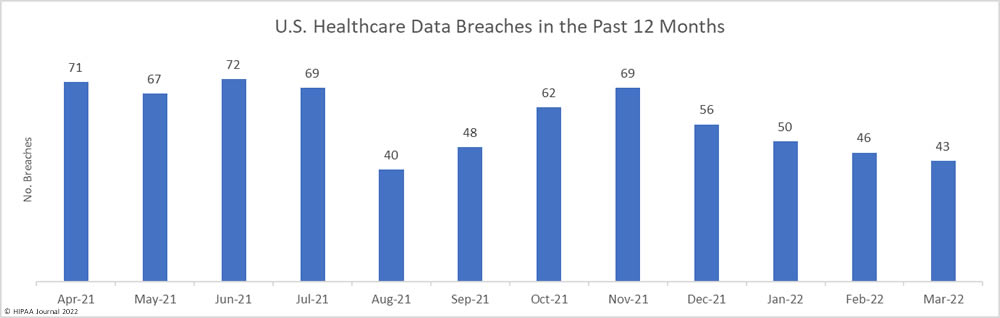
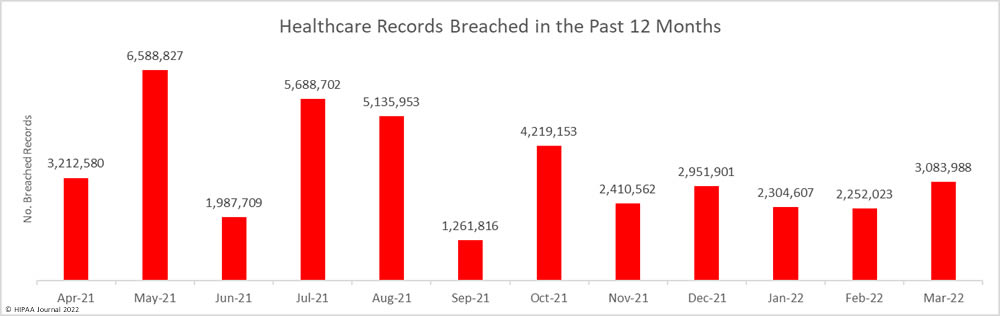
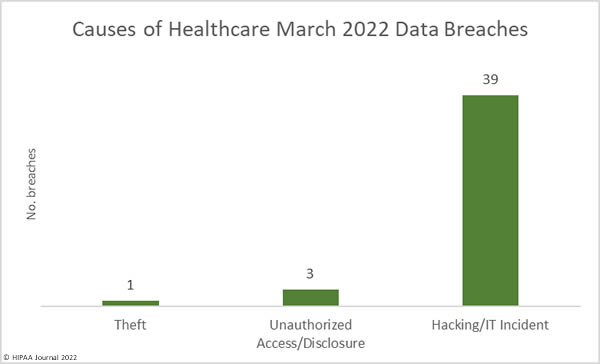
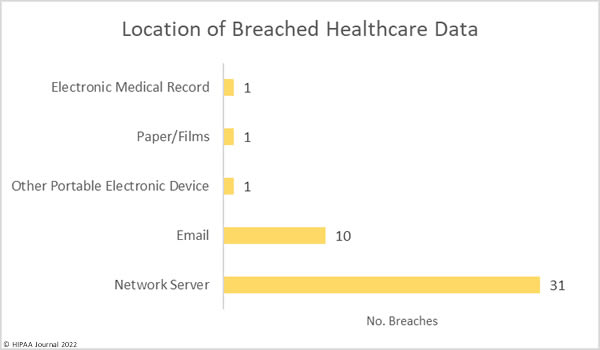
The American Dental Association (ADA) suffered a cyberattack on Friday and has been forced to take many of its systems offline. The ADA website is currently available and explains that “The ADA is experiencing technical difficulties,” and that work is underway to get its systems running smoothly. While the website does not provide any further information on the cause of the technical difficulties, emails have been sent to ADA members advising them about the cyberattack.
The letters explain that parts of its network were taken offline and that Aptify, ADA email, the telephone system, and web chat have all been affected. Many of its online services are currently unavailable; however, details of the attack have not been shared at this time.
The ADA said it has reported the cyberattack to law enforcement and it is investigating the nature and scope of the attack and is being assisted by third-party cybersecurity professionals. The investigation has not uncovered any evidence of data theft at this stage and the extent to which its members, dental practices, and other dental organizations have been affected is not known. Several state dental associations have also reported on their websites that technical difficulties are being experienced, including the New York and Florida Dental Associations.
While little information has been made public about the exact nature of the attack, it has the hallmarks of a ransomware attack. According to Bleeping Computer, a new ransomware operation – Black Basta – has claimed responsibility for the cyberattack and has published a sample of the stolen data on its data leak site. Black Basta claims the leaked data is around 30% of what was stolen from the ADA and includes employee information, financial information, and other sensitive data.
Black Basta is a new ransomware group that started conducting attacks in the middle of April 2022, with the first known victim being the German wind farm operator, Deutsche Windtechnik. The ransomware encrypts files using AES+RSA algorithms and adds the .basta extension to encrypted files. The group claims in its ransomware notes that data has been stolen and will be published on its TOR website if the ransom is not paid. The desktop on victim devices is replaced with an image stating, “your network is encrypted by Black Basta group,” and a readme.txt file is dropped on the desktop with instructions for recovering files.
Tenet Healthcare Confirms Recent Cyberattack
The Dallas, TX-based multinational health system Tenet Healthcare, which operates 620 facilities in 34 states including 60 hospitals, is currently recovering from a cyberattack that disrupted some of its acute care operations.
The attack occurred last week, and the health system says most critical functions have now been restored and normal operations are starting to be resumed at the affected locations. Tenet explained on its website in an April 26, 2022 post that user access was immediately suspended on the affected technology applications when the cyberattack was detected, its cybersecurity protocols were immediately implemented, and rapid action was taken to prevent further unauthorized access to its systems.
Tenets said, “Efforts to restore impacted information technology operations continue to make important progress,” and that all of its healthcare facilities remained operational and continued to deliver patient care safely, using well-established backup processes. An investigation has been launched to determine the nature and scope of the cyberattack, and that investigation is ongoing. It is currently unclear to what extent, if any, patient and employee data has been affected.
The post American Dental Association and Tenet Healthcare Recovering from Cyberattacks appeared first on HIPAA Journal.