It has been 28 years since President Clinton signed the Health Insurance Portability and Accountability Act (HIPAA) into law – and 22 years since the first of the Administrative Simplification Rules became effective – but HIPAA compliance is still proving a challenge for many HIPAA-regulated entities. This article explores the current state of HIPAA and some of the main aspects of the HIPAA Rules that are proving difficult for HIPAA-regulated entities.
Predictions for 2024
- OCR will increase enforcement actions for violations of the HIPAA Security Rule that have contributed to data breaches and HIPAA Breach Notification Rule violations for failing to issue timely notifications to individuals whose PHI has been compromised in data breaches. 2024 will see record numbers of settlements and civil monetary penalties.
- The HIPAA Right of Access will continue to be an enforcement priority for OCR – This is low-hanging fruit. The investigations are straightforward and require few OCR resources and the findings of investigations are unlikely to face legal challenges.
- OCR is planning a HIPAA Security Rule update in Spring 2023 which we predict will include several new mandatory requirements for cybersecurity, including stricter access control requirements such as mandatory multi-factor authentication.
- A new rule will be introduced regarding disclosures of reproductive health information, which will be prohibited for reasons other than treatment, payment, and healthcare operations and for PHI to be used for identifying, investigating, and prosecuting patients, providers, and others involved in the provision of legal reproductive health care services, in response to the overturning of Roe v. Wade
- The lawsuit filed by the AHA in response to OCR’s December 2022 guidance on tracking technologies makes strong arguments that OCR has stretched the definition of protected health information to more than the current statute can bear. Should that challenge not prove to be successful, 2024 will see the first enforcement action over the use of tracking technologies on hospital websites. If the lawsuit is successful, further rulemaking will be proposed regarding tracking technologies to ensure patient privacy.
- The HHS’ Centers for Medicare and Medicaid Services (CMS) will introduce new cybersecurity requirements as a condition for participation in the Medicare and Medicaid programs
- State Attorneys General will step up enforcement of HIPAA compliance and will impose more financial penalties against healthcare organizations that have failed to meet minimum standards for cybersecurity.
HIPAA Enforcement in 2023
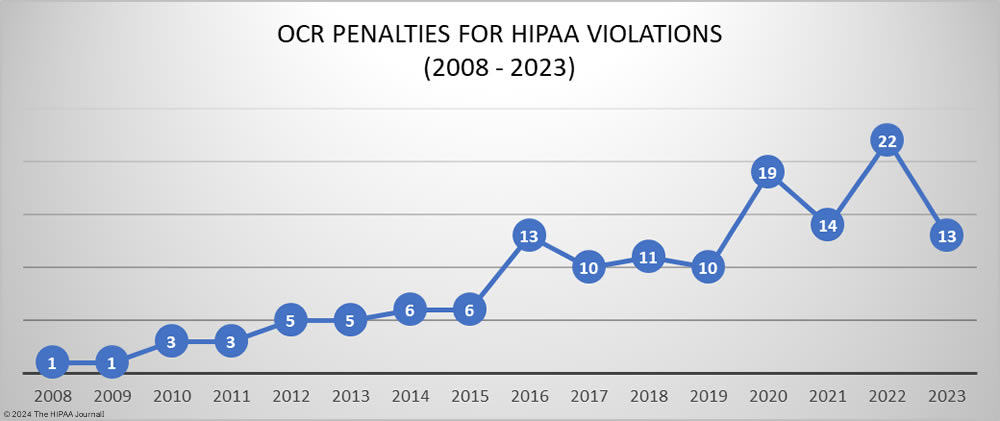
The HHS’ Office for Civil Rights (OCR) has been enforcing HIPAA compliance more aggressively in recent years and 2022 was a record year, with 22 penalties imposed to resolve violations of the HIPAA Rules. 17 of the 22 financial penalties imposed in 2022 resolved violations of the HIPAA Right of Access – the failure to provide individuals with timely access to their medical records. OCR’s HIPAA Right of Access enforcement initiative appears to have worked. In 2023, OCR only imposed 4 penalties for HIPAA Right of Access violations. The other 9 penalties were imposed for HIPAA Security Rule failures – risk analysis, technical and administrative safeguards, reviews of information system activity, and verification of identity – and other HIPAA Privacy Rule failures – disclosures of PHI in response to online reviews, disclosures of PHI to reporters, and a lack of policies and procedures/training to prevent HIPAA violations by employees.
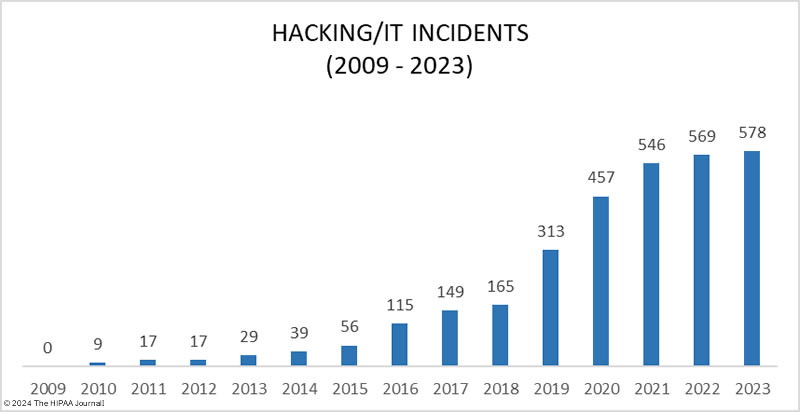
OCR has faced challenges with HIPAA enforcement due to a significant increase in its workload in recent years while its budget has remained flat. OCR investigates all data breaches of 500 or more records, and data breaches have been increasing at an alarming rate. OCR explained in its annual report to Congress that since fiscal year 2017, OCR has received a 100% increase in large breach reports, largely driven by an increase in hacking incidents, especially ransomware attacks. In 2021, 75% of breaches of 500 or more records were due to hacking compared to 41.6% of data breaches in 2017, and the problem is getting worse. In 2023, 79.7% of the year’s 725 data breaches were due to hacking.
Between 2017 and 2021, OCR also saw a 28% increase in complaints about potential HIPAA violations, which also need to be investigated. OCR’s hands are somewhat tied as funding has remained flat for years and OCR is also having to cope with inflationary increases. OCR explained in its 2022 report to Congress that it has been forced to decrease its enforcement staff by 45%, and with its resources under incredible strain, that naturally has an impact on the speed of investigations and the number of cases where financial penalties can be pursued.
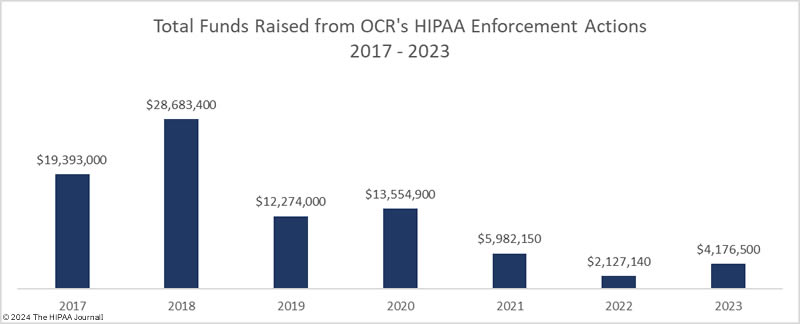
OCR can increase funding through its enforcement actions, but despite OCR more than doubling the number of settlements and civil monetary penalties (CMPs) in 2022 compared to 2017-2019 levels, OCR had a 92.6% reduction in total penalties compared to 2018, falling from $28.7 million in 2018 to just $2.13 million in 2022 and $4.18 million in 2023. The average HIPAA penalty has fallen from $2.6 million in 2018 (median: $500,000) to just $321,269 in 2023 (median: $100,000). The decrease in penalties is due to a reinterpretation of the language of the HITECH Act, which has seen the maximum penalties for HIPAA violations reduced in three of the four penalty tiers. OCR has asked Congress to increase the maximum penalties for HIPAA violations and is constantly pushing to have its budget increased, but there are no indications at present that additional funding will be provided.
The budgetary pressures have forced OCR to look at other ways of increasing funding such as improving efficiency and productivity through restructuring and getting better use of its existing resources. In 2023, OCR restructured and created a new enforcement division, which it is hoped will allow OCR to investigate data breaches faster, clear the current backlog of investigations, and impose more financial penalties. In 2024 we should start to see results from that restructuring. Time will tell how effective that move has been.
OCR Director, Melanie Fontes Rainer, has confirmed that OCR’s HIPAA Right of Access enforcement initiative is continuing and OCR is making compliance with HIPAA with respect to reproductive healthcare information an enforcement priority, as well as HIPAA Security Rule compliance to protect against the increasing numbers of hacking incidents.
State attorneys general also enforce the HIPAA Rules and in 2023, 16 investigations resulted in settlements to resolve allegations of violations of HIPAA and state privacy laws. State attorneys general in California, Colorado, Florida, Indiana, New York, New Jersey, Ohio, Oregon, and Pennsylvania have taken action against HIPAA-regulated entities for security failures that have led to data breaches, and there were three multi-state actions, including a $49.5 million settlement with Blackbaud to resolve violations of HIPAA and state laws that led to its 5.5 million record data breach.
One of the latest actions, taken against Refuah Health Center Inc. by the New York Attorney General involved a $450,000 financial penalty to resolve multiple violations of the HIPAA Security Rule. The settlement also included the requirement for $1.2 million to be invested in improving cybersecurity. This could become common in enforcement actions as a way of helping to ensure that similar breaches do not occur in the future.
The State of HIPAA Compliance
OCR has conducted two rounds of compliance audits to assess the state of HIPAA compliance since the HIPAA Privacy and Security Rules were enacted. The second phase of HIPAA audits was launched in 2016, and while OCR has announced its intention to conduct an ongoing program of compliance audits, they have failed to materialize due to budget constraints and it is unlikely that those plans will be resurrected until OCR’s funding issues have been resolved. The 2016-2017 HIPAA audit program identified many areas of noncompliance. Most covered entities were found to have failed to have achieved compliance in the following areas:
- HIPAA Security Rule risk analysis and risk management requirements
- Timely breach notifications and adequate content of breach notifications
- Prominent posts of Notices of Privacy Practices on websites and insufficient content of those notices
- Timely responses to individuals’ right of access requests and charges for copies of medical records
It has been 6 years since the second phase of the compliance audits came to an end and many of the compliance issues identified by OCR continue to pose problems for HIPAA-regulated entities, as can be seen in OCR’s enforcement actions, which give an indication of the current state of HIPAA compliance.
Most Common HIPAA Violations in OCR’s Enforcement Actions (2020-2023)
| HIPAA Violation | Number of Cases |
| HIPAA right of access | 45 |
| Risk analysis | 13 |
| Reviews of system activity | 5 |
| Risk management | 4 |
| Notice of Privacy Practices | 4 |
| Audit controls | 3 |
| Business associate agreements | 3 |
| Appointment of a HIPAA Privacy Officer | 2 |
| Impermissible disclosure on social media/Internet | 3 |
| Lack of technical safeguards | 3 |
| Technical and nontechnical evaluation | 3 |
| HIPAA Privacy Rule policies | 2 |
Top HIPAA Security Rule Compliance Challenges in 2023
Complying with all HIPAA provisions and implementation specifications can be a challenge, especially for smaller healthcare providers and business associates who do not have extensive resources available to devote to HIPAA compliance. While there are many aspects of the HIPAA Security Rule that can prove challenging, there are some common areas of vulnerability that are identified time and again in OCR’s investigations.
Risk Analyses
The HIPAA Security Rule mandates that regulated entities must conduct comprehensive and accurate organization-wide risk analyses to identify risks and vulnerabilities to electronic protected health information (ePHI). The risk analysis process needs to be ongoing, and the best practice is to conduct these at least annually or as needed, such as following any material change to policies and procedures or changes in technology. The risk analysis must be comprehensive, which means an organization must identify all ePHI within the organization, external ePHI created received, or maintained by business associates, and all threats to that information must be identified, including human, natural, and environmental threats to ePHI and the systems on which the information is stored. The HHS has developed a Security Risk Assessment Tool to help regulated entities with this vital process.
Risk Management Processes
Once risks and vulnerabilities have been identified they must be subjected to risk management processes and be reduced to a low and acceptable level in a timely manner. Risks must be assessed and remediations prioritized to ensure the risks that are most likely to be exploited are addressed first. Risk management processes also need to be extended to third parties – business associates – which means performing due diligence on vendors throughout the supply chain and implementing processes to identify, assess, and manage vendor risk at each stage of the vendor life cycle – onboarding, ongoing, and offboarding. Reducing risk exposure from vendor relationships is one of the biggest security challenges in healthcare in 2024 and a pressing issue, as hackers are actively targeting the supply chain.
Technical Security Controls
The HIPAA Security Rule does not specify the technical controls that should be implemented to secure systems containing ePHI, as these need to be based on the specific IT architectures of each regulated entity. It is the responsibility of each regulated entity to ensure that appropriate security controls are implemented and that they are effective at reducing risk. Security controls need to be regularly subjected to security assessments to make sure they have been implemented correctly, are operating as intended, and are achieving the desired outcome. HIPAA-regulated entities should conduct vulnerability scans and consider penetration testing to gain a better understanding of vulnerabilities to allow them to be properly managed.
Audit Controls and Information System Activity Reviews
All IT systems that contact ePHI must have audit controls and create logs of system activity and information system activity reviews should be conducted on audit logs, access reports, and security incident tracking reports. Despite information system activity reviews being a requirement of the HIPAA Security Rule, OCR’s investigations have revealed many organizations only conduct reviews on an ad-hoc basis in response to potential security incidents. Regular reviews allow HIPAA-regulated entities to rapidly identify unauthorized access to ePHI by malicious insiders and hackers. All too often, regulated entities discover unauthorized access by insiders and hackers, which has been ongoing for many months or years.
Access Controls
Technical policies and procedures need to be developed, implemented, and maintained for all electronic information systems that contain or allow access to ePHI to only allow access to persons or software programs that have been granted access rights per the organization’s access management policies and procedures. Access controls need to be based on the principle of least privilege, and access must be promptly revoked when individuals leave employment or no longer require access to ePHI. Ineffective access controls can be exploited by malicious actors to move laterally within networks and gain access to huge volumes of ePHI.
Telehealth Services
In response to the pandemic, OCR introduced telehealth flexibilities to make it easier for HIPAA-regulated entities to provide virtual care to clients and exercised enforcement discretion with regard to the technologies that can be used to provide these services. Now that the COVID-19 Public Health Emergency has been declared over, that period of enforcement discretion is due to terminate. OCR’s notice of enforcement discretion for telehealth expired at 11:59 p.m. on May 11, 2023, but HIPAA-regulated entities were given a 90-day transition period that came to an end on August 9, 2023. Now, all telehealth platforms must be fully compliant with the HIPAA Security Rule.
Challenges with HIPAA Privacy Rule Compliance in 2024
There are several aspects of HIPAA Privacy Rule compliance that are likely to prove challenging for HIPAA-regulated entities in 2024 and OCR has confirmed that these HIPAA Privacy Rule issues are still or will be enforcement priorities in 2023 and beyond.
Timely Access to Medical Records
The 2016 HIPAA compliance audits identified widespread noncompliance with the HIPAA Right of Access and increasing numbers of complaints were being received from individuals struggling to obtain copies of their medical records. OCR launched a new compliance initiative in 2019 targeting noncompliance with the HIPAA Right of Access, and the bulk of OCR’s subsequent enforcement actions to date have been for noncompliance with the HIPAA Right of Access. OCR is continuing with this enforcement initiative, and further, the proposed Privacy Rule changes that are expected to be finalized in 2024 will likely see the time frame for providing records decrease from 30 days to 15 days.
Tracking Technologies
In 2022, investigations into the use of tracking technologies on websites revealed the extent to which these third-party code snippets were being used by healthcare organizations. The code snippets collect valuable data on websites and web app user activity, which can be used to improve those services; however, the code can also collect identifiable health information and transmit that information to third parties. Those third parties typically do not sign business associate agreements, and using the code without a BAA in place or first obtaining consent from individuals to share that information is a HIPAA violation. OCR issued guidance on tracking technologies and HIPAA in December 2022 and the OCR Director has issued a statement confirming OCR will be enforcing this aspect of compliance. Many lawsuits have been filed against healthcare providers over privacy violations related to the use of tracking technologies, some of which have resulted in multi-million-dollar settlements. Whether there will be enforcement will hinge on the ruling in a lawsuit filed against the HHS by the AHA, which challenges the legality of its guidance and is attempting to prevent OCR from enforcing the guidance.
Disclosures of Reproductive Health Information
The decision of the Supreme Court in Dobbs v. Jackson Women’s Health Organization removed the federal right to abortion, leaving it to individual states to decide on the legality of abortions in their respective states. As of January 2024, 14 states have implemented total bans on abortions, a further 2 have placed 6-week limits, and another 6 have implemented bans that are not yet being enforced due to legal challenges.
Fears exist that some anti-abortion states may attempt to take legal action against individuals who facilitate terminations in states where abortion is legal as well as prosecuting individuals who travel out of state to have abortions in more permissive states. OCR is concerned the threat of criminal activity may prevent some patients from sharing important health information with their healthcare providers. Consequently, OCR is proposing a new category of PHI for reproductive health information. If finalized, Covered Entities will only be allowed to disclose reproductive health information (other than for TPO purposes) to third parties who attest the disclosure will not be used to prosecute facilitators of terminations in states where abortions are legal. False attestations will be considered wrongful disclosures under §1177 of the Social Security Act.
Staff Training
The Verizon Data Breach Investigations Report highlighted the extent to which data breaches are caused by human error. Out of all data breaches analyzed by Verizon in 2022, 82% involved the human element. Those data breaches include misconfigurations, responses to phishing and social engineering attacks, failures to set strong passwords, and other mistakes. These mistakes often expose ePHI and make it easy for hackers to gain access to healthcare networks. The only way of tackling human error is through education. The HIPAA Privacy Rule requires regulated entities to provide training on HIPAA policies relevant to each individual’s role, while the HIPAA Security Rule requires a security awareness training program. In the case of the latter, increasing the frequency of training can help to create a security culture and eradicate bad security practices.
Looking Forward – Pending Changes to the HIPAA Rules
While updates to the HIPAA Rules are made fairly infrequently, there are pending changes to the HIPAA Privacy Rule, that are due to be finalized in 2024. OCR has also recently announced its intention to improve privacy protections for reproductive health information through new HIPAA rulemaking, and the HHS’ Centers for Medicare and Medicaid Services (CMS) has proposed updates to transaction code sets to enable the electronic transmission of healthcare attachment transactions. States are also introducing new laws to better protect the privacy of state residents and ensure they are notified in the event of privacy breaches. Staying up to date with changes to state laws and ensuring compliance will be an ongoing challenge.
In December 2023, OCR also published its Healthcare Cybersecurity Strategy which outlined its plans for improving the resiliency of the healthcare industry to cyberattacks. OCR said it will be establishing voluntary Healthcare and Public Health Sector-specific Cybersecurity Performance Goals (HPH CPGs) and will be incentivizing healthcare organizations to adopt these goals. The priority is raising baseline cybersecurity across the healthcare sector by providing incentives to achieve essential HPH CPGs and encouraging the adoption of enhanced HPH CPGs. While HPH CPGs will be voluntary initially, OCR intends to make the essential HPH CPGs mandatory and enforceable. OCR is seeking additional funding for enforcement but also to help healthcare organizations make the necessary investments in cybersecurity and cover the initial costs.
OCR believes regulatory updates are required in addition to funding and voluntary goals to drive the behavioral changes needed across the sector and has confirmed that a much-needed update to the HIPAA Security Rule will be proposed in Spring 2024, which will include new cybersecurity requirements. Action is also being taken at the state level to improve healthcare cybersecurity. In response to a large increase in cyberattacks on hospitals in New York State, the New York Attorney General is proposing new cybersecurity requirements for New York hospitals and has also budgeted for assistance for hospitals that have limited resources to help them comply with the new regulations.
While the proposed HIPAA updates are intended to improve the privacy and security of personally identifiable information and reduce the administrative burden on HIPAA-regulated entities, they are a cause of concern for many HIPAA-regulated entities that will have to spend considerable time and effort implementing the changes and ensuring their employees are fully trained. The HHS will provide a grace period to allow the changes to be implemented before compliance becomes mandatory, but it is important to start updating policies and procedures as soon as possible to ensure compliance with these new requirements to ensure the deadlines are not missed.
Steve Alder, Editor-in-Chief, HIPAA Journal
The post State Of HIPAA – 2024 Predictions appeared first on HIPAA Journal.