A HIPAA risk assessment assesses threats to the privacy and security of PHI, the likelihood of a threat occurring, and the potential impact of each threat so it is possible to determine whether existing policies, procedures, and security mechanisms are adequate to reduce risks and vulnerabilities to a reasonable and appropriate level.
The requirements for covered entities and business associates to conduct a HIPAA risk assessment appear twice in the Administrative Simplification provisions of the Health Insurance Portability and Accountability Act. However, it may be necessary for organizations to conduct risk assessments beyond these requirements.
The first requirement to conduct a HIPAA risk assessment appears in the HIPAA Security Rule (45 CFR § 164.308 – Security Management Process). This standard requires covered entities and business associates to conduct an “accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI”.
The second requirement appears in the HIPAA Breach Notification Rule (45 CFR § 164.402). This standard only applies when there has been an impermissible acquisition, access, use, or disclosure of unsecured PHI (in any format), and a HIPAA risk assessment is necessary to determine whether the event is notifiable to HHS and the affected individual(s).
However, beyond the HIPAA risk assessment requirements of the HIPAA Security and Breach Notification Rules, risks exist to the confidentiality, integrity, and availability of PHI when it is not in electronic format – for example, when unauthorized disclosures are made verbally or when a printed medical report is left unattended in an area of public access.
Because of these risks, it may be necessary to conduct a HIPAA privacy risk assessment which not only takes into account risks to the confidentiality, integrity, and availability of non-electronic PHI, but which also covers individuals’ access rights (to their PHI), Business Associate Agreements, and other Organizational Requirements of HIPAA.
HIPAA Security Risk Assessment
The objective of a HIPAA security risk assessment is outlined in the General Rules (CFR 45 § 164.306) that precede the Administrative, Physical, and Technical Safeguards of the HIPAA Security Rule. These are to:
- Ensure the confidentiality, integrity, and availability of all electronic PHI the covered entity or business associate creates, receives, maintains, or transmits.
- Protect against any reasonably anticipated threats or hazards to the security or integrity of such information.
- Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required under subpart E of this part (the HIPAA Privacy Rule).
- Ensure compliance with this subpart (the HIPAA Security Rule) by its workforce. Note: This is achieved via security awareness training and the enforcement of a sanctions policy.
With regards to the Administrative, Physical, and Technical Safeguards of the HIPAA Security Rule, the General Rules allow a “flexibility of approach” in how the standards are implemented. Despite the flexibility of approach clause, it is important that all standards are implemented unless an implementation specification is not “reasonable and appropriate” and an equivalent alternate measure is implemented in its place. The full list of Administrative, Physical, and Technical implementation specifications is:
| Standards |
Sections |
Implementation Specifications
(R)=Required, (A)=Addressable |
Implementation Commentary |
| Security Management Process |
164.308(a)(1) |
Risk Analysis (R), Risk Management (R), Sanction Policy (R), Information System Activity Review (R) |
Organizations should perform a comprehensive risk analysis to identify potential vulnerabilities to ePHI. Develop and document a risk management strategy that prioritizes remediation activities. Enforce a sanction policy for employees who fail to comply with security policies, and implement tools for reviewing system activity regularly to detect any unauthorized access. |
| Assigned Security Responsibility |
164.308(a)(2) |
(R) |
Assign a senior-level individual (such as a CISO or Privacy Officer) to be responsible for ensuring the implementation and oversight of security policies and procedures across the organization. This individual should have authority and resources to enforce HIPAA compliance. |
| Workforce Security |
164.308(a)(3) |
Authorization and/or Supervision (A), Workforce Clearance Procedure (A), Termination Procedures (A) |
Establish and document procedures for supervising workforce members who access ePHI. Screen employees before granting access, and ensure prompt deactivation of accounts and access upon termination or role change to prevent unauthorized access. |
| Information Access Management |
164.308(a)(4) |
Isolating Health Care Clearinghouse Function (R), Access Authorization (A), Access Establishment and Modification (A) |
Create controls to isolate systems that manage ePHI, especially if a healthcare clearinghouse is part of a larger organization. Define procedures for granting, modifying, and removing user access based on job roles. Access should be reviewed periodically and updated accordingly. |
| Security Awareness and Training |
164.308(a)(5) |
Security Reminders (A), Protection from Malicious Software (A), Log-in Monitoring (A), Password Management (A) |
Develop a formal training program that includes regular security updates, awareness of phishing and malware threats, instructions for recognizing suspicious activities, and best practices for password management. Training should be documented and mandatory for all employees. |
| Security Incident Procedures |
164.308(a)(6) |
Response and Reporting (R) |
Develop and maintain a written incident response plan that defines how to detect, report, and respond to security incidents. Train staff on recognizing incidents, and test the plan through simulated exercises to improve readiness. |
| Contingency Plan |
164.308(a)(7) |
Data Backup Plan (R), Disaster Recovery Plan (R), Emergency Mode Operation Plan (R), Testing and Revision Procedure (A), Applications and Data Criticality Analysis (A) |
Implement a robust contingency planning framework that includes regular data backups, disaster recovery procedures, and emergency mode operations to ensure continuity of care. Conduct periodic testing and revise plans based on outcomes. Assess and prioritize data and application criticality to focus recovery efforts effectively. |
| Evaluation |
164.308(a)(8) |
(R) |
Regularly evaluate your security program’s effectiveness through audits, risk assessments, and policy reviews. Document evaluation results and implement improvements as needed to address any weaknesses or evolving threats. |
| Business Associate Contracts |
164.308(b)(1) |
Written Contract or Other Arrangement (R) |
Enter into Business Associate Agreements (BAAs) with all vendors who handle ePHI on your behalf. Ensure these agreements outline security responsibilities and establish that the associate is subject to HIPAA rules. |
| Facility Access Controls |
164.310(a)(1) |
Contingency Operations (A), Facility Security Plan (A), Access Control and Validation Procedures (A), Maintenance Records (A) |
Implement procedures to control physical access to facilities where ePHI is stored. This includes locking doors, using ID badges, and ensuring that emergency access is planned. Document maintenance activities and control how visitors and staff are validated before entering sensitive areas. |
| Workstation Use |
164.310(b) |
(R) |
Define appropriate uses of workstations that access ePHI. Restrict the use of unauthorized software and internet access, and place workstations in secure locations where unauthorized individuals cannot view screen content. |
| Workstation Security |
164.310(c) |
(R) |
Physically secure workstations by using cable locks, locking office doors, and ensuring terminals are not left unattended when logged in. This helps prevent unauthorized access or tampering. |
| Device and Media Controls |
164.310(d)(1) |
Disposal (R), Media re-use (R), Accountability (A), Data Backup and Storage (A) |
Develop policies for securely disposing of media containing ePHI, such as shredding paper records or wiping hard drives. Maintain a media tracking system to ensure accountability and store backups securely offsite or in the cloud. |
| Access Control |
164.312(a)(1) |
Unique User Identification (R), Emergency Access Procedure (R), Automatic Logoff (A), Encryption and Decryption (A) |
Assign unique user IDs for tracking access to systems containing ePHI. Ensure emergency access is available when needed. Set automatic logoff policies to reduce risk from unattended terminals, and encrypt data both at rest and in motion where appropriate. |
| Audit Controls |
164.312(b) |
(R) |
Use software tools that track and log all access to ePHI, including login attempts, file accesses, and modifications. Regularly audit these logs to identify unusual activity and respond to potential breaches. |
| Integrity |
164.312(c)(1) |
Mechanism to Authenticate Electronic Protected Health Information (A) |
Use checksums, digital signatures, or similar tools to ensure that ePHI has not been altered or destroyed in an unauthorized manner. Validate these mechanisms regularly to ensure reliability and security. |
| Person or Entity Authentication |
164.312(d) |
(R) |
Ensure users authenticate themselves before accessing ePHI using secure methods such as strong passwords, biometric verification, or multi-factor authentication. Regularly update and review authentication policies. |
| Transmission Security |
164.312(e)(1) |
Integrity Controls (A), Encryption (A) |
Encrypt data transmissions such as emails or data sent via APIs to protect ePHI from interception. Implement integrity controls like message authentication codes to ensure that data is not altered during transmission. |
The final section of the HIPAA Security Rule covers Business Associate Agreements and other Organizational Requirements. This section requires covered entities to ensure their Business Associate Agreements require business associate to comply with the HIPAA Security Rule and report any security incidents (not just data breaches) to the covered entity. With regards to the Organization Requirements, the standard in 45 CFR § 164.314 applies to group health plans; but all covered entities in hybrid, affiliated, or OHCA arrangements should review the content of this standard as well.
HIPAA Breach Risk Assessment
The second “required” HIPAA risk assessment is actually optional inasmuch as the HIPAA Breach Notification Rule states any that impermissible acquisition, access, use, or disclosure of PHI is presumed to be a breach unless a low probability of compromise can be demonstrated via a risk assessment that takes at least the following factors into account:
- The nature and extent of breached PHI including the types of identifiers and the likelihood of reidentification,
- The unauthorized person (if known) who acquired, accessed, or used the breached PHI or to whom an impermissible disclosure was made,
- Whether PHI was actually acquired or viewed (read HHS’ guidance on ransomware to establish what constitutes “acquired or viewed” in cyberattacks),
- The extent to which the risk to PHI has been mitigated.
The reason for the HIPAA breach risk assessment being described as optional is that covered entities and business associates could – if they wish – skip this HIPAA assessment and notify every impermissible acquisition, access, use, or disclosure of PHI. The drawback to this approach is that it may result in business disruption if HHS’ Office for Civil Rights feels your organization is experiencing an above-average number of data breaches and decides to conduct a compliance review.
It can also cause a loss of trust from individuals served by the organization if patients and plan members are receiving frequent breach notifications – especially if they are advised to take measures to protect themselves against fraud, theft, and loss unnecessarily because “breached” PHI has not actually been acquired or viewed. Although “optional”, it can be a good idea to conduct a HIPAA breach risk assessment to prevent unavoidable notifications.

HIPAA Privacy Risk Assessment
Due to the requirement to conduct risk assessments being in the HIPAA Security Rule, many covered entities and business associates overlook the necessity to conduct a HIPAA privacy risk assessment. A HIPAA privacy risk assessment is equally as important as a security risk assessment but can be a much larger undertaking depending on the size of the organization and the nature of its business.
In order to complete a HIPAA privacy risk assessment, an organization should appoint a Privacy Officer, whose first task it is to identify organizational workflows and get a “big picture” view of how the requirements of HIPAA Privacy Rule impact the organization´s operations. Thereafter the Privacy Officer needs to map the flow of PHI both internally and externally in order to conduct a gap analysis to identify where breaches may occur.
The final stage of a HIPAA privacy risk assessment should be the development and implementation of a HIPAA privacy compliance program. The program should include policies to address the risks to PHI identified in the HIPAA privacy assessment and should be reviewed as new work practices are implemented or new technology is deployed.
As required by 45 CFR § 164.530, it is essential employees are trained on any policies and procedures developed as a result of a HIPAA privacy risk assessment and when material changes to policies and procedures impact employees’ functions. Although covered entities and business associates may comply with this requirement “to tick the box”, better trained staff make fewer HIPAA errors, so training on HIPAA policies and procedures should be embraced as a risk mitigation strategy.
Not Identifying Risks Can be Costly
The severity of fines for non-compliance with HIPAA has historically depended on the number of patients affected by a breach of PHI and the level of negligence involved. Few fines are now issued in the lowest “Did Not Know” HIPAA violation category, because there is little excuse for not knowing a legal requirement exists to protect PHI.
More recently, the majority of fines have been under the “Willful Neglect” HIPAA violation category, where organizations knew – or should have known – they had a responsibility to safeguard PHI. Many of the largest fines – including the $5.5 million fine issued against the Advocate Health Care Network – are attributable to organizations failing to identify where risks to the integrity of PHI exist.
However, since the start of the second round of HIPAA audits, fines have also been issued for potential breaches of PHI. These are where flaws in an organization´s security have not been uncovered by a HIPAA risk assessment, or where no assessment has been conducted at all. In March 2016, North Memorial Health Care of Minnesota paid more than $1.5 million to settle related HIPAA violation charges.
It’s Not Just Large Organizations in the Firing Line
Although the majority of headlines relating to HIPAA violations concern large medical organizations and large fines for non-compliance, there are very many small medical practices also investigated by the Office for Civil Rights (OCR) or subject to HIPAA audits. Since 2003, OCR has received more than 300,000 reports of alleged HIPAA violations. Less than 2% of these relate to data breaches involving 500 individuals or more.
A significant problem for small and medium sized medical practices is that not all insurance carriers cover the cost of a HIPAA breach. The cost of a HIPAA breach not only includes the fine, but also the cost of hiring IT specialists to investigate the breach, the cost of repairing public confidence, and the cost of providing credit monitoring services for individuals. Insurers may also limit their coverage according to the nature of the HIPAA violation and the level of negligence.
Without insurance coverage, the cost of a HIPAA breach could potentially close a small medical practice. However, this scenario can be mitigated by conducting a HIPAA risk assessment and implementing measures to resolve any uncovered issues. An assessment can be complicated and time-consuming, but the alternative is potentially terminal to small medical practices and their business associates.
Business Associates Must Be Included
Every covered entity that creates, receives, maintains, or transmits PHI has to conduct an accurate and thorough HIPAA risk assessment in order to comply with the Security Management requirements of the HIPAA Security Rule. This condition of HIPAA compliance not only applies to medical facilities and health plans. Business associates, subcontractors, and vendors must also conduct a HIPAA security risk assessment. Similar to covered entities, fines for non-compliance can be issued by OCR against business associates for potential breaches of PHI.
OCR treats these risks seriously. In December 2014, the agency revealed that 40% of all HIPAA breaches involving an exposure of more than 500 patient records are attributable to the negligence of business associates. In June 2016, it issued its first fine against a business associate – the Catholic Health Care Services of the Archdiocese of Philadelphia agreeing to pay $650,000 following a breach of 450 records. The non-profit organization had failed to conduct a HIPAA risk assessment since 2013.
More recently, the proportion of data breaches attributable to a lack of compliance by business associates may appear to have reduced, but this is not necessarily the case. Under the HIPAA Breach Notification Rule (CFR § 164.410), a business associate is required to notify a covered entity when a breach of unsecured PHI occurs. It is then the covered entity’s responsibility to notify HHS and the affected individual(s) – so it may be the case many data breaches are recorded as being attributable to a covered entity when in fact a business associate is at fault.
Developing a Risk Management Plan and Implementing New Procedures
A HIPAA risk assessment should reveal any areas of an organization’s security that need attention. Organizations then need to compile a risk management plan in order to address the weaknesses and vulnerabilities uncovered by the assessment and implement new procedures and policies where necessary to close the vulnerabilities most likely to result in a breach of PHI.
The risk levels assigned to each vulnerability will give an organization direction on the priority that each vulnerability needs to be given. The organization can then create a remediation plan to tackle the most critical vulnerabilities first. The remediation plan should be complemented with new procedures and policies where necessary, and appropriate workforce training and awareness programs.
It has been noted by OCR that the most frequent reason why covered entities and business associates fail HIPAA audits is because of a lack of procedures and policies – or inadequate policies and procedures. It is important that the appropriate procedures and policies are implemented in order to enforce changes to the workflow that have been introduced as a result of the HIPAA risk assessment.
Tools to Assist with a HIPAA Risk Assessment
Conducting a HIPAA risk assessment on every aspect of an organization’s operations – not matter what its size – can be complex. This is particularly true for small medical practices with limited resources and no previous experience of complying with HIPAA regulations. To help reduce the complexity of conducting HIPAA risk assessments, in 2014, OCR released a downloadable Security Risk Assessment (SRA) tool that helps small and medium sized medical practices with the compilation of a HIPAA risk assessment.
The SRA tool is very helpful in helping organizations identify some locations where weaknesses and vulnerabilities may exist – but not all. In the User Guide accompanying the software, it is stated at the beginning of the document “the SRA tool is not a guarantee of HIPAA compliance”. This is because, although the tool consists of 156 questions relating to the confidentiality, availability, and integrity of all PHI, there are no suggestions on how assign risk levels or what policies and procedures to introduce.
Much the same applies to other third-party tools that can be found on the Internet. They may also help organizations identify some weaknesses and vulnerabilities, but not provide a fully compliant HIPAA risk assessment. Indeed, many third-party vendors publish disclaimers in the small print of their terms and conditions similar to that at the beginning of the SRA tool User Guide. The conclusion is that tools to assist with a HIPAA risk assessment can be helpful for identifying issues but are not suitable for providing solutions to all issues.
HIPAA Risk Assessment FAQ
Where are risks most commonly identified?
Where risks are most commonly identified vary according to each organization and the nature of its activities. For example, a small medical practice may be at greater risk of impermissible disclosures through personal interactions, while a large healthcare group may be at greater risk of a data breach due to the misconfiguration of cloud servers.
What is a “reasonably anticipated threat”?
A reasonably anticipated threat is any threat to the privacy of individually identifiable health information or to the confidentiality, integrity, or availability of PHI that is foreseeable. These not only include threats from external bad actors, but also threats originating from human error or a lack of knowledge due to a lack of training. This is why a “big picture” view of organizational workflows is essential to identify reasonably anticipated threats.
What is the difference between a risk assessment and a risk analysis?
The difference between a risk assessment and a risk analysis is that a risk assessment identifies the risks to HIPAA compliance, whereas a risk analysis assigns risk levels for vulnerability and impact combinations. The objective of assigning risk levels to each risk is so that risks with the potential to be most damaging can be addressed as priorities. Most HIPAA risk analyses are conducted using a qualitative risk matrix.
Who is responsible for conducting a HIPAA security risk assessment?
The responsibility for conducting a HIPAA security risk assessment usually lies with a HIPAA Compliance Officer; or, if the responsibility for HIPAA compliance is shared between a HIPAA Privacy Officer and a HIPAA Security Officer, the risk assessment and analysis should be conducted by the HIPAA Security Officer with assistance from his or her colleague depending on the nature of risks identified.
Are there different types of risk assessment for covered entities and business associates?
There are not different types of risk assessment for covered entities and business associates. Both covered entities and business associates need to conduct “A-to-Z” risk assessments for any Protected Health Information created, used, or stored. While business associates may experience a lower volume of PHI than a covered entity, the risk assessment has to be just as thorough and just as well documented.
What is a HIPAA risk assessment?
A HIPAA risk assessment is a risk assessment that organizations subject to the Administrative Simplification provisions of the Health Insurance Portability and Accountability Act have to complete in order to be compliant with the “Security Management Process” requirements. Non-compliant organizations have been filed for failing to comply with this requirement of HIPAA.
What is the difference between a HIPAA risk assessment and a HIPAA compliance assessment?
The difference between a HIPAA risk assessment and a HIPAA compliance assessment is that a HIPAA risk assessment identifies potential threats and vulnerabilities so measures can be implemented to mitigate their likelihood. A HIPAA compliance assessment is usually an assessment performed by a third party to assess an organization´s compliance with the HIPAA Privacy, Security, and Breach Notification Rules.
Why can I not find a HIPAA risk assessment template on the Internet?
You will not find a HIPAA risk assessment template on the Internet because covered entities and business associates vary significantly in size, complexity, and capabilities, and there is no “one-size-fits-all” HIPAA risk assessment. Due to the number of variables, there is no such thing as a HIPAA risk assessment template; and, if you do source a template from the Internet, you should treat it with caution as it may not include every potential risk to PHI maintained by your organization.
When is a HIPAA risk assessment necessary?
A HIPAA risk assessment is necessary in two instances. The first instance appears in the HIPAA Security Rule (45 CFR § 164.308 – Security Management Process). The second instance occurs under the HIPAA Breach Notification Rule (45 CFR § 164.402), which applies when there has been an impermissible acquisition, access, use, or disclosure of unsecured PHI. However, organizations should conduct risk assessments more often than these requirements, particularly related to non-electronic PHI and organizational requirements.
What is the objective of a HIPAA security risk assessment?
The objective of a HIPAA security risk assessment is to identify risks to the confidentiality, integrity, and availability of all electronic PHI the covered entity or business associate creates, receives, maintains, or transmits. The risk assessment should not only focus on external threats, but also those within the organization attributable to malicious insiders or a lack of security awareness training.
What factors are considered in a HIPAA breach risk assessment?
The factors considered in a HIPAA breach risk assessment include the nature and extent of breached PHI, the types of identifiers and the likelihood of re-identification, the unauthorized person who accessed or used the breached PHI, whether PHI was actually acquired or viewed, and the extent to which the risk to PHI has been mitigated.
What could be the consequence of not identifying risks to PHI in a risk assessment?
The consequences of not identifying risks to PHI in a risk assessment are an increased likelihood of a data breach or impermissible disclosure, and – following on from such an event – a sanction issued by HHS’ Office for Civil Rights for failing to conduct a thorough risk assessment. It is important to be aware there are no excuses for failing to conduct a thorough risk assessment as covered entities and business associates “know or should know” they have a responsibility to safeguard PHI.
Do the HIPAA risk assessment requirements apply to Business Associates?
The HIPAA risk assessment requirements apply to business associates as business associates are required to comply with the HIPAA Security and Breach Notification Rules and the two HIPAA standards relating to HIPAA risk assessments appear in these Rules. Business associates are also advised to conduct HIPAA Privacy Rule risk assessments if the nature of their activities for a covered entity could violate the privacy of individually identifiable health information.
What tools can assist organizations with a HIPAA risk assessment?
The tools that can assist organizations with a HIPAA risk assessment include a downloadable Security Risk Assessment (SRA) tool released by HHS’ Office for Civil Rights in 2014 to help small and medium-sized medical practices with the compilation of a HIPAA risk assessment. There are also many tools available from third party compliance experts that are best used for identifying issues in situations not covered by the Security Risk Assessment Tool (i.e., HIPAA Privacy Rule compliance).
The post HIPAA Risk Assessment appeared first on The HIPAA Journal.

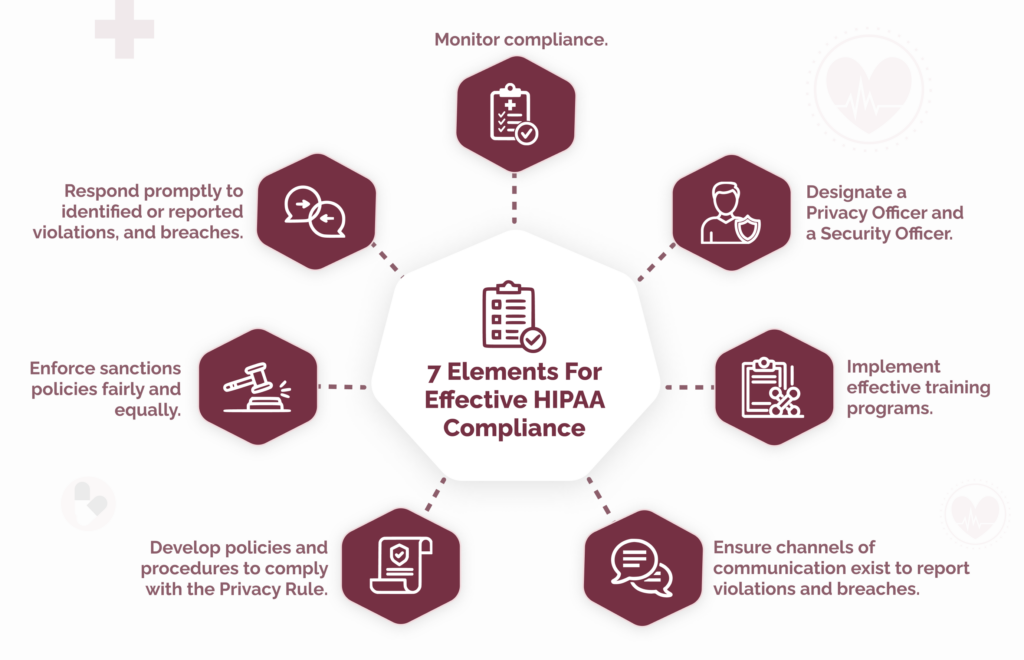
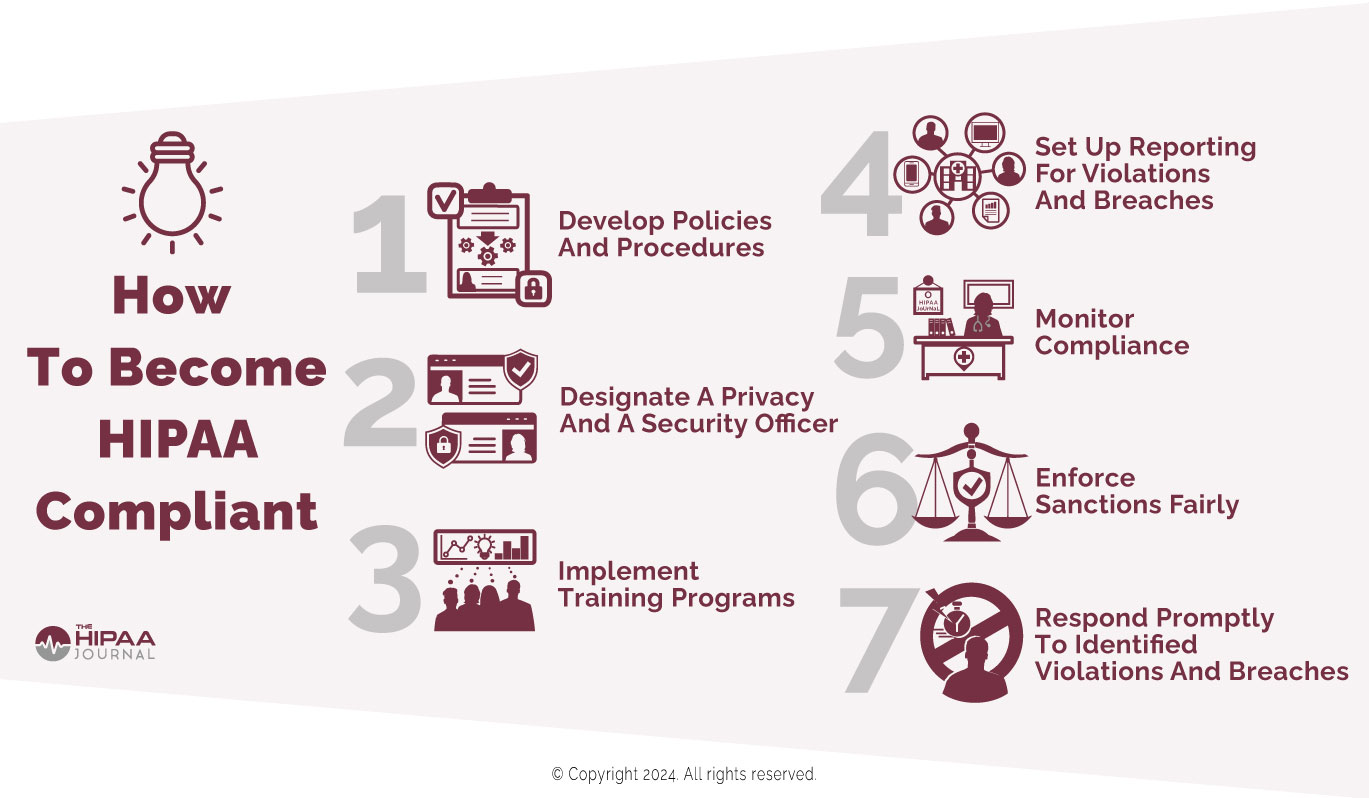
 Since the first appearance of the seven elements, some versions have been amended or extended to meet organizational or regulatory requirements.
Since the first appearance of the seven elements, some versions have been amended or extended to meet organizational or regulatory requirements.
 Adopting the seven elements of a compliance plan can be challenging for an organization starting from scratch. It can be difficult to get leadership buy-in because compliance is not perceived as a revenue generator, it can be difficult to define compliance roles in a complex regulatory environment, and it can be difficult to pull everything together with limited resources.
Adopting the seven elements of a compliance plan can be challenging for an organization starting from scratch. It can be difficult to get leadership buy-in because compliance is not perceived as a revenue generator, it can be difficult to define compliance roles in a complex regulatory environment, and it can be difficult to pull everything together with limited resources.