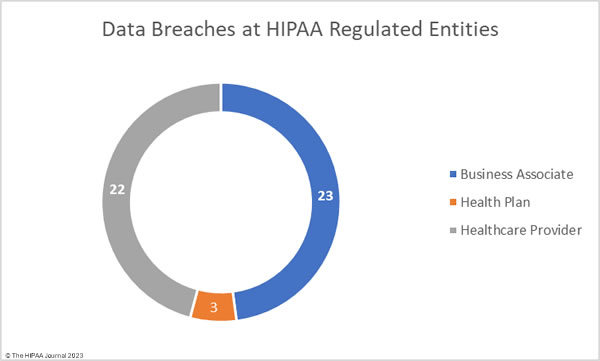
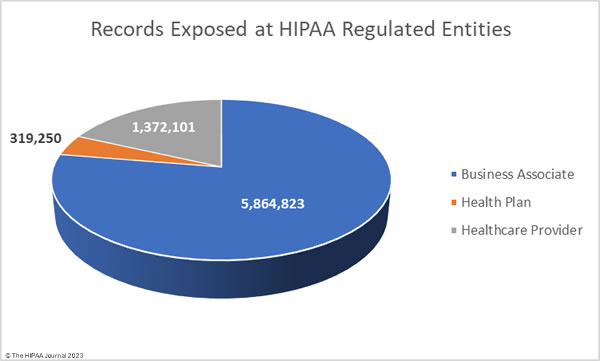
In 2019, SolarWinds experienced one of the worst cyber espionage incidents in history. The company is now being sued by the U.S. Securities and Exchange Commission (SEC) which alleges it defrauded investors and failed to maintain adequate internal security controls for several years.
The Largest and Most Sophisticated Attack the World has Ever Seen
In 2019, the Austin, TX-based software vendor was targeted by a nation-state hacking group that Microsoft tracks as Nobelium. Nobelium is a highly skilled hacking group that is believed to be backed by the Russian Foreign Intelligence Service. The hackers conducted a supply chain attack by gaining access to the SolarWinds network and added malicious code to an IT performance monitoring system called Orion. More than 30,000 public and private sector organizations use the Orion software to manage their IT resources.
When SolarWinds delivered updated software, backdoor malware was delivered that compromised the networks, systems, and data of its customers. More than 18,000 customers applied the update and infected their networks including U.S. government agencies. While the malware was installed on thousands of customers’ systems, SolarWinds said the threat group appeared to only target a small subset of high-value customers such as federal government agencies, and concluded that fewer than 100 of its customers had been actively targeted. Victims of the “SUNBURST” attack included FireEye, Microsoft, Deloitte, Cisco Systems, Intel Corp, Nvidia, VMWare, Belkin International, the California Department of State Hospitals, and the Departments of Homeland Security, State, Commerce, and the Treasury.
The threat actors gained access to the SolarWinds network in September 2019, tested the initial Orion code injection in October 2019, injected their malicious code into Orion in February 2020, and the backdoor malware was unknowingly distributed by SolarWinds in software updates that started on March 26, 2020. FireEye was the first to disclose the breach in December 2020. The purpose of the attack has not been confirmed, although it appears to have been a large-scale Russian espionage operation. Russia denied any involvement in the attack. Microsoft President, Brad Smith, said the SolarWinds hack was “the largest and most sophisticated attack the world has ever seen.”
Securities and Exchange Commission Alleges Fraud and Internal Control Failures
After an extensive investigation, the SEC filed a lawsuit on Monday against SolarWinds Corp. and its Chief Information Security Officer (CISO), Timothy G. Brown, alleging SolarWinds committed fraud by making misrepresentations to its investors about its cybersecurity practices and understated known vulnerabilities in its systems.
The SEC alleges that SolarWinds only disclosed vague and hypothetical risks to its investors when internally the company had acknowledged that there were specific cybersecurity deficiencies and escalating risks. Evidence uncovered by the SEC included an internal presentation created by a SolarWinds engineer and shared in 2018 with Brown, that stated its remote access configuration was not very secure and vulnerabilities could be exploited resulting in “major reputation and financial loss”. Further presentations in 2018 and 2019 were presented as evidence, where Brown had expressed concerns about the company’s security posture.
Further communications in 2019 and 2020 questioned whether SolarWinds was able to protect its critical assets from cyberattacks, and Brown expressed concern in June 2020 that SolarWinds software could be targeted in a much larger attack on its clients. Brown was also notified in September 2020 that the volume of security issues identified in the previous month was greater than the capacity of its engineering teams. Some of the vulnerabilities known to SolarWinds, which were not disclosed to its investors, were exploited by Nobelium in the Orion supply chain attack.
The SEC alleges that SolarWinds was aware of the vulnerabilities and risks, that Brown failed to address them adequately, and that the company could not provide reasonable assurances that its most important assets were adequately protected. Further, in December 2020, the company failed to disclose complete information about the SUNBURST attack, resulting in a 25% drop in stock price within 2 days of the disclosure, and a 35% fall in its stock price by the end of the month.
“From at least its October 2018 initial public offering through at least its December 2020 announcement that it was the target of a massive, nearly two-year long cyberattack, dubbed “SUNBURST,” SolarWinds and Brown defrauded investors by overstating SolarWinds’ cybersecurity practices and understating or failing to disclose known risks,” explained the SEC in a press release announcing the charges against SolarWinds.
“We allege that, for years, SolarWinds and Brown ignored repeated red flags about SolarWinds’ cyber risks, which were well known throughout the company and led one of Brown’s subordinates to conclude: ‘We’re so far from being a security-minded company,’” said Gurbir S. Grewal, Director of the SEC’s Division of Enforcement. “Rather than address these vulnerabilities, SolarWinds and Brown engaged in a campaign to paint a false picture of the company’s cyber controls environment, thereby depriving investors of accurate material information.”
The 68-page complaint was filed in the Southern District of New York and alleges violations of the antifraud provisions of the Securities Act of 1933 and the Securities Exchange Act of 1934. The defendants are also alleged to have violated reporting and internal controls provisions of the Exchange Act, and that Brown aided and abetted the company’s violations. The SEC seeks permanent injunctive relief, disgorgement with prejudgment interest, civil penalties, and an officer and director bar against Brown.
A spokesperson for SolarWinds provided a statement to The HIPAA Journal about the SEC lawsuit. “We are disappointed by the SEC’s unfounded charges related to a Russian cyberattack on an American company and are deeply concerned this action will put our national security at risk. The SEC’s determination to manufacture a claim against us and our CISO is another example of the agency’s overreach and should alarm all public companies and committed cybersecurity professionals across the country. We look forward to clarifying the truth in court and continuing to support our customers through our Secure by Design commitments”
The post SEC Sues SolarWinds over 2019 Cyberattack Alleging Company Defrauded Investors appeared first on HIPAA Journal.