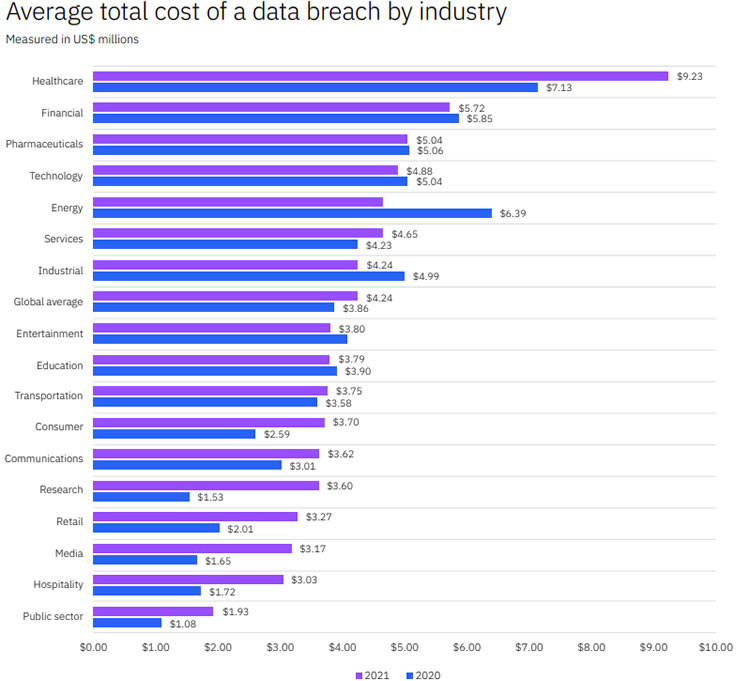
IBM Security has published its 2021 Cost of a Data Breach Report, which shows data breach costs have risen once again and are now at the highest level since IBM started publishing the reports 17 years ago. There was a 10% year-over-year increase in data breach costs, with the average cost rising to $4.24 million per incident. Healthcare data breaches are the costliest, with the average cost increasing by $2 million to $9.42 million per incident. Ransomware attacks cost an average of $4.62 million per incident.
Source: IBM Security
The large year-over-year increase in data breach costs has been attributed to the drastic operational shifts due to the pandemic. With employees forced to work remotely during the pandemic, organizations had to rapidly adapt their technology. The pandemic forced 60% of organizations to move further into the cloud. Such a rapid change resulted in vulnerabilities being introduced and security often lagged behind the rapid IT changes. Remote working also hindered organizations’ ability to quickly respond to security incidents and data breaches.
According to IBM, data breaches costs were more than $1 million higher when remote work was indicated as a factor in the data breach. When remote work was a factor, the average data breach cost was $4.96 million compared to $3.89 million when remote work was not a factor. Almost 20% of organizations that reported data breaches in 2020 cited remote work as a factor, with the cost of a data breach around 15% higher when remote work was a factor.
To compile the report, IBM conducted an in-depth analysis of data breaches involving fewer than 100,000 records at 500 organizations between May 2020 and March 2021, with the survey conducted by the Ponemon Institute.
The most common root cause of data breaches in the past year were compromised credentials, which accounted for 20% of data breaches. These breaches took longer to detect and contain, with an average of 250 days compared to an overall average of 212 days.
The most common types of data exposed in data breaches were customers’ personal data such as names, email addresses, passwords, and healthcare data. 44% of all data breaches included those types of data. A data breach involving email addresses, usernames, and passwords can easily have a spiral effect, as hackers can use the compromised data in further attacks. According to the Ponemon Institute survey, 82% of individuals reuse passwords across multiple accounts.
Breaches involving customers’ personally identifiable information (PII) were more expensive than breaches involving other types of data, with a cost per record of $180 when PII was involved compared to $161 per record for other types of data.
Data breach costs were lower at companies that had implemented encryption, security analytics, and artificial intelligence-based security solutions, with these three mitigating factors resulting in data breach cost savings of between $1.25 million and $1.49 million per data breach.
Adopting a zero-trust approach to security makes it easier for organizations to deal with data breaches. Organizations with a mature zero trust strategy had an average data breach cost of $3.28 million, which was $1.76 million lower than those who had not deployed this approach at all.
“Higher data breach costs are yet another added expense for businesses in the wake of rapid technology shifts during the pandemic,” said Chris McCurdy, Vice President and General Manager, IBM Security. “While data breach costs reached a record high over the past year, the report also showed positive signs about the impact of modern security tactics, such as AI, automation and the adoption of a zero-trust approach – which may pay off in reducing the cost of these incidents further down the line.”
Security automation greatly reduces data breach costs. Organizations with a “fully deployed” security automation strategy had average breach costs of $2.90 million per incident, compared to $6.71 million at organizations that had no security automation.
Companies with an incident response team that had tested their incident response plan had 54.9% lower breach costs than those that had neither. The average data breach cost was $3.25 million compared to $5.71 million when neither were in place.
The cost of a data breach was $750,000 (16.6%) higher for companies that had not undergone any digital transformation due to COVID-19. Cloud-based data breach costs were lower for organizations that had adopted a hybrid cloud approach, with an average cost of $3.61 million at organizations with hybrid cloud infrastructure compared to $4.80 million for organizations with a primarily public cloud and $4.55 million for those that had adopted a private cloud approach. Data breach costs were 18.8% higher when a breach was experienced during a cloud migration project.
Organizations that were further into their cloud migration plan were able to detect and respond to data breaches far more quickly – on average 77 days more quickly for organizations that were at a mature state of their cloud modernization plan than those in the early stages.
Mega data breaches – those involving between 50 million and 65 million records – cost an average of $401 million per incident, which is more than 100 times the cost of breaches involving between 1,000 and 100,0000 records.
The post The Average Cost of a Healthcare Data Breach is Now $9.42 Million appeared first on HIPAA Journal.
