OCR Opens HIPAA Compliance Investigation of Change Healthcare
The HHS’ Office for Civil Rights has opened an investigation of Change Healthcare following its February 21, 2024, cyberattack, just three weeks after the attack occurred. Typically, OCR’s investigations of cyberattacks and data breaches are initiated several months after the breach is reported, which may even be years after the breach occurred. In this case, the incident has not even been reported to OCR as it is still under investigation. Change Healthcare has only just brought its systems back online – 99% of pharmacy and payment platforms are now up and running according to a recent statement – and there are still 5 weeks before the HIPAA Breach Notification Rule’s deadline for reporting breaches is reached.
The rapidly initiated investigation is in response to the magnitude of the incident, which is disrupting health care and billing information systems nationwide and has been estimated to be costing providers well over a billion in reimbursement losses per day due to Change Healthcare’s systems being unavailable. The disruption caused to providers that use Change Healthcare’s systems is causing extreme financial difficulties and some providers have had to make difficult decisions about whether they can continue to operate. As such, the incident poses a direct threat to critically needed patient care and essential operations of the healthcare industry.
In a “Dear Colleague” letter uploaded to the HHS website, OCR Director Melanie Fontes Rainer said “Given the unprecedented magnitude of this cyberattack, and in the best interest of patients and health care providers, OCR is initiating an investigation into this incident. OCR’s investigation of Change Healthcare and UHG will focus on whether a breach of protected health information occurred and Change Healthcare’s and UHG’s compliance with the HIPAA Rules.”
OCR also explained in the letter that its interest in other entities that partner with Change Healthcare and UnitedHealth Group is secondary. While OCR is not prioritizing investigations of healthcare providers, health plans, and business associates that have partnered with Change Healthcare or UnitedHealth Group, OCR has taken the opportunity to remind them that they have regulatory responsibilities under HIPAA and they must ensure that they have business associate agreements in place and that they issue timely notifications to the HHS and any affected individuals. In the letter, the OCR Director shared resources to assist HIPAA-regulated entities with protecting records, systems, and patients from cyberattacks.
“This is an unusual move by OCR but given the far-reaching impact of the cyberattack and the massive effect it is having on healthcare organizations that rely on Change Healthcare’s services and systems, the breach warrants swift investigation to determine if Change Healthcare and its parent company were fully compliant with the HIPAA Rules,” commented Steve Alder, Editor-in-Chief, The HIPAA Journal.
Lisa Plaggemier, Executive Director of the National Cybersecurity Alliance (NCA), offered some advice for readers of The HIPAA Journal and shared some of the lessons that can be learned from this devastating cyberattack.
The cyberattack on UnitedHealth Group and Change Healthcare serves as a stark reminder of the critical need for robust cybersecurity measures within the healthcare sector. Firstly, healthcare organizations must prioritize comprehensive risk assessments and implement stringent security protocols to safeguard sensitive patient data. This includes regular security audits, employee training on cybersecurity best practices, encryption of data both at rest and in transit, and proactive monitoring for suspicious activities. Furthermore, investments in cutting-edge cybersecurity technologies and partnerships with reputable cybersecurity firms can bolster defenses against evolving cyber threats.
Additionally, the incident highlights the indispensable role of government oversight and regulation in safeguarding healthcare data. Government agencies, such as the Department of Health and Human Services’ Office for Civil Rights, play a vital role in enforcing compliance with health privacy laws, such as the Health Insurance Portability and Accountability Act (HIPAA). Through rigorous investigations and enforcement actions, regulatory bodies can hold healthcare entities accountable for lapses in data protection and ensure swift responses to cyber incidents. Moreover, collaboration between government agencies, law enforcement, and private sector stakeholders is essential to enhance threat intelligence sharing and coordinate responses to cyber threats, ultimately bolstering the resilience of the healthcare sector against future cyberattacks.
In light of the recent cyberattack on UnitedHealth Group and Change Healthcare, consumers and patients also play a crucial role in protecting their personal health information. One key step is to remain vigilant about sharing sensitive data, both online and offline, only with trusted healthcare providers and entities. Patients should inquire about the security measures implemented by their healthcare providers, including encryption protocols and data breach response plans. Additionally, individuals should regularly review their medical bills and insurance statements for any discrepancies or unauthorized charges, which could indicate fraudulent activity. Furthermore, maintaining strong, unique passwords for healthcare portals and enabling multi-factor authentication can add an extra layer of security to personal health information. By staying informed, vigilant, and proactive, consumers can contribute to safeguarding their own health data and mitigating the risks posed by cyber threats in the healthcare sector.
The post OCR Opens HIPAA Compliance Investigation of Change Healthcare appeared first on HIPAA Journal.
HHS opens probe into hack at UnitedHealth unit – AOL
HHS Office for Civil Rights Issues Letter and Opens Investigation of Change Healthcare Cyberattack – HHS.gov
Is age part of HIPAA? – HIPAA Challenges – allnurses
How Much Does HIPAA Compliance Cost? – HIPAA Journal
How Much Does HIPAA Compliance Cost?
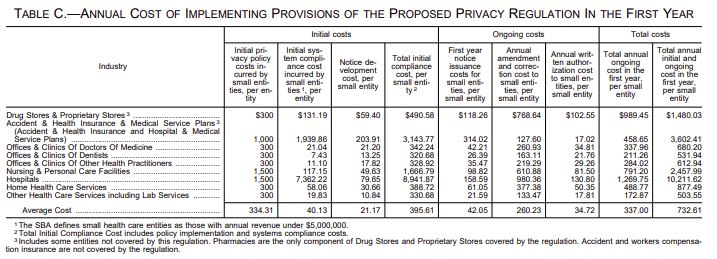
Estimates of how much does HIPAA compliance cost have risen sharply since HHS forecast costs of between $458 and $3,602 for health plans – and of between $1,269 and $10,211 for hospitals – for complying with the Privacy Rule in 1999. A quarter of a century later, mid-range estimates of how much does HIPAA compliance cost fall into the range of between $80,000 and $120,000.
The Health Insurance Portability and Accountability Act was passed in 1996 in an attempt to reform the health insurance industry. To neutralize the costs of the reforms to the industry and protect tax revenues, Congress added measures to reduce fraud and abuse in the healthcare industry and simplify the administration of healthcare transactions such as eligibility checks, authorizations for treatment, and claims for reimbursement.
The measures to simplify the administration of healthcare transactions led to the publication of the Administrative Simplification Regulations (Subchapter C of Subtitle A of the Public Welfare Code). The Regulations include the HIPAA General Provisions, the Transaction Rules and Code Sets, and the HIPAA Privacy, Security, and Breach Notification Rules. Since their publication, the Administrative Simplification Regulations have been updated multiple times.
What Does it Mean to be HIPAA Compliant?
What it means to be HIPAA compliant is that an individual or organization that qualifies as a covered entity or business associate (see “Who Needs to be HIPAA Compliant?” below) complies with all the applicable standards, and implementation specifications of the Administrative Simplification Regulations. For some individuals and organizations, this can mean complying with far fewer standards and implementation specifications than for others.
For example, whereas a large health system that conducts healthcare transactions in-house will have to comply with most of the Administrative Simplification Regulations, a cloud service provider that provides “no view” data storage services as a business associate will only have to comply with the applicable standards and implementation specifications of the Security and Breach Notification Rules – reducing how much it can cost to become HIPAA compliant.
Who Needs to be HIPAA Compliant?
An individual or organization needs to be HIPAA compliant if they qualify as a HIPAA covered entity – i.e., a health plan, a health care clearinghouse or a healthcare provider that conducts electronic transactions for which the Department of Health and Human Services (HHS) has published standards in 45 CFR Part 162. It is important to be aware that not all providers of insured health benefits or all healthcare providers qualify as HIPAA covered entities.
In addition, a third party service provider that provides a service to or on behalf of a HIPAA covered entity also needs to be HIPAA compliant if the service involves the creation, receipt, storage, or transmission of Protected Health Information (PHI). Service providers that provide such services are referred to as “business associates”, and not only must business associates comply with all applicable standards of HIPAA, but their subcontractors must do as well.
How Much Does HIPAA Compliance Cost According to HHS
HHS has only produced partial estimates of how much does HIPAA compliance cost because the different types of organizations covered by HIPAA and because – at the time the proposed Security Rule was published – it was assumed that covered entities who conducted electronic healthcare transaction would already have most of the required security measures in place, and would only need to implement minimal additional measures to become HIPAA compliant.
However, in the Notice of Proposed Rulemaking for the Privacy Rule, HHS estimated the average cost of implementing the provisions of the Privacy Rule as between $337 and $732 depending on the size of an organization and the nature of its activities. This estimation of how much HIPAA compliance cost in 1999 failed to take into account that many covered entities were already required to comply with state laws relating to the privacy of healthcare data.
Similarly, when HHS estimated the average cost of compliance with the Omnibus Final Rule in 2013 at $1,040 per organization, the estimate failed to take into account that many states already had breach notification laws. As 75% of the 2013 Omnibus Final Rule estimate was based on the cost of breach notifications – and the number of future breaches that would incur costs was unknown – it is probably best to ignore this estimated cost of HIPAA compliance.
How Much Does HIPAA Compliance Cost in 2024
Taking inflation into account, the cost of HIPAA compliance in 2024 should be double what it cost in 1999, but that is unlikely to be the case. Although there is no consensus of opinion among compliance professionals, the mid-range estimate seems to be between $80,000 and $120,000 depending on whether compliance efforts are mostly in-house (potentially with help from software or consultants) or completely outsourced.
In reality, how much does HIPAA compliance cost in 2024 depends on the size, nature, and distribution of an organization, the degree of compliance with other healthcare regulations, and the resources available to the organization to become HIPAA compliant. Due to these variables, it may cost less for a larger, multi-specialty, multi-location health system to become HIPAA compliant than for a smaller, single-location dental practice.
Does Size, Nature, and Distribution Matter?
The size, nature, and distribution of an organization is not such a big factor in determining how much does HIPAA compliance cost compared to some other variables. For example, it might be assumed that a large health system providing a variety of medical services to patients in multiple physical service delivery sites and in the community is going to have a larger workforce to train, more standards to comply with, and more compliance challenges to overcome.
However, the HIPAA regulations protecting the privacy of individually identifiable health information are the same regardless of the medical service provided, the additional standards protecting sensitive psychiatry, SUD, and reproductive healthcare information are similar (and only apply to a subset of the workforce), and the implementation specifications for securing PHI apply whether colleagues are communicating PHI from adjoining offices or from miles apart.
Compliance with Other Healthcare Regulations
How much does HIPAA compliance cost is more likely to be affected by the degree of compliance with other healthcare regulations than by an organization’s size, nature, and distribution. For example, a health system that complies with the conditions for participation in Medicare is going to be much closer to HIPAA compliance than a dental practice that only bills health plans and has not implemented any measures to protect the privacy or security of PHI.
Compliance with federal non-health regulations and voluntary standards can also make a difference to how much does HIPAA compliance cost. If a health system complies with OSHA and voluntary standards such as SOC 2, ISO/IEC 27001, or NIST SP 800-66r2, the health system will most likely already have the measures in place to comply with HIPAA’s Disaster Recovery, Contingency Operations Planning, and Emergency Access requirements.
The Resources Available to Become HIPAA Compliant
Similarly, the resources available to become HIPAA compliant are also going to affect how much does HIPAA compliance cost. A large health system will already likely be paying for legal, compliance, and IT services – either directly (i.e., via employed members of the workforce) or indirectly (i.e., outsourced contractors). The health system may only need to redirect the resources it is already paying for in order to fund becoming HIPAA compliant.
A smaller, single-location dental practice might also be paying directly or indirectly for legal, compliance, and IT services. However, the existing paid-for resources are less likely to have the capacity to scale up in order to support HIPAA compliance (depending on the existing degree of HIPAA compliance), and it is more likely that the smaller, single-location dental practice will have to engage third party consultants or outsource certain compliance activities.
How Much Does HIPAA Non-Compliance Cost?
There is no one-size-fits-all scale for how much does HIPAA non-compliance cost because penalties for HIPAA compliance failures are assessed according to multiple factors. These factors include (but are not limited to):
- Whether the covered entity/business associate knew or should have known the compliance failure was a violation of HIPAA.
- The nature and extent of the violation(s), the number of individuals affected, and how long the violation(s) continued.
- Whether the violation(s) resulted in physical, financial, and/or reputational harm, or prevented/hindered access to health care.
- The history of prior compliance and whether violations of a similar nature have previously been reported or notified to HHS.
- How the covered entity/business associate has responded to previous compliance failures or technical assistance provided by HHS.
Even when the penalties for HIPAA violations are not financial, they can still incur indirect costs. HHS Office for Civil Rights initiates hundreds of compliance reviews each year; and, when non-compliance with HIPAA is identified, organizations are required to adopt corrective actions. The corrective actions can include the implementation of further safeguards, revisions to policies and procedures, and workforce retraining – all of which can be disruptive and costly.
Calculating How Much Does HIPAA Compliance Cost
To calculate how much does HIPAA compliance cost, a covered entity or business associate needs to review their current degree of healthcare regulatory compliance against a HIPAA compliance checklist and then conduct a gap analysis to identify what measures need to be implemented to raise HIPAA compliance to the required level. The measures can then be costed to calculate how much achieving a state of HIPAA compliance will cost.
However, HIPAA compliance is an ongoing requirement. Achieving “point-in-time” HIPAA compliance is not sufficient to excuse a covered entity or business associate from a penalty for a violation of HIPAA, and organizations not only need to calculate how much does HIPAA compliance cost, but also how much maintaining a healthcare compliance program will cost. Organizations requiring help with these calculations should seek professional compliance advice.
The post How Much Does HIPAA Compliance Cost? appeared first on HIPAA Journal.
Florida Legislature Passes Bill Providing Companies with Immunity from Data Breach Lawsuits
Companies in Florida may soon be immune from lawsuits if they suffer data breaches provided that prior to the cybersecurity incident, they have been maintaining a cybersecurity program that substantially aligns with industry standards, cybersecurity frameworks such as the NIST CSF, or a state or federal law such as HIPAA, and they comply with Florida’s data breach notification law. The cybersecurity incident liability bill – House Bill 473 – was recently passed by the Florida legislature and now heads to the state governor’s desk for his signature. Governor Ron DeSantis is expected to sign the bill into law.
Currently, healthcare organizations in the state of Florida have a degree of immunity from regulatory sanctions and penalties if they can demonstrate that they have implemented recognized security practices that have been continuously in place for the 12 months prior to a data breach, following a 2021 amendment to the HITECH Act. When determining appropriate penalties in its enforcement activities, the HHS’ Office for Civil Rights will consider the recognized security practices that have been in place and will reduce the penalties accordingly. There are no provisions in HITECH or HIPAA that provide immunity from or limit liability in class action data breach lawsuits.
Any significant healthcare data breach is likely to see one – or most likely several – class action data breach lawsuits filed for exposing sensitive data, and the cost of defending against those lawsuits and paying settlements is considerable. If lawsuits are likely to be filed following any data breach regardless of the cybersecurity measures that have been implemented, then businesses may simply accept the risk and fail to invest appropriately in cybersecurity.
The aim of the bill is to incentivize organizations to invest in security and implement cybersecurity measures to protect the personal data they collect and store as it is in their best interests to do so. The bill goes a step further than similar laws that have been enacted in Ohio, Utah, and Connecticut, where companies that implement appropriate security measures have limited protection against class action data breach lawsuits. In Florida, companies will be provided with immunity from more types of claims and there are no carve-outs for failing to address known threats, and immunity is not conditioned on compliance with a cybersecurity program. Should the bill be signed into law it will be effective immediately.
While the law will undoubtedly be good for businesses, the benefits to consumers are questionable. If the law does have the intended effect and companies invest in cybersecurity as a result, Florida residents will be less likely to have their data compromised. However, in the event of a data breach, consumers will have to cover the cost of protecting themselves against identity theft and fraud and will incur out-of-pocket expenses, as well as costs if they do fall victim to identity theft and fraud if they cannot recover those costs by other means.
The post Florida Legislature Passes Bill Providing Companies with Immunity from Data Breach Lawsuits appeared first on HIPAA Journal.