December 2023 Healthcare Data Breach Report
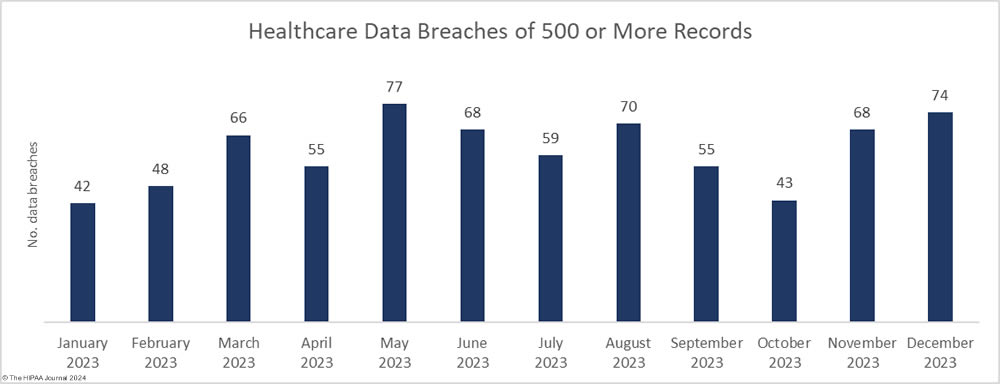
There was no letup in healthcare data breaches as the year drew to a close, with December seeing the second-highest number of data breaches of the year. The Department of Health and Human Services (HHS) Office for Civil Rights received 74 reports of healthcare data breaches of 500 or more records in December, which helped make 2023 a record-breaking year for healthcare data breaches. While there may still be some late additions to the list, as of January 18, 2023, 725 data breaches of 500 or more healthcare records have been reported to OCR in 2023 – The highest number since OCR started publishing records of data breaches on its “Wall of Shame.” To add some perspective, that is more than twice the number of data breaches that were reported in 2017.
It is not just the number of data breaches that is concerning. Healthcare data breaches have been increasing in severity and there have been ransomware attacks that have seen patients contacted and threatened directly with the exposure of their sensitive health data. Many of the data breaches reported in 2023 have been on a colossal scale, with December no exception with two multi-million-record data breaches reported.
Since 2009, when OCR created its Wall of Shame, the number of breached records has been trending upwards, but even the most pessimistic of security professionals would not have predicted at the start of 2023 that there would be such a massive rise in breached records. 2021 was a bad year with 45.9 million records breached, and 2022 was worse with 51.9 million breached records, but in 2023, an astonishing 133 million records were exposed or stolen. On January 18, 2023, the OCR breach portal showed 133,068,542 individuals had their protected health information exposed or stolen in 2023.
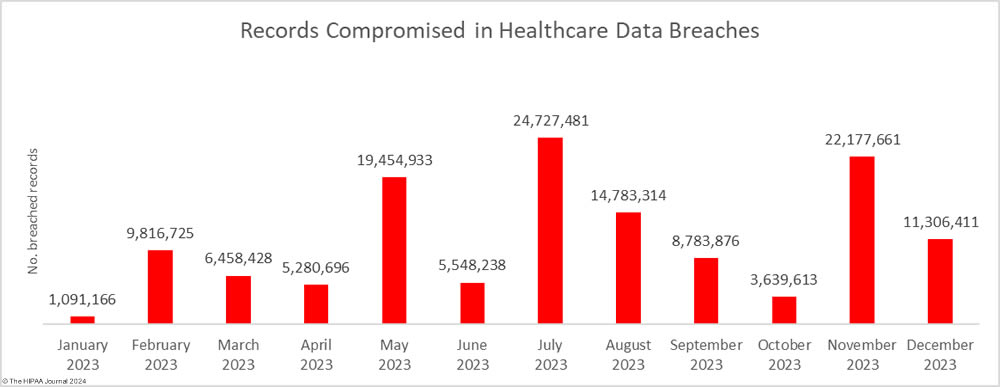
We will explore the year’s data breaches in greater detail and make predictions for the coming year in posts over the next few days but first, let’s take a dive into December’s data breaches to see where and how 11,306,411 healthcare records were breached.
The Biggest Healthcare Data Breaches in December 2023
Two of the largest data breaches of 2023 were reported in December, the largest of which occurred at the New Jersey-based analytics software vendor, HealthEC. Hackers gained access to a system used by more than 1 million healthcare professionals to improve patient outcomes. The platform contained the protected health information of 4,452,782 individuals. The data breach was the second in as many months to result in the exposure of the health data of more than 1 million Michigan residents, prompting the Michigan Attorney General to call for new legislation to hold companies accountable for breaches of healthcare data.
A 2.7 million-record data breach was reported by another business associate, ESO Solutions. ESO Solutions is a provider of software solutions for hospitals, health systems, EMS agencies, and fire departments, and had its network breached and files encrypted with ransomware. At least 12 health systems and hospitals are known to have been affected.
More than 900,000 records were obtained by hackers who gained access to an archive of data from the now defunct Fallon Ambulance Services, which was being stored to meet data retention requirements by Transformative Healthcare, and a cyberattack on Electrostim Medical Services exposed the data of almost 543,000 patients.
It has now been 7 months since the Clop hacking group exploited a zero-day vulnerability in Progress Software’s MOVEit Transfer solution and data breach reports continue to be issued. More than 2,600 organizations worldwide had data stolen in the attacks, with the healthcare industry among the worst affected.
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Cause of Data Breach |
| HealthEC LLC | NJ | Business Associate | 4,452,782 | Hacking incident (Data theft confirmed) |
| ESO Solutions, Inc. | TX | Business Associate | 2,700,000 | Ransomware attack |
| Transformative Healthcare (Fallon Ambulance Services) | MA | Healthcare Provider | 911,757 | Hacking incident (Data theft confirmed) |
| Electrostim Medical Services, Inc. dba EMSI | FL | Healthcare Provider | 542,990 | Hacking incident |
| Cardiovascular Consultants Ltd. | AZ | Healthcare Provider | 484,000 | Ransomware attack (Data theft confirmed) |
| Retina Group of Washington, PLLC | MD | Healthcare Provider | 455,935 | Ransomware attack |
| CompleteCare Health Network | NJ | Healthcare Provider | 313,973 | Ransomware attack (Data theft confirmed) |
| Health Alliance Hospital Mary’s Avenue Campus | NY | Healthcare Provider | 264,197 | Hacking incident (Data theft confirmed) |
| Independent Living Systems, LLC | FL | Business Associate | 123,651 | Hacking incident (MOVEit) |
| Pan-American Life Insurance Group, Inc. | LA | Health Plan | 105,387 | Hacking incident (MOVEit) |
| Meridian Behavioral Healthcare, Inc. | FL | Healthcare Provider | 98,808 | Hacking incident |
| Mercy Medical Center | IA | Healthcare Provider | 97,132 | Hacking incident at business associate (PJ&A) |
| Pan-American Life Insurance Group, Inc. | LA | Business Associate | 94,807 | Hacking incident (MOVEit) |
| Regional Family Medicine | AR | Healthcare Provider | 80,166 | Hacking incident |
| HMG Healthcare, LLC | TX | Healthcare Provider | 80,000 | Hacking Incident (Data theft confirmed) |
| Heart of Texas Behavioral Health Network | TX | Healthcare Provider | 63,776 | Hacking incident |
| Kent County Community Mental Health Authority d/b/a Network180 | MI | Healthcare Provider | 59,334 | Unauthorized email account access |
| Highlands Oncology Group PA | AR | Healthcare Provider | 55,297 | Ransomware attack |
| Southeastern Orthopaedic Specialists, PA | NC | Healthcare Provider | 35,533 | Ransomware attack (Data theft confirmed) |
| Eye Physicians of Central Florida, PLLC, a division of Florida Pediatric Associates, LLC | FL | Healthcare Provider | 31,189 | Hacking incident (Data theft confirmed) |
| Clay County Social Services | MN | Business Associate | 22,005 | Ransomware attack (Data theft confirmed) |
| Bellin Health | WI | Healthcare Provider | 20,790 | Hacking incident |
| Neuromusculoskeletal Center of the Cascades, PC | OR | Healthcare Provider | 19,373 | Unauthorized email account access |
| Independent Living Systems, LLC | FL | Healthcare Provider | 19,303 | Hacking incident (MOVEit) |
| Community Memorial Healthcare, Inc. | KS | Healthcare Provider | 14,798 | Hacking incident |
| VNS Choice dba VNS Health Health Plans | NY | Health Plan | 13,584 | Unauthorized email account access |
| Hi-School Pharmacy | WA | Healthcare Provider | 12,779 | Ransomware attack |
Many HIPAA-regulated entities keep information to the bare minimum in their breach reports, which allows them to meet legal requirements for breach reporting while minimizing the risk of disclosing information that could be used against them in class action lawsuits. The problem with this minimalistic breach reporting is the victims of the breach are not given enough information to accurately assess the risk they face, and the lack of transparency in data breach reporting makes it difficult to accurately assess how hackers are gaining access to healthcare networks and the nature of the attacks.
This is especially true for ransomware attacks and data theft/extortion attacks. Several breaches have been reported as hacking incidents where a possibility of unauthorized access to or theft of patient data, when the threat actors behind the attacks have claimed responsibility and have added the breached entity to their data leak sites. This trend has grown throughout the year.
December 2023 Data Breach Causes and Data Locations
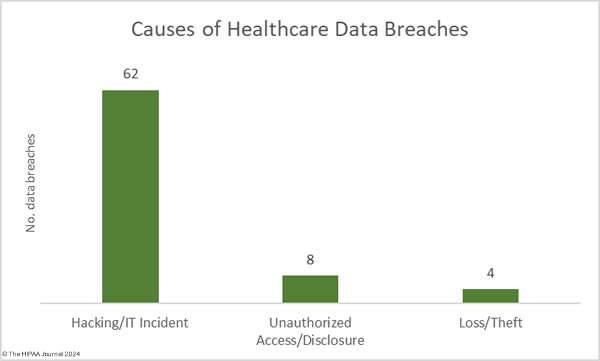
All of December’s data breaches of 10,000 or more records were hacking incidents, which accounted for 83.78% of the month’s 74 data breaches (62 incidents) and 99.79% of the month’s breached healthcare records (11,283,128 records). The average breach size was 181,986 records and the median breach size was 6,728 records. In 2009, hacking incidents accounted for 49% of all data breaches of 500 or more records. In 2023, hacking incidents accounted for 79.72% of all large data breaches. Something clearly needs to be done to improve resiliency to hacking and there are signs of action being taken at the state and federal level.
In December 2023, OCR published its Healthcare Sector Cybersecurity Strategy which details several steps that OCR plans to take to improve cyber resiliency in the healthcare sector and patient safety. The extent to which these plans will be made a reality will depend on Congress making the necessary funding available. OCR is planning a much-needed update to the HIPAA Security Rule in 2024 and has stated that it will establish voluntary cybersecurity goals for the healthcare sector. OCR will be working with Congress to provide financial assistance for domestic investments in cybersecurity to help cover the initial cost. The New York Attorney General has also announced that there will be new cybersecurity requirements for hospitals in the state after a significant increase in cyberattacks, and that funds have been made available to help low-resource hospitals make the necessary improvements.
There were 8 data breaches classified as unauthorized access/disclosure incidents, involving 14,998 healthcare records. The average breach size was 1,875 records and the median breach size was 1,427 records. There were four loss/theft incidents reported in December, two of which involved stolen paperwork and two involved the loss of electronic devices, with the latter preventable if encryption had been used. 8,285 records were lost across these incidents.
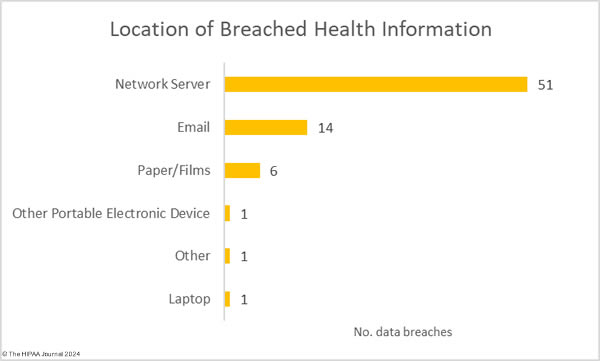
The most common location of breached healthcare data was network services, which is unsurprising given the large number of hacking incidents. 14 data breaches involved protected health information stored in email accounts, three of which resulted in the exposure of more than 10,000 records.
Where did the Data Breaches Occur?
The raw data from the OCR data breach portal shows healthcare providers were the worst affected entity in December with 49 reported breaches of 500 or more records, followed by business associates with 13 breaches, health pans with 11, and a single breach at a healthcare clearinghouse. While healthcare providers suffered the most breaches, it was data breaches at business associates that exposed the most records. Across the 13 business associate-reported breaches, 7,416,567 records were breached, compared to 3,730,791 records in the 49 breaches at healthcare providers. The health plan breaches exposed 156,479 records and 2,574 records were exposed in the healthcare clearinghouse data breach.
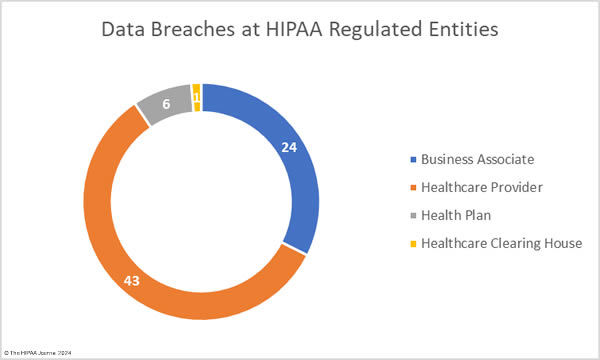
These figures do not tell the full story, as the reporting entity may not be the entity that suffered the data breach. Many data breaches occur at business associates of HIPAA-covered entities but are reported to OCR by the covered entity rather than the business associate. A deeper dive into the data to determine where the breach actually occurred reveals there were 24 data breaches at business associates (7,544,504 records), 43 data breaches at healthcare providers (3,616,078 records), 6 data breaches at health plans (143,255 records), and one breach at a healthcare clearinghouse (2,574 records).
The average size of a business associate data breach was 314,354 records (median: 2,749 records), the average size of a healthcare provider data breach was 84,095 records (median: 5,809 records), and the average health plan data breach was 23,876 records (median: 7,695 records). The chart below shows where the data breaches occurred rather than the reporting entity.
Geographical Distribution of Healthcare Data Breaches
HIPAA-regulated entities in 32 states reported data breaches of 500 or more records in December. California was the worst affected state with 85 large data breaches followed by New York and Texas with 7 reported breaches.
| State | Number of Breaches |
| California | 8 |
| New York & Texas | 7 |
| Florida | 6 |
| Massachusetts | 4 |
| New Jersey, Tennessee & Wisconsin | 3 |
| Arkansas, Connecticut, Illinois, Kansas, Kentucky, Louisiana, Maryland, North Carolina & Washington | 2 |
| Alaska, Arizona, Colorado, Iowa, Michigan, Minnesota, Mississippi, Missouri, Montana, New Mexico, North Dakota, Oregon, South Carolina, Virginia & West Virginia | 1 |
HIPAA Enforcement in December 2023
OCR announced two enforcement actions against healthcare providers in December to resolve alleged violations of the HIPAA Rules. OCR continued its enforcement initiative targeting noncompliance with the HIPAA Right of Access with its 46th enforcement action over the failure to provide individuals with timely access to their medical records. Optum Medical Care of New Jersey settled its investigation and agreed to pay a financial penalty of $160,000 to resolve allegations that patients had to wait between 84 days and 231 days to receive their requested records when they should have been provided within 30 days.
OCR also announced its first-ever settlement resulting from an investigation of a phishing attack. Lafourche Medical Group in Louisiana suffered a phishing attack that resulted in the exposure of the protected health information of almost 35,000 individuals. While phishing attacks are not HIPAA violations, OCR’s investigation uncovered multiple violations of the HIPAA Security Rule, including no risk analyses prior to the 2021 phishing attack, and no procedures to regularly review logs of system activity before the attack. Lafourche Medical Group chose to settle the investigation and paid a $480,000 penalty.
These two enforcement actions bring the total number of OCR enforcement actions involving financial penalties up to 13, the lowest annual total since 2019, although there was a slight increase in funds raised from these enforcement actions with $4,176,500 collected in fines. OCR is pushing Congress to increase the penalties for HIPAA violations to make penalties more of a deterrent and also to provide much-needed funding to allow OCR to clear the backlog of HIPAA compliance investigations, in particular investigations of hacking incidents. Currently, OCR’s hands are tied, as the department’s budget has remained the same for years, aside from annual increases for inflation, yet its caseload of breach investigations has soared.
HIPAA Enforcement by State Attorneys General
State attorneys general have the authority to enforce HIPAA compliance and 2023 saw an increase in enforcement actions. The HIPAA Journal has tracked 16 enforcement actions by state attorneys general in 2023 that resolved violations of HIPAA or equivalent state consumer protection and data breach notification laws. In December, three enforcement actions were announced, two by New York Attorney General Letitia James and one by Indiana Attorney General Todd Rokita. New York has been particularly active this year having announced 4 settlements to resolve HIPAA violations in 2023 and the state also participated in two multi-state actions.
In December, AG James announced a settlement had been reached with Healthplex to resolve alleged violations of New York’s data security and consumer protection laws with respect to data retention, logging, MFA, and data security assessments which contributed to a cyberattack and data breach that affected 89,955 individuals. The case was settled for $400,000. AG James also investigated New York Presbyterian Hospital over a reported breach of the health information of 54,396 individuals related to its use of tracking technologies on its website, which sent patient data to third parties such as Meta and Google in violation of the HIPAA Privacy Rule and New York Executive Law. The case was settled for $300,000.
The Indiana Attorney General investigated CarePointe ENT over a breach of the health information of 48,742 individuals. AG Rokita alleged that CarePointe ENT was aware of security issues several months before they were exploited by cybercriminals but did not address them in a timely manner. There was also no business associate agreement with its IT services provider. The investigation was settled for $125,000.
The data for this report was obtained from the U.S. Department of Health and Human Services’ Office for Civil Rights on January 18, 2023.
The post December 2023 Healthcare Data Breach Report appeared first on HIPAA Journal.
Is Google Workspace HIPAA Compliant?
Google Workspace is HIPAA compliant for services that have “covered functionality”, provided HIPAA-covered organizations subscribe to a Workspace Plan that supports HIPAA compliance and configure the services to comply with the HIPAA Security Rule. To make Google Workspace HIPAA compliant, it is also necessary to agree to Google’s Business Associate Addendum (BAA) to the Workspace Terms of Service Agreement.
Google Workspace – formally known as G Suite – is a collection of productivity and communication services that can be integrated with each other to streamline workflows and enhance collaboration. It is a popular choice for organizations in the healthcare industry because most users already have experience of services such as Gmail and Drive, while most other Workspace services have familiar controls and are intuitive to use.
However, most organizations in the healthcare industry are required to comply with HIPAA – a federal law which led to the development of privacy and security standards for “Protected Health Information” (PHI). The standards govern how PHI can be used and disclosed, and what measures must be put in place to protect the confidentiality, integrity, and availability of PHI created, collected, maintained, or transmitted electronically.
In the context of the question is Google Workspace HIPAA compliant, it is important that – when PHI is created, collected, maintained, or transmitted by Workspace services – the services have controls in place to support HIPAA compliance with the security standards, the controls are configured to comply with the applicable implementation specifications, and that members of the workforce are trained on how to use the services compliantly.
Which Workspace Plan Supports Compliance?
Excluding the personal (free) and “solopreneur” editions of Workspace, there are four subscription plans for business. Although the first three plans – “Starter”, “Standard”, and “Business Plus” – include basic administrative controls, they lack important features such as shared Drives, retention Vaults, and Data Loss Prevention. If any of these plans are used, it may be necessary to integrate third party solutions to ensure HIPAA compliance.
The Enterprise Workspace Plan supports HIPAA compliance without additional integrations. The Enterprise Plan does not limit the number of users, has S/MIME email encryption, and includes enterprise endpoint management to support the compliant use of personal devices on site or in the community. The Enterprise Plan also include a unified Security Center which provides data on external file sharing, malware attacks, and other security threats.
However, although the Enterprise Workspace Plan supports compliance, it is important to be aware that not every Google service included in or connected to the Plan can be used in compliance with HIPAA. Google recommends restricting user access to core services without “covered functionality” (i.e., Google Contacts) and all non-core services not covered by the Workspace Service Agreement (i.e., Google Photos, Blogger, YouTube, etc.).
With regards to restricting user access to Google Contacts, the recommendation will affect the functionality of other HIPAA compliant Workspace services. Therefore, we suggest ignoring Google’s recommendation. Instead, administrators should implement a policy prohibiting PHI being stored in Google Contacts and monitoring compliance with the policy via the Security Center. (Note: Names and contact details are NOT PHI when maintained separately from health information – see “What is Considered PHI under HIPAA?” for a full explanation).
Which Services have Covered Functionality?
The Workspace services that can be configured to be used in compliance with HIPAA and that are covered by the Google Workspace HIPAA compliant BAA are currently:
| Google Workspace Services with Covered Functionality | ||
| Google Calendar | Google Forms | Google Keep |
| Google Chat | Duet AI for Workspace | Google Meet |
| Cloud identity | Gmail | Google Sites |
| Google Drive | Google Cloud Search | Google Tasks |
| Google Docs | Google Groups | Google Vault |
| Google Sheets | Google Voice | Jamboard |
| Google Slides | ||
To configure these services in compliance with HIPAA, it is advisable to follow the guidance in Google’s HIPAA Implementation Guide. The guidance will not be suitable for every covered entity and business associate because it may be necessary to (for example) integrate a third party app with a Google service. If the default guidance is not to allow access by third party apps, this element of guidance will have to be circumnavigated.
Covered entities and business associates that encounter issues with configuring covered Workspace services should be able to take advantage of Google’s customer support channels depending on the subscription (The Admin Help pages are very good for resolving technical issues). However, for HIPAA-related issues, it is probably more beneficial to seek accurate and timely advice from an external HIPAA compliance expert.
The Google Workspace HIPAA Compliant BAA
Before any Workspace service is used to create, collect, store, or transmit PHI, it is necessary to agree to Google’s Business Associate Addendum (BAA) to the Workspace Terms of Service Agreement. The Google Workspace HIPAA compliant BAA is relatively straightforward and there are no contentious clauses that may cause further issues. In most cases it is possible for Super Administrators to digitally sign the Addendum via the Admin console.
However, before digitally signing the Google Workspace HIPAA compliant BAA, it is important Super Administrators review the Terms of Service Agreement. While the entire agreement should be reviewed, Super Administrators are advised to pay careful attention to the Customer Obligations in Clause #3, which:
- Prohibit the storage and transmission of PHI without a signed BAA,
- Makes customers responsible for end user compliance with the Agreement,
- Requires customers to prevent and terminate unauthorized use of Workspace, and
- Requires customers to notify Google of any unauthorized use of, or access to, a Workspace account (including compromised passwords).
A failure to comply with the Terms of Service Agreement could result in suspension of the account and the removal of content – regardless of compliance with the Google Workspace HIPAA compliant BAA. If this happened to a Workspace account in which PHI was stored, it would not only result in an operational disruption, but also in a HIPAA violation for failing to ensure the availability of the removed PHI.
Why Provide Training on How to Use Gmail?
Google is not unique in having compliance clauses in both its Terms of Service Agreement AND in its Business Associate Agreement. Most software providers do the same. However, many workplace members will already have personal Google accounts which they use with little consideration for the privacy and security of the information they receive, store, and share. (You can check this theory by asking how many users have 2FA enabled on their personal accounts).
Using Gmail and other Workspace services in compliance with HIPAA is a lot different from using the same services for personal use. To ensure the privacy and security of PHI, workforce members should be trained on permissible disclosures, the minimum necessary standard, and verifying the identity of unknown correspondents who request PHI. It is essential they are also trained on detecting malware, phishing emails, and other threats to the security of PHI.
With regards to what has previously been discussed, it is important that members of the workforce are told not to save PHI with contact information, not to import files from non-covered services (i.e., Google Photos), and not to export files to non-covered services (i.e., Blogger). Even if these access to these services have been disabled, inventive workforce members can often find ways to circumnavigate controls to “get the job done”.
Is Google Workspace HIPAA Compliant? Conclusion
It may appear as if there are a lot of hurdles to overcome in order to make Google Workspace HIPAA compliant, but they are not insurmountable – and the benefits are more than worthwhile. Not only can covered entities and business associates in the healthcare sector share PHI compliantly to streamline workflows and enhance collaboration, but they can also better communicate with patients via a range of chat, phone, and video communication tools.
If you would like to find out more about using Google Workspace in your healthcare environment, Google offers a free 14 day trial for up to ten users. This should be long enough for Administrators to configure covered services in compliance with the Security Rule’s implementation specifications and to identify any user issues that may materialize as a result. If, during the free trial, you encounter HIPAA-related issues, you will also have time to speak with a HIPAA compliance expert before committing to a Workspace subscription.
The post Is Google Workspace HIPAA Compliant? appeared first on HIPAA Journal.
Growth99 Unveils Groundbreaking HIPAA-Compliant Solution for Global Med Spa Industry – Yahoo Finance
New HIPAA Rules
The New HIPAA Rules and the Changes for Reporting Breaches of PHI
Although the new HIPAA rules introduced in the Final Omnibus Rule of 2013 did not make many changes to the existing Security and Privacy Rules, they did have significant implications for covered entities that have failed to take measures to prevent the unauthorized disclosure of Protected Health Information (PHI).
Whereas previously, covered entities could avoid reporting breaches of PHI when there was a low risk of harm to a patient´s reputation or finances, the new HIPAA rules stipulate that all breaches of PHI must now be reported to the Office for Civil Rights (OCR) unless a documented procedure is completed that justifies the failure to report the breach.
The documented procedure has to demonstrate that there was a low risk of harm to the patient due to the nature of the PHI that was disclosed or due to the person(s) to whom it was disclosed. If multiple identifying elements have been disclosed, or the person to whom it was disclosed is unknown, HIPAA covered entities must report the breach to the OCR – unless it can be proven that the breach of PHI did not result in an unauthorized disclosure, or the risk of harm to a patient was mitigated by the destruction of the disclosed PHI.
In addition to this revised criteria for reporting breaches of PHI to the OCR, the new HIPAA rules increased the fines for non-compliance with the Security and Privacy Rules – the additional revenue being allocated to tougher enforcement of HIPAA. Shortly following the release of the new HIPAA rules, it was announced that the OCR would be conducting a round of audits – a worrying concern for any covered entity that has still failed to take measures to prevent the unauthorized disclosure of PHI.
How to Avoid Data Breaches with Secure Messaging
Rather than finding ways to avoid reporting data breaches to the OCR, it is in a covered entity´s best interests to avoid data breaches altogether. Studies conducted into the primary reasons for the unauthorized disclosure of PHI report that the theft of laptops, mobile devices and USB Flash drives account for nearly half of all PHI breaches. Therefore, these risks of harm to a patient´s reputation or finances should be the first to be eliminated.
One of the best solutions for achieving this objective is secure messaging – a communications platform that protects the integrity of PHI and prevents the unauthorized disclosure of Protected Health Information by encapsulating PHI within a private network. Secure messaging is an ideal and HIPAA compliant alternative to emails and SMS, as safeguards exist to prevent PHI being saved to a user´s device or a USB Flash drive.
Secure messaging also restricts access to PHI to authorized users, who can then communicate encrypted PHI with other authorized users via secure messaging apps. The secure messaging apps work across all operating systems and devices so that authorized users retain the same speed and convenience of modern technology as they currently enjoy using personal mobile devices to support their workloads.
All activity on the secure messaging network is monitored to ensure compliance with the new HIPAA rules and the secure messaging policies that have been implemented to support them. In the event that a laptop of Smartphone – to which a message containing PHI has been sent – is stolen, administrators have the ability to remote delete all protected Health Information and PIN-lock the app to prevent the unauthorized disclosure of PHI.
The Comprehensive Benefits of Secure Messaging
The mechanisms included in secure messaging solutions to ensure 100% message accountability have resulted in a significant acceleration of the communications cycle in healthcare organizations. Phone tag has been practically eliminated in many healthcare organizations that have implemented a secure messaging solution to comply with the new HIPAA rules – resulting in increased productivity among healthcare providers.
The group messaging facility on the secure messaging apps has been proven to foster collaboration between healthcare providers, and also to accelerate patient admissions and hospital discharges – saving many medical facilities more than $500,000 per year. Studies into the cost of operating a secure messaging solution have also found secure messaging up to 40% less expensive than alternative, unsecure channels of communication.
As well as reducing costs, increasing staff efficiency and helping healthcare organizations to comply with the new HIPAA rules, secure messaging solutions have also been beneficial to patients. According to a 2015 study by the Tepper School of Business at the Carnegie Mellon University, patient safety issues are reduced by 27% and medication errors reduced by 30% when a secure messaging solution is integrated with a healthcare organization´s EMRs.
The post New HIPAA Rules appeared first on HIPAA Journal.
Is Apple Pay HIPAA Compliant? – HIPAA Journal
Is Apple Pay HIPAA Compliant?
Apple Pay is not HIPAA compliant – but, but due the way the payment service works, Apple Pay does not need to be HIPAA compliant before the service can be used by healthcare providers to collect payments from patients, or by health plans to collect payments from plan members. In addition, the payment service is exempted from HIPAA under §1179 of the HIPAA Act.
What is Apple Pay?
Apple Pay is a mobile payment service available on iPhones, iPads, Apple Watches, and other Mac devices that facilitates online, app, and contactless payments. The service works by allowing users to enter the details of their payment cards into an Apple Wallet app. The app then sends the user’s Apple account and device information to the card issuer and creates a unique Device Account Number for each card.
When a user wants to use Apple App to pay for goods or services, they either click on an Apple Pay button for online and in-app purchases, or run their device over a Near Field Communications (NFC) reader for in-store purchases. Apple Pay sends the payment request and the Device Account Number to the card issuer, where the payment is processed. Apple does none of the processing. It only facilitates the payment.
Because of the way the payment service works, the organization in receipt of the payment never has access to the user’s debit or credit card number – or, in the context of is Apple Pay HIPAA compliant – any information that could be used to identify the user. Even Apple does not know what a user buys, where they bought it from, or how much they paid for it. Due to this high level of privacy, any information sent through the service would not qualify as Protected Health Information (PHI).
HIPAA Exempts Payment Services Anyway
Even without this high level of privacy, it would not be necessary to make Apple Pay HIPAA compliant and sign a Business Associate Agreement with Apple as §1179 of the HIPAA Act exempts “entities engaged in authorizing, processing, clearing, settling, billing, transferring, reconciling, or collecting payments for a financial institution. The exemption was confirmed by HHS’ Office for Civil Rights in the preamble to the HIPAA Final Omnibus Rule in 2013.
However, this exemption only applies to the payment facilitation element of Apple Pay. If a covered entity or business associate uses Apple Pay for B2B transactions, there is no exemption for PHI stored in an Apple Wallet app to support transactions or reconcile payments. As Apple will not sign a Business Associate Agreement for the Apple Wallet app, it is a violation of HIPAA to store any individually identifying health information in the Apple Wallet app.
It may also be important for covered entities and business associates to identify – and conduct risk assessments on – any third party integration with Apple Pay. If Apple Pay is used (for example) to reconcile payments, the reconciliation software must be HIPAA compliant and Business Associate Agreements must be entered into with the software vendors. Members of the workforce may also need security awareness training on using Apple Pay in compliance with HIPAA.
Is Apple Pay HIPAA Compliant? Conclusion
For the reasons discussed above, Apple Pay does not have to be HIPAA compliant in order for covered entities and business associates to use the service to collect payments from patients and plan members. When used for B2B transactions, covered entities and business associates may have to implement Apple Pay HIPAA compliant integrations and conduct risk assessments if the integrations will create, collect, maintain, or transmit PHI. Covered entities and business associates with questions relating to is Apple Pay HIPAA compliant should seek professional compliance advice.
The post Is Apple Pay HIPAA Compliant? appeared first on HIPAA Journal.