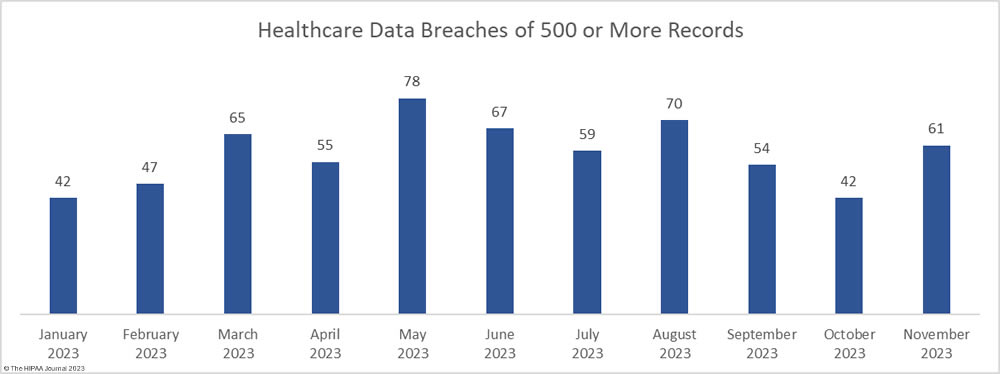
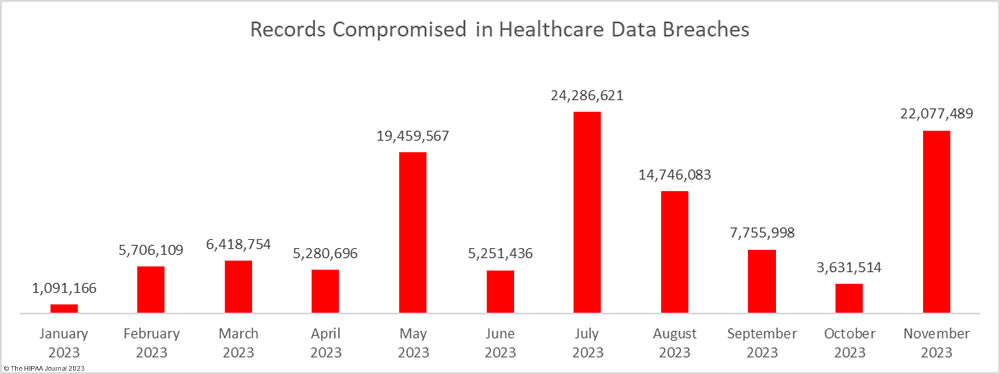
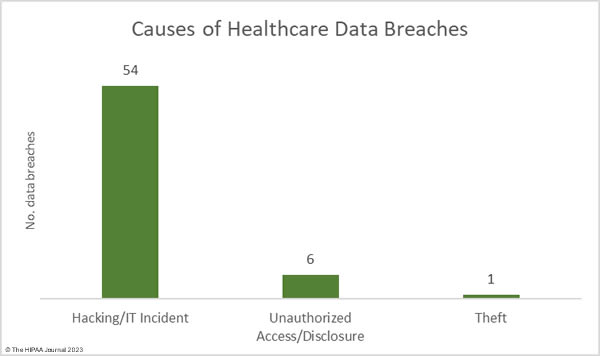
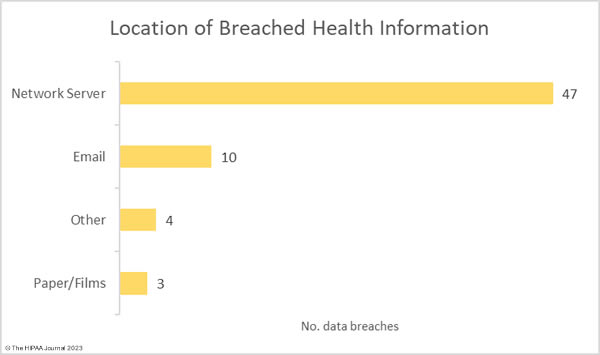
Liberty Hospital in Kansas City is recovering from a cyberattack that has disrupted its IT systems. The cyberattack was detected on the morning of December 19, 2023, and the decision was taken to divert ambulances to other facilities until access to IT systems was restored. Some appointments have been canceled and will be rescheduled. Liberty Hospital has only released limited information about the attack; however, KMBC News obtained a copy of a ransom note. The hackers claim to have downloaded all confidential data stored on its systems and gave the hospital 72 hours to make contact. The threat actor behind the attack is currently unknown.
The Qilin ransomware group has recently added the Neurology Center of Nevada to its data leak site and claims to have exfiltrated at least 198 GB of sensitive data. Neurology Center of Nevada has not publicly confirmed whether the claims of Qilin are genuine. There is no mention of a cyberattack or data breach on its website. If Qilin’s claims are genuine, this will be the second ransomware attack in a year for the Neurology Center of Nevada.
The DragonForce threat group, which was responsible for a recent attack on the Heart of Texas Behavioral Health Network, has claimed responsibility for an attack on Greater Cincinnati Behavioral Health Services and has added it to its data leak site. DragonForce claims to have exfiltrated 72.4 GB of data in the attack although the stolen data has not been uploaded to the group’s data leak site. Greater Cincinnati Behavioral Health Services has not made any announcement about a cyberattack.
4 Over, LLC Notifies Group Health Plan Members About November 2022 Cyberattack
The Glendale, CA-based printing company, 4 Over, LLC, has experienced a cyberattack in which hackers gained access to parts of its network that contained the protected health information of 6,491 members of its group health plan. Suspicious activity was detected within its network on November 19, 2022, and the forensic investigation confirmed there had been unauthorized network access between November 16, 2022, and November 19, 2022. Notification letters started to be sent to the affected individuals on December 5, 2023, more than a year after the breach was detected. 4 Over said the delay was due to undertaking “a time-intensive and thorough review” of the impacted documents.
The information potentially removed from its systems included full names, Social Security numbers, driver’s license or state-issued identification numbers, financial account numbers or credit or debit card numbers, Passport numbers, medical information, treatment information, diagnosis information, health insurance information, and dates of birth. 4 Over said it is reviewing its existing policies and procedures regarding cybersecurity and is evaluating additional measures and safeguards to protect against this type of incident in the future.
Email Accounts Compromised at VNS Health
VNS Health Home Care, VNS Health Hospice Care, and VNS Health Personal Care in New York recently notified patients that an unauthorized third party gained access to the email accounts of some of its employees and potentially viewed or obtained some of their protected health information. Unauthorized access was detected on August 14, 2023, and the investigation revealed several employee email accounts had been accessed by an unauthorized third party between August 10, 2023, and August 14, 2023.
On September 14, 2023, VNS Health determined that emails and associated files in the accounts contained information such as names, dates of birth, addresses, phone numbers, diagnosis and treatment information, and health insurance information. VNS Health said the email accounts appeared to have been compromised to defraud individual VNS personnel rather than to obtain patient information.
VNS Health has implemented additional safeguards and measures to further protect and monitor its systems, including technical systems enhancements, updated security policies and protocols, and staff education. The breach has been reported to the HHS’ Office for Civil Rights as affecting 5,175 VNS Health Personal Care patients and 13,584 members of VNS Health’s Health Plans.
Lake County Health Department Reports Email Account Breach
Lake County Health Department in Illinois is investigating a security incident involving unauthorized access to an employee’s email account. The account breach was detected on November 1, 2023, and the investigation confirmed that the account contained partially de-identified information relating to Lake County residents who may have been part of a disease cluster or outbreak investigated by the health department between July 2014 and October 2023.
No evidence was found that indicated any information in the email account was exfiltrated, but data theft could not be ruled out. The information in the account only included names, addresses, ZIP codes, dates of birth, phone numbers, email addresses, and diagnoses/conditions. The incident is not yet showing on the HHS’ Office for Civil Rights breach portal, so it is currently unclear how many individuals have been affected.
PHI Potentially Obtained in Fresno Surgical Hospital Cyberattack
Fresno Surgical Hospital in California experienced a cyberattack that was detected and blocked on November 4, 2023. Third-party cybersecurity experts were engaged to investigate to determine the nature and extent of the incident and confirmed that some data had been removed from its network on November 4, 2023. All files on the compromised parts of the network were reviewed, and on December 11, 2023, Fresno Surgical Hospital confirmed that personal information may have been involved.
The types of information involved varied from patient to patient and may have included names in combination with one or more of the following: demographic/ contact information such as address and date of birth, medical and/or treatment information such as provider and facility names, medical record number or other patient identifiers, diagnosis information, procedure information, and other clinical information. Fresno Surgical Hospital said security and monitoring capabilities are being enhanced and systems are being hardened to minimize the risk of similar incidents in the future.
The post Ransomware Groups Attack 3 Healthcare Providers appeared first on HIPAA Journal.