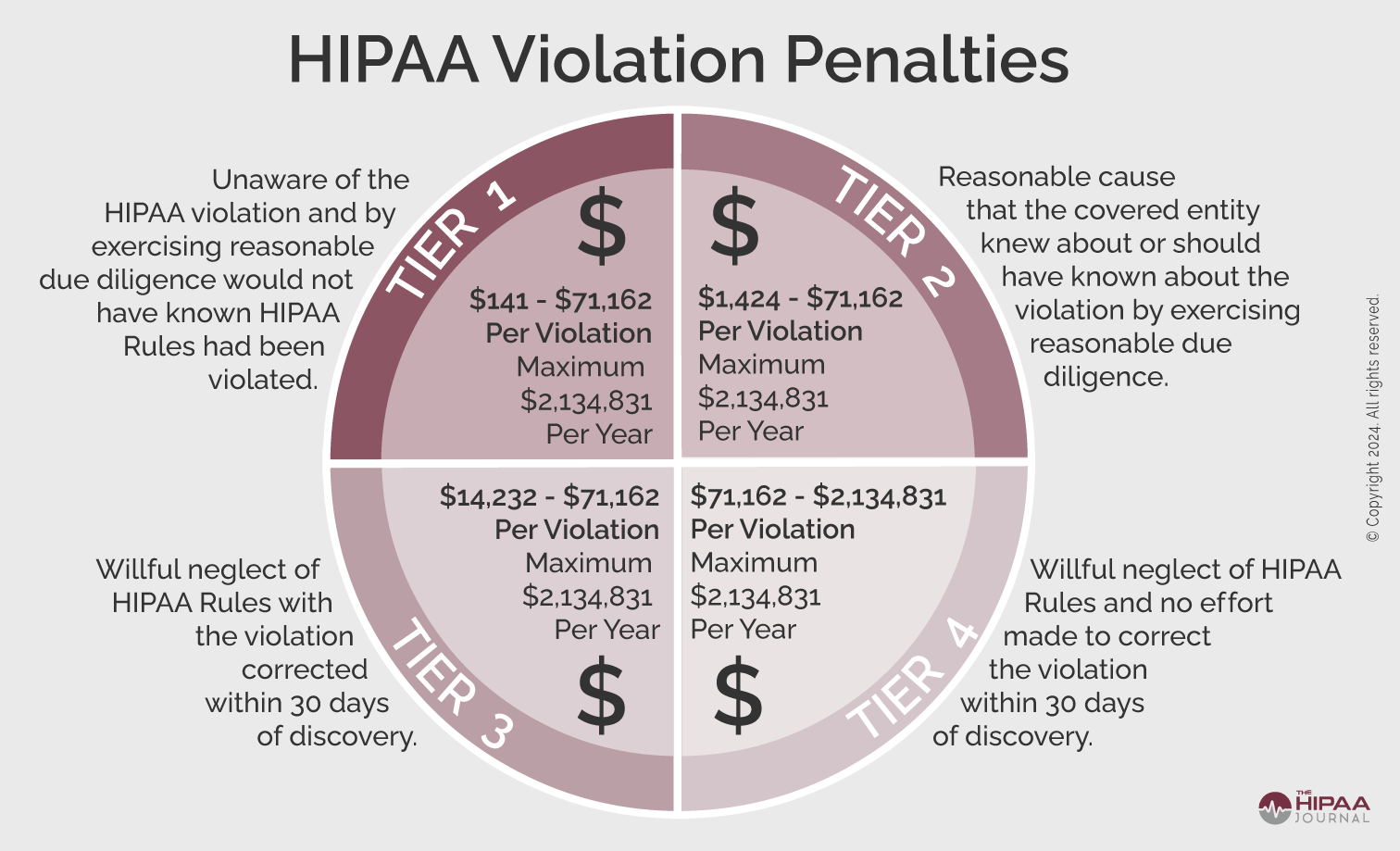


 In 2025, 95% of OCR HIPAA fines cited missing or deficient HIPAA risk assessments as a core basis for enforcement.
In 2025, 95% of OCR HIPAA fines cited missing or deficient HIPAA risk assessments as a core basis for enforcement. Liam Degnan brings more than eight years of experience in risk management, SaaS sales, and healthcare compliance. As Compliancy Group’s Senior Solutions Engineer, he advises healthcare decision-makers, healthcare providers, and medical vendors. He speaks on a variety of platforms and topics, with an emphasis on simplifying HIPAA, OSHA, SOC 2, and other healthcare compliance regulations.
Liam Degnan brings more than eight years of experience in risk management, SaaS sales, and healthcare compliance. As Compliancy Group’s Senior Solutions Engineer, he advises healthcare decision-makers, healthcare providers, and medical vendors. He speaks on a variety of platforms and topics, with an emphasis on simplifying HIPAA, OSHA, SOC 2, and other healthcare compliance regulations.