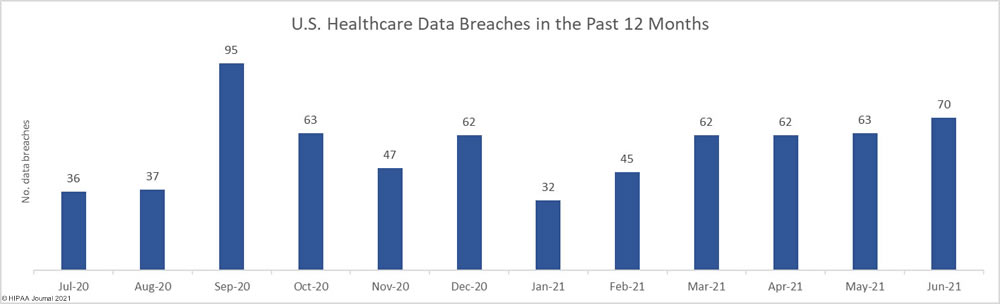
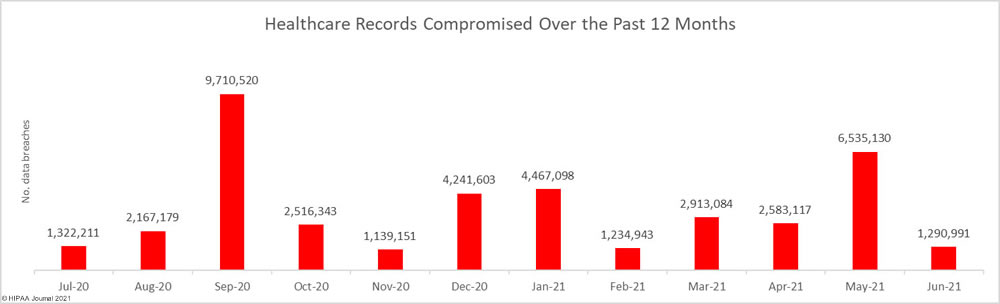
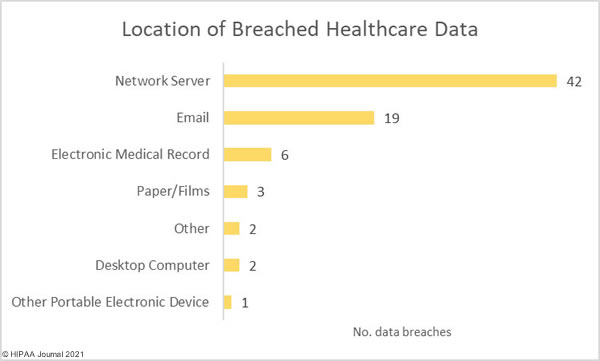
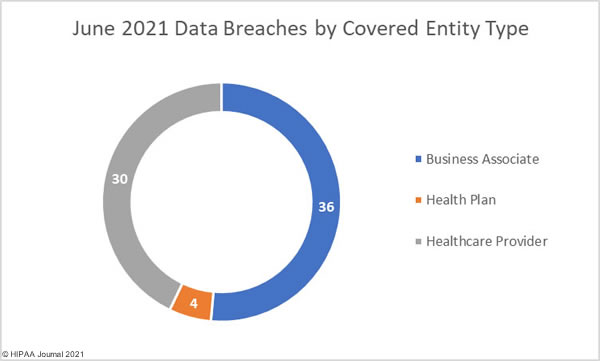
In June, a bipartisan group of senators circulated a draft federal breach notification bill – the Cyber Incident Notification Act of 2021 – that requires all federal agencies, contractors, and organizations considered critical to U.S. national security to report data breaches and security incidents to the DHS’ Cybersecurity and Infrastructure Security Agency (CISA) within 24 hours of discovery. On Wednesday this week, an amended bill was formally introduced in the Senate.
The draft bill was introduced by Senators Mark Warner (D-VA) and Marco Rubio (R-FL), and Susan Collins (R-ME). Another 12 senators across both parties have now added their names to the bill.
The bill seeks to address some of the key issues that have come to light in the wake of recent cyberattacks that impacted U.S. critical infrastructure, including the SolarWinds Orion supply chain attack and the ransomware attacks on JBS and Colonial Pipeline.
“The SolarWinds breach demonstrated how broad the ripple effects of these attacks can be, affecting hundreds or even thousands of entities connected to the initial target,” said Sen. Warner. “We shouldn’t be relying on voluntary reporting to protect our critical infrastructure. We need a routine federal standard so that when vital sectors of our economy are affected by a breach, the full resources of the federal government can be mobilized to respond to and stave off its impact.”
The purpose of the new bill is to ensure timely federal government awareness of cyber intrusions that pose a threat to national security, with the bill enabling the development of a common operating picture of national-level cyber threats.
Security incidents that warrant notifications to be sent to CISA are those that:
- Involve or are believed to involve a nation state.
- Involve or are believed to involve an Advanced Persistent Threat (APT) actor.
- Involve or are believed to involve a transnational organized crime group.
- Could harm U.S. national security interests, foreign relations, or the U.S. economy.
- Likely to be of significant national consequence.
- Has potential to affect CISA systems.
- Involve ransomware
Reportable ransomware attacks are those that are assessed to involve a nation state actor, advanced persistent threat (APT) actor, transnational organized crime group, or an attack that has the potential to result in demonstrable harm to national security, foreign relations, the economy of the United States, the public confidence, civil liberties, or public health and safety of U.S. residents.
When reporting a security incident or cyber threat, organizations are required include a description of the incident, detail the systems and networks affected, provide an estimate of when the incident is likely to have occurred, provide information about any vulnerabilities that were exploited, any tactics, techniques, and procedures (TTPs) known to have been used. Actionable cyber threat information will be made available to government and private sector entities and the public to allow prompt action to be taken to counter threats. The bill gives CISA 48 hours to respond to reports of an intrusion and request information about the security incident.
To encourage organizations to report data breaches, the bill includes liability protections for breached entities to protect against potential lawsuits that could arise from disclosing security breaches and allows anonymized personal data to be submitted when reporting breaches.
The bill requires the Department of Homeland Security to work with other federal agencies to draw up a set of reporting criteria and to harmonize those criteria with the regulatory requirements in effect on the date of enactment.
The failure to report a security incident to CISA can attract a financial penalty, which will be determined by the Administrator of the General Services Administration. The maximum financial penalty will be 0.5% of gross revenue for the previous fiscal year. Other possible sanctions include removal from federal contracting schedules.
“It is critical that American organizations act immediately once an attack occurs. The longer an attack goes unreported, the more damage can be done. Ensuring prompt notification will help protect the health and safety of countless Americans and will help our government track down those responsible,” said Sen. Rubio.
The post Cyber Incident Notification Act of 2021 Introduced in the Senate appeared first on HIPAA Journal.