The sharp drop in healthcare data breaches seen in May proved to be short lived, with June seeing a major increase in data breaches. In June, 52 breaches were reported by HIPAA covered entities and business associates. That represents an 85.71% month-over-month increase in reported breaches.
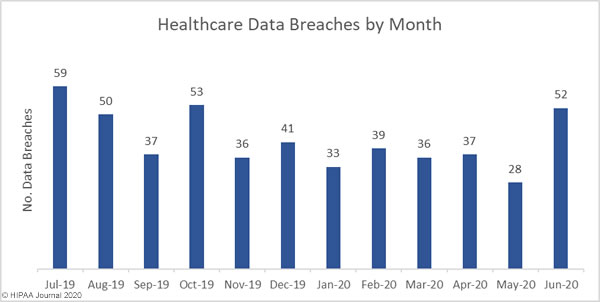
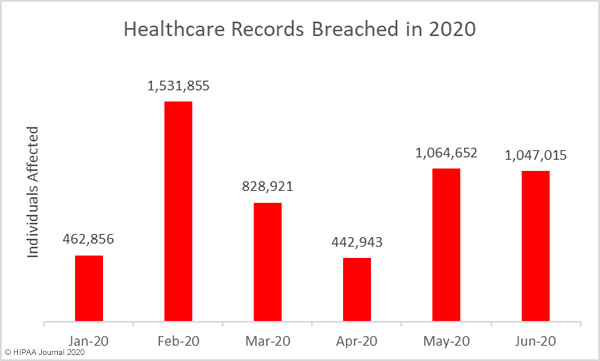
The number of individuals impacted by healthcare data breaches changed little despite the large increase in breaches, with a month-over-month fall of 1.65% to 1,047,015 records, which is well above the 2020 monthly average of 896,374 breached records.
Largest Healthcare Data Breaches in June 2020
The largest healthcare data breach reported by a single entity in June affected the Texas billing and collections agency, Benefit Recovery Specialists, Inc. (BRS) Malware was detected on its systems that potentially gave unauthorized individuals access to the protected health information of more than a quarter of a million people.
There was, however, a much larger data breach reported in June that affected more than 365,000 individuals but was reported individually by each entity affected by the breach. Magellan Health suffered a ransomware attack that also affected at least 9 healthcare providers, health plans, and business associates, specifically Merit Health Insurance Company, Magellan Complete Care of Florida, the University of Florida Health Jacksonville, Magellan Healthcare in Maryland, Magellan Rx Pharmacy, National Imaging Associates, UF Health Shands, UF Health, and Magellan Complete Care of Virginia. The ransomware attack ranks as the the third largest healthcare data breach so far in 2020.
| Name of Covered Entity |
Covered Entity Type |
Type of Breach |
Individuals Affected |
| Benefit Recovery Specialists, Inc. |
Business Associate |
Hacking/IT Incident |
274,837 |
| Merit Health Insurance Company |
Health Plan |
Hacking/IT Incident |
102,748 |
| Magellan Complete Care of Florida |
Health Plan |
Hacking/IT Incident |
76,236 |
| Healthcare Fiscal Management Inc. |
Business Associate |
Hacking/IT Incident |
58,000 |
| UF Health Jacksonville |
Healthcare Provider |
Hacking/IT Incident |
54,002 |
| Magellan Healthcare |
Business Associate |
Hacking/IT Incident |
50,410 |
| Providence Health Plan |
Health Plan |
Unauthorized Access/Disclosure |
49,511 |
| American Medical Technologies |
Healthcare Provider |
Hacking/IT Incident |
47,767 |
| Oral and Maxillofacial Surgery Associates, P.A. |
Healthcare Provider |
Hacking/IT Incident |
35,498 |
| City of Philadelphia |
Health Plan |
Hacking/IT Incident |
33,376 |
| Magellan Rx Pharmacy |
Healthcare Provider |
Hacking/IT Incident |
33,040 |
| Cano Health |
Healthcare Provider |
Hacking/IT Incident |
28,268 |
| National Imaging Associates |
Business Associate |
Hacking/IT Incident |
22,560 |
| Legacy Community Health Services |
Healthcare Provider |
Hacking/IT Incident |
19,000 |
| Human Affairs International of California |
Business Associate |
Hacking/IT Incident |
15,843 |
| UF Health Shands |
Healthcare Provider |
Hacking/IT Incident |
13,146 |
| North Shore Pain Management |
Healthcare Provider |
Hacking/IT Incident |
12,472 |
| Choice Health Management Services, LLC |
Business Associate |
Hacking/IT Incident |
11,650 |
| Iowa Total Care, Inc. |
Health Plan |
Unauthorized Access/Disclosure |
11,581 |
| The Kroger Co., for itself and its affiliates and subsidiaries |
Healthcare Provider |
Hacking/IT Incident |
10,974 |
Causes of June 2020 Healthcare Data Breaches
There were 37 reported hacking/IT incidents in June, which accounted for 71.15% of the month’s breaches and 91.14% of records breached in June. 957,082 records were exposed or stolen in those breaches. The average breach size was 25,867 records and the median breach size was 9,271 records.
There were 11 unauthorized access/disclosure incidents reported in June that impacted 85,580 individuals. The average breach size was 7,780 records and the median breach size was 1,650 records. There were 4 loss/theft incidents reported that impacted 4,353 individuals. The average breach size was 1,088 records and the median breach size was 910 records.

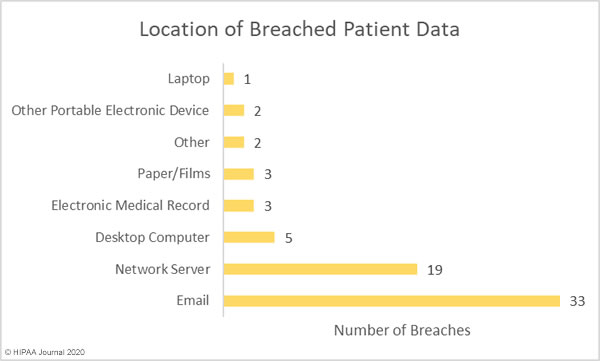
The most common location of breached protected health information was email. 63.46% of the month’s breaches involved ePHI stored in emails and email attachments, with 36.53% of breaches involving network servers. The majority of the email breaches were due to phishing attacks, with the network server breaches mostly involving malware and ransomware.
June 2020 Healthcare Data Breaches by State
Data breaches of 500 or more record were reported by HIPAA-covered entities and business associates in 21 states. California was the worst affected state with 9 breaches, followed by Florida with 7, Texas with 5, Maryland and New York with 4, and three in Illinois.
There were two breaches in each of Arkansas, North Carolina, Ohio, Oregon, and Pennsylvania, and one breach in each of Colorado, Connecticut, Iowa, Kentucky, Massachusetts, Michigan, Missouri, South Carolina, Tennessee, and Utah.
Healthcare Data Breaches by Covered Entity Type
Healthcare providers were the worst affected covered entity in June with 33 reported data breaches. There was an increase in health plan data breaches with 9 reported incidents, and also an increase in business associate breaches. While there were 10 breaches reported by business associates, a further 7 breaches involved business associates but were reported by the covered entity.

HIPAA Enforcement in June 2020
There were no HIPAA enforcement actions announced by state attorneys general or the HHS’ Office for Civil Rights in June 2020. The HHS has stated that it is prepared to be flexible with HIPAA investigations during the pandemic, so the lack of enforcement actions so far in 2020 may not be due to any reduction in enforcement, there may just be a delay in imposing penalties until the COVID-19 pandemic is brought under control.
On July 23, 2020, the Secretary of the Department of Health and Human Services, Alex Azar, announced that the nationwide public health emergency has been renewed for a further 90 days so OCR’s Notices of Enforcement Discretion covering good faith uses and disclosures of PHI in relation to telehealth and the operation of COVID-19 testing centers, and the waivers under Section 1135(b)(7) of the Social Security Act remain in effect.
The post June 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.




