A delayed October 2025 healthcare data breach report due to the government shutdown for the whole of the month, which caused a significant delay at the HHS’ Office for Civil Rights, which failed to upload any data breach reports in October. The shutdown ended on November 12, 2025, and the HHS had a considerable backlog of data breaches to add to the data breach portal. When a data breach report is received, OCR verifies the data, a process that may take up to around two weeks, before it is added to the OCR breach portal. Data breaches continued to be added for October well into December.

Based on data obtained from OCR on December 31, 2025, OCR received 28 reports of data breaches affecting 500 or more individuals in October – the lowest monthly total of the year, the lowest total since the 28 reported data breaches in May 2020, and a 31.7% month-over-month reduction in large healthcare data breaches.
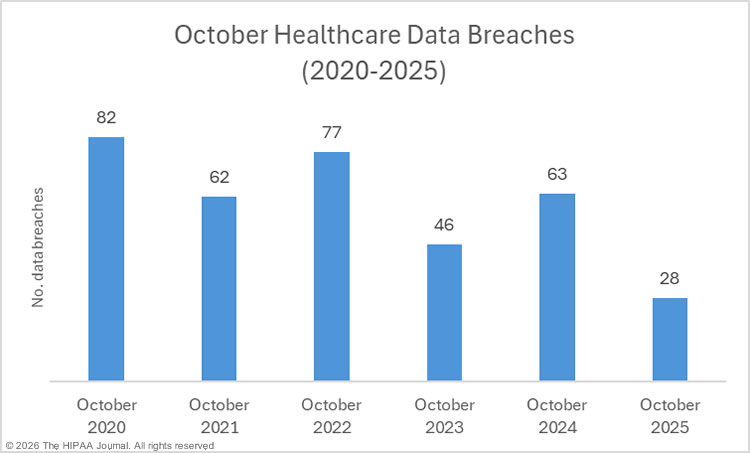
While there has been a downward trend in data breaches, the October total is suspiciously low, which could indicate the backlog of data breach reports has yet to be cleared. The totals will be better reflected in our 2025 healthcare data breach report, due for publication in late January, and our healthcare data breach statistics page.
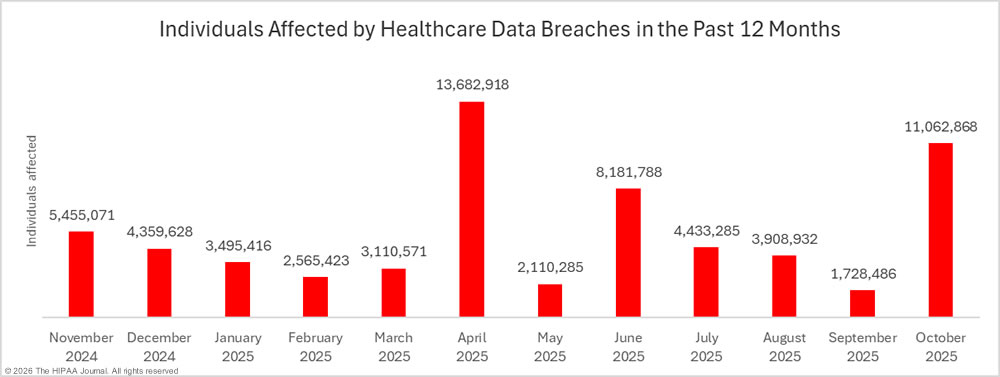
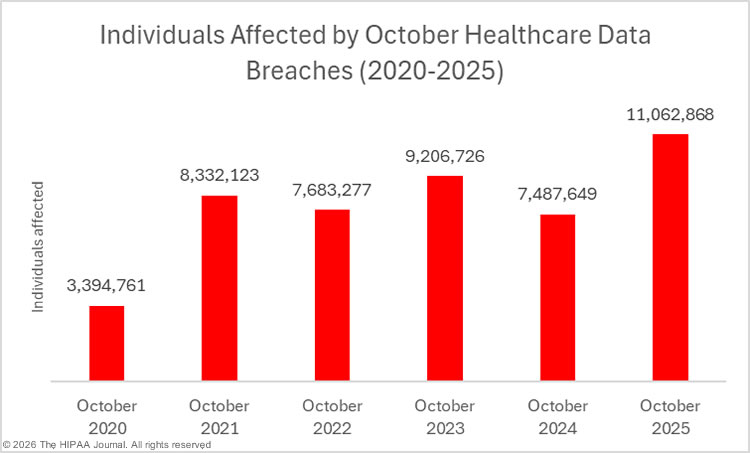
While breach numbers are down, the number of affected individuals increased by 540% month-over month to 11,062,868 individuals – the second-highest monthly total of the year. That total is certain to increase well past April’s total, as the largest data breach of the month is still under investigation and the number of affected individuals has yet to be confirmed.
The Largest Healthcare Data Breaches Reported in October 2025
In October, 7 healthcare data breaches were reported that affected more than 10,000 individuals, all of which were network server hacking incidents. The largest data breach of the month occurred at the business associate Conduent Business Services, a provider of back-office services to healthcare providers, health plans, and government agencies. Conduent’s client list includes major U.S. health insurers such as Humana and Premera Blue Cross.
Conduent experienced a hacking incident in May 2025, and while not stated as a ransomware attack, the SafePay ransomware group claimed responsibility. On its data leak site, SafePay claimed to have stolen 8.5 terabytes of data. Conduent notified the HHS’ Office for Civil Rights that 42,616 individuals had been affected; however, a few months later, the Oregon Attorney General was informed that more than 10.5 million individuals were affected nationwide.
Since the data for this report were compiled, there has been a further breach report from Conduent. The Texas Attorney General has been informed that the Conduent data breach affected almost 14.8 million individuals in Texas alone.
The HIPAA Breach Notification Rule requires data breaches to be reported to OCR within 60 days of the discovery of a data breach. If the total number of affected individuals is not known, an estimate should be provided. HIPAA-regulated entities often submit a breach report using a placeholder figure of 500 or 501 affected individuals when the data review is ongoing. In October, two data breaches were reported with suspected 501 placeholder totals.
Causes of December 2024 Healthcare Data Breaches
As is usually the case, hacking and other IT incidents dominated the breach reports in October, accounting for 21 (75%) of the month’s data breaches and 99.8% of the affected individuals. Across the 21 data breaches, 11,037,882 individuals had their protected health information exposed or stolen. The average breach size was 525,613 individuals, and the median breach size was 6,633 individuals.

The next most common category of data breaches was unauthorized access/disclosure incidents. There were 7 of these incidents in October, affecting 24,986 individuals. The average breach size was 3,569 individuals, and the median breach size was 3,177 individuals.
While loss and theft incidents were among the most common types of data breaches when OCR first started publishing healthcare data breach data in 2009, along with improper disposal incidents, they are relatively rare. No loss, theft, or improper disposal incidents were reported in October. The most common location of breached protected health information in October was network servers, with email the second most common location of breached PHI.

Where did the Data Breaches Occur?
Healthcare providers reported 20 data breaches in October (472,481 affected individuals), 4 data breaches were reported by health plans (60,358 affected individuals), and four data breaches were reported by business associates of HIPAA-covered entities (10,530,029 affected individuals)
When a data breach occurs at a HIPAA business associate, the business associate must report the data breach to each affected covered entity, and the covered entity must decide who should send out individual notifications and notify OCR and the media. Some covered entities choose to report business associate breaches to OCR and issue their own notifications, while others delegate that responsibility to the business associate. If a business associate works with multiple covered entities, some of their covered entity clients may report the breach, while others delegate the responsibility to the business associate.
The consequence of that is that business associate data breaches are often underrepresented in many healthcare data breach reports. The HIPAA Journal calculates where the breach occurred rather than the entity that reported the breach to ensure business associate data breaches are reported accurately. As you can see from the pie chart below, while 4 data breaches were reported by business associates, 9 of the month’s data breaches occurred at business associates.


Geographic Distribution of Healthcare Data Breaches
HIPAA-regulated entities in 18 U.S. states reported data breaches in October. Florida and Texas were the worst-affected states in October, with three large healthcare data breaches reported by entities headquartered in each of those states.
| States |
Breaches |
| Florida & Texas |
3 |
| Alaska, Arizona, California, Illinois, New Jersey & Pennsylvania |
2 |
| Kentucky, Massachusetts, Michigan, Missouri, Montana, Nebraska, New Mexico, Ohio, Oklahoma & Utah |
1 |
While Florida and Texas had the highest number of data breaches, each affected a relatively low number of individuals. Unsurprisingly, given the scale of the data breach at Conduent Business Services, New Jersey was the worst-affected state, although that total includes individuals across the United States.
| State |
Individuals Affected |
| New Jersey |
10,603,849 |
| Pennsylvania |
200,501 |
| New Mexico |
75,054 |
| Michigan |
55,000 |
| Nebraska |
43,728 |
| Texas |
14,233 |
| Utah |
10,800 |
| California |
9,700 |
| Kentucky |
9,536 |
| Illinois |
9,405 |
| Florida |
8,503 |
| Oklahoma |
6,633 |
| Montana |
5,617 |
| Arizona |
4,177 |
| Alaska |
2,641 |
| Missouri |
1,680 |
| Ohio |
1,310 |
| Massachusetts |
501 |
HIPAA Enforcement Activity in October 2025
The government shutdown for the entire month of October meant all but the most critical workflows ground to a halt at the Department of Health and Human Services. As such, there were no announcements about HIPAA settlements and civil monetary penalties, and no penalties were announced by state attorneys general in October.
The post October 2025 Healthcare Data Breach Report appeared first on The HIPAA Journal.







