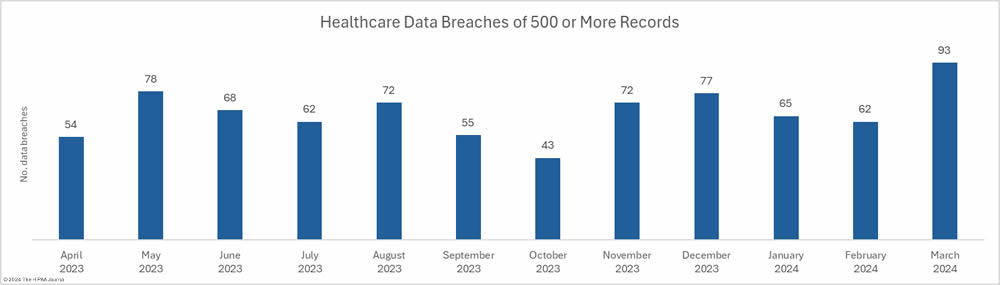
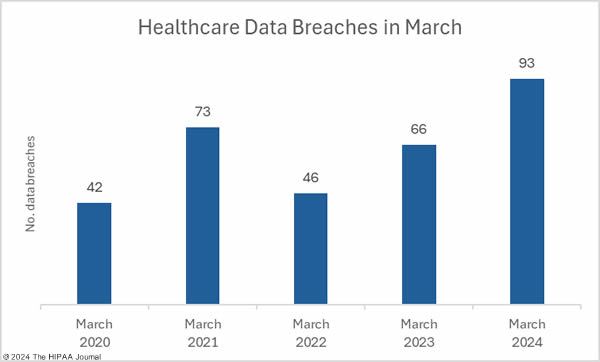
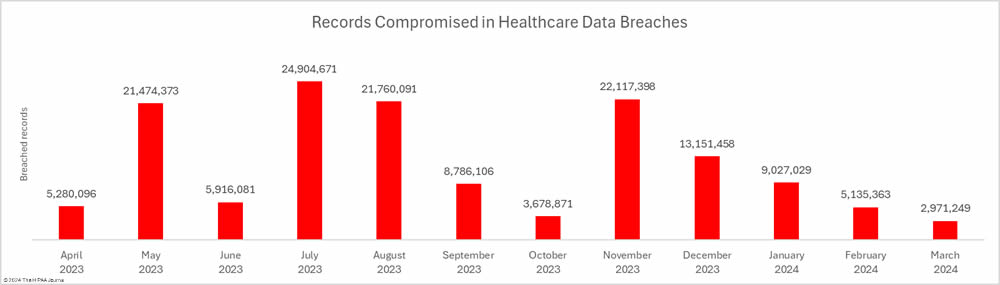
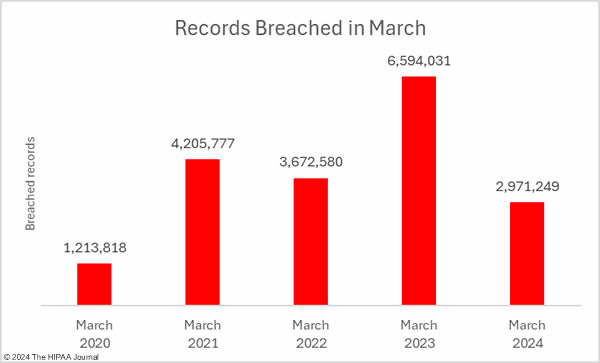
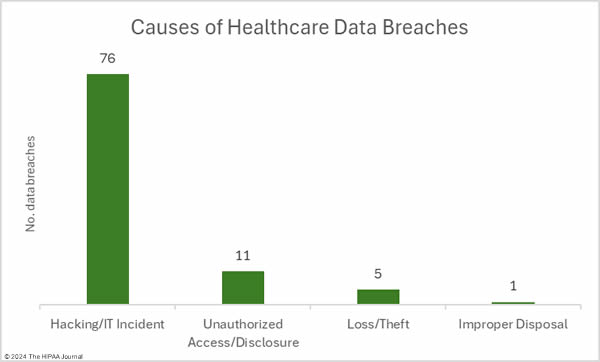
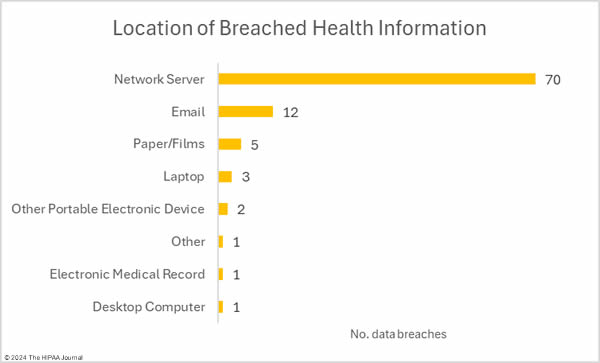
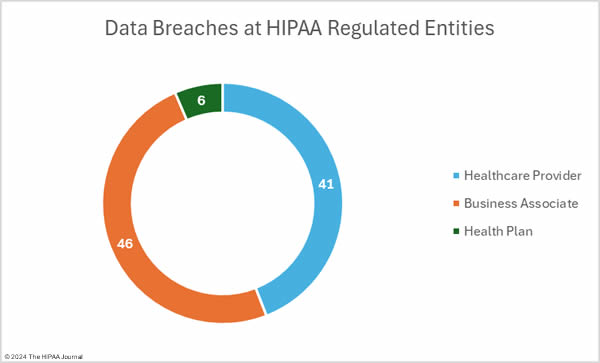
The medical device manufacturer Livanova, the Massachusetts community behavioral health center Aspire Health Alliance, and Santa Rosa Behavioral Healthcare Hospital in California have experienced ransomware attacks that exposed patient data.
Livanova, London, UK
Livanova, a UK-headquartered medical device manufacturer specializing in cardiac surgery and neuromodulation devices, has suffered a ransomware attack that disrupted portions of its IT systems. The ransomware attack was discovered on November 19, 2023, and the forensic investigation confirmed that hackers gained access to its network on October 26, 2023. The LockBit ransomware group claimed responsibility for the attack.
Livanova announced in a SEC filing in November that it was dealing with a cyberattack; however, it was initially unclear to what extent patient data was involved. On April 10, 2024, Livanova confirmed that the personal and protected health information of U.S. patients had been exfiltrated from its systems in the attack. In an April 25, 2024, announcement, Livanova said the investigation is ongoing however it has been determined that information such as names, contact information, dates of birth, Social Security numbers, health insurance information, and medical information such as diagnoses, conditions, treatment information, prescription information, medical record number, device serial numbers, and physician names were involved.
The affected individuals have been advised to monitor their credit reports and account statements and to be alert to unsolicited communications involving personal information. Livnova has arranged for complimentary identity protection and credit monitoring services to be provided to the affected U.S. patients. It is currently unclear how many individuals have been affected. In a February 2024 earnings call, the company confirmed that the company had incurred costs of around $2.6 million in Q4, 2023, as a result of the attack.
Aspire Health Alliance, Massachusetts
Aspire Health Alliance, a state-designated community behavioral health center with facilities in Quincy, Braintree, and Marshfield in Massachusetts, has notified 17,490 individuals about a cyberattack that was detected on September 13, 2023. Suspicious activity was identified within its computer network and a third-party forensic investigation confirmed that its systems had been accessed by an unauthorized third party that acquired certain files and data stored on its network.
A comprehensive review was conducted to determine the types of data involved, and that process was completed on February 26, 2024, when it was confirmed that personal and protected health information was involved. The types of data varied from individual to individual and may have included names, other personal identifiers, and Social Security numbers. While data was exposed or acquired, no reports have been received to indicate any patient data has been misused. Complimentary credit monitoring and identity protection services have been offered to individuals whose Social Security numbers were impacted, and additional security measures have been implemented to reduce the risk of a similar incident occurring in the future.
Santa Rosa Behavioral Healthcare Hospital, California
Santa Rosa Behavioral Healthcare Hospital, part of the Northern California Behavioral Health System (NCBHS), has fallen victim to a cyberattack that disrupted some of its IT systems. The attack was detected on January 28, 2024, and a third-party forensic investigation confirmed that an unauthorized third party accessed its network between January 27, 2024, and January 28, 2024. During that time, files containing patient data were accessed or acquired.
The file review confirmed that the following types of information had been exposed or stolen: names, dates of birth, medical record numbers, services received, dates of services, treating physician, and for some patients, Social Security numbers and/or driver’s license numbers. Affected patients have been advised to monitor the statements they receive from their healthcare providers and health insurers and report any services they haven’t received. Individuals whose Social Security or driver’s license numbers were involved have been offered complimentary identity theft protection services. The incident has been reported to regulators but is not yet shown on the Office for Civil Rights breach portal, so it is currently unclear how many individuals have been affected.
The post Patient Data Stolen from Livanova in October 2023 Ransomware Attack appeared first on HIPAA Journal.