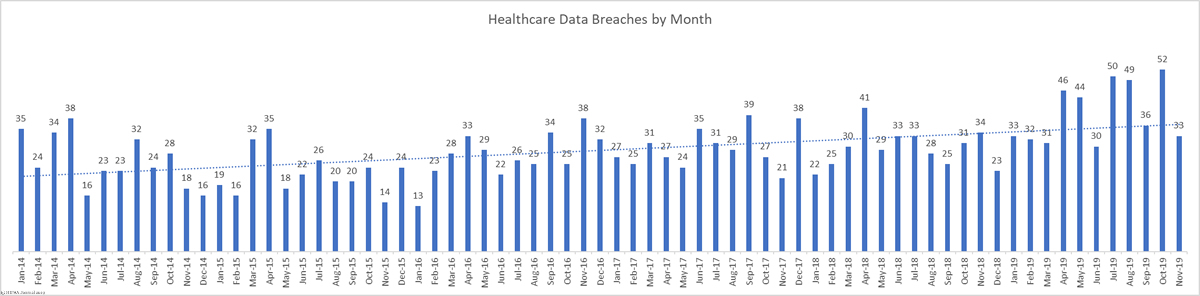
There was a 44.44% month-over-month increase in healthcare data breaches in October. 52 breaches were reported to the HHS’ Office for Civil Rights in October. 661,830 healthcare records were reported as exposed, impermissibly disclosed, or stolen in those breaches.
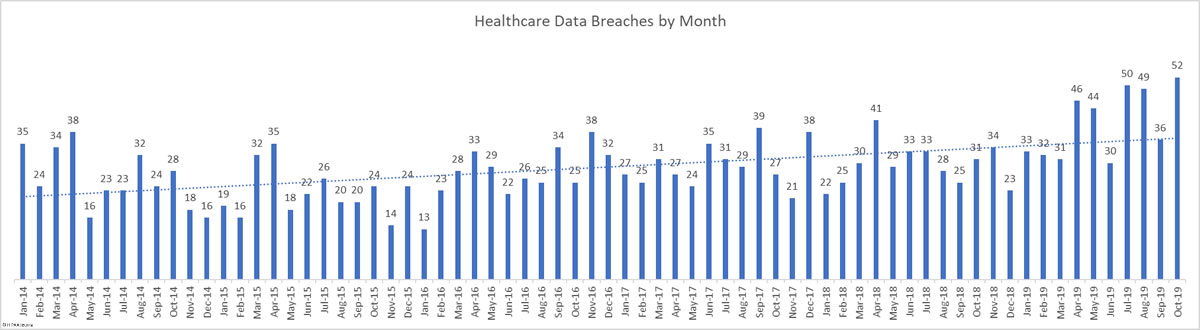
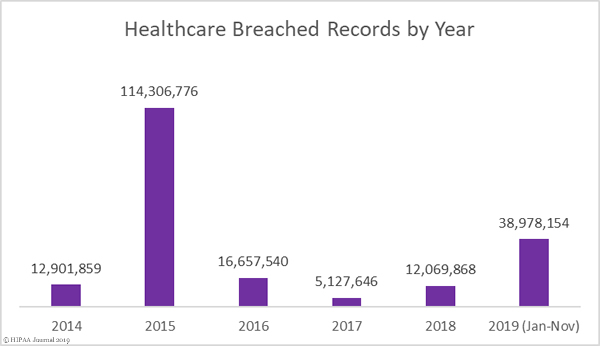
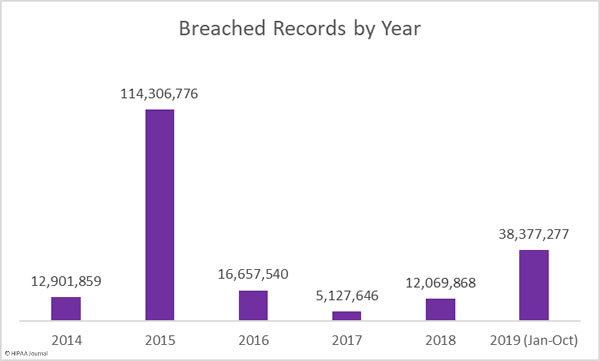
This month takes the total number of breached healthcare records in 2019 past the 38 million mark. That equates to 11.64% of the population of the United States.
Largest Healthcare Data Breaches in October 2019
| Breached Entity |
Entity Type |
Individuals Affected |
Type of Breach |
| Betty Jean Kerr People’s Health Centers |
Healthcare Provider |
152,000 |
Hacking/IT Incident |
| Kalispell Regional Healthcare |
Healthcare Provider |
140,209 |
Hacking/IT Incident |
| The Methodist Hospitals, Inc. |
Healthcare Provider |
68,039 |
Hacking/IT Incident |
| Children’s Minnesota |
Healthcare Provider |
37,942 |
Unauthorized Access/Disclosure |
| Tots & Teens Pediatrics |
Healthcare Provider |
31,787 |
Hacking/IT Incident |
| University of Alabama at Birmingham |
Healthcare Provider |
19,557 |
Hacking/IT Incident |
| Prisma Health – Midlands |
Healthcare Provider |
19,060 |
Hacking/IT Incident |
| South Texas Dermatopathology Laboratory |
Healthcare Provider |
15,982 |
Hacking/IT Incident |
| Central Valley Regional Center |
Business Associate |
15,975 |
Hacking/IT Incident |
| Texas Health Harris Methodist Hospital Fort Worth |
Healthcare Provider |
14,881* |
Unauthorized Access/Disclosure |
The largest healthcare data breach in October was reported by Betty Jean Kerr People’s Health Centers and was the result of a ransomware attack. At the time of issuing notifications, files that were encrypted in the attack remained locked. The decision was taken not to pay the ransom demand, but it was not possible to restore files from backups. Those files contained the health information of 152,000 patients.
The Kalispell Regional Healthcare data breach was due to a May 2019 phishing attack. An initial investigation did not uncover the extent of the breach. The forensic investigation revealed in August that the health information of up to 140,209 patients may have been accessed.
The Methodist Hospitals, Inc. data breach was also the result of a phishing attack. The incident was reported in October, but the initial email account compromise occurred in March 2019. Two accounts were breached for a total of four months.
South Texas Dermatopathology Laboratory is the last healthcare organization to report that its patients have been impacted by the data breach at the collection agency, AMCA. Its 15,982 records take the total number of individuals impacted by the AMCA breach to 26,059,725.
*Also of note is the data breach at Texas Health Resources. The breach makes the top 10 list of the most healthcare records exposed, but the breach was more far reaching than the table above shows. The Texas Health data breach involved a total of 82,577 records, but the breach was reported to the HHS’ Office for Civil Rights as 15 separate breaches, with one breach report submitted for each of its affected facilities. Had the incident been reported as a single incident, the month’s total would stand at 38 breaches – two more than September.
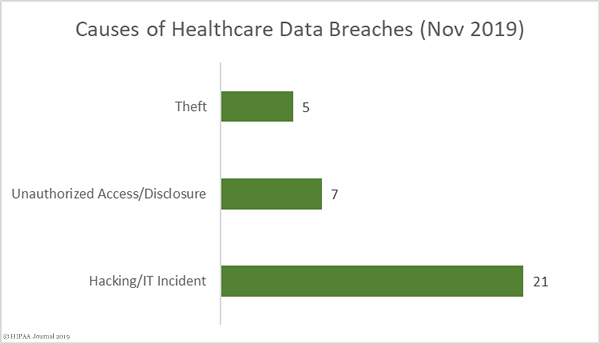
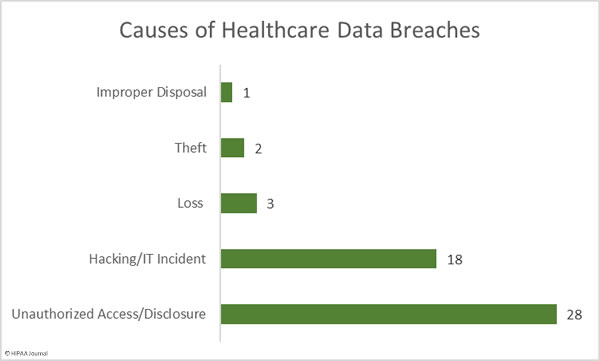
Causes of October 2019 Healthcare Data Breaches
There were 18 hacking/IT incidents reported in October involving 501,847 healthcare records. The average breach size was 27,880 records and the median breach size was 9,413 records.
There were 28 reported unauthorized access/disclosure incidents involving a total of 134,775 records. The mean breach size was 4,813 records and the median breach size was 2,135 records. Those incidents include the 15 separate breach reports from Texas Health Resources.
There were 5 loss/theft incidents involving 13,454 records. The mean breach size was 2,350 records and the median breach size was 2,752 records. One improper disposal incident was reported involving 11,754 records.
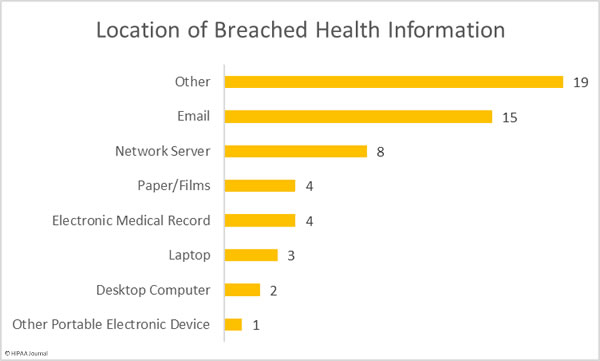
Location of Breached Health Information
Phishing continues to cause problems for healthcare organizations. Not only are healthcare providers struggling to block phishing attacks, they are also not detected quickly when they do occur. Several phishing attacks have been reported that have taken weeks to discover.
Multi-factor authentication can help to reduce the risk of stolen credentials being used by cybercriminals to access corporate email accounts, yet many healthcare organizations only implement this important security measure after a phishing attack has occurred.
This high number of “other” breaches is due to the mailing error at Texas Health, which accounts for 15 of the 19 incidents in the other category.
The majority of the network server breaches were due to ransomware attacks, which include the largest healthcare data breach of the month. That breach highlights just how important it is to ensure that a viable backup copy of all data is created, that the backup is tested to make sure data recovery is possible, and that at least one backup copy is stored on a non-networked device that is not exposed to the internet.
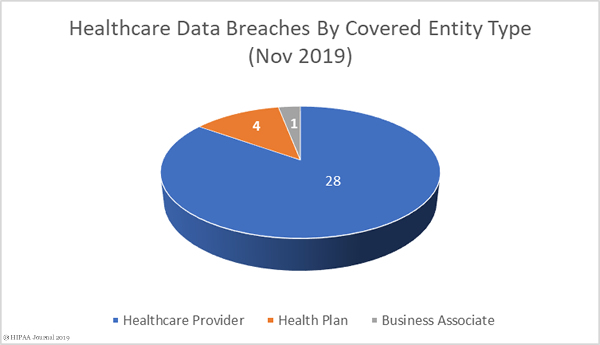
October 2019 Data Breaches by Covered Entity Type
Healthcare providers were the worst affected by data breaches in October with 45 reported incidents. Three breaches were reported by health plans, and four breaches were reported by business associates of HIPAA-covered entities. A further four breaches also had some business associate involvement but were reported by the covered entity.

October 2019 Healthcare Data Breaches by State
October saw healthcare organizations and business associates in 24 states report data breaches. With 15 breach reports coming from Texas Health, Texas was unsurprisingly the worst affected state with 17 incidents.
There were 4 breaches reported by entities based in Ohio, three breaches reported in California, and two breaches reported in each of Arkansas, Florida, Louisiana, Maryland, New Mexico, South Carolina, and Virginia. A single breach was reported in each of Alabama, Arizona, Georgia, Illinois, Indiana, Kentucky, Minnesota, Missouri, Mississippi, Montana, New York, Oregon, South Dakota, and Washington.
HIPAA Enforcement Actions in October 2019
A further two financial penalties for HIPAA violations were announced by the HHS’ Office for Civil Rights in October – One settlement and one civil monetary penalty.
OCR launched an investigation of Elite Dental Associates following a complaint from a patient who had some of her PHI publicly disclosed in response to a Yelp review. OCR found she was not the only patient to have had PHI disclosed in that manner. OCR also determined that the practice’s notice of privacy practices did not include sufficient information and was therefore not compliant with the HIPAA Privacy Rule. Elite Dental Associates agreed to settle its HIPAA violation case with OCR for $10,000.
OCR launched an investigation of Jackson Health System following the disclosure of PHI in the media. A photograph of an operating room display had been published which contained the health information of two individuals, including a well-known NFL star. The OCR investigation uncovered multiple Privacy Rule, Security Rule, and Breach Notification Rule violations spanning several years. OCR imposed a civil monetary penalty of $2,154,000 on Jackson Health System.
The post October 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.