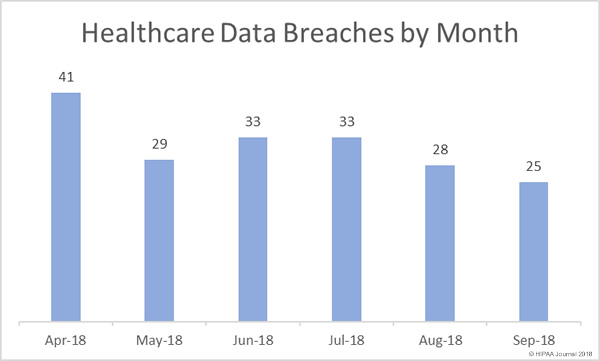
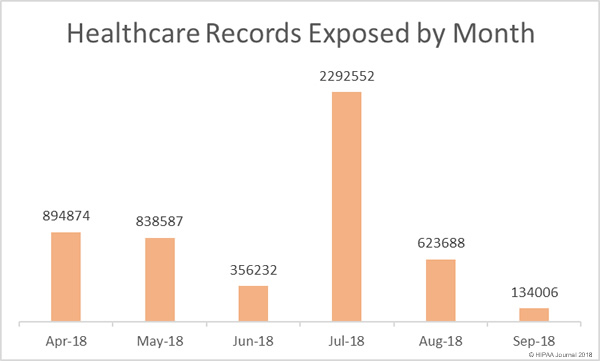
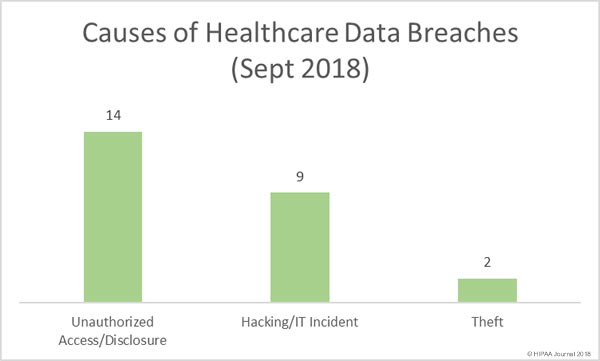
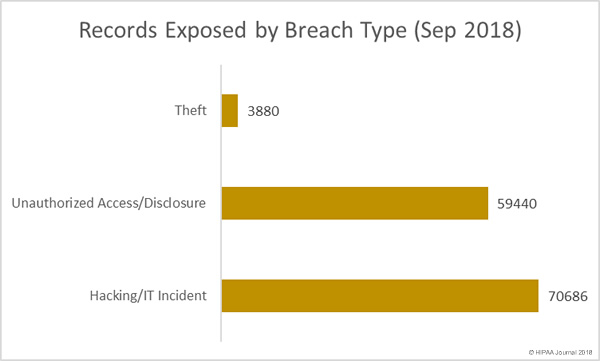
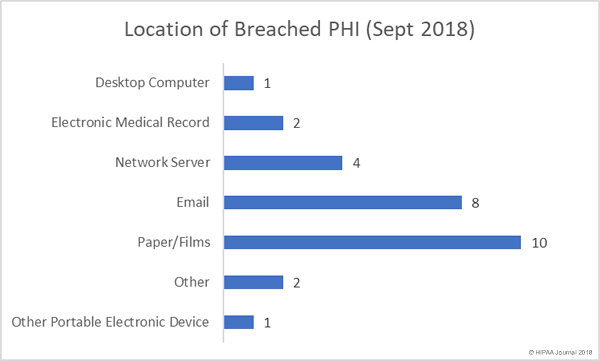
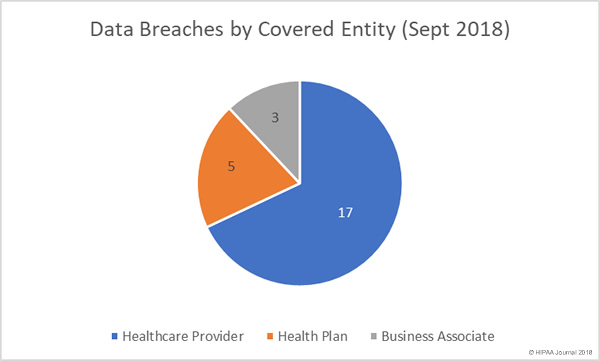
For the past three years, security awareness training company MediaPRO has conducted an annual study of employees’ security awareness and knowledge of cybersecurity best practices.
The study measures the susceptibility of employees to a wide range of security threats and assesses their ability to identify phishing threats, possible malware infections, and cloud computing and social media risks. Their knowledge of best practices concerning physical security, working remotely, and reporting security incidents is also tested.
This year, 1,024 employees from 7 industry sectors took part in the State of Privacy and Security Awareness study and were asked questions relating to all of the above aspects of privacy and security.
MediaPRO assigned each participant a category based on the percentage of questions they got right:
- Hero – An individual with an excellent understanding of security and how to protect assets.
- Novice – Someone that has a reasonable understanding of the basics of security but needs to improve their knowledge in key areas.
- Risk – An individual whose lack of understanding of threats and best practices represents a considerable risk to their organization.
This year, there was an improvement in the number of employees who ranked as hero – 25% of those taking part in the study. However, 75% of employees lacked security awareness to some degree and answered fewer than 90% of the questions correctly.
The figures are considerably worse than last year across the board. In 2016, only 16% of employees were rated as risks. In 2017, the percentage increased to 19%, and this year 30% of employees were rated as a risk. The percentage of heroes also fell year-over-year from 30% in 2017 to 25% in 2018. 45% of participants were rated as novices this year, down from 51% in 2017.
Employees were worse than last year at reporting suspicious activity, identifying physical security risks, cloud computing security, identifying personal information, identifying malware infections, and identifying possible phishing attempts. A quarter of employees took risks when working remotely and while on social media sites, compared with one of respondents fifth last year.
Employees in management roles or higher performed worse than workers in lower positions. 77% of managers (and above) were found to lack security awareness compared to 74% of lower workers.
One of the most worrying findings was the failure of employees to identify phishing emails, given the increase in phishing attacks in recent years. In 2017, 8% of employees got phishing questions incorrect. This year, 14% of employees failed to answer the questions correctly. There was also a lack of understanding email threats, in particular Business Email Compromise (BEC) scams, which 58% of employees failed to correctly define.
While 8 out of 10 employees were able to identify phishing emails in the test, 18% chose to open an unexpected attachment or click on a link in an email from an unknown sender to find out where it went. Worse still, finance employees were the most susceptible to phishing attacks based on the assessments.
“The lack of awareness when it came to phishing emails was particularly troubling,” explained MediaPRO in the report. “We put more of a focus on phishing this year because of the massive thorn in the sides of IT managers and CISOs it represents. The added focus given to phishing in our survey unfortunately revealed additional weaknesses.”
The 2018 State of Privacy and Security Awareness Report can be downloaded on this link.
The post Study Reveals 75% of Employees Lack Security Awareness appeared first on HIPAA Journal.