International Law Enforcement Operation Takes Down LockBit RaaS Infrastructure
The prolific LockBit ransomware-as-a-service (RaaS) group has been severely disrupted by a global law enforcement operation that has seen much of the group’s infrastructure seized, including servers, its affiliate portal, Tor sites, Stealbit data exfiltration tool, public-facing data leak site, and more than 200 cryptocurrency wallets. Two individuals who conducted attacks using LockBit ransomware have been arrested in Poland and Ukraine, and they will be extradited to the United States to face trial. The French and U.S. judicial authorities have also issued three international arrest warrants and five indictments. More than 1,000 decryption keys were obtained and a free decryptor for LockBit 3.0 has been created and made available on the No More Ransom portal. The seizure of the cryptocurrency wallets means it might be possible for victims to recover some of the ransoms they paid.
LockBit was branded the world’s most harmful cybercrime group by the UK’s National Crime Agency (NCA). The RaaS group has been active for the past four years and has targeted thousands of organizations around the world, and in Q3, 2023 alone the group added 275 new victims to its data leak site. The group has conducted many attacks on critical infrastructure entities, including healthcare organizations, and the attacks have caused billions of dollars of losses. According to the Department of Justice, the group conducted attacks on more than 2,000 victims, issued ransom demands of hundreds of millions of dollars, and had been paid at least $120 million.
Law enforcement agencies in 10 countries participated in “Operation Cronos,” which was headed by the NCA and coordinated by Europol and Eurojust. The operation commenced in April 2022 and has resulted in 34 servers being taken down in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States, and the United Kingdom, and more than 14,000 rogue accounts have been identified and referred for removal by law enforcement. The accounts were used by LockBit members for hosting tools and software used in attacks and for storing data stolen from victims.
The affiliate panel now displays a message for all affiliates from the NCA, FBI, Europol, and the Operation Cronos Law Enforcement Task Force. “Law enforcement has taken control of LockBit’s platform and obtained all the information on its servers. This information relates to the LockBit group and you, their affiliate. We have source code details of the victims you have attacked, the amount of money stolen, chats, and much, much more. You can thank LockBitSupp and their flawed infrastructure for this situation… we may be in touch with you very soon.”
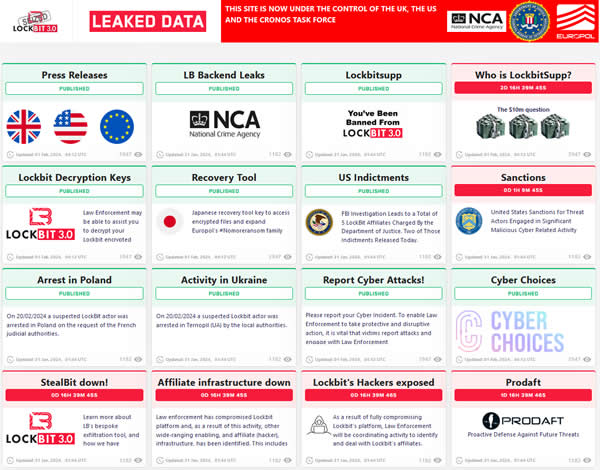 LockBitSupp is the threat actor that controls the LockBit RaaS operation, with the LockBitSupp persona believed to be run by one or two individuals. The Russian-speaking threat actor claimed that the law enforcement operation exploited a critical PHP vulnerability, CVE-2023-3824, that was first disclosed in August 2023. The vulnerability leads to a stack buffer overflow, potential memory corruption, and remote code execution.
LockBitSupp is the threat actor that controls the LockBit RaaS operation, with the LockBitSupp persona believed to be run by one or two individuals. The Russian-speaking threat actor claimed that the law enforcement operation exploited a critical PHP vulnerability, CVE-2023-3824, that was first disclosed in August 2023. The vulnerability leads to a stack buffer overflow, potential memory corruption, and remote code execution.
The takedown of the group’s infrastructure is significant and the extent of the data breach will be of concern to affiliates of the group, especially those that reside in locations where they can be reached by law enforcement. It is unlikely, however, that the core members of the group will be brought to justice as they are believed to reside in Russia. They may choose to rebuild and return with a new operation, as ransomware groups typically do following law enforcement disruption.
“A vast amount of data gathered throughout the investigation is now in the possession of law enforcement,” explained Europol. “This data will be used to support ongoing international operational activities focused on targeting the leaders of this group, as well as developers, affiliates, infrastructure and criminal assets linked to these criminal activities.”
The U.S. Department of State is also offering a reward of up to $15 million via the Transnational Organized Crime Rewards Program for anyone with information about LockBit associates, including a reward of up to $10 million for information leading to the identification or location of any individual who holds a leadership role in the LockBit operation, and a reward offer of up to $5 million for information that leads to the arrest and/or conviction of any individual conspiring to participate in or attempting to participate in LockBit ransomware activities.
The post International Law Enforcement Operation Takes Down LockBit RaaS Infrastructure appeared first on HIPAA Journal.
NetSource One Strengthens Compliance Measures with SOC 2 Type 2 & HIPAA Certification – PR Web
What is Healthcare Regulatory Compliance? – HIPAA Journal
What is Healthcare Regulatory Compliance?
Healthcare regulatory compliance is the practice of meeting or exceeding the requirements of all applicable federal, state, local, and industry regulations and any voluntary standards a healthcare organization adopts in order to demonstrate a good faith effort to comply with the regulations. Due to the number of regulations and standards a healthcare organization may have to comply with, healthcare regulatory compliance is complex and has the potential for failure in many different areas.
Most healthcare organizations are required to comply with dozens of federal, state, local, and industry regulations. The regulations can cover subjects as diverse as building safety, data security, codes of conduct, the regulation of controlled substances, and the provision of medical assistance in emergency circumstances. To complicate the challenge of healthcare regulatory compliance, some regulations conflict with each other, while others duplicate standards from other regulations.
It can also be the case that some regulations exempt healthcare organizations from complying with some standards, but not with other standards. An example of this scenario is when a state privacy law exempts HIPAA covered entities from complying with its standards relating to Protected Health Information (PHI), but not from complying with its standards for individually identifiable non-health information maintained by the same organization in a separate non-protected record set.
The Importance of Regulatory Compliance in Healthcare
To understand the importance of regulatory compliance in healthcare, it is necessary to understand the purposes of federal, state, local, and industry regulations and why they exist. Although it is not practical to provide a synopsis of – and the reason for – every healthcare regulation, the following list provides a cross section of regulations a healthcare organization may have to comply with.
The Health Insurance Portability and Accountability Act (HIPAA)
The purpose of HIPAA was to reform the health insurance industry. But, due to concerns that the cost of the reforms would be passed onto employers and employees in the form of increased, tax-deductible premiums – and the impact this would have on Treasury revenues – Congress adopted measures to mitigate the costs to the health insurance industry by reducing fraud, waste, and abuse in the healthcare industry and simplifying the administration of healthcare transactions.
The measures to simplify the administration of healthcare transactions led to the HIPAA Privacy, Security, and Breach Notification Rules. These Rules stipulate permissible uses and disclosures of PHI to protect patient privacy, the safeguards required to ensure the confidentiality, integrity, and availability of electronic PHI, and the procedures for alerting individuals when their health information has been accessed, viewed, or acquired without authorization.
The Conditions of Participation in Medicare and Medicaid
The original conditions of participation in federal Medicare and Medicaid programs were published in 1966 by the Social Security Administration to provide a baseline of care for qualifying beneficiaries throughout the country. As the Medicare and Medicare programs expanded, further conditions for participation have been added, and the responsibility for enforcing compliance transferred to HHS’ Centers for Medicare and Medicaid Services (CMS).
The penalties for non-compliance with the conditions of participation are the same as the penalties for non-compliance with HIPAA – plus non-compliant organizations can also be excluded from federal health programs. CMS has yet to issue a civil monetary penalty for non-compliance with the conditions of participation, but has referred non-compliant healthcare organizations to HHS’ Office of Inspector General when there is evidence of fraud, abuse, or misconduct.
HHS’ Office of Inspector General Exclusions List
HHS’ Office of Inspector General (OIG) investigates individuals and organizations suspected of fraud, patient abuse and neglect, or other incidents of misconduct – for example, violations of the Social Security Administration’s Anti-Kickback Statute or the Stark Law. Individuals and organizations found guilty of fraud, abuse, or misconduct are excluded from the Medicare and Medicaid programs in addition to being fined and/or given a custodial sentence.
In the context of healthcare regulatory compliance, healthcare organizations are prohibited from conducting business with, or engaging the services of, an individual or organization that appears on the HHS OIG Exclusions List. Healthcare organizations that violate this condition of participation can themselves be excluded from the program, fined up to $20,000 per violation, and made to repay up to three times the amount claimed for non-compliant services or items.
The Emergency Medical Treatment and Active Labor Act (EMTALA)
Another way in which healthcare organizations can be excluded from federal health programs is by violating EMTALA. Congress passed EMTALA in 1986 to eliminate the practice of “patient dumping” – a practice in which healthcare organizations refused to provide emergency medical treatment to individuals because of their inability to pay. The Act also prohibits healthcare organizations from discharging patients prematurely because of high anticipated treatment costs.
To comply with EMTALA, healthcare organizations must implement policies for ED workforces to ensure an appropriate screening exam is provided and, if the patient has an emergency medical condition, stabilizing treatment is provided or the patient is transferred to a facility with appropriate capabilities. In addition to being excluded from federal health programs, healthcare organizations that violate EMTALA can be fined up to $129,233 per violation and subject to civil damages.
The Occupational Safety and Health Act
The Occupational Safety and Health Act (OSH Act) in 1970 created the Occupational Safety and Health Administration (OSHA). The Administration was authorized to develop standards for workplace safety and health to reduce the number of avoidable accidents, injuries, and workplace illnesses attributable to poor working conditions. The Administration enforces the standards via a program of inspections and investigations in response to accident reports and workforce complaints.
OSHA compliance consists of complying with applicable safety and health standards, maintaining injury and illness reports, and providing safety training to members of the workforce exposed to specific risks (i.e., bloodborne pathogens). Healthcare organizations that fail to comply with the OSHA requirements can be fined up to $161,323 per violation depending on the nature of the violation, the organization’s history of compliance, and its cooperation during an investigation.
Payment Card Industry Data Security Standards (PCI DSS)
PCI DSS is a contractual obligation (rather than a rule or regulation) that has the objective of ensuring the security of debit and credit card transactions and protecting cardholders against fraud, theft, and the misuse of their personal information. The actual standards themselves closely match the Technical Safeguards of the HIPAA Security Rule, so healthcare organizations that comply with the Security Rule will automatically be in compliance with PCI DSS.
However, when personal information and/or payment information is stored independently of PHI, different breach notification procedures apply if the information is accessed, viewed, or acquired without authorization. The procedures are most often governed by states’ data breach rules; but it is important to be aware that some data breach laws extend across state boundaries and apply to citizens of the state regardless of where the breach of personal or payment information occurs.
Food and Drug Administration (FDA) Regulations
Among other responsibilities, the FDA ensures the safety and effectiveness of drugs, biologics, and medical devices. However, because the Administration is the enforcer of more than two hundred laws, regulations, and standards, there is no one-size-fits-all approach to FDA regulatory compliance in healthcare. It is up to each healthcare organization to determine which FDA laws, regulations, and standards apply to their activities and implement compliance programs for each.
To ensure compliance with healthcare-related laws, the FDA’s Office of Regulatory Affairs conducts regulatory assessments, inspects drug facilities, oversees laboratory testing and clinical trials, and investigates fraudulent or other criminal activities that threaten public health. The Office has the authority to seize unregulated goods, obtain injunctions against healthcare organizations operating unlawfully, or pursue criminal convictions through the FDA’s Office of Criminal Investigations.
Physician Payments Sunshine Act /CMS Open Payments
The Physician Payments Sunshine Act is an Act requiring the transparency of financial relationships between healthcare organizations and drugs companies – including suppliers of biologics, medical supplies, and medical devices. The purpose of the Act is to prevent conflicts of interest that could result (for example) in a patient being provided with an unsuitable medication or an unnecessary treatment because the healthcare provider has a financial interest in doing so.
CMS oversees compliance with the Act via the Open Payments Program, which does not prohibit healthcare organizations from receiving payments or items of value from drugs companies, but requires that payments are reported accurately, completely, and in a timely manner. CMS has the authority to audit healthcare organizations in federal health programs for compliance with the Sunshine Act, and can impose civil monetary penalties of up to $1 million per violation for non-compliance.
State Privacy and Data Security Legislation
State privacy and data security legislation can create more compliance headaches for healthcare organizations than the web of federal legislation. To date, thirteen states have passed some form of consumer protection, privacy, and/or data security legislation, while a further eighteen states have legislation at the committee stage or beyond. In many cases, state legislation can increase an organization’s healthcare regulatory compliance obligations by filling the gaps in federal legislation.
An example of this is the Texas Medical Record Privacy Act which defines covered entities as any person or organization that assembles, collects, analyzes, uses, evaluates, stores, or transmits PHI. This means that a healthcare organization that does not qualify as a HIPAA covered entity or business associate still has to comply with the HIPAA regulations in respect of any PHI relating to a resident of Texas – regardless of where the healthcare organization is located.
Local Fire, Building, Noise, and Safety Codes
Local fire, building, noise, and safety codes can also increase an organization’s healthcare regulatory compliance obligations by requiring more stringent protections for patients, the workforce, and the community in which the organization is located. Although the financial penalties for local code violations are minor in relation to the penalties for violations of federal or state regulations, citations can be issued for some unusual violations (i.e., the failure to remove graffiti from a building).
With regards to requiring more stringent protections than federal or state regulations, there are likely examples of this in every location. For example, in Dallas, §403.11.1.3 of the local Fire Code has more stringent qualifications for standby personnel than OSHA; in New York, §28.103.21 of the Construction Code has more stringent injury reporting requirements than OSHA; and hospitals in Atherton, CA, are not be permitted to use gas-powered leaf blowers under §8.16.040 of the Atherton Municipal Code.
Healthcare Regulatory Compliance Issues and Challenges
In addition to the healthcare regulatory compliance issues and challenges that have already been mentioned (i.e., conflicts, duplications, and partial exemptions) a further issue is that – although individual regulations may not change frequently – because a healthcare organization may have to comply with (say) twelve regulations, if each regulation adds or changes a standard once a year, it is the equivalent of a change to the healthcare regulatory compliance requirements once a month.
The frequency of regulatory changes is not necessarily a challenge if, for example, the change relates to a little used process or a process that is used by a small number of the workforce (i.e. electronic signatures in healthcare transactions). However, larger scale changes – such as changes to the HIPAA Privacy Rule – will have an impact on most healthcare organizations, their Notices of Privacy Practices, workforce policies and procedures, and sanctions for impermissible disclosures.
When regulatory changes represent a material change (for example, the changes to disclosures of reproductive health information), it is also necessary for healthcare organizations to provide members of the workforce whose roles are affected by the changes with additional HIPAA training. While it can be the case that the timing of the mandated training coincides with scheduled refresher training, it can equally be the case additional resources may be required to comply with the training requirement.
As one-off events, these healthcare regulatory compliance issues and challenges are usually manageable. However, over the next year or so, a large number of regulatory changes are scheduled that could create simultaneous compliance challenges for organizations impacted by the FDA’s proposals for remote regulatory assessments, the new CMS requirements for hospital epidemic preparedness, and HHS’ recently released Cybersecurity Performance Goals.
The Benefits of Adopting Voluntary Healthcare Standards
Voluntary healthcare standards are standards that most often exceed the healthcare regulatory compliance requirements to better protect patients, healthcare data, or members of the workforce. Examples include the Joint Commission accreditation standards, ISO 7101:2023, SOC 2, and the American Institute of Architects’ Acoustic Guidelines in Healthcare Facilities (which benefits patients, visitors, and members of the healthcare organization’s workforce).
Adopting voluntary healthcare standards often requires just a little more effort than complying with regulatory standards. For example, if an organization already complies with HIPAA, OSHA, and CMS’ conditions for participation in Medicare, there are minimal training, administrative, and documentation requirements to complete before an organization can apply for ISO 7101:2023 certification to demonstrate it has an effective healthcare quality management system.
The benefit of adopting a voluntary healthcare standard in this example is that organizations that achieve ISO 7101:2023 certification must continue to monitor clinical and non-clinical performance to continually improve their processes and results. Healthcare organizations that comply with this voluntary requirement will simultaneously be complying with matching HIPAA, OSHA, and CMS mandatory requirements – mitigating the risk of non-compliance across the matching requirements.
In addition, achieving an accreditation or certification of voluntary compliance not only demonstrates a good faith effort to comply with mandatory healthcare regulations – which can mitigate a penalty for non-compliance in certain circumstances – but it can also enhance an organization’s brand reputation and can give it a competitive advantage. This may be extremely valuable for a business associate being evaluated by a covered entity for a lucrative contract.
How Software can Support Healthcare Compliance Efforts
It is not difficult to see how the number of mandatory regulations and voluntary standards a healthcare organization may have to comply with – and the volume of changes that might occur as a result – can increase the potential for compliance failures. Nor is it difficult to see how a well-resourced compliance team using a mature risk management strategy might still overlook a critical implementation specification due to the number of similar requirements.
To mitigate the risk of being swamped by regulations and standards, or overlooking a critical implementation specification, healthcare organizations should evaluate customizable healthcare regulatory compliance software. Software solutions for healthcare regulatory compliance are getting more sophisticated, and can be used to determine when one standard conflicts with or duplicates another, or when a state regulation partly exempts an organization from compliance.
When configured to meet an organization’s requirements, healthcare regulatory compliance software can produce guided risk assessments for each business unit and, once the risk assessments are concluded, a corrective action plan if compliance gaps are identified. The software can also be used to assess what changes to policies, procedures, and business practices may be required due to changes to or new regulatory standards. Organizations interested in taking advantage of healthcare regulatory compliance software are advised to seek professional compliance advice.
The post What is Healthcare Regulatory Compliance? appeared first on HIPAA Journal.
