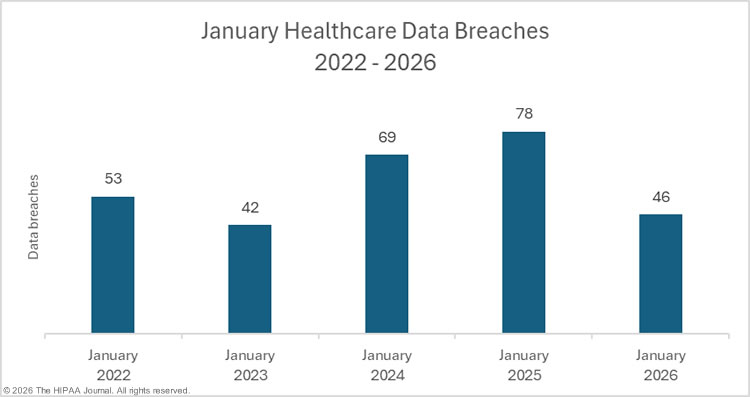
More than 700 healthcare data breaches affecting 500 or more individuals are being reported to the Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) each year. While that unwelcome trend didn’t change in 2025, there was a year-over-year reduction in healthcare data breaches. Based on the current data downloaded from OCR, data breaches have fallen by 4.3% year-over-year.
While that could signal a turn in the tide, it is perhaps a little early to draw such conclusions, as data breaches from 2025 are still being added to the OCR breach portal. When we compiled our 2024 healthcare data breach report in January 2025, 725 large healthcare data breaches were listed on the OCR breach portal. That total increased to 742 data breaches over the following few months. While a similar number of late additions would still mean an annual decrease in data breaches, there was a 43-day shutdown of the federal government in late 2025 due to the failure of Congress to pass appropriations legislation. During that period, no data breaches were added to the OCR breach portal. The late additions in 2026 could therefore be considerably higher than in previous years.
What is clear is that the large annual increases in data breaches between 2018 and 2021 appear to have come to an end, with data breaches plateauing in the 700 to 750 range, which is around two large healthcare data breaches a day – twice the rate in 2018.

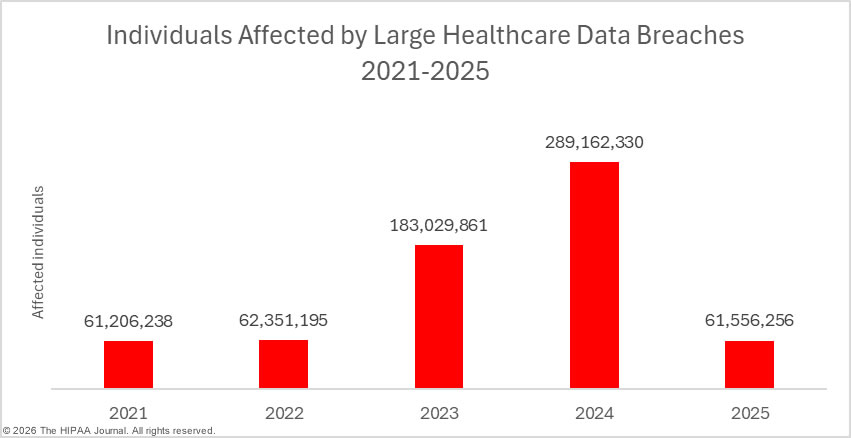
While data breaches are only down slightly, there has been a massive reduction in the number of individuals affected by healthcare data breaches. In 2024, a new record was set for breached healthcare records, with 289,162,330 individuals having their protected health information exposed or impermissibly disclosed in 2024. In 2025, at least 61,556,256 individuals had their protected health information exposed or impermissibly disclosed, a 78.7% percentage decrease from 2024. Even if the 192,700,000 individuals affected by the Change Healthcare ransomware attack in 2024 are discounted entirely, last year’s would still be significantly down year-over-year, largely due to a fall in the number of mega data breaches affecting more than 1 million individuals. In 2024, there were 18 of these mega breaches, but only 9 mega breaches were reported in 2025. The average data breach size fell from 389,707 individuals (median: 6,702 individuals) in 2024 to 86,699 individuals (median: 4,011 individuals) in 2025.
The Biggest Healthcare Data Breaches of 2025
The table below shows the top 20 healthcare data breaches of 2025, the biggest of which was a hacking incident at the insurance company Aflac, which affected more than 22.6 million individuals globally and involved unauthorized access to the protected health information of almost 14 million individuals in the United States. While the nature of the attack was not disclosed, the cyberattack is thought to be the work of the Scattered Spider hacking group, a financially-motivated English-speaking hacking group whose members are primarily located in the United States and the United Kingdom.
While most of the top 20 data breaches were hacking incidents, the data breach at Blue Shield of California involved the use of tracking tools on its website, which may have disclosed personal information and, in some cases, protected health information to third parties such as Meta Platforms and Google. The data breach at Serviceaide involved an improperly secured database, which could be freely accessed via the internet without any authentication, and two of the top 20 data breaches of 2025 involved compromised email accounts: Numotion and Onsite Mammography.
The table below could change over the coming few months as many investigations of 2025 healthcare data breaches have not yet concluded. For instance, the data breach at Covenant Health was reported to OCR as affecting just 7,864 individuals, but in January 2025, the Maine Attorney General was informed that 478,188 individuals were affected. The OCR data breach portal has yet to be updated with the new total. Further, the OCR breach portal currently lists 64 data breaches with totals of 500 or 501 affected individuals – placeholder figures commonly used when data reviews have yet to conclude.
| Rank |
Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| 1 |
Aflac Incorporated (“Aflac”) |
GA |
Health Plan |
13,924,906 |
Hacking incident |
| 2 |
Yale New Haven Health System |
CT |
Healthcare Provider |
5,556,702 |
Hacking incident |
| 3 |
Episource, LLC |
CA |
Business Associate |
5,418,866 |
Hacking incident |
| 4 |
Blue Shield of California |
CA |
Business Associate |
4,700,000 |
PHI disclosure due to website tracking tools |
| 5 |
DaVita Inc. |
CO |
Healthcare Provider |
2,689,826 |
Ransomware attack |
| 6 |
Anne Arundel Dermatology |
MD |
Healthcare Provider |
1,905,000 |
Hacking incident |
| 7 |
Radiology Associates of Richmond, Inc. |
VA |
Healthcare Provider |
1,419,091 |
Hacking incident |
| 8 |
Southeast Series of Lockton Companies, LLC (Lockton) |
GA |
Business Associate |
1,124,727 |
Hacking incident |
| 9 |
Community Health Center, Inc. |
CT |
Healthcare Provider |
1,060,936 |
Hacking incident |
| 10 |
Frederick Health |
MD |
Healthcare Provider |
934,326 |
Ransomware attack |
| 11 |
McLaren Health Care |
MI |
Healthcare Provider |
743,131 |
Ransomware attack |
| 12 |
Medusind Inc. |
FL |
Business Associate |
701,475 |
Hacking incident |
| 13 |
Kelly & Associates Insurance Group, Inc. |
MD |
Business Associate |
553,332 |
Hacking incident |
| 14 |
Decisely Insurance Services, LLC |
GA |
Business Associate |
537,603 |
Hacking incident |
| 15 |
United Seating and Mobility, LLC d/b/a Numotion |
TN |
Healthcare Provider |
529,004 |
Phishing attack |
| 16 |
Serviceaide, Inc. |
CA |
Business Associate |
483,126 |
Database exposed on the internet |
| 17 |
Goshen Medical Center |
NC |
Healthcare Provider |
456,385 |
Hacking incident |
| 18 |
Ascension Health |
MO |
Healthcare Provider |
437,329 |
Hacking incident at a business associate |
| 19 |
Northwest Radiologists, Inc./Mount Baker Imaging |
WA |
Healthcare Provider |
362,713 |
Hacking incident |
| 20 |
Onsite Mammography |
MA |
Business Associate |
357,265 |
Compromised email account |
| 2025 Healthcare Data Breaches |
| Data Breach Size |
Number of breaches |
| 10,000,000+ |
1 |
| 1,000,000 – 9,999,999 |
8 |
| 500,000 – 999,999 |
6 |
| 100,000 – 499,000 |
64 |
| 10,000 – 99,999 |
176 |
| 1,000 – 9,999 |
309 |
| 500 – 999 |
146 |
| Total |
710 |


2025 Healthcare Data Breach Causes
Hacking and other IT incidents continue to dominate the breach reports. The majority of these incidents are hacking incidents, as has been the case for many years. There has been a growing trend in recent years of entities suffering data breaches failing to disclose the root cause of the data breach, such as if a hacking incident involved data theft, extortion, malware, or ransomware. The Identity Theft Resource Center reports that this is a problem across all industry sectors, not just healthcare.

The problem with the lack of information in breach notices is that individuals are not given sufficient information to make an accurate determination about the level of risk they face. Most ransomware attacks involve data theft and extortion. If the ransom is not paid, the stolen data is leaked on the dark web or sold. According to the cybersecurity firm Black Fog, 96% of ransomware attacks involve data theft, and the ransomware remediation firm Coveware reports that in Q4, 2025, only 20% of ransomware victims paid the ransom. Those figures suggest that 76.8% of ransomware attacks result in data being leaked. If the breach victims are told that ransomware was involved, their data will likely be leaked, and it would be prudent to take steps to prevent data misuse. If they are only told that their data has been exposed, they may incorrectly assume that they do not face a high risk of data misuse and may choose to take no action.
Black Fog reports that ransomware attacks reached record levels in 2025, with 1,174 confirmed attacks across all industry sectors, and healthcare was the worst affected sector, accounting for 22% of attacks. There has also been a growing trend of data theft and extortion, with threat actors skipping file encryption. The PEAR threat group emerged in 2025 and only engages in data theft and extortion. The group claimed many healthcare victims in 2025. Other common IT incidents in 2025 include improperly secured databases, which exposed healthcare data via the internet, and phishing attacks that resulted in unauthorized access to email accounts.


Hacking and other IT incidents tend to affect more individuals than other types of breaches. In 2025, these incidents affected an average of 105,623 individuals (median: 5,434 individuals), compared to an average of 9,909 individuals (median: 1,662 individuals) for unauthorized access/disclosure incidents, and an average of 4,402 individuals (median: 1,690 individuals) for loss/theft incidents.
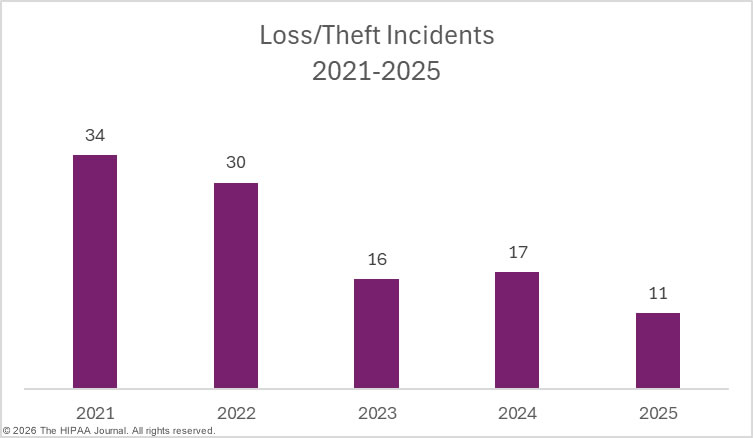
While there were small decreases in hacking/IT incidents, loss/theft incidents, and improper disposal incidents year-over-year, there was a 17.4% increase in unauthorized access/disclosure incidents. These incidents include data theft by malicious insiders and inadvertent data exposures due to carelessness by employees. Staff HIPAA training can go a long way toward reducing these types of breaches. Making all staff members aware of their responsibilities under HIPAA and the consequences of HIPAA violations if they are discovered can help to reduce the risk of these types of breaches.

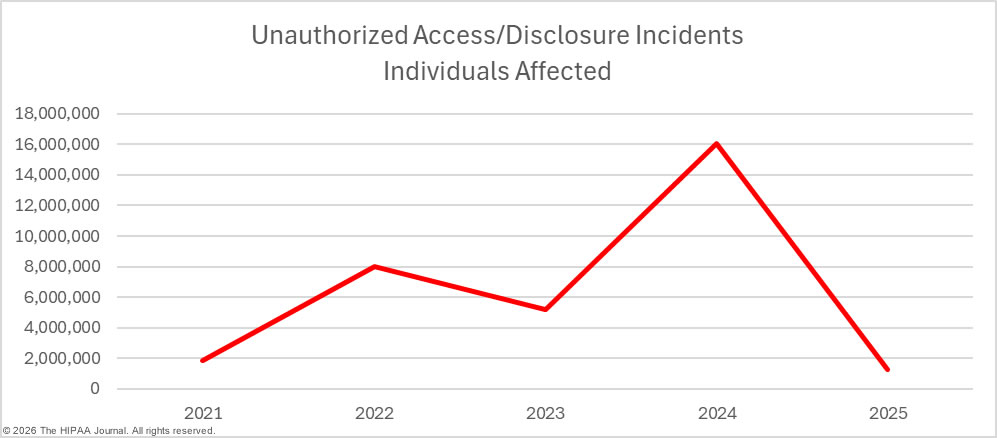
Regular security awareness training can help to eradicate risky security practices that frequently result in data breaches. It is also important for regulated entities to have the software, policies, and procedures in place to allow them to identify and remediate insider incidents quickly. Loss and theft incidents are becoming far less common due to the shift to cloud storage of PHI, and easier-to-implement and more cost-effective encryption options. While these incidents were once a leading cause of healthcare data breaches, they are now relatively rare.
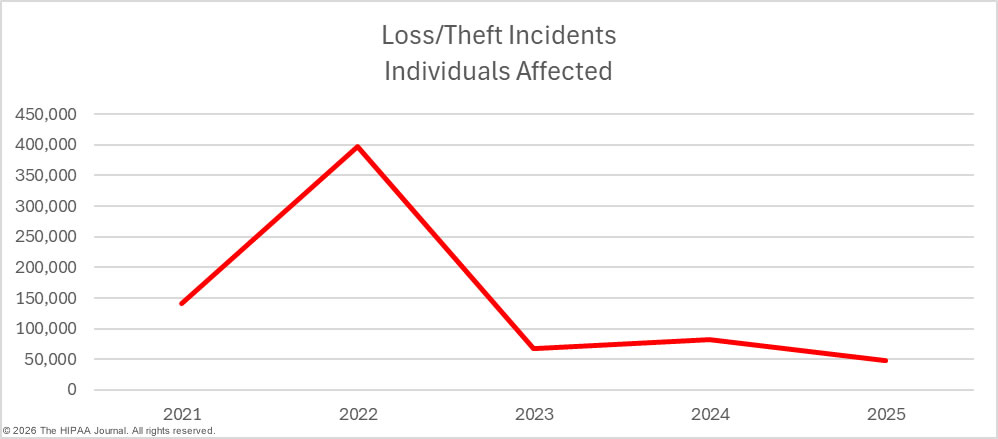
Improper disposal incidents are also something of a rarity. In 2025, there was only one such incident at a HIPAA-regulated entity, although it was a significant data breach, affecting more than 35,000 individuals.


Location of Breached Protected Health Information
A majority of the year’s data breaches involved exposed and stolen protected health information stored on network servers (61.5%), with almost a quarter of data breaches (24.9%) involving compromised email accounts. Physical PHI – paper and films – was compromised in 5.6% of the year’s data breaches, and 4.6% of data breaches involved unauthorized access to electronic medical records.

Data Breaches at HIPAA-Regulated Entities
The OCR data breach portal currently lists 523 data breaches at healthcare providers, 56 data breaches at health plans, and two data breaches at healthcare clearinghouses. A further 128 data breaches were reported by business associates of HIPAA-covered entities.
When a data breach occurs at a business associate, it is ultimately the responsibility of each affected covered entity to ensure compliance with the notification requirements of the HIPAA Breach Notification Rule. The covered entity may delegate the responsibility of issuing notifications to the business associate, or the covered entity may choose to issue notifications, or a combination of the two. Some healthcare data breach reports fail to take this into account, resulting in business associate data breaches being undercounted.
The charts below are based on the entity that experienced the data breach, rather than the entity that reported the breach. In 2025, 57.5% of data breaches occurred at healthcare providers, 35.8% at business associates, 6.5% at health plans, and 0.3% at healthcare clearinghouses.


Geographical Distribution of Healthcare Data Breaches
Data breaches affecting 500 or more individuals were reported by HIPAA-regulated entities in 49 U.S states, the District of Columbia, and Puerto Rico in 2025. The only state to avoid a large healthcare data breach in 2025 was Vermont.
| State/Territory |
Data Breaches |
State/Territory |
Data Breaches |
| California |
69 |
Kansas |
8 |
| Florida |
47 |
Oklahoma |
8 |
| Texas |
47 |
Arkansas |
7 |
| New York |
44 |
Iowa |
7 |
| Ohio |
37 |
Nebraska |
7 |
| Pennsylvania |
32 |
South Carolina |
7 |
| Michigan |
26 |
Alaska |
6 |
| Illinois |
25 |
Alabama |
6 |
| Georgia |
23 |
Colorado |
6 |
| North Carolina |
22 |
Maine |
6 |
| Missouri |
20 |
Utah |
5 |
| Indiana |
18 |
Idaho |
4 |
| Massachusetts |
17 |
Mississippi |
4 |
| Maryland |
17 |
Montana |
4 |
| Minnesota |
17 |
New Mexico |
4 |
| Tennessee |
16 |
Nevada |
4 |
| Virginia |
16 |
Rhode Island |
4 |
| Washington |
16 |
West Virginia |
4 |
| Wisconsin |
16 |
New Hampshire |
3 |
| Arizona |
15 |
Delaware |
2 |
| Louisiana |
13 |
Hawaii |
2 |
| New Jersey |
12 |
South Dakota |
2 |
| Connecticut |
11 |
Wyoming |
2 |
| Oregon |
10 |
District of Columbia |
1 |
| Kentucky |
9 |
North Dakota |
1 |
While California was the worst-affected state in terms of data breaches, Georgia took top spot for affected individuals.
| State/Territory |
Affected Individuals |
State/Territory |
Affected Individuals |
| Georgia |
16,050,351 |
Minnesota |
222,210 |
| California |
11,849,467 |
Iowa |
218,559 |
| Connecticut |
7,048,122 |
Wisconsin |
199,972 |
| Maryland |
3,809,252 |
Rhode Island |
176,500 |
| Florida |
3,372,753 |
Maine |
158,054 |
| Colorado |
2,708,292 |
Idaho |
154,525 |
| Virginia |
1,900,219 |
South Dakota |
132,161 |
| Michigan |
1,812,898 |
Louisiana |
114,599 |
| North Carolina |
1,484,108 |
Nebraska |
114,313 |
| Texas |
1,034,662 |
South Carolina |
97,122 |
| New York |
1,032,819 |
Nevada |
90,241 |
| Tennessee |
832,230 |
Alaska |
90,073 |
| Pennsylvania |
811,816 |
Oregon |
86,813 |
| Missouri |
787,413 |
New Mexico |
86,235 |
| Washington |
628,651 |
West Virginia |
76,191 |
| Indiana |
621,441 |
New Hampshire |
73,816 |
| Ohio |
577,751 |
Mississippi |
60,205 |
| Illinois |
513,672 |
Puerto Rico |
50,000 |
| Massachusetts |
465,095 |
Utah |
42,651 |
| New Jersey |
448,143 |
Oklahoma |
38,342 |
| Kansas |
438,181 |
Montana |
36,485 |
| Arkansas |
261,435 |
Wyoming |
15,883 |
| Arizona |
243,894 |
Delaware |
14,635 |
| Kentucky |
233,836 |
Hawaii |
8,972 |
| Alabama |
228,199 |
District of Columbia |
1,847 |
HIPAA Violation Penalties in 2025

Last year, OCR almost set a new record for HIPAA enforcement actions, with 21 investigations of complaints and data breaches resolved with settlements or civil monetary penalties. While 2025 saw the second-highest-ever number of HIPAA cases resolved with financial penalties, OCR only collected $8,330,066 in fines, as the majority of penalties were imposed for violations of a single HIPAA provision.

In 2025, a key focus for OCR was compliance with the risk analysis provision of the HIPAA Security Rule. A comprehensive, organization-wide risk analysis is vital for security. If a risk analysis is not conducted or if it is incomplete, risks are likely to remain unaddressed and may be found and exploited by threat actors. OCR’s compliance audits and data breach investigations have frequently identified risk analysis failures, prompting OCR to launch a risk analysis enforcement initiative.
By focusing on this vital aspect of HIPAA compliance, rather than investigating data breaches more broadly for HIPAA noncompliance, OCR has been able to make significant inroads into addressing its backlog of data breach investigations. The consequence of this approach is that by focusing on violations of a single HIPAA provision, financial penalties are lower.
| Area of Noncompliance |
Number of Enforcement Actions |
| Risk Analysis |
16 |
| Breach notifications |
5 |
| Impermissible disclosure of ePHI |
4 |
| Recording and monitoring activity in information systems |
3 |
| Right of Access |
3 |
| Risk management |
3 |
| Social media |
1 |
| Information access management |
1 |
| Procedures to create and maintain retrievable exact copies of ePHI |
1 |
In 2025, 76% of all enforcement actions included a penalty for a risk analysis failure. OCR has also started to look closely at compliance with the Breach Notification Rule, which was the second most common reason for a financial penalty. The HIPAA Breach Notification Rule requires notices to OCR, individuals, and the media within 60 days of the discovery of a data breach. More than one-fifth of enforcement actions included a penalty for breach notification failures.
OCR has confirmed that its enforcement priorities in 2026 will be largely the same as in 2025. OCR will continue with its HIPAA Right of Access and risk analysis enforcement initiatives, with the latter being expanded to include risk management. In addition to demonstrating that risks have been identified, OCR will want to see evidence that the identified risks have been managed and reduced in a timely manner.
OCR HIPAA Settlements in 2025
| HIPAA-Regulated Entity |
Penalty Amount |
Reason for Penalty |
| Elgon Information Systems |
$80,000 |
Risk analysis failure |
| Virtual Private Network Solutions |
$90,000 |
Risk analysis failure |
| USR Holdings |
$337,750 |
Risk analysis failure; recording activity in information systems; procedures to create and maintain retrievable exact copies of ePHI; impermissible disclosure of 2,903 individuals’ PHI |
| Solara Medical Supplies |
$3,000,000 |
Risk analysis failure; risk management failure; breach notification failure (individuals, media, HHS); impermissible disclosure of the PHI of 114,007 and 1,531 individuals, |
| South Broward Hospital District (Memorial Health System) |
$60,000 |
HIPAA Right of Access failure |
| Northeast Surgical Group |
$10,000 |
Risk analysis failure |
| Health Fitness Corporation |
$227,816 |
Risk analysis failure |
| Northeast Radiology, P.C. |
$350,000 |
Risk analysis failure |
| Guam Memorial Hospital Authority |
$25,000 |
Risk analysis failure |
| PIH Health |
$600,000 |
Risk analysis failure; breach notification failure (media notice, HHS notice); impermissible disclosure of PHI |
| Comprehensive Neurology, PC |
$25,000 |
Risk analysis failure |
| Vision Upright MRI |
$5,000 |
Risk analysis failure; breach notification failure |
| BayCare Health System |
$800,000 |
Information access management failure (minimum necessary standard); risk management failure; lack of information system activity reviews |
| Comstar, LLC |
$75,000 |
Risk analysis failure |
| Deer Oaks – The Behavioral Health Solution |
$225,000 |
Risk analysis failure; impermissible disclosure of ePHI |
| Syracuse ASC (Specialty Surgery Center of Central New York) |
$250,000 |
Risk analysis failure; breach notification failure (OCR, individuals) |
| BST & Co. CPAs, LLP |
$175,000 |
Risk analysis failure |
| Cadia Healthcare Facilities |
$182,000 |
Social media disclosure without authorization; breach notification failure |
| Concentra Inc. |
$112,500 |
HIPAA Right of Access failure |
OCR HIPAA Civil Monetary Penalties in 2025
| HIPAA-Regulated Entity |
Penalty Amount |
Reason for Penalty |
| Warby Parker |
$1,500,000 |
Risk analysis failure; risk management failure; lack of monitoring of activity in information systems containing ePHI. |
| Oregon Health & Science University |
$200,000 |
HIPAA Right of Access failure |
State attorneys general also enforce HIPAA compliance and can impose financial penalties, although some state attorneys general impose fines for violations of state data privacy and security rules. In 2025, only one enforcement action was announced by a state attorney general. The New York attorney general imposed a $500,000 financial penalty on Orthopedics NY LLP for cybersecurity failures that led to a data breach affecting 656,086 individuals. The penalty was imposed for violations of New York laws, although the HIPAA Security Rule was undoubtedly also violated.
The post 2025 Healthcare Data Breach Report appeared first on The HIPAA Journal.