There has been a fall in the number of reported healthcare data breaches for the second consecutive month, with 59 data breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights (OCR).
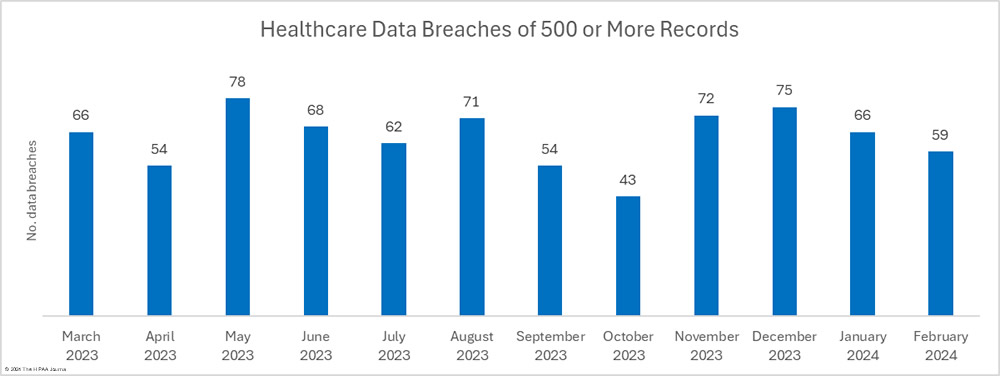
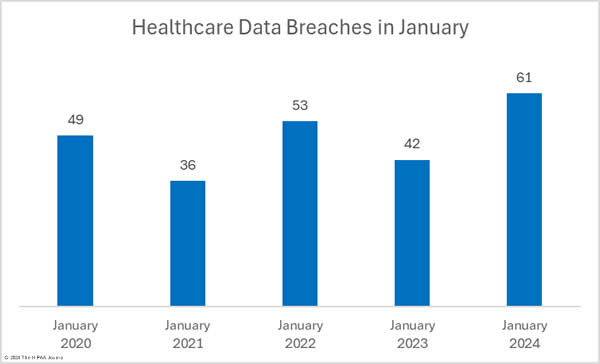
There were 10.6% fewer breaches reported in February than in January, which followed a 22% reduction between December 2023 and January 2024. Over the past 12 months, an average of 64 healthcare breaches have been reported each month, and while February is well under that average, 22.9% more breaches were reported in February 2024 than in February 2023.
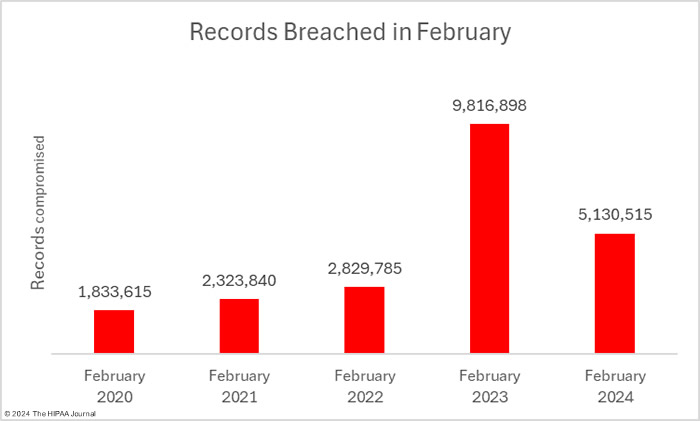
For the third consecutive month, the number of breached records has fallen, reducing by 41.7% from January to 5,130,515 records, which is well below the 12-month average of 8.9 million records a month and around half as many records as were breached in February 2023. These figures could increase as three data breaches were reported as involving 500 or 501 records. These figures are often placeholders to meet HIPAA’s breach reporting requirements when the number of affected individuals has yet to be determined.

Biggest Healthcare Data Breaches in February 2024
There were 24 data breaches of 10,000 healthcare records in February, the largest of which was a 2.35 million record data breach at Medical Management Resource Group, which does business as American Vision Partners. A further 1.67 million records were compromised in breaches at Eastern Radiologists and Unite Here, both of which were hacking incidents. Only four breaches of 10,000 or more records were not hacking incidents.
Ransomware attacks continue to plague the healthcare industry, but it is difficult to determine the scale of the problem since breach notifications rarely mention whether ransomware was used. Ransomware groups typically steal data and leak it or sell it if the ransom is not paid. If the nature of the attack is not explained to the affected individuals, it is difficult for them to accurately assess the level of risk they face and make informed decisions about the steps they need to take to prevent their personal information from being misused.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Business Associate Present |
| Medical Management Resource Group, L.L.C. |
AZ |
Business Associate |
2,350,236 |
Hacking incident (Data theft confirmed) |
| Eastern Radiologists, Inc |
NC |
Healthcare Provider |
886,746 |
Hacking incident |
| UNITE HERE |
NY |
Business Associate |
791,273 |
Hacking incident |
| Northeast Orthopedics and Sports Medicine, PLLC |
NY |
Healthcare Provider |
177,101 |
Hacking incident |
| Bold Quail Holdings, LLC (NewGen Administrative Services, LLC) |
CA |
Healthcare Provider |
105,425 |
Hacking incident |
| Prime Healthcare Employee Health Plan |
CA |
Health Plan |
101,135 |
Hacking incident at business associate (Keenan & Associates) |
| Egyptian Health Department |
IL |
Healthcare Provider |
100,000 |
Hacking incident |
| Scurry County Hospital District dba Cogdell Memorial Hospital |
TX |
Healthcare Provider |
86,981 |
Hacking incident |
| MedQ, Inc. |
TX |
Business Associate |
54,725 |
Ransomware attack (Data theft confirmed) |
| Coleman Professional Services Inc. |
OH |
Healthcare Provider |
51,889 |
Email accounts compromised |
| Greater Cincinnati Behavioral Health Services |
OH |
Healthcare Provider |
50,000 |
Hacking incident |
| Kirkland & Ellis LLP |
IL |
Business Associate |
48,802 |
Hacking incident (MOVEit Transfer) |
| Employee Benefits Corporation of America and Benefit Design Group, Inc. |
VA |
Health Plan |
38,912 |
Hacking incident |
| Washington County Hospital and Nursing Home |
AL |
Healthcare Provider |
29,346 |
Ransomware attack (Data theft confirmed) |
| Qualcomm Incorporated |
CA |
Health Plan |
27,038 |
Hacking incident at a business associate |
| McKenzie County Healthcare System, Inc. |
ND |
Healthcare Provider |
21,000 |
Email accounts compromised |
| East Carolina University’s Brody School of Medicine, a member of the ECU Health affiliated covered entity |
NC |
Healthcare Provider |
19,085 |
Unauthorized access to a network server |
| Tiegerman |
NY |
Healthcare Provider |
19,000 |
Hacking incident |
| Human Affairs International of California |
CA |
Business Associate |
18,347 |
Unauthorized Access/Disclosure of paper/films |
| Maryville, Inc. |
NJ |
Healthcare Provider |
15,503 |
Email account compromised |
| Bay Area Anesthesia, LLC |
FL |
Healthcare Provider |
15,196 |
Hacking incident at business associate (Bowden Barlow Law) |
| AGC Flat Glass North America, Inc. Welfare Benefits Plan |
GA |
Health Plan |
13,079 |
Hacking incident |
| Littleton Regional Healthcare |
NH |
Healthcare Provider |
12,614 |
Misdirected email |
| CVS Caremark Part D Services, L.L.C. (“CVS”) |
RI |
Business Associate |
11,193 |
Unauthorized Access/Disclosure of paper/films |
Data Breach Causes and Location of Compromised PHI
As has been the case for many months, the main cause of healthcare data breaches in February was hacking. In February, there were 41 data breaches classed as hacking/IT incidents – 69.5% of the month’s data breaches. These incidents typically see large numbers of records compromised and February was no exception. Across those 41 incidents, the protected health information of 5,017,167 individuals was exposed or compromised – 97.8% of the month’s breached records. The 16 largest healthcare data breaches in February were all hacking incidents. The average breach size was 122,370 records and the median breach size was 7,288 records.
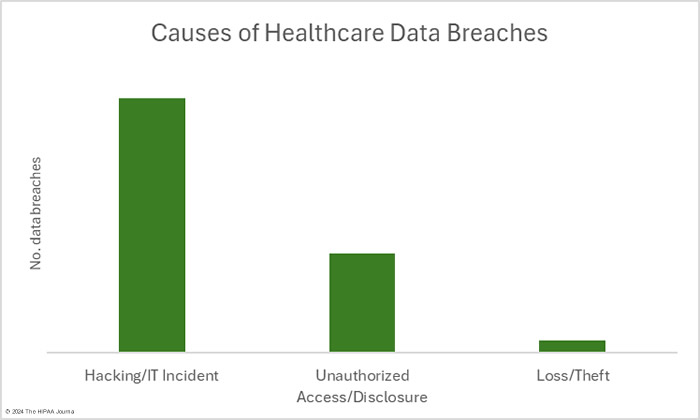
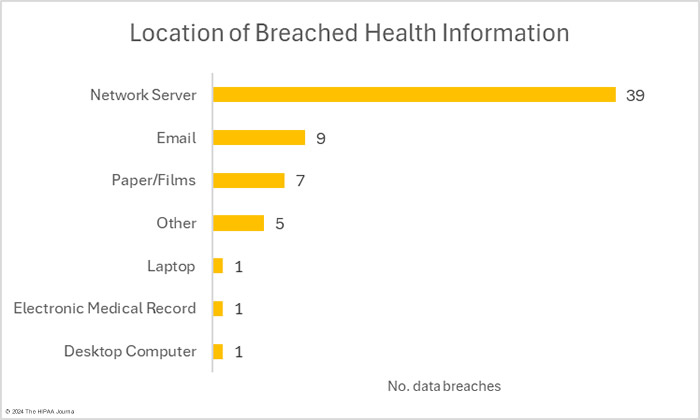
HIPAA-regulated entities reported 16 data breaches that were classed as unauthorized access/disclosure incidents. Across those 16 data breaches, the records of 104,359 individuals were accessed by unauthorized individuals or were impermissibly disclosed. The largest of those incidents was a phishing attack that saw multiple email accounts compromised and the records of 21,000 individuals exposed. The average breach size was 6,522 records and the median breach size was 2,516 records. There were two theft incidents involving the records of 8,989 individuals. No loss or improper disposal incidents were reported in February. The most common location of breached healthcare data was network servers, followed by email accounts.
While it is not possible to prevent all data breaches, many could be avoided by ensuring compliance with the HIPAA Security Rule and implementing OCR’s HPH Cybersecurity Performance Goals (CPGs). The CPGs are split into essential CPGs and advanced CPGs. The Essential CPGs address common vulnerabilities, will significantly improve an organization’s security posture and incident response, and minimize residual risk. The Enhanced CPGs are intended to help HPH sector organizations mature their cybersecurity capabilities and improve their defences against additional attack vectors. A recent IBM study determined that 85% of cyberattacks in critical infrastructure sectors could have been prevented with basic security measures such as those included in the essential CPGs.
Where Did the Data Breaches Occur?
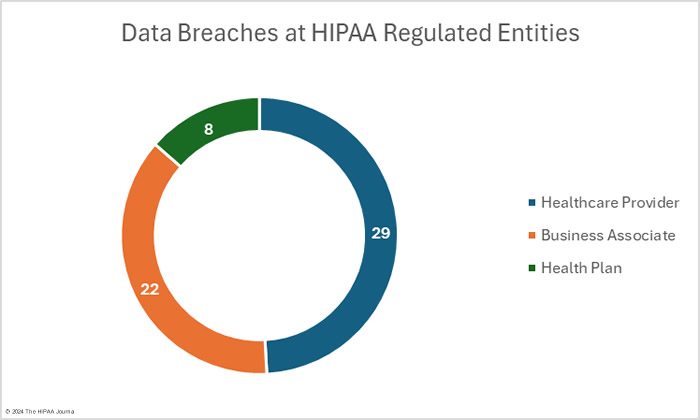
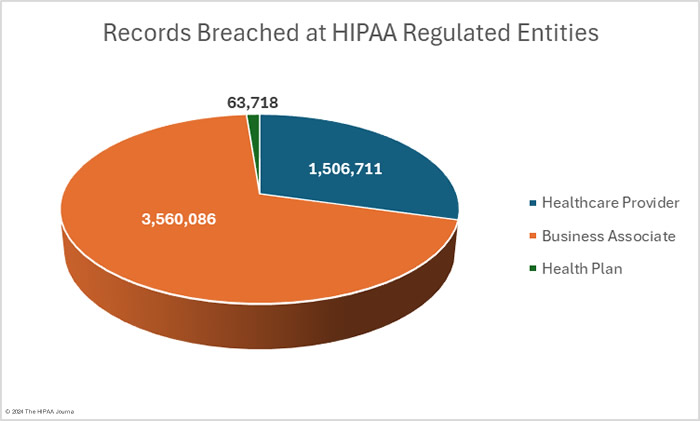
OCR’s data breach portal shows there were 33 data breaches at healthcare providers (1,632,712 records), 16 data breaches at health plans (212,785 records), and 10 data breaches at business associates (3,285,018 records). These figures show the reporting entity rather than where the data breach occurred. When a data breach occurs at a business associate, it may be reported by the business associate, the affected covered entities, or a combination of the two. For example, in February,16 data breaches were reported by health plans, but 8 of those breaches occurred at business associates. The pie charts show where the data breaches occurred rather than the entity that reported the breach.
Geographical Distribution of Healthcare Data Breaches
In February, large healthcare data breaches were reported by HIPAA-regulated entities in 27 states and the District of Columbia. California had the most breaches but Arizona was the worst affected in terms of the number of breached records, with 2,351,027 records compromised in 2 data breaches.
| State |
Breaches |
| California |
6 |
| New York & Ohio |
5 |
| Illinois, Kentucky & Texas |
4 |
| Alabama, Florida & Michigan |
3 |
| Arizona, North Carolina & Rhode Island |
2 |
| Colorado, Georgia, Iowa, Maryland, Massachusetts, Missouri, New Hampshire, New Jersey, North Dakota, Oklahoma, Pennsylvania, South Carolina, Tennessee, Virginia, West Virginia & the District of Columbia |
1 |
HIPAA Enforcement Activity in February 2024
In February, OCR announced two settlements with HIPAA-regulated entities to resolve HIPAA compliance failures. OCR investigated Montefiore Medical Center, a non-profit hospital system based in New York City, over a data breach involving a malicious insider. The breach was discovered in 2015 by the New York Police Department, and the investigation revealed a former employee had stolen the data of 12,517 patients over a 6-month period in 2013. OCR launched an investigation in 2015, but it took until February 2024 for the case to be settled.
OCR identified multiple HIPAA failures, and the severity of those failures warranted a significant fine. Montefiore Medical Center was determined to have failed to conduct a comprehensive risk analysis, failed to implement procedures to regularly review records of information system activity, and failed to implement hardware, software, and/or procedural mechanisms that record and examine activity in all information systems that contain or use ePHI. Montefiore Medical Center agreed to pay a $4.75 million penalty to settle the alleged HIPAA violations.
OCR also announced a $40,000 settlement with Green Ridge Behavioral Health, a Gaithersburg, MD-based provider of psychiatric evaluations, medication management, and psychotherapy. This was the second settlement to be reached with a HIPAA-regulated entity over a ransomware attack. OCR determined that a comprehensive risk analysis had not been conducted, there was a failure to manage risks to the confidentiality, integrity, and availability of ePHI, and there were insufficient policies and procedures for reviewing records of information system activity. These failures contributed to the ransomware attack and the impermissible disclosure of the PHI of more than 14,000 patients.
State Attorneys General also have the authority to issue financial penalties for HIPAA violations; however, no civil monetary penalties or settlements were announced in February.
The post February 2024 Healthcare Data Breach Report appeared first on HIPAA Journal.







